What is Unified Endpoint Management (UEM)?
Unified endpoint management, popularly known as UEM, is a unified solution that is designed to enable security and IT teams to monitor, manage, and secure all remote work devices. From managing desktops, laptops, and smartphones to wearables, UEM offers security to every endpoint connected to the organization’s network.
Organizations opt for UEM as it helps in strengthening the endpoint security and protects all the connected devices using a single consistent solution. One of the primary aims of UEM is to reduce the burden on IT and security teams, who are tasked with managing and securing a huge amount of endpoints.
Usually, a UEM amalgamates the capabilities of traditional mobile management solutions like MDM and MAM with modern tools used for managing on-premises and endpoint devices. This solution also plays a major role in helping IT departments reduce the burden of integrating legacy systems to endpoints, ultimately reducing cost and the chance of any risk.
The Evolution of UEM
Unified endpoint management is the latest solution in the series of mobile security management for securing endpoints in an organization’s network. The UEM solution has come a long way, and it has evolved from MDM, MAM, and EMM.
MDM or mobile device management was first introduced to enable organizations to manage and secure all the company-owned devices in the workplace. It quickly became popular due to its ability to control all the features of a device.
With MDM, the IT administrator can encrypt and provision a device, manage applications, lock devices, and configure network access.
Once smartphones became popular among employees for work purposes and employees refused to provide complete control of their phones, MDM started becoming obsolete. However, smartphones or tablets used for work couldn’t be left unprotected and that is why mobile application management or MAM was introduced.
With this solution, administrators, instead of taking control of the whole device, could control all the apps and data used for corporate work. Through this solution, administrators can control the activity of the user on their personal app so that the corporate data remains secure.
However as the number of applications and activity by users increased on their mobile device, the MAM solution became ineffective. It couldn’t cope with the addition of modern apps. Thus, vendors came up with enterprise mobility management suites or EMM by combining the capability of MDM, MAM, and other related solutions.
With EMM, administrators can protect data like MDM, provide experience like MAM, and control and manage the security of every device used outside of the office.
However, EMM fell short when it came to managing on-site endpoints, and administrators had to use additional tools for the management and security of on-site and off-site devices.
Unified endpoint management or UEM came as the best solution that blended the capabilities of EMM with client management tools to ease out the endpoint management. UEM quickly became popular for its user experience and functionalities. It is also capable of integrating with endpoint security tools to enhance the overall endpoint security.
How UEM Improves Endpoint Security
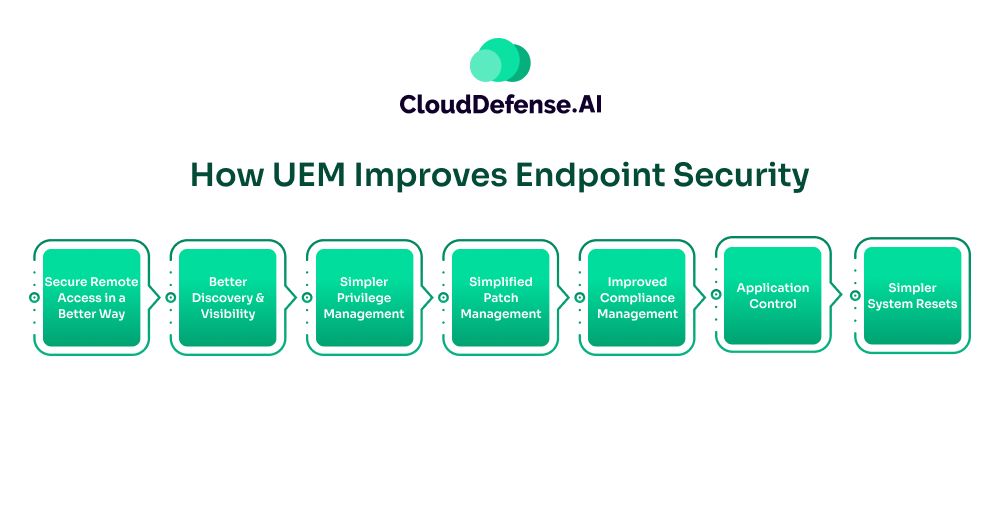
UEM plays a major role in an organization as it eases the management of multiple endpoints and provides a single tool for looking after the security of all of them.
UEM helps in reducing the chances of misconfigurations and inconsistencies in security controls and makes it easy to control everything through a central dashboard. Here are some ways UEM helps in improving endpoint security:
Secure Remote Access in a Better Way
UEM tool enables not only to manage a large number of endpoints efficiently but also to make sure the employees can establish safe access to the organization’s network. With this tool, the IT administrator and security team will have the capability to discard devices that have been infected or don’t adhere to compliance requirements.
Better Discovery and Visibility
By implementing a UEM solution in your IT environment, the IT team gets the opportunity to discover all the endpoints or software connected to the network. Most importantly, the solution provides complete visibility into all the devices in the network, enabling the security team to identify issues when they appear.
Simpler Privilege Management
With this solution, managing access privileges gets easier. The IT administrators can ensure employees can only access the endpoints they have been authorized to use and can only access areas of the network they require.
Simplified Patch Management
Another way UEM improves endpoint security is by simplifying patch management. The security teams can easily update patches across all the endpoints depending on security policies and requirements. These patches make it easier to mitigate vulnerabilities and make endpoints more secure.
Improved Compliance Management
There are certain organizations that need to adhere to strict regulatory requirements like HIPAA, GDPR, and PCI DSS. The organization has to follow some strict policies regarding how customer data is accessed and shared.
UEM makes it easier for the organization to manage sensitive data and monitor access to each endpoint accessed by employees. It also employs policies that prevent employees from accessing sensitive information and areas of the network that they aren’t authorized to use.
Application Control
UEM provides IT administrators the ability to control the application on the endpoints. They can control what type of applications they can use on the endpoint and how many applications they can install on the endpoint. Thus, IT administrators can prevent users from downloading malicious or vulnerable applications that can lead to breaches in the network.
Simpler System Resets
A UEM solution integrates with your IT environment and makes it easier for administrators to reset endpoint devices from the central console. Besides, in case of an emergency, the team also gets the capability to reset any device through the UEM server.
It gives the IT administrator the ability to safeguard the network when a device has been breached or infected by malware.
The Benefits of Unified Endpoint Management
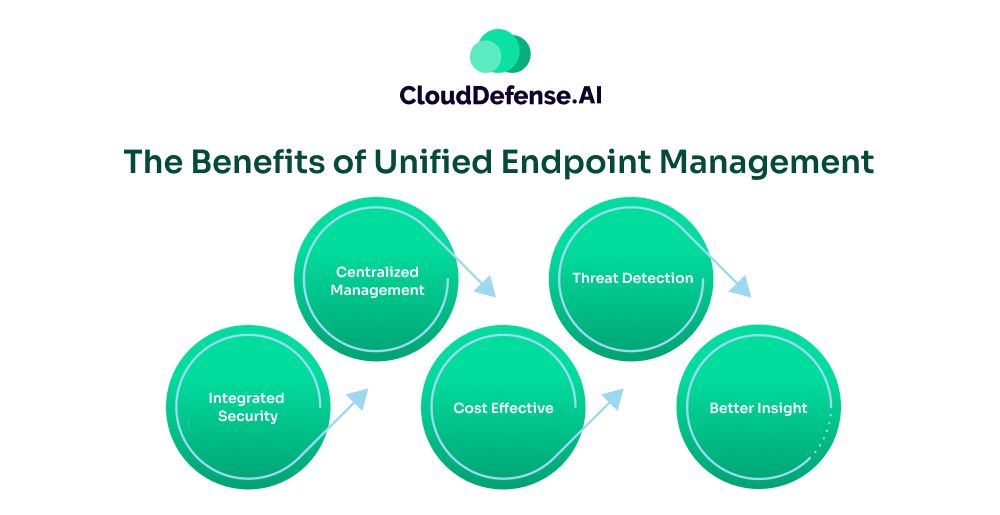
UEM offers a centralized management system that enables organizations to monitor and manage all the endpoints. UEM has been designed in such a way that it benefits organizations in many ways. Here are some primary benefits that UEM has on offer:
Centralized Management
The primary benefit that has made unified endpoint management a necessary choice is its centralized management console.
Organizations working on hybrid and remote working models with numerous endpoints are highly benefited from it because it helps them manage everything through a single console. It not only improves visibility but also makes it easy to monitor all the endpoints.
Threat Detection
Nowadays, endpoints are constantly attacked by cybercriminals as endpoints are the weakest link in the network.
However, UEM solves this issue by constantly monitoring all the activities and identifying any abnormal behavior that indicates that the endpoint has been compromised. Thus, security teams were able to respond to security threats before they could impact the network.
Integrated Security
UEM solution helps the security team to implement compliance policies across the entire network and mitigate any gaps or backdoors that can be utilized by an attacker to breach the network. It plays an instrumental role in solving common issues like non-compliance and poorly matched management associated with endpoints in a network.
Cost Effective
Another reason many organizations prefer UEM tools is that they reduce the cost of operation by helping manage all the endpoints from a single console. By having this solution, you won’t have to maintain multiple standalone tools, ultimately helping in reducing the operation and capital cost needed to manage IT infrastructure.
Better Insight
Since the UEM solution constantly monitors the endpoints, it provides the security team with better insight. It not only enables the organization to discover threats and generate reports but also achieve predictive analysis which ultimately helps the top officials to make data-driven decisions.
What’s the Difference Between UEM and MTD?
Unified endpoint management and mobile threat defense are two vital solutions that help organizations manage a large number of mobile devices connected to the network. Even though the process is similar, their purpose remains different.
UEM centralizes the management of all the endpoints, including mobile devices connected to the network in a single console. At the same time, MTD is designed to detect and protect mobile devices against all kinds of cyber threats.
Another major difference between the UEM and MTD solutions is the approach toward enhancing the overall security of the mobile device. UEM takes a passive approach where it ensures all the endpoints follow the security policies set by the organization for protection.
However, MTD solution works actively to block and mitigate cyber threats that might compromise the mobile device.
Primary Features of Unified Endpoint Management
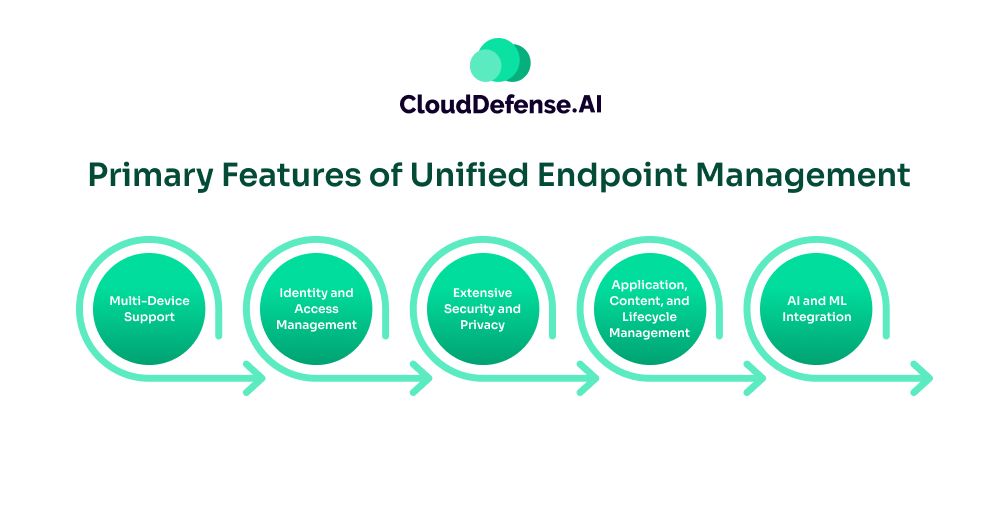
A UEM solution offers an organization a comprehensive set of features that helps them to monitor and manage all the endpoints while keeping them secure. Here are the primary features of UEM:
Multi-Device Support
A UEM solution natively supports a range of devices and vendors, thus ensuring seamless integration. Moreover, a wide variety of support ensures the solution to discover and identify all the types of devices connected to the network.
Identity and Access Management
Another important feature of UEM is identity and access management, which enables the security team to control the devices and users’ access. It controls access depending on password management, encryption, multi-factor authentication, and other policies. UEM also provides a better alternative to passwords for enhanced security.
Extensive Security and Privacy
UEM provides security and IT teams with various resources that help them protect all the critical assets in the network. It leverages threat monitoring and elimination capabilities to improve the overall cybersecurity across the network.
Some advanced UEM solutions also include encryption, containerization, and other tools to ensure extensive security and privacy.
Application, Content, and Lifecycle Management
UEM is highly effective in managing the data access, application, and life cycle of devices. Through a UEM solution, the IT administrators can seamlessly manage and decommission a device depending on the security policies.
Importantly, they can also deploy and update an application upon requirement and manage data access. This feature makes it highly useful for organizations to manage all the contents, applications, and devices securely and ensure the seamless operation of endpoints.
AI and ML Integration
Most modern UEM solutions integrate AI and machine learning to help generate contextual analytics and get deep insight into the security posture.
By leveraging AI and machine learning, it enables the organization to identify new endpoints, secure a connection to the network, assign permission for access, and others. Some UEM vendors have been integrating AI and ML to enhance the overall security posture by a large margin.
Final Words
With remote and work-from-home working models, the need for unified endpoint management is increasing gradually. UEM is increasingly becoming a vital component of every organization’s endpoint security as it enables organizations to manage endpoints and keep them secured at the same time.
With the shift to hybrid and remote working models, enterprises were looking for a plausible solution that would help them manage all endpoints consistently, and UEM came up as the right choice. It helped in eliminating the silos associated with managing multiple tools for all the endpoints and utilizing a centralized console.







