What is Root Cause Analysis in Cybersecurity?
When a data breach occurs, it’s chaos. Alarms blare, teams scramble, and everyone asks, “What just happened?” But Root Cause Analysis has answers to it. It’s not about quick fixes or pointing fingers. It’s about digging deep to find out why the breach happened in the first place.
Cyber attacks come in all shapes and sizes. You’ve got your classic malware, sneaky phishing attempts, and even insider jobs. Each attack is unique, like a digital fingerprint. That’s why we can’t use a one-size-fits-all approach.
Here’s the kicker: sometimes, it’s not just one thing that went wrong. Often, you’re dealing with a perfect storm of vulnerabilities. Root Cause Analysis helps you peel back the layers and expose all the weak spots.
By getting to the bottom of things, you’re not just cleaning up the current mess. You’re building a stronger defense for the future. It’s about learning from your mistakes and staying one step ahead of the bad guys.
How do we Know the Root Cause?
Identifying a root cause isn’t a straightforward process. It’s more of an art than a science, and it varies depending on who you ask and where you work. In software projects, you’ll often see a dedicated Root Cause Analysis team taking charge.
These know the ins and outs of the problem, and they’re led by an Root Cause Analysis manager. Some places call this “incident response” and fold it into their post-incident reviews.
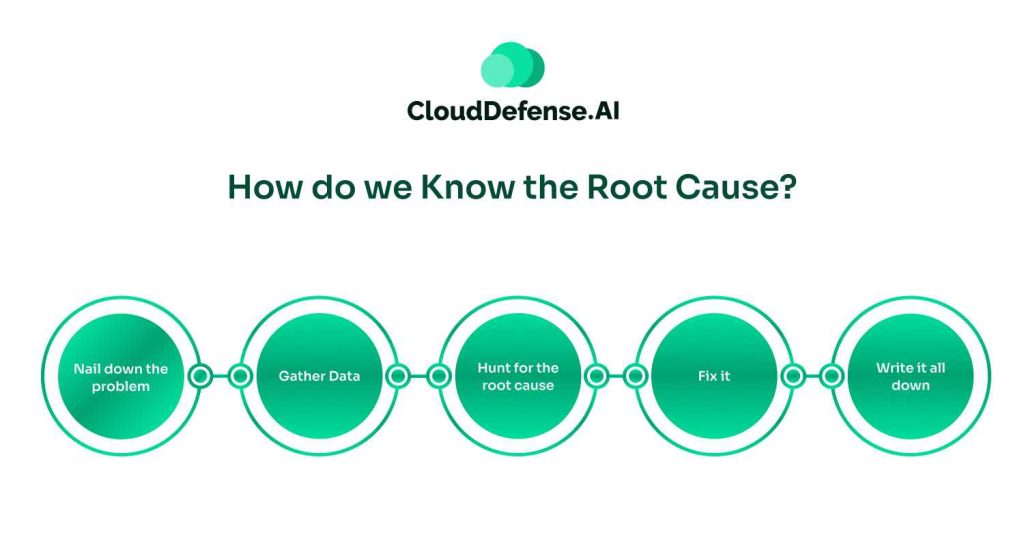
Now, let’s break down the basic steps:
1. Nail down the problem. You’ve got to define what’s wrong and what symptoms you’re seeing. Maybe it’s a machine acting up, a process gone haywire, or someone messed up. Once you’ve got that, isolate any factors you think might be contributing. It’s like quarantining the issue while you figure out what’s really going on.
2. Gather Data. Grab everything you can – incident reports, screenshots, logs, you name it. Talk to anyone who was involved. You’re building a timeline here, figuring out what happened when, what systems were affected, how long it went on, and what kind of damage we’re looking at.
3. Hunt for the root cause. This is where the Root Cause Analysis team rolls up their sleeves. They’ll use tools like Fishbone diagrams and Pareto charts to brainstorm. The Root Cause Analysis manager keeps things on track, making sure everyone collaborates without pointing fingers.
4. Fix it. Once you know what’s causing the problem, you might have a few options for fixing it. The team needs to figure out the best solution and when to put it in place. After that, keep an eye on things to make sure the fix sticks.
5. Write it all down. This step is crucial for preventing future headaches. Document everything – the problem, how you solved it, and any recommendations for improving things going forward. This becomes your playbook for handling similar issues down the line.
Remember, the goal here isn’t just to patch things up. It’s about digging deep, learning from what went wrong, and making sure it doesn’t happen again. It’s a continuous process of improvement, not a one-and-done deal.
Root Cause Analysis Methods
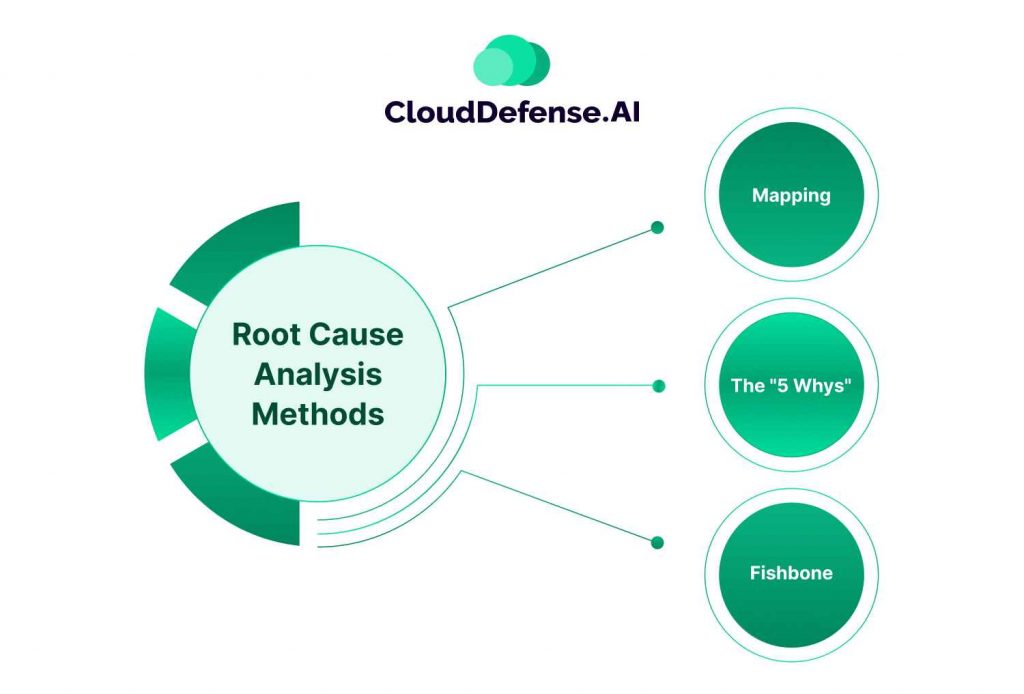
Let’s dive into these three Root Cause Analysis methods. They’re real problem-solving tools that can make a big difference in how we handle security incidents.
Mapping
This one’s all about visualization. After an incident hits, the team creates a detailed cause map. It’s like drawing a roadmap of what went wrong. The goal? Answer three key questions:
- What happened?
- Why did it happen?
- How do we stop it from happening again?
The map connects all the dots between cause and effect. It’s like playing detective, following the clues until you uncover the root cause.
The “5 Whys”
This method is deceptively simple, but don’t let that fool you. It’s powerful stuff. You start by asking “Why?” and then keep digging deeper with each answer. The idea is to peel back the layers of the problem until you hit the core issue.
Here’s the kicker: sometimes you might need to ask “Why?” more than five times. And don’t be afraid to throw in some “What?”, “When?”, and “How?” questions too. Remember, one root cause might be hiding another, so keep digging!
Fishbone
Also known as the Ishikawa diagram, this method is a bit different. It’s great for separating symptoms from root causes. Picture a fish skeleton – the head is your problem, and the bones are potential causes.
Fun fact: this method started in shipbuilding for quality control. Now it’s used everywhere from cybersecurity to marketing. It’s a versatile tool that helps teams see the big picture and identify all the factors that might be contributing to a problem.
Each of these methods has its strengths. The key is choosing the right one for your situation and using it to really get to the bottom of things. It’s not just about fixing the immediate problem – it’s about preventing it from happening again.
Core Principles of Root Cause Analysis
Root Cause Analysis (RCA) isn’t just about fixing what broke. It’s about preventing it from breaking again. The key is to find out why something happened, not just what happened. Imagine it like peeling an onion – layer by layer, you uncover the real problem.
So, what guides this process?
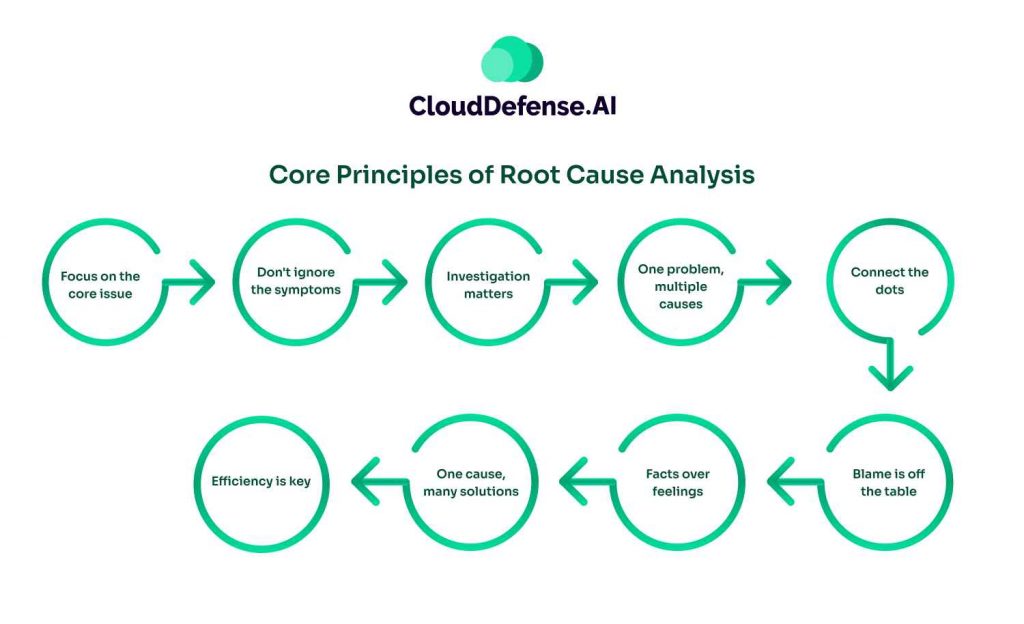
- Focus on the core issue. Don’t just patch up the problem; find its root. This stops it from happening again.
- Don’t ignore the symptoms. While the main goal is the root cause, sometimes fixing a symptom can provide quick relief. It’s like taking a painkiller before the full diagnosis.
- Investigation matters. RCA needs a systematic approach. Think of it as a detective story, where every detail counts.
- One problem, multiple causes. Often, there isn’t just one reason for a problem. It’s usually a mix of things.
- Connect the dots. To truly understand the problem, you need to see how everything links together. A timeline can help here.
- Blame is off the table. Root Cause Analysis is about the problem, not the person. It’s a safe space to learn.
- Facts over feelings. Hunches won’t cut it. You need solid evidence to pinpoint the root cause.
- One cause, many solutions. There might be several ways to fix the root cause. Find the best one.
- Efficiency is key. Fixing the problem should be done in the smartest, cheapest way possible.
Approaching RCA After a Cybersecurity Incident
A cybersecurity incident is a crisis, but it’s also an opportunity to learn and improve. Root Cause Analysis (RCA) is your compass in this situation. Here’s how to approach it:
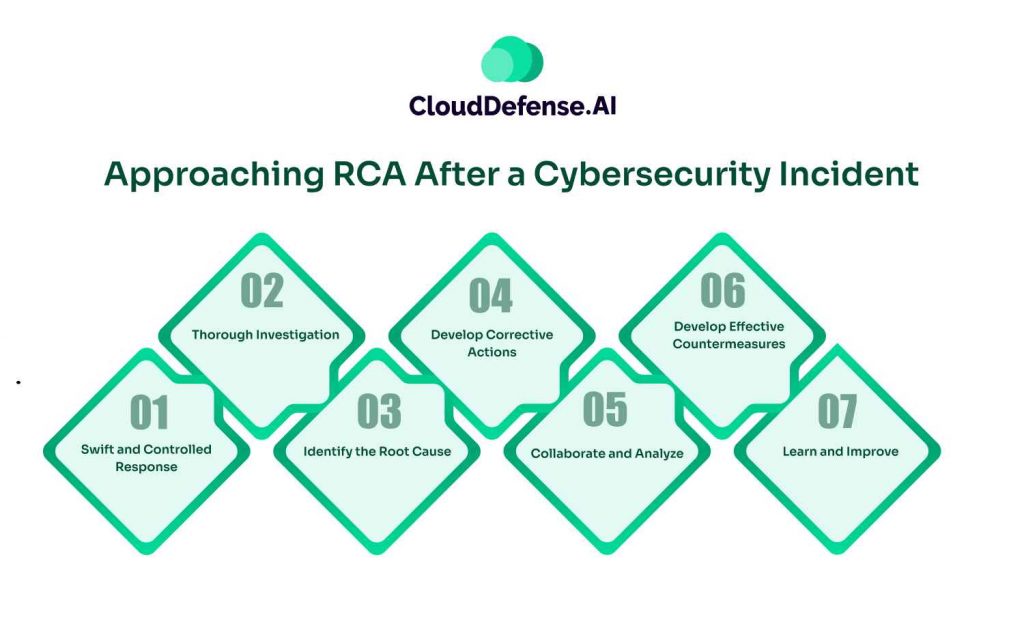
1. Swift and Controlled Response:
- Contain the damage: Prioritize stopping the breach and limiting its spread.
- Gather evidence: Preserve digital artifacts as soon as possible. They’ll be crucial for Root Cause Analysis.
- Form the RCA team: Bring together experts from IT, security, and other relevant departments.
2. Thorough Investigation:
- Timeline creation: Build a clear sequence of events leading to the incident.
- Evidence analysis: Scrutinize logs, network traffic, and system data for clues.
- Vulnerability assessment: Identify weaknesses that the attacker exploited.
- Employee interviews: Understand actions and decisions made before the incident.
3. Identify the Root Cause:
- Ask the “why” questions: Keep digging deeper to uncover the underlying issues.
- Consider multiple causes: Often, a combination of factors leads to a breach.
- Use RCA methodologies: Techniques like the 5 Whys or Fishbone diagram can help.
4. Develop Corrective Actions:
- Prioritize solutions: Focus on addressing the most critical root causes first.
- Implement countermeasures: Strengthen defenses against similar threats.
- Review and update policies: Ensure procedures align with the new threat landscape.
5. Collaborate and Analyze
- Cross-Functional Team: Involve IT, security, and business teams for a holistic view.
- Leverage Tools: Use specialized Root Cause Analysis software or frameworks to structure the analysis.
- Data Analysis: Apply data analytics to uncover patterns and correlations.
6. Develop Effective Countermeasures
- Risk Assessment: Evaluate the potential impact of identified risks.
- Mitigation Strategies: Develop specific actions to address each root cause.
- Implement Controls: Strengthen security measures to prevent recurrence.
7. Learn and Improve
- Knowledge Sharing: Document the RCA process and findings for future reference.
- Continuous Improvement: Integrate lessons learned into security policies and procedures.
- Incident Response Plan: Update the incident response plan based on new insights.
Final Words
While we’ve covered key principles and strategies, it’s important to remember that security is an ongoing process, not a one-time fix. As you implement these ideas, don’t forget to be proactive with your cloud security tools from the get-go. Many breaches could be prevented by properly configuring and actively monitoring these systems.
Remember, cybersecurity isn’t just about fancy tech – it’s about people too. Train your team, develop a security-aware culture, and always stay curious. Keep learning, adapting, and questioning. The bad guys are constantly upping their game, so we need to do the same.
Lastly, don’t go it alone. Collaborate with cloud security enterprises, join security communities, and share knowledge. Together, we stand a better chance of keeping our digital world safe. Stay vigilant!







