What is SLSA?
To answer “What is SLSA?” It can be defined as a security framework to ensure the integrity of software artifacts. Supply-chain Levels of Software Artifacts is a collaborative effort of Google, OpenSSF, and other stakeholders to standardize the protection of the software supply chain.
The framework serves as a checklist of standards and security controls to prevent any cyberattack in the supply chain. The primary priority is to improve the integrity of software components and provide a model for enhancing security capability in the supply chain. Supply-chain Levels for Software Artifact works as an industry-approved guideline that helps developers determine whether the code they are using can be tampered with.
Moreover, it also helps in assessing the trustworthiness of the source code used in the software package. SLSA has been designed for large-scale adoption and developers can easily implement it to ensure the software works at a specific Supply-chain Levels for Software Artifact level.
Unlike other guidelines, it automatically creates verifiable metadata, which in turn assists in implementing policy decisions. This metadata is segregated into different levels where security assurances increase with the SLSA level.
SLSA Levels
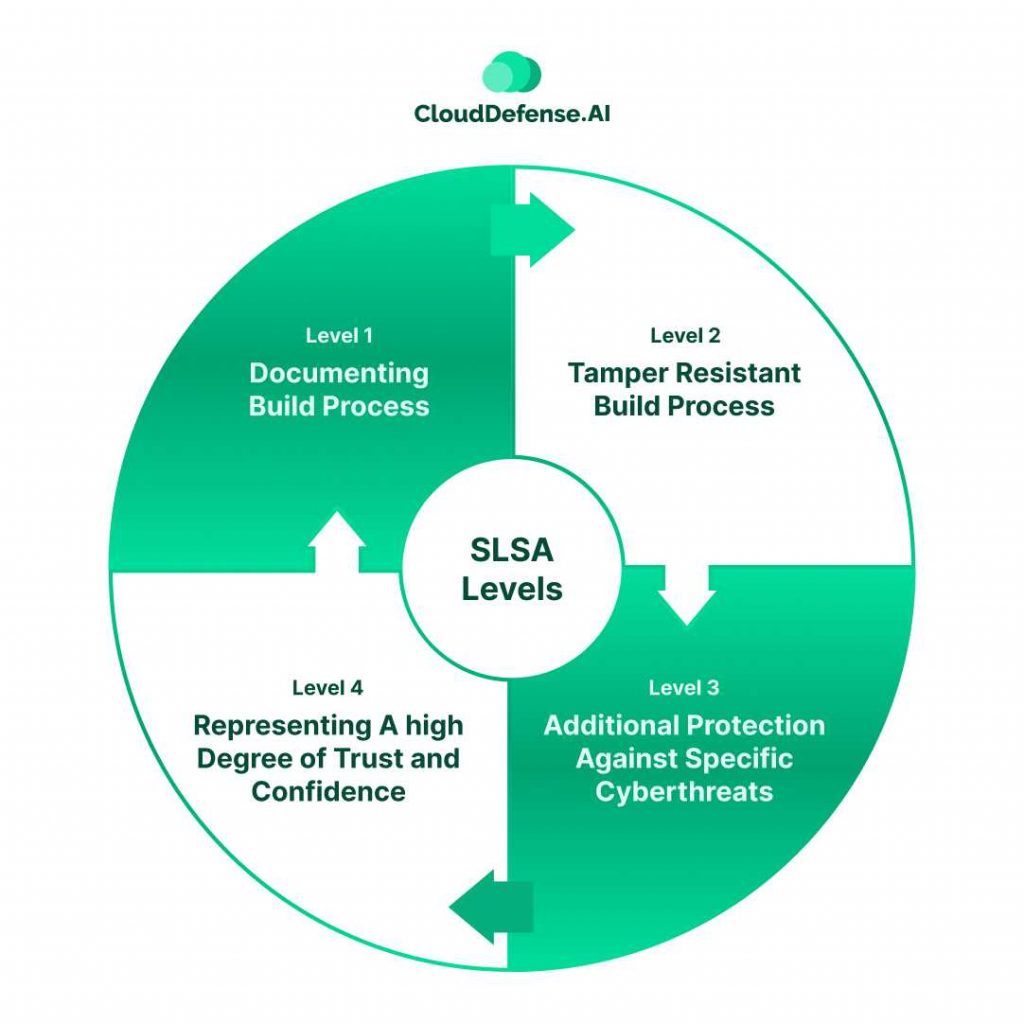
The Supply-chain Levels for Software Artifact requirements are segregated into four levels. Each level in SLSA indicates a specific degree of security posture that contributes to the overall security of the supply chain. Here are all four levels:
Level 1: Documenting Build Process: It acts as the foundation level of the complete framework. It is the level where developers will adopt Supply-chain Levels for Software Artifact and need to fully document the software build environments. Along with all the processes, the metadata of the source and dependencies must be documented. The developers also need to track all the changes in the build environment. The end-user can verify the documents and find security risks.
Level 2: Tamper Resistant Build Process: The Level 2 SLSA indicates the implementation of security measures to achieve the highest degree of tamper resistance in the build process. Achieve Level 2 needs version control and requirements for a hosted build service that will assist in authenticating provenance. The hosted build service will authenticate the software artifacts. It provides consumer information about software origin.
Level 3: Additional Protection Against Specific Cyberthreats: Level 3 in the SLSA framework requires the implementation of certain security controls. To adhere to Level 3, the source and build platform needs to fulfill certain standards that ensure the trustworthiness of provenance and auditing of the source. It assures consumers that software components are highly protected against specific threats.
Level 4: Representing A high Degree of Trust and Confidence: Level 4 in the SLSA framework indicates the software artifacts are completely secured. To achieve this, two certified reviewers need to assess all the changes in the code and components of the software. Another criterion to achieve this Level 4 is the build process needs to be hermetic and reproducible.
Why is SLSA Important for Organizations?

A software supply chain involves the complete process, ranging from the development to the distribution of software. As the complexity of the software supply chain increases, it gets more vulnerable to different threats. Factors like vulnerable components and affected build environments often compromise the supply chain.
SLSA mitigates such issues by providing an industry-approved standard to developers and organizations. It highlights compliance requirements and security measures every developer needs to maintain.
The frameworks assist in finding and mitigating vulnerabilities in the build environment while maintaining the integrity of software artifacts. It inherits an adaptable design so that anyone can adopt it to ensure their software operates at a certain level. Other factors that also make the Supply-chain Levels for Software Artifact framework important are:
- Providing a Plan to Improve Security: Supply-chain Levels for Software Artifact specifies the roadmap that will help organizations traverse from Level 1 to Level 4, improving security posture gradually.
- Incident Response: This framework aids in quick incident response during supply chain attacks by opting for provenance and developing integrity.
- Implementation of Best Practices: Supply-chain Levels for Software Artifact provides the guidelines for best practices that enterprises need to adopt to prevent supply chain attacks.
- Provenance of Artifacts: SLSA provides provenance of software artifacts, which showcases verified metadata of all the software components. Since it provides documentation of all the processes and changes in the build environment, it promotes transparency and trust among stakeholders.
- Risk Mitigation: The software supply chain often uses third-party software components, libraries, and dependencies. Supply-chain Levels for Software Artifact frameworks verify and ensure the integrity of all outside software artifacts to mitigate any risk from vulnerable code.
- Steady Improvement: SLSA frameworks always push towards improving software supply chain practices. It encourages developers to regularly verify all the processes so that organizations can cope with evolving cyber threats and adopt best practices.
SLSA Use Cases

SLSA can be utilized in the software supply chain in different ways, entirely depending upon the organization’s software development processes. Here are some common use cases:
Securing Open Source Software
The SLSA framework is widely adopted by organizations that utilize open-source software components in their software chain. Since open-source software components are vulnerable to attacks, SLSA frameworks are implemented by organizations. Supply-chain Levels for Software Artifact helps maintain the integrity of the open-source software components throughout the supply chain. It provides guidelines for best practices to prevent attacks on the supply chain.
Securing SaaS Vendors
SLSA is often used by SaaS vendors to ensure the security and integrity of their software supply chain. They adopt SLSA frameworks to protect customer data and systems from any vulnerability and maintain integrity. SLSA frameworks are integrated into the SaaS development lifecycle and maintenance to showcase the credibility of the vendor’s security posture. Many organizations look for SLSA certification as a part of their contract with SaaS vendors.
Securing Native Software
Many organizations nowadays use cloud-native software which comprises microservices, APIs, and containers. So it becomes vital for organizations to secure the supply chain of all these components as it will help in maintaining integrity in the application. SLSA framework creates the roadmap on how developers can protect the supply chain containing microservices, containers, and software artifacts.
Securing CI/CD Pipeline
Nowadays, application development is all about automating builds and deployment through the CI/CD pipeline. Any vulnerability in the pipeline can make the whole application prone to attack. Organizations can implement Level 2 of the SLSA framework to generate provenance, document all the artifacts, and integrate integrity throughout the CI/CD pipeline. As a result, it will not only minimize attacks in the supply chain but also ensure that only verified codes are used in production. Importantly, it enables organizations to meet data security compliance and regulatory requirements by protecting sensitive data.
Drawbacks in the SLSA Framework
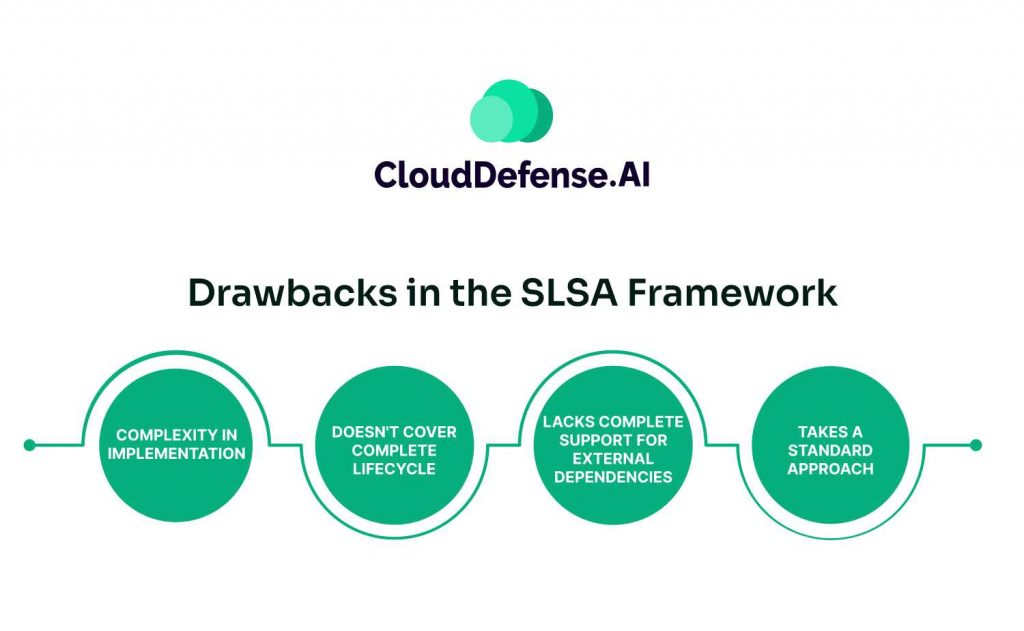
The SLSA Version 1.0 has become a powerful tool for many organizations to prevent attacks on their software supply chain. However, it comes with certain drawbacks:
- Complexity in Implementation: While the SLSA framework is highly beneficial, getting up to SLSA Level 3 or 4 can be complex. Developers will make a lot of modifications in their build environment and CI/CD pipeline to adhere to Supply-chain Levels for Software Artifact guidelines. It not only increases the complexity of the build but also increases the use of resources.
- Doesn’t Cover Complete Lifecycle: The SLSA framework is about maintaining the integrity of the build environment and provenance. However, it doesn’t address the complete lifecycle, which includes vulnerability management and runtime protection.
- Lacks Complete Support for External Dependencies: Supply-chain Levels for Software Artifact doesn’t completely address the integrity of all the external dependencies. The guidelines mitigate many risks but don’t offer complete visibility into all external components.
- Takes a Standard Approach: The SLSA framework is designed to make a standardized approach. However, it doesn’t always meet industry-specific requirements. Sectors like finance can’t fully take advantage of the SLSA framework and would require additional customization to adhere to compliances and regulations.
Starting an SLSA Program
Organizations looking to implement an Supply-chain Levels for Software Artifact program can easily launch it by first achieving SLSA Level 1. Here is the way to do it:
Creating the Setup
The first step is to start a build service or CI/CD pipeline. Having a build service in the program creates the base for higher SLSA levels.
Producing Provenance
The developers have to generate source data in the build environment which will be useful for provenance information. It allows the organization to track all the sources and ensure the integrity of the components in the complex supply chain. Automation has to be introduced in the build pipeline to automatically verify details of all the software artifacts.
Supplying Provenance Information to Consumers
In the pursuit of achieving SLSA Level 1, developers need to define the state of their security posture. Achieving the ideal security posture is a time-consuming process. Thus, developers must focus on the best achievable level for immediate needs. Supplying provenance information to end-users and other stakeholders will help in adhering to Level 1 guidelines. Once SLSA Level 1 is achieved, developers can continue their efforts to achieve higher SLSA Levels.
Final Words
The SLSA framework is gradually becoming a standard for organizations to ensure the integrity and security of software artifacts. Even though Supply-chain Levels for Software Artifact is still an evolving standard, organizations are adopting SLSA to achieve better security posture for their software supply chain. A threat or vulnerability in the external dependence of a library can lead to a serious cyberattack. By adopting SLSA, organizations can ensure the software is securely built and build trust among consumers. Implementation of the SLSA framework has become more important than ever.







