What is DNS Security?
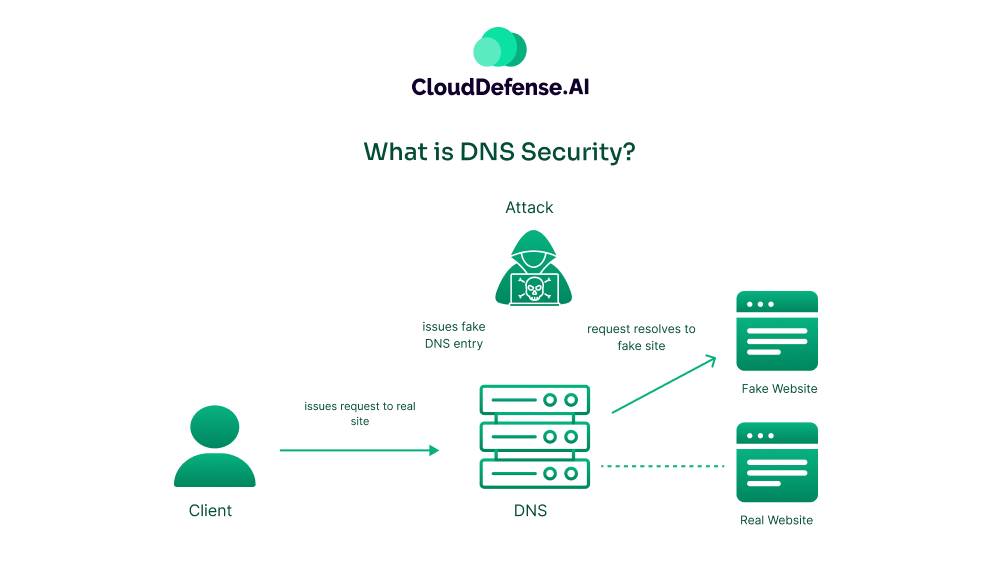
The notion of DNS security refers to the collection of techniques and protocols developed to secure the Domain Name System (DNS), which translates human-readable domain names into machine-readable IP addresses. Essentially, DNS security ensures that when you enter a web address, you reach the intended site and not a malicious one.
Here’s what DNS security covers:
- Secures your online journey: DNS security provides assurance that your web traffic is being sent to legitimate websites.
- Blocks malicious redirects: Prevents hackers from redirecting you to fake or malicious sites.
- Prevents cache poisoning: Protects against attacks in which the hacker injects false data into the DNS cache, e.g. poison the cache and sends to a malicious site.
At its core, DNS security seeks to uphold the integrity, confidentiality, and availability of the DNS Security ecosystem. This refers to preserving the authenticity and intactness of DNS data, encrypting DNS queries for your privacy, and confirming that DNS servers are trustworthy and functional. In other words:
- Authenticates DNS responses: Verifies that the information you receive is from a legitimate source.
- Encrypts DNS queries: Protects your browsing activity from being intercepted or monitored.
This combination of action helps ensure that your environment online is safe and you arrive at the proposed website without disruption.
Why is DNS Security Important?
DNS security is vital because every time your computer communicates with websites or applications, it relies on DNS to convert domain names (like www.example.com) into IP addresses (like 192.168.1.1).
Once the IP address has been defined, routers use it to determine which servers to connect to in order to provide you the content you are requesting. For example, when you enter “www.example.com” into your web browser, DNS will interpret “www.example.com” to the appropriate IP, and your web browser will use that IP to find and load the website.
The DNS protocol was initially built to work securely within networks with boundaries and appropriately authenticated systems. By default, the DNS protocol transmits traffic in clear text, meaning it is not encrypted. This also means that your DNS requests and responses could all be monitored.
Consider this scenario: if a hacker is able to intercept your unencrypted DNS request, they could potentially see every website that you are visiting to make it worse; they could even insert a response to the DNS cache to corrupt the cache. In this situation, they could potentially redirect you from “www.bank.com” to a fake but accurate looking website that is stealing your login username and password.
Also, with modern day computing it is worth noting that with remote workers, branch office workers and workers using laptops and other mobile devices which may connect to DNS servers anywhere, all of which potentially could connect to DNS servers while traversing security zones which use potentially less secure traffic speeds.
Once the hacker has vulnerable systems or applications targeted, they can perform various attacks with the DNS, including the following:
- Intercepting plain text DNS communication: Capturing unencrypted DNS requests to spy on users’ online activities.
- Poisoning the DNS cache: Inserting false information to redirect users to phishing sites. For example, they might trick you into visiting a malicious site that mimics a popular online store to steal credit card information.
- Compromising DNS servers: Taking control of DNS servers to reroute users to harmful destinations.
- Launching DDoS attacks: Overloading DNS servers with traffic to cause service outages.
Without effective DNS security, organizations risk losing access to critical online resources and may face severe disruptions in service. In fact, attackers could also use DNS disruptions as a cover for more dangerous attacks, such as data theft or deploying ransomware.
To protect against these threats, it’s essential for organizations to secure their DNS processes, ensuring both local and remote users are safe from cyber threats.
How does DNS Security Work?
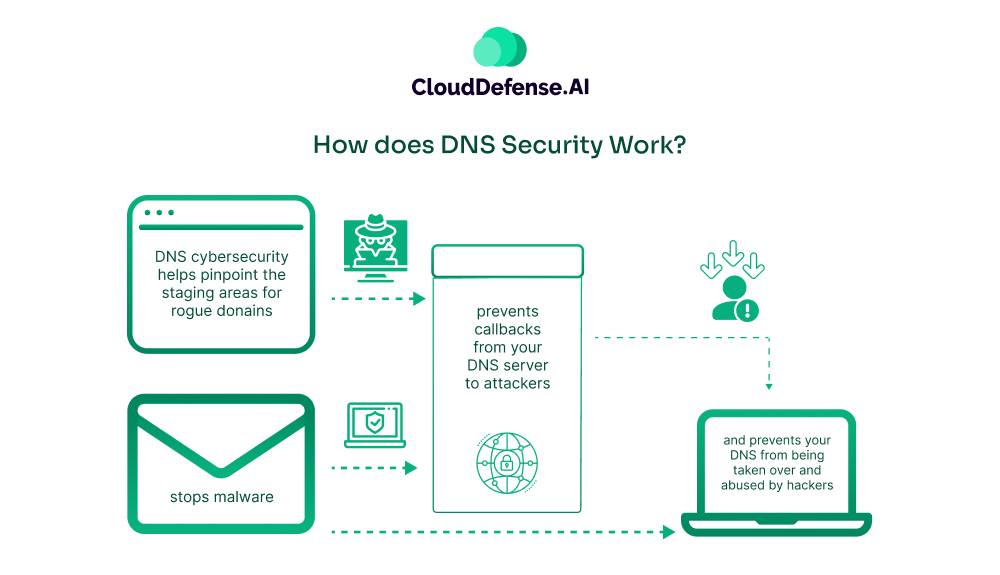
Use this Content in graphics:
- DNS security helps identify rogue domains and their staging areas
- Blocks callbacks from your DNS server to malicious attackers
- Prevents attackers from hijacking your DNS and abusing it for attacks
The security of Domain Name System (DNS) is very important for securing internet activity, as the DNS acts as a mechanism for routing web traffic. Below is a discussion on how DNS security can help you secure your network:
Monitor DNS Queries: Monitoring DNS queries and the associated IP addresses can help detect unusual or suspicious activity. For example, if a large volume of resolve requests are made for unknown or unfamiliar sites, this is an indication that something could be wrong.
Establish Security Policies: You may want to implement comprehensive security policies to help identify and prevent unusual behavior within your DNS service. Such policies may involve initiating queries on behalf of policy instruments that cause queries to be matched differently (i.e. flags) against unknown queries or even blocking queries that are not authorized or from reliable sources.
Identify Rogue Domains: Implementing DNS security will allow for identification and management of threats posed by rogue or malicious sites. Being able to monitor and control DNS traffic is key to avoid traffic to a domain that is associated with malware or phishing schemes.
Avoiding DNS Leaks: It is important to secure the DNS service in a way that prevents querying from un-authorized or unknown sources. This is helpful to mitigate the chances of data leaks or unauthorized access to your network.
Prevent Malware: DNS-layer protection is effective in preventing malware from contacting its command and control servers. In the case that a compromised device attempts to initiate communication to exfiltrate data, receive instructions to carry out additional attacks or update malware, DNS security will prevent this type of communication.
Preventing Denial of Service for Attacks: A DNS “leak” can allow an attacker direct access to contact IPs or addresses of which are flagged to evolve exploits. Ensuring that authorization of network incomes is prevented from threats will supplement your controls.
How DNS is Used in Cyberattacks?
When DNS is a fundamental component of administering internet connections, attackers can misuse DNS in various cyberattacks. These are a few examples of how attackers misuse DNS:
Distributed Denial of Service (DDoS) Attacks
Due to its importance in sustaining the internet, DDoS attacks are carried out against DNS infrastructure. In a DDoS attack, attackers send excessive amounts of network traffic to DNS servers, disrupting DNS servers from responding to legitimate user requests.
For example, a DDoS attack occurred against Dyn that targeted a large botnet made up of Internet-connected cameras in October 2016. The attack resulted in major websites like Amazon, Netflix, and Twitter being taken offline.
DNS DDoS Amplification
DNS servers use UDP, or User Datagram Protocol. With UDP, attackers can fake the source address of their DNS request packets. In an attack, an attacker spoofs a small request, receiving a response that is significantly larger than the initial request was.
This allows attackers to amplify their attack’s impact and overwhelm the targeted server with high rates of traffic that lead to a denial of service – flooding the targeted server with an extremely large amount of unnecessary potential traffic.
Denial of service (DoS) attacks
In addition to network-level DoS attacks, attackers can take advantage of vulnerabilities in application-level DNS server software. Attackers exploit flaws in application code on DNS servers, thus resulting in the inability of the server to serve legitimate requests, and causing service outages.
DNS hijacking attack
The thought process behind this attack is to convince users to connect to an illegitimate domain that looks legitimate. This attack can be successful if an attacker has hijacked a DNS server, or has tampered with the DNS server, and have directed incorrect DNS information (cache poisoning).
For example, users think they are visiting their bank’s banking site, a user is redirected to a phishing site which will steal their login credentials.
DNS tunneling
Cybercriminals can take advantage of the trust in the DNS infrastructure to exfiltrate data out of a network. In this attack, cybercriminals hide stolen or exfiltrated data in DNS request packets and packets decode the request or send it to their own server. Normal internet traffic has free access through a normal firewall, allowing cybercriminals to avoid security checks through common traffic types.
Security Evasion with Random Domain Names (DGA):
Using Domain Generation Algorithms (DGA), attackers can generate thousands of new and random domains. A malicious application running on an infected machine then references a newly generated domain to connect to the attackers Command and Control infrastructure. Often, traditional security mechanisms are relatively slow to recognize domain names generated by DGAs as malicious, leading to them often going undetected.
Common DNS Security Mistakes to Avoid

Neglecting to Secure DNS Servers
Poor security of the DNS servers exposes them to several types of attacks, like DNS hijacking and cache poisoning. Therefore, it is very significant to ensure that the servers are configured with the latest patches for maximum security as well as ensuring that tight access controls are implemented in order to protect them from various types of threats.
Using Unencrypted DNS Queries
Sending digital traffic over the internet using plain text DNS queries makes the contained sensitive information highly susceptible to interception and possible manipulation by malicious actors. To ensure DNS traffic is secure and encrypted, some automated systems (commonly known as robots) can be configured with protocols such as DNS over HTTPS-DoH or Domain Name System over Transport Layer Security-DoT that efficiently protect your data.
Ignoring DNS Logs
The logs generated for the domain name system play a vital role in letting people keep a close eye on different activities taking place in the network. It enables one to identify and view any forthcoming security threat that is most likely to occur. However, one thing to be noticed here is that if these essential logs are not checked regularly, there is a high probability of missing those essential signs that indicate a compromise has already taken place in the system.
For this, there is a great need to go through regular detailed checks on the unusual patterns or suspicious queries that take place in the Domain Name System log files for ensuring comprehensive oversight as well as protection.
Not Implementing DNSSEC
DNS Security Extensions (DNSSEC) can, in different scenarios, play a great role in avoiding such types of attacks by an attacker, like cache poisoning, through efficient validation of DNS responses. Therefore, not implementing this important thing opens up the chance for an attacker to fabricate responses that are targeted and hunt down their domains of interest.
Overlooking Internal DNS Security
A single-minded and absolute focus on securing only external DNS systems and remaining absolutely oblivious to the internal DNS operations that exist within domestic networks could potentially create a situation where attackers find greater opportunities for finding vulnerabilities in them.
Therefore, it becomes critically important that internal DNS systems are also adequately secured and protected; otherwise, they become susceptible to insider threats or malware that has already infiltrated their systems. Such attacks could easily strike them down without any of the personnel or network administrators even noticing the malicious activities occurring.
Failing to Restrict DNS Recursion
DNS, without restrictions on recursion, can introduce serious vulnerabilities. In other words, if it allows unrestricted DNS recursion, then automatically your DNS server becomes a very ideal target for the amplification attacks. Limit recursion to only trusted internal IP addresses to improve the security of your DNS infrastructure. If the DNS recursion is not required by your operational needs, then its complete disabling is recommended on the basis of risk mitigation.
Using Outdated DNS Software
By choosing to run outdated DNS software, organizations inadvertently set a higher exploitation bar for attackers to utilize known vulnerabilities that may exist within such versions of the software. All these serious security risks are going to be better avoided when one has kept one’s DNS software up to date with recent patches and updates.
Neglecting Redundant DNS Infrastructure
Many are found relying on one single DNS server or service, and when that goes down due to an attack or any system failure, everything goes down. Utilize multiple DNS servers or services to ensure redundancy to attain high availability.
Failing to Monitor for DNS Tunneling
DNS tunneling could be utilized to exfiltrate sensitive information or establish a covert communication channel that bypasses normal security controls. Monitoring for potential DNS tunneling activities-indicators such as unusually large DNS query or response sizes, or simply those that deviate from the norm-should be performed in a periodic and comprehensive manner.
Overlooking Security for Remote and Mobile Users
With more staff working from home, DNS security would need to address remote and mobile users. This requires the deployment of VPNs, secure DNS resolvers, and other protection mechanisms to safeguard DNS queries outside of the corporate network.
Final Words
DNS security is one of the most vital, yet forgotten, areas of your whole cybersecurity strategy. If it isn’t implemented correctly, it opens up your network to a series of attacks, including disruptions to services, stolen sensitive data, and huge financial and reputational loss. By addressing common DNS security mistakes, with good countermeasures in place and good vigilance against emerging threats, you can protect your organization from possible risks.
Remember, securing your DNS is not a one-time task; it’s a continuous process. Keep your protocols updated, monitor for unusual activity, and educate your staff about the importance of DNS security. If you take the right attitude, DNS infrastructure can be a strong line of defense against threats.







