What Is a Denial-of-Service (DoS) Attack?
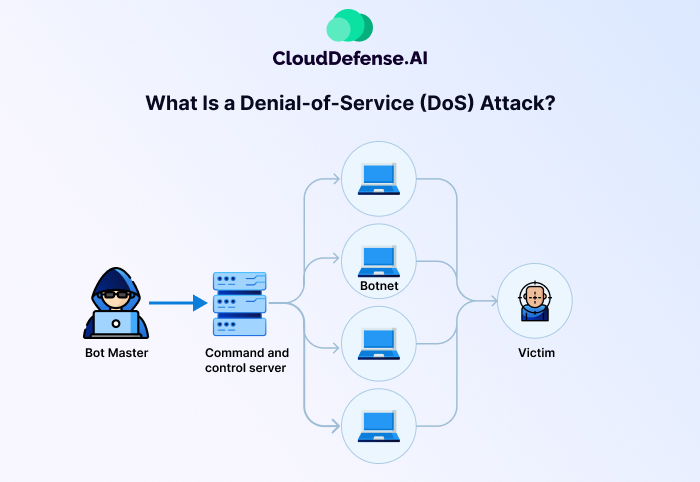
A Denial-of-Service (DoS) attack is a malicious attempt to disrupt the normal functioning of a website, online service, or computer system by overwhelming it with excessive traffic or exploiting vulnerabilities.
This flood of fake requests makes the system unable to handle legitimate users, effectively rendering it inaccessible.
DoS can be thought of as a digital traffic jam where fake traffic prevents real users from reaching their destination. These attacks aim to cripple systems, causing downtime and disrupting operations.
How Do DoS Attacks Work?
DoS attacks achieve their disruptive goals through three main methods: flooding , exploiting vulnerabilities, and buffer overflow attacks. Let’s break them down:
1. Flooding the Target
Attackers overwhelm the target with excessive traffic, akin to a traffic jam that halts movement. This can involve:
- Connection Flooding: Sending endless connection requests, overloading the server’s capacity
- Data Flooding: Bombarding with large data requests, exhausting bandwidth and processing power.
- Amplification Attacks: Exploiting third-party servers to amplify traffic, multiplying the attack’s intensity.
2. Exploiting Vulnerabilities:
By exploiting flaws in the server’s software or security, attackers can:
- Crash the System: Forcing a shutdown and complete denial of service.
- Consume Resources: Overloading the server’s CPU or memory, rendering it unresponsive.
3. Buffer Overflow Attacks
This attack involves overloading a memory buffer, causing the machine to consume all available disk space, memory, or CPU time. The result is often sluggish performance, system crashes, or other disruptive behaviors that lead to denial-of-service.
Types of DoS Attacks
DoS attacks come in many forms, each with unique characteristics designed to disrupt services. Here’s a breakdown of the most common types:
UDP Flood
Attackers inundate the target with massive amounts of User Datagram Protocol (UDP) packets, often sent to random ports. This forces the target to waste resources processing fake requests, rendering legitimate traffic inaccessible.
TCP/IP Connection Exhaustion
This attack exploits the server’s limit on simultaneous connections. By exhausting all available connections, attackers prevent legitimate users from establishing new ones, effectively shutting out access.
ICMP Flood
Also known as a Ping Flood, this involves flooding the target with Internet Control Message Protocol (ICMP) echo requests. The sheer volume of these requests overwhelms the system, making it unreachable.
SYN/ACK Flood
This attack disrupts the TCP handshake process. Attackers send an overwhelming number of incomplete SYN (synchronize) or ACK (acknowledge) packets, tying up resources and blocking legitimate connections.
DNS Amplification
By exploiting vulnerable DNS servers, attackers amplify traffic to the target. Small DNS queries with spoofed source IPs result in large responses directed at the victim, overwhelming their network.
HTTP/HTTPS Flood
In these application-layer attacks, web servers are bombarded with HTTP or HTTPS requests, overloading their ability to respond and causing slowdowns or complete outages.
Slowloris Attack
This low-and-slow tactic involves keeping many server connections open by sending incomplete requests. The server remains tied up, waiting for these requests to complete, leaving no resources for legitimate users.
Teardrop Attack
This method sends fragmented packets with overlapping offset fields, confusing the target’s system during reassembly and causing crashes or unresponsiveness.
NTP Amplification
Exploiting Network Time Protocol (NTP) servers, attackers amplify traffic sent to the target by leveraging small queries that result in disproportionately large responses.
Ping of Death
This older attack involves sending oversized ICMP packets to a target. While modern systems are typically protected, outdated ones may still crash or freeze under this attack.
Application Layer Attacks
Targeting specific applications, these attacks exhaust critical resources like database connections, bandwidth, or server processing power. Examples include SQL injection and Cross-Site Scripting (XSS) attacks.
DoS attacks use both brute force and precision tactics to wreak havoc. Understanding these types can help organizations better prepare defenses against such disruptive threats.
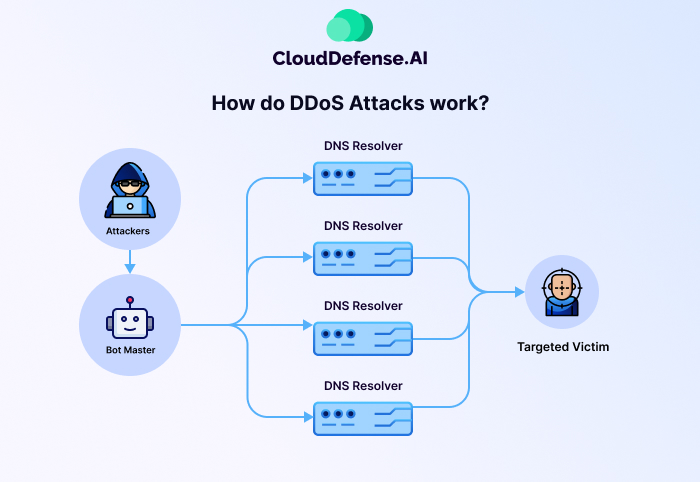
Difference between DoS and DDoS Attack
DDoS attack is also a type of DoS attack but with a crucial distinction: the scale and distribution of the attack. It amplifies the impact by harnessing multiple compromised devices (often called a botnet) to launch a coordinated DoS attack from geographically dispersed locations.
Here’s what makes DDoS attacks particularly challenging:
- Increased Attack Volume: The combined traffic from numerous compromised devices creates a much larger flood, exponentially amplifying the disruption.
- Geographic Dispersion: Tracing the attack source becomes difficult due to the distributed nature of the botnet, making it harder to pinpoint and mitigate.
- Redundancy and Obfuscation: Attackers can leverage different attack methods and constantly change their tactics, making it harder to predict and defend against.
How to investigate if under the DoS attack?
Identifying a DoS attack in real-time can be crucial in minimizing its impact and initiating countermeasures. While specific symptoms might vary depending on the attack type, here are some key signs to watch out for:
Unusual Traffic Patterns:
- Sudden Spikes: A drastic and unexplained increase in website traffic, particularly from unfamiliar locations or IP addresses, is a red flag. Monitor your analytics tools for anomalies.
- Suspicious Traffic Patterns: Look for unusual patterns in traffic flows, like consistent peaks at odd hours or traffic originating from a single device type or geolocation.
- Failed Login Attempts: A surge in failed login attempts could indicate a brute-force attack, potentially part of a broader DoS strategy.
Performance Issues:
- Slow Loading Times: If your website or application experiences sluggishness, delays, or timeouts, it could be due to overwhelmed resources from excessive traffic.
- Frequent Errors and Crashes: Unexplained errors, service outages, or unexpected server crashes might signal attempts to disrupt systems.
- Limited Functionality: Certain features or functionalities becoming unavailable can point towards specific vulnerabilities being exploited.
Network and Server Issues:
- High Resource Utilization: Monitor CPU, memory, and network bandwidth usage. Unexplained spikes exceeding typical levels could indicate malicious activity.
- Connection Timeouts: If clients report trouble connecting or maintaining connections, it might be due to overloaded servers or network capacity exhaustion.
- Security Alerts: Intrusion detection or security information & event management (SIEM) systems might raise alerts regarding suspicious activity or attempted DoS attacks.
How to Prevent DoS Attacks?
In the face of escalating DoS attacks, organizations must adopt an active approach to protect their systems and ensure uninterrupted service availability.
Preventing DoS attacks requires a combination of security practices, continuous monitoring, and a well-prepared response plan. Here’s how to stay ahead of the threat:
- Patch and Update Regularly: Keep operating systems, applications, and firmware up to date. Hackers often exploit known vulnerabilities, and timely updates can close these gaps before they’re exploited.
- Monitor Traffic and Logs: Actively track network traffic and system logs for unusual spikes or error patterns that may signal an attack. Employ cloud-based SIEM solutions to aggregate and analyze data for early detection.
- Limit Attack Surface: Reduce the number of entry points available to attackers. Use solutions like CloudDefense.AI’s CIEM to manage and monitor user access across your cloud environment, minimizing vulnerabilities and exposure.
- Input Validation and Sanitization: Implement input validation techniques to block code injection attacks and other exploits that attackers might leverage to disrupt your systems.
- Secure Authentication and Authorization: Enforce strong authentication protocols, mandate complex passwords, and apply least-privilege access controls. These measures restrict unauthorized access and limit damage if credentials are compromised.
- Regular Security Testing: Conduct periodic vulnerability assessments and penetration testing to uncover and address weaknesses in your infrastructure before attackers exploit them.
- Stay Informed: Stay ahead of emerging threats by keeping up with the latest DoS attack techniques and trends. Adapt your defense strategies accordingly to counter evolving tactics.
- Develop a Response Plan: Prepare for worst-case scenarios with a detailed incident response plan. Outline communication protocols, mitigation strategies, and recovery procedures to ensure swift and effective action during an attack.
A Secure Future Starts with Preparedness
These practices can allow businesses to significantly reduce their vulnerability to DoS attacks and maintain operational continuity even in the face of targeted disruptions. Proactive measures are your best defense against these persistent threats.
Conclusion
DoS attacks remain a significant threat to businesses of all sizes. The key to staying ahead lies in understanding how these attacks work, recognizing the warning signs, and implementing proactive prevention strategies. By taking action early, you can dramatically reduce the risk and impact of these malicious disruptions.
Prevention is always better than cure. Strengthen your network, secure your servers and applications, and maintain vigilant monitoring to respond swiftly to any threats. Partnering with trusted security experts like CloudDefense.AI can make all the difference. With cutting-edge cloud security solutions, CloudDefense.AI ensures your systems remain resilient, and your services uninterrupted, even in the face of attacks.
Don’t wait for an attack—act now! Book a FREE demo with CloudDefense.AI today and experience the future of cloud security firsthand.







