What is a Proxy Server?
A proxy server acts as an intermediary between a user and the websites they visit. It can be set up as a firewall or web filter, adding an extra layer of security that helps protect private networks from cyber attackers and malware. Essentially, a proxy server is a gateway that anonymously passes data between users and the internet. This intermediary can be a computer system or a router that facilitates secure communication on behalf of the user.
When an individual uses a browser, they typically communicate directly with the internet. However, with a proxy server in place, the proxy handles all communication with the internet, providing an additional level of security and privacy. IT companies often rely on proxy servers to filter out potentially harmful data before it reaches their networks.
How Does a Proxy Server Works?
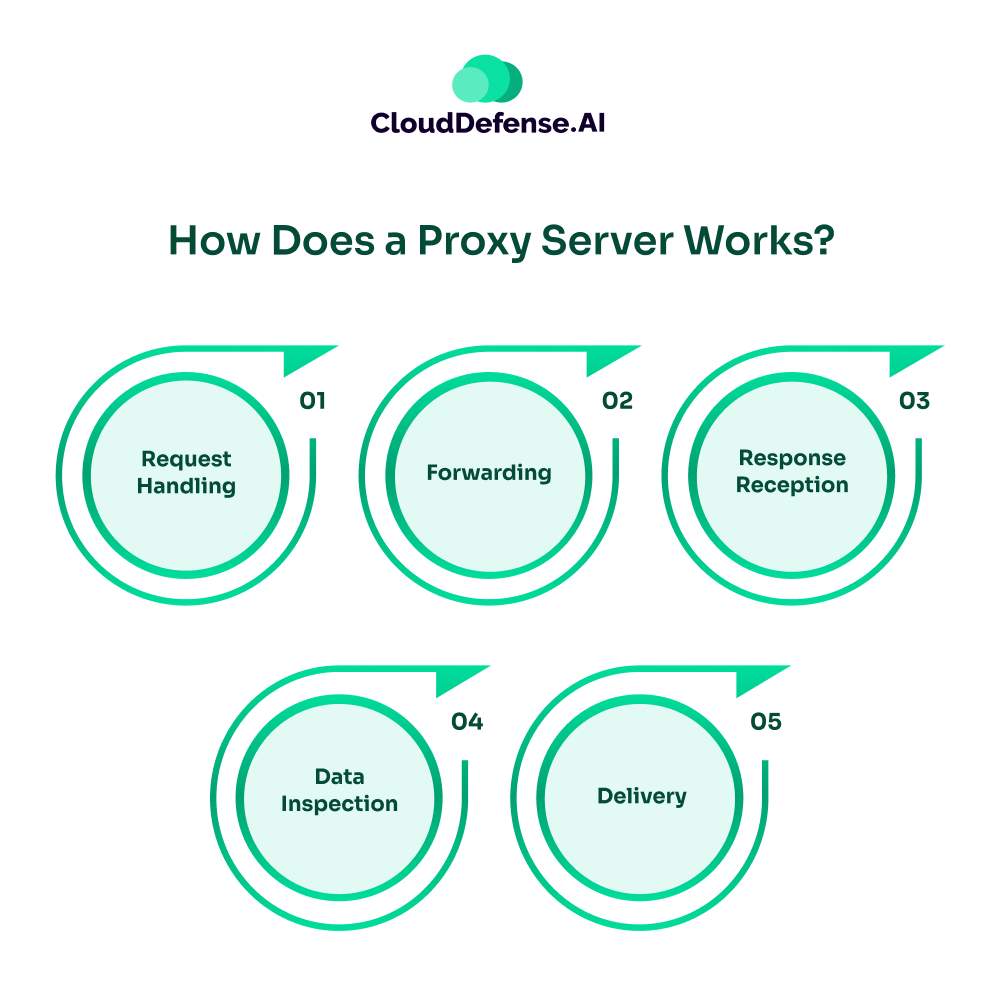
Every device connected to the internet has an Internet Protocol (IP) address, which is used to identify it online. Proxy servers utilize this IP address to function. Here’s a simplified overview of how a proxy server works:
- Request Handling: When a device makes a request to access the internet through a proxy server, the proxy reads and interprets the request.
- Forwarding: The proxy server then forwards this request to the appropriate internet server.
- Response Reception: The internet server processes the request and sends the requested data back to the proxy server.
- Data Inspection: The proxy server receives this data, examines it for any potential malware or threats, and ensures it is safe.
- Delivery: Once verified, the proxy server forwards the safe data back to the original requesting device.
Benefits of a Proxy Server?
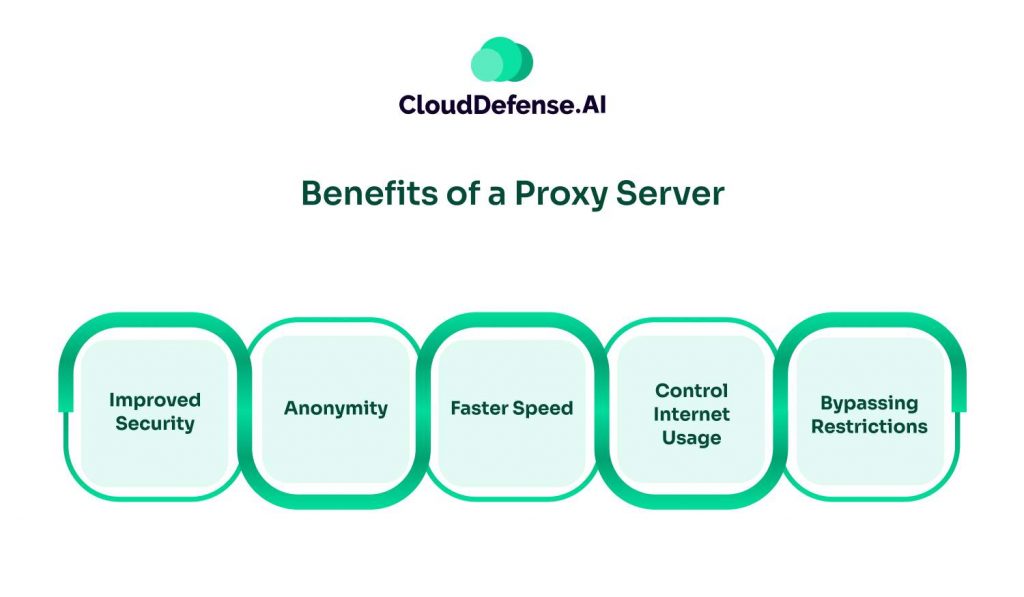
Proxy servers offer several significant advantages that make them indispensable for many organizations and individuals. Here are some of the primary benefits:
1. Improved Security
One of the main reasons companies use proxy servers is to enhance security. Data breaches can be incredibly costly, with global losses due to cybercrime reaching over $6 trillion in 2021 and expected to exceed $10.5 trillion annually by 2025. Proxy servers act as a filter, blocking malicious data before it reaches a company’s internal network. While not a complete solution to all cyber threats, proxy servers significantly reduce the risk of cyberattacks by adding an extra layer of defense.
2. Anonymity
Proxies help maintain anonymity by masking the IP address of the user or organization. This is crucial for protecting sensitive data, such as a company’s research and development activities, from being exposed or stolen. By obscuring the IP address, proxies prevent potential spies or malicious actors from tracking online activities and gaining access to confidential information.
3. Faster Speed
Proxy servers can enhance internet speed through caching, which involves storing frequently visited websites. This eliminates the need to repeatedly send requests to internet servers for the same pages, speeding up access. Additionally, proxies can compress traffic and remove ads from websites, further improving browsing speed and efficiency.
4. Control Internet Usage
Organizations can use proxy servers to control and monitor internet usage within their networks. This includes blocking access to distracting or inappropriate websites, ensuring that employees remain focused on work-related tasks. Network administrators can also monitor internet activity to prevent illegal or improper usage, maintaining a productive and secure online environment.
5. Bypassing Restrictions
Proxy servers enable users to bypass geo-restrictions on certain websites. For businesses needing access to region-specific content, proxies can mask the IP address and provide access as if the user is located in an allowed region. This capability is essential for conducting global research and accessing necessary information without being hindered by geographic limitations.
Difference Between Forward and Reverse Proxy Servers
Forward and reverse proxy servers are two essential tools in network management, each serving distinct purposes.
Forward Proxy Servers act as intermediaries between a user’s device and the internet. When a user requests access to a website, the forward proxy fetches the information on behalf of the user, masking their IP address. This adds a layer of privacy and security, filters content, and can cache data for faster access.
Reverse Proxy Servers, on the other hand, sit between the internet and a web server, handling incoming requests to the server. They distribute incoming traffic across multiple servers to balance the load, enhance performance, and provide an extra security layer by hiding the server’s IP address from potential attackers.
The primary difference lies in their direction of service: forward proxies protect the client by acting on their behalf to the internet, while reverse proxies protect the server by managing incoming traffic from the internet.
What Protocol do Proxy Servers Use?
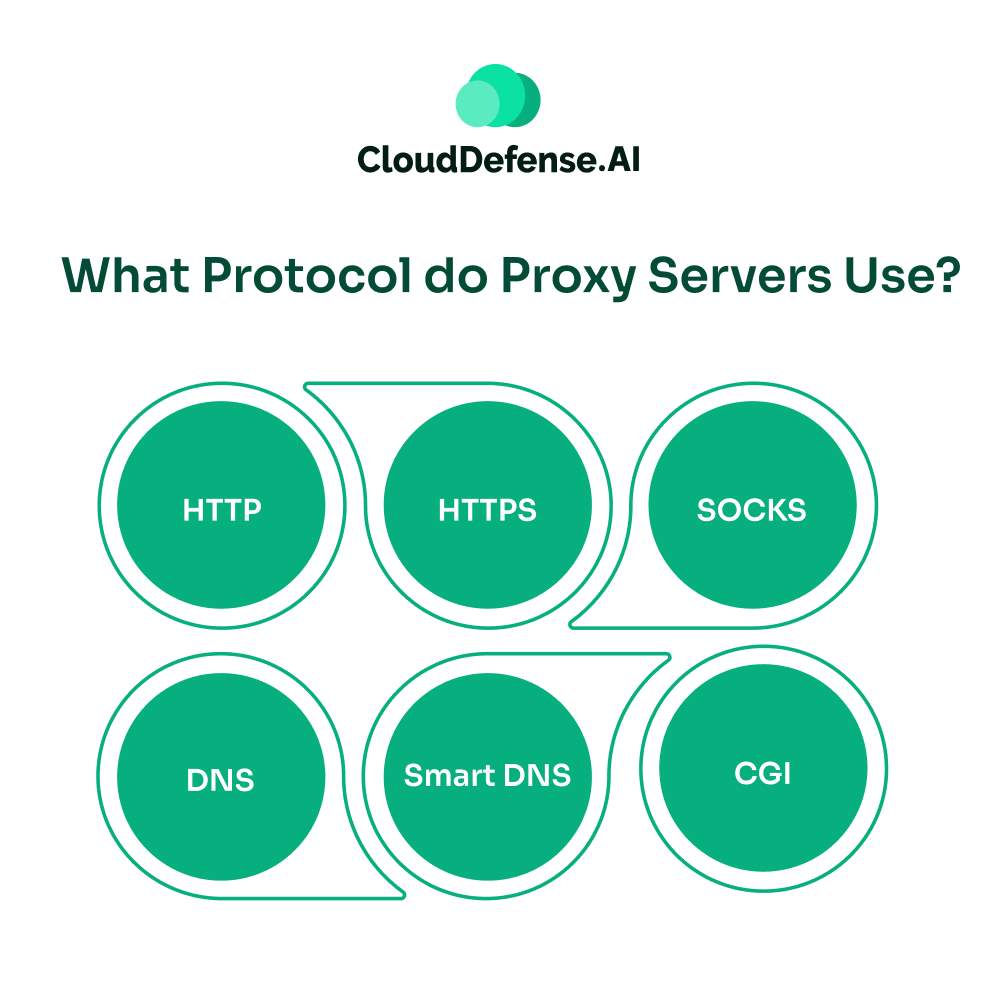
Proxy servers use a variety of protocols to manage and secure internet traffic, catering to different needs and levels of security. Here’s a look at some of the most relevant protocols used by consumer-level proxies.
1. HTTP
HTTP proxies utilize the unsecured Hypertext Transfer Protocol to route user traffic and downloads. Typically configured through the browser or a web interface, these proxies are known for their speed and accessibility. However, they do not support connections to HTTPS-protected destinations, limiting their usefulness given the prevalence of HTTPS websites in 2023.
2. HTTPS
HTTPS proxies, also known as SSL proxies, operate similarly to HTTP proxies but use the secure HTTPS protocol. This encryption enables users to connect safely to HTTPS web domains protected by SSL certificates, ensuring data privacy and integrity during transmission.
3. SOCKS
SOCKS proxies, short for SOCKets Secure, use the SOCKS5 protocol to facilitate data and traffic transfer. These proxies route user traffic through a third-party server via Transmission Control Protocol (TCP), offering more versatility than HTTP and HTTPS proxies as they support a wider range of data types, including email and peer-to-peer sharing.
4. DNS
DNS proxies work by forwarding DNS requests from the user to a DNS-based web domain or server. These proxies automatically select a server to forward the user’s request, often bypassing network restrictions. This capability is particularly useful in regions with heavy internet censorship, like China.
5. Smart DNS
Smart DNS proxies allow users to spoof their geolocation by diverting only DNS requests. This selective routing is advantageous for accessing geo-restricted content, such as streaming services. For instance, if you’re traveling abroad and want to continue watching a show available only in your home country, a Smart DNS proxy can make this possible.
6. CGI
CGI-based proxies, or Common Gateway Interface proxies, are accessible via web browsers and are ideal for environments where installing software is restricted, such as public libraries or corporate networks. These web-based proxies provide a way to utilize proxy features without needing administrative rights on the device.
Final Words
Proxy servers act as intermediaries between you and the internet. They enhance your online experience by providing benefits like privacy, security, and faster load times. Whether you’re an individual concerned about your digital footprint or a business looking to protect sensitive data, understanding proxy servers will benefit you greatly. By acting as a shield and a speed booster, proxy servers play a major role in the modern digital space.







