Is your security approach keeping up with today’s threats, or is it stuck in the past? Zero Trust Security vs Perimeter Security is a critical debate as attackers find new ways to bypass traditional defenses.
Perimeter security assumes everything inside the network is safe, but that mindset no longer works against modern cyberattacks. Zero Trust flips the approach, everyone and everything must be verified, no exceptions.
As businesses deal with insider threats, breaches, and evolving attacks, the real question is: which security model actually holds up? Let’s discuss here.
Understanding Perimeter-Based Security
Perimeter-based security focuses on protecting a network’s outer boundary using firewalls, gateways, and other tools to block unauthorized access before threats can enter the internal systems or data.
Perimeter security follows a straightforward idea: protect the outer walls, and everything inside stays safe. This approach has been around for years, relying on firewalls, VPNs, and intrusion detection systems to block threats at the network’s edge. But here’s the problem, attackers don’t play by these rules anymore.
How Perimeter Security Works:
- Defined Network Boundary: Trust is granted based on location – inside the corporate network means safe, outside means dangerous.
- Firewalls & Gateways: These act as primary defense layers, filtering incoming and outgoing traffic.
- VPNs for Remote Access: Extends internal network access to remote employees but assumes they can be trusted once inside.
Where It Falls Short:
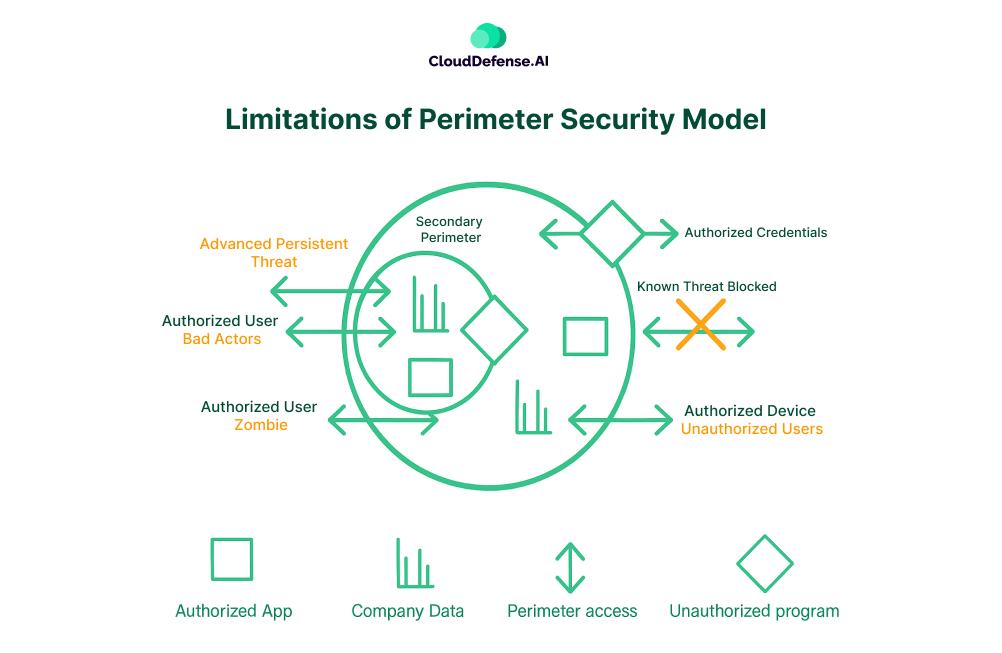
- Trusting everything inside is a mistake: Once an attacker gets in, they can move freely, accessing critical systems without resistance.
- Insider threats go unchecked: Employees, contractors, or compromised accounts can be exploited, and perimeter security does little to stop them.
- Cloud and remote work have changed everything: People work from anywhere, use personal devices, and access cloud services that perimeter security was never designed to protect.
- Attackers don’t need to break in, they log in: Phishing, stolen credentials, and weak VPN security give attackers easy access, bypassing perimeter defenses completely.
For example, let’s imagine an employee clicks on a phishing email, unknowingly handing over their VPN credentials to an attacker. Since perimeter security assumes that anyone inside the network is trustworthy, the attacker logs in without triggering alarms. Once inside, they move laterally, accessing sensitive databases, exfiltrating data, and deploying ransomware – all without resistance.
And it proves one thing: perimeter security alone is no longer enough. Back then, perimeter security worked when companies had a clear, contained network. But today, businesses operate in a completely different environment. The reality? This model is outdated, and relying on it alone is a serious risk.
Understanding Zero Trust Security
Zero Trust Security is a modern security model that assumes no one, inside or outside the network, can be trusted by default. It requires strict verification for every user, device, and request.
As discussed above, perimeter security assumes everything inside the network is safe. But Zero Trust does the opposite, it assumes nothing is safe, no matter where it is. Every user, device, and request is continuously verified before access is granted. This approach eliminates the blind trust that perimeter security relies on and directly addresses its biggest flaws.
What Zero Trust Solves:
- No More Implicit Trust: Just because someone is inside the network doesn’t mean they should have access. Zero Trust verifies every request, regardless of origin.
- Stops Lateral Movement: Even if an attacker gets in, Zero Trust prevents them from moving deeper into the network without additional authentication.
- Protects Against Insider Threats: Employees and contractors don’t get unrestricted access. Their permissions are limited, and their activity is monitored.
- Secures Remote and Cloud Access: Unlike perimeter security, Zero Trust works everywhere such as on-prem, cloud, hybrid environments, and remote work setups.
How It Works:
- Least Privilege Access: Users and devices get only the minimum access needed, nothing more.
- Continuous Authentication: Verifications don’t stop at login. Every action is checked to ensure legitimacy.
- Microsegmentation: The network is divided into smaller, isolated zones, preventing unauthorized access across systems.
- Real-Time Monitoring: Behavioral analytics detect unusual activity, blocking potential threats before they cause damage.
Let’s go back to the phishing attack scenario. The attacker successfully steals an employee’s credentials, but with Zero Trust in place, logging in isn’t that simple. Here, the system detects an unusual login attempt from a new device and location.
Then, Multi-factor authentication (MFA) prompts the user for verification; something the attacker doesn’t have. So, even if the attacker somehow bypasses MFA, strict access controls prevent them from reaching critical systems. Continuous monitoring detects anomalies, flagging the unauthorized behavior before damage is done.
With perimeter security, that attacker would have roamed freely. With Zero Trust, they’re stopped at every step. This isn’t just an upgrade – it’s the only way to defend against modern threats.
Key Differences: Zero Trust Security vs. Perimeter Security
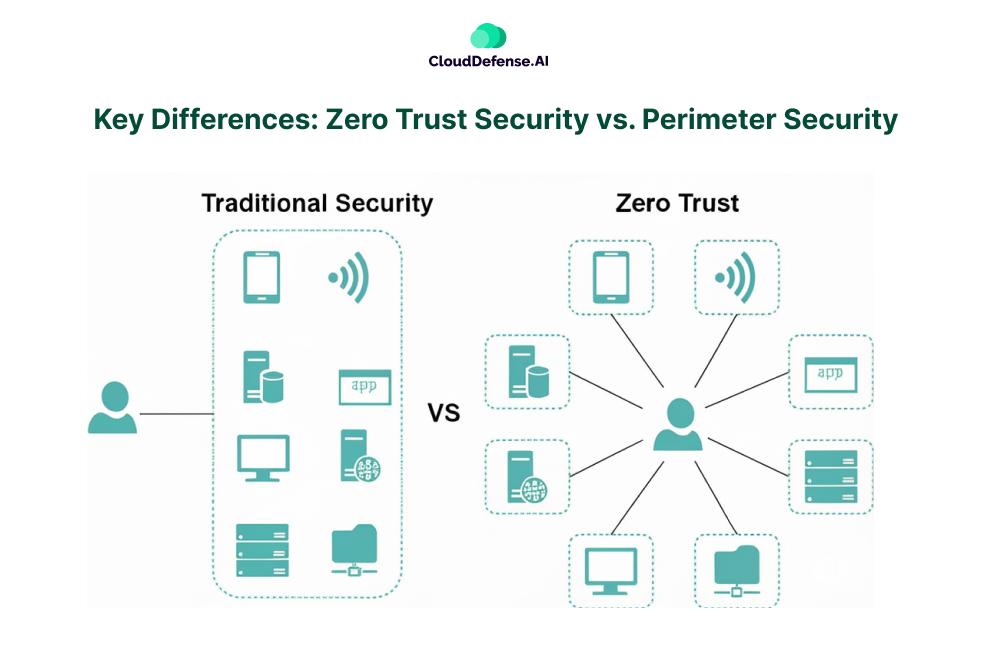
The Zero Trust vs. Perimeter Security debate boils down to one key issue: trust. Perimeter security assumes that once someone is inside the network, they’re safe. Zero Trust assumes no one is safe by default and requires verification at every step. Let’s break it down.
Trust Model – Who Do You Trust?
- Perimeter Security: Operates on an implicit trust model – if a user is inside the corporate network, they are automatically trusted. This means that once a user logs in, they can move around freely.
- Zero Trust Security: Trust is never assumed. Every access request, whether from inside or outside the network, must be continuously verified based on identity, device security, and behavior.
Attackers can easily exploit perimeter security by stealing credentials or finding an entry point. Zero Trust minimizes this risk by requiring ongoing verification rather than a one-time login.
Access Control – Who Gets Access to What?
- Perimeter Security: Users often get broad access once authenticated. If a hacker gains access, they can reach multiple systems.
- Zero Trust Security: Access is strictly controlled using the principle of least privilege (PoLP), meaning users can only access what they need for their job and nothing more.
If an employee’s account is compromised in a Zero Trust setup, the damage is limited because the attacker can’t access everything. In perimeter security, one breach can expose the entire network.
Network Defense Approach – How Are Threats Blocked?
- Perimeter Security: Defends at the network’s edge using firewalls, VPNs, and intrusion detection systems (IDS). Once inside, there’s minimal oversight.
- Zero Trust Security: Focuses on verifying every user and device continuously. Security controls are applied at multiple levels, not just at the perimeter.
Perimeter security is like locking the front door but leaving all the rooms inside open. Zero Trust locks every room and asks for ID every time someone tries to enter.
Lateral Movement – What Happens After a Breach?
- Perimeter Security: Once inside, attackers can move laterally across systems with little resistance.
- Zero Trust Security: Uses micro-segmentation, meaning every system and workload is isolated. If an attacker compromises one area, they can’t easily move to another.
Lateral movement is how ransomware spreads. If one endpoint is compromised in a perimeter-based system, attackers can escalate their access and hit critical infrastructure. Zero Trust prevents this by limiting movement.
Suitability for Cloud & Remote Work – Can It Secure Modern Environments?
- Perimeter Security: Built for on-premise networks where employees worked inside office buildings with corporate-controlled devices.
- Zero Trust Security: Designed for a world where employees work from anywhere, using personal devices, cloud applications, and third-party services.
The shift to cloud and remote work has made perimeter security ineffective. Zero Trust ensures that security follows the user, no matter where they are.
Insider Threat Protection – What Happens When an Employee Goes Rogue?
- Perimeter Security: Assumes employees and contractors can be trusted once inside. Malicious insiders can exploit this trust.
- Zero Trust Security: Treats every user as a potential threat. Even employees must go through authentication and access verification at all times.
Data breaches often come from within. Perimeter security doesn’t monitor trusted users closely, but Zero Trust enforces security controls regardless of who the user is.
Response to Modern Threats – Can It Stop Phishing and Credential Theft?
- Perimeter Security: If an attacker steals a user’s password, they can log in without any extra hurdles.
- Zero Trust Security: Uses multi-factor authentication (MFA) and behavioral analysis to detect suspicious activity. If an attacker logs in from an unusual location or device, access is blocked.
Cybercriminals no longer “hack” in the traditional sense as they simply log in with stolen credentials. Zero Trust ensures that even if passwords are compromised, attackers still can’t get in without additional verification.
Here’s, the brief summary about Zero Trust Security vs. Perimeter Security for your quick understanding:
| Aspect | Perimeter Security | Zero Trust Security |
| Trust Model | Assumes trust once inside the network. | Never assumes trust, every request is verified continuously. |
| Access Control | Broad access once authenticated. | Strict least-privilege access based on identity and device security. |
| Network Defense | Focuses on firewalls, VPNs, and IDS at network boundaries. | Uses identity verification, micro-segmentation, and continuous monitoring. |
| Lateral Movement | Attackers can move freely once inside. | Blocks lateral movement with segmentation and just-in-time access. |
| Cloud & Remote Work | Struggles with modern, decentralized work environments. | Designed for cloud, hybrid, and remote work environments. |
| Insider Threats | Trusts employees and internal users by default. | Enforces continuous authentication and monitoring for all users. |
| Response to Threats | Relies on perimeter defenses that can be bypassed. | Uses MFA, behavioral analysis, and continuous verification to detect and block attacks. |
Zero Trust Security vs. Perimeter Security – Checklist
The following checklist compares Perimeter Security vs. Zero Trust to help you assess where your organization stands. If your security model aligns more with perimeter-based controls, it might be time to rethink your approach.
Now, let’s break it down:
| Security Measure | Perimeter Security | Zero Trust Security |
| Assumes every user and device is a potential threat | No | Yes |
| Enforces least-privilege access (users get only what they need) | No | Yes |
| Requires continuous authentication & verification | No | Yes |
| Uses firewalls & VPNs as primary defense | Yes | No |
| Implements micro-segmentation to limit lateral movement | No | Yes |
| Secures remote work & cloud environments effectively | No | Yes |
| Detects and mitigates insider threats | No | Yes |
| Blocks unauthorized access even if credentials are stolen | No | Yes |
| Monitors user behavior for anomalies | No | Yes |
| Encrypts data at all stages (in transit & at rest) | Yes | Yes |
| Grants broad access once a user is inside the network | Yes | No |
| Prevents ransomware and phishing-based lateral movement | No | Yes |
If your organization leans more towards Perimeter Security, it’s time to rethink your security approach and transition to Zero Trust for better protection against modern threats.
Implementing Zero Trust: How to Make the Shift
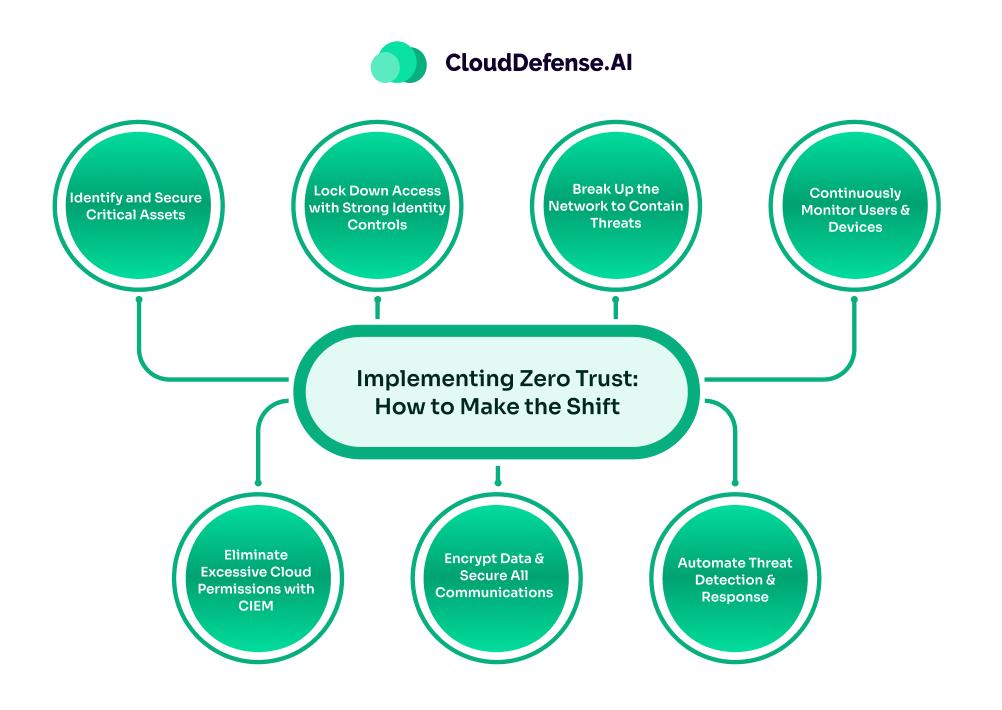
Moving from Perimeter Security to Zero Trust is not simply a technical upgrade, it is a fundamental change in how security works. Instead of assuming that everything inside the network is safe, Zero Trust operates on one simple rule: never trust, always verify. Every request, user, and device is continuously validated before gaining access.
Here’s how to implement Zero Trust effectively:
Identify and Secure Critical Assets
- Start by mapping out all applications, databases, and systems that store sensitive data.
- Define who needs access and why.
- Prioritize securing high-risk assets first like financial records, customer data, or intellectual property.
Lock Down Access with Strong Identity Controls
- Multi-Factor Authentication (MFA) should be non-negotiable for all users.
- Single Sign-On (SSO) makes access easier but must be combined with strict authentication policies.
- Implement least-privilege access users should only have access to what they need, nothing more.
Break Up the Network to Contain Threats
- Micro-segmentation ensures attackers can’t move freely if they get in.
- Internal systems should communicate only when necessary, no broad network access.
- Enforce role-based access controls (RBAC) to limit exposure.
Continuously Monitor Users & Devices
- Track real-time user behavior where sudden changes could mean an attack is happening.
- Validate device security before granting access.
- Use AI-driven security analytics to detect anomalies instantly.
Eliminate Excessive Cloud Permissions with CIEM
- In cloud environments, over-permissioned users are a massive security risk.
- CloudDefense.AI’s CIEM solution helps detect and revoke unnecessary privileges, enforcing the principle of least privilege.
- Automating security policies reduces the chances of human errors and insider threats.
Encrypt Data & Secure All Communications
- Ensure end-to-end encryption for data both in transit and at rest.
- Move beyond traditional VPNs use Zero Trust Network Access (ZTNA) for secure remote access.
- Make encryption a default setting, not an optional feature.
Automate Threat Detection & Response
- Use SIEM tools to analyze security events and detect threats in real time.
- Endpoint Detection and Response (EDR) solutions help identify compromised devices before they become a problem.
- Automate incident response to shut down threats instantly instead of waiting for manual intervention.
To put into perspective, let’s say an employee’s credentials got stolen in a phishing attack. In a perimeter security model, the attacker could move freely inside the network once logged in. But with Zero Trust, every access request triggers multiple checks:
- Is this login from an unusual location or device?
- Does the user behavior match past activity?
- Is the device compliant with security policies?
If anything seems suspicious, access is denied, or additional authentication is required. This prevents unauthorized access, stopping the attack before it starts.
Conclusion
When you look at Zero Trust Security vs. Perimeter Security, it’s pretty clear why so many companies are moving away from perimeter-based models. Perimeter security was built for a time when everything sat inside a controlled office network.
That world doesn’t exist anymore. With cloud, remote work, and evolving threats, Zero Trust gives you the flexibility and protection you actually need that is verifying every user, every device, every time. It’s a smarter way to stay secure, period.







