What is a DDoS attack? DDoS Explained
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal functioning of a website, computer, or online service by overwhelming it with a flood of requests from multiple sources.
Unlike a Denial of Service (DoS) attack, which originates from a single source, a DDoS attack leverages a distributed network of compromised devices, often called a botnet. This coordinated assault consumes the target’s resources, making it inaccessible to legitimate users and harder to mitigate due to the varied and widespread origins of the traffic.
How do DDoS Attacks work?
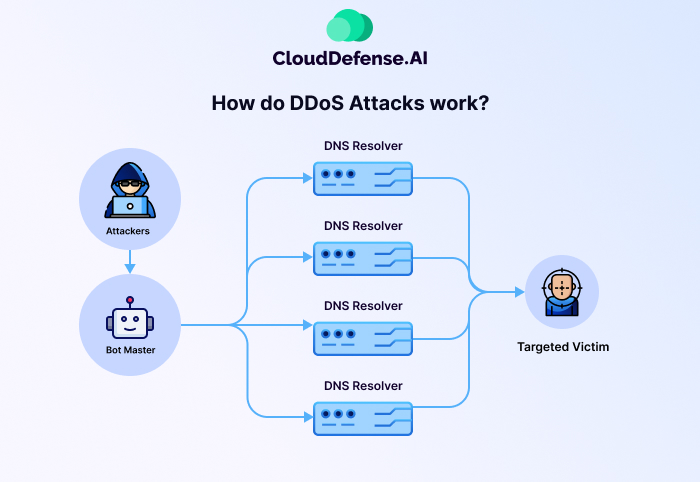
DDoS attacks exploit a fundamental aspect of how online services function: their capacity to handle a certain amount of traffic. Imagine a busy restaurant with a limited number of tables and servers. If more customers than usual come at once, the place might get too crowded and people will have to wait longer.
Similarly, websites and online services have limitations on the number of requests they can process simultaneously. This could be a limit on web application requests, server connections, or even network bandwidth. DDoS attacks essentially weaponize this legitimate functionality by overwhelming the target with a massive influx of traffic originating from multiple sources.
Unlike other cyberattacks that attempt to steal data or breach security systems, DDoS attacks aim to make the target unavailable to genuine users. This can be achieved through various methods, essentially bombarding the target with:
- A massive surge of requests: This overwhelms the server’s capacity to process legitimate traffic, causing it to slow down or crash completely.
- Flooding the network with data: This congestion disrupts the flow of communication, preventing legitimate users from reaching the target.
This overwhelming influx can target various aspects of the target’s infrastructure, including:
- Network bandwidth: A lot of traffic can fill up the network’s channels, stopping real users from getting to the target’s services.
- Computing resources: The overloaded system struggles to keep up with the excessive demands, leading to slowdowns, crashes, and outages.
- Network devices: Routers, switches, and other critical infrastructure components can become overwhelmed, disrupting overall network functionality.
The effects of a successful DDoS attack can be far-reaching. Businesses can suffer significant financial losses due to downtime, reputational damage, and potential legal repercussions. Hacktivists and cybercriminals often use DDoS attacks to disrupt critical infrastructure, extort money, or silence dissenting voices.
Types of DDoS Attacks
| Attack Type | Target Layer | Key Impact | Example |
| Volume-Based Attacks | Layer 3 (Network) | Bandwidth saturation | DNS Amplification |
| Protocol Attacks | Layers 3 & 4 (Network & Transport) | Exhaust infrastructure resources | SYN Flood |
| Application-Layer Attacks | Layer 7 (Application) | Overload application processing | HTTP Flood |
| Degradation-of-Service | Layer 7 (Application) | Gradual decrease in performance | Low-volume traffic spikes |
DDoS (Distributed Denial of Service) attacks target various components of a network, exploiting different weaknesses to disrupt services. These attacks are categorized based on the layers of the OSI model they exploit. Here are the primary types of DDoS attacks:
Volume-Based or Volumetric Attacks
Objective: Overwhelm the target by consuming all available bandwidth.
Volumetric attacks flood a network with massive amounts of traffic, saturating the bandwidth between the target and the internet. This type of attack often leverages amplification techniques, where small requests generate significantly larger responses.
- DNS Amplification Attack: Attackers spoof the target’s IP address and send DNS lookup requests to open DNS servers. The servers respond with amplified DNS record data to the target, overwhelming its resources.
Protocol Attacks
Objective: Exhaust server resources and infrastructure, such as firewalls or load balancers, by exploiting protocol vulnerabilities.
Protocol attacks target weaknesses in Layers 3 (Network) and 4 (Transport) of the OSI model, causing the server to become unresponsive.
- SYN Flood Attack: Attackers send an overwhelming number of TCP handshake requests with spoofed IP addresses. The target server tries to respond to each request, but the handshake remains incomplete, consuming server resources.
Application-Layer Attacks
Objective: Overload the application layer (Layer 7), where user requests are processed, to disrupt normal operations.
Application-layer attacks mimic legitimate traffic, making them harder to detect and mitigate. They often target web applications, APIs, or servers that process HTTP requests.
- HTTP Flood Attack: Attackers send a high volume of HTTP requests, forcing the target’s server to process excessive database queries. This overwhelms the server’s capacity, resulting in slow or failed responses.
Degradation-of-Service Attacks
Objective: Gradually reduce a service’s performance rather than completely taking it offline.
Unlike full-scale DDoS attacks, degradation attacks involve lower volumes of traffic designed to make detection difficult. These attacks subtly impact a service’s accessibility and user experience without triggering immediate alarms.
Understanding the various types of DDoS attacks allows organizations to prepare better defenses and implement tailored response strategies. While these attacks evolve in complexity, identifying the attack vector is the first step to effective mitigation.
Recognizing the Signs of a Potential DDoS Attack
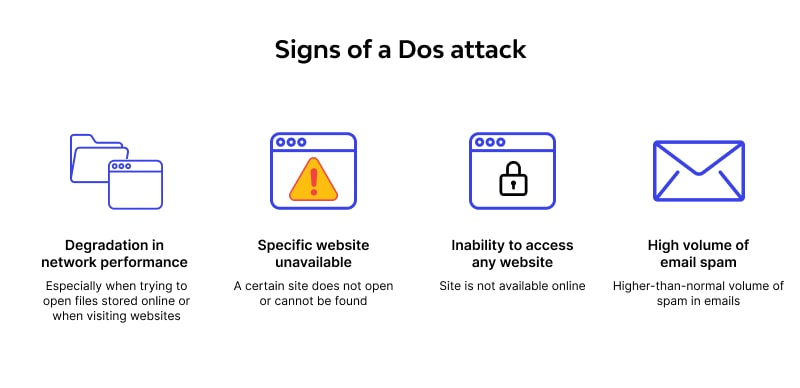
These cyberattacks aim to overwhelm your servers or network, making your services unavailable to legitimate users. Knowing how to recognize the early warning signs of a DDoS attack can save your business from chaos. Here’s how you can spot the red flags:
Sudden Traffic Spikes
If your analytics show an unexpected surge in traffic, then it is a red alert for you. While a successful marketing campaign can draw in new visitors, traffic from unfamiliar or suspicious sources—such as one geographic location or even a single IP address—is a huge red flag.
What to watch for:
- A flood of requests from the same region or network.
- An unusual number of repeated requests to specific parts of your website.
Website Performance Issues
If your site is suddenly slower than usual or pages keep timing out, don’t dismiss it as “just the internet acting up.” DDoS attacks flood your servers with traffic to deliberately slow or halt your service.
Symptoms include:
- Slow-loading pages even with a good internet connection.
- Complete service outages that make your website or applications inaccessible.
Strained Server Resources
Behind every website, your servers are working hard to handle requests. During a DDoS attack, those servers can become overloaded, leaving little capacity for legitimate users.
Look out for:
- CPU or memory spikes—your server resources being maxed out for no apparent reason.
- Log anomalies—patterns like repeated access requests or failed attempts to connect, which may indicate malicious activity.
Network Disruptions
A DDoS attack doesn’t just affect your website—it can also target your network infrastructure, disrupting all connected services.
Signs to monitor:
- Frequent network slowdowns or instability.
- Difficulty accessing external resources or communicating across your own network.
Alerts from Security Providers
If you use hosting services or security monitoring tools, they may detect unusual traffic patterns or malicious activity and notify you.
- Pro tip: Don’t ignore alerts from your security provider or hosting platform. They might see things you can’t, like abnormal DNS traffic or protocol-specific threats.
Why Early Detection can be a Gamechanger?
The longer a DDoS attack goes unnoticed, the more damage it can cause. Beyond frustrating your users, these attacks can harm your reputation, disrupt your operations, and even lead to financial losses. That’s why it’s essential to stay vigilant and address suspicious activity immediately.
By knowing what to look for—whether it’s unusual traffic, sluggish performance, or server overload—you can take action to protect your business before the damage becomes irreversible. And remember, you don’t have to do it alone.
Partnering with security experts, such as CloudDefense.AI, can help you detect and stop these attacks with modern, AI-powered cloud security solutions. Staying prepared means staying online. Don’t let cybercriminals shut you down—stay watchful, stay secure!
How to Defend Yourself from DDoS Attacks?
DDoS attacks are a serious threat to businesses, disrupting services and damaging trust. Staying prepared with proactive defenses is essential. Here’s how to protect your organization effectively
Implement DDoS Mitigation Solutions
Investing in specialized DDoS mitigation services is one of the most effective ways to protect your systems. These services can:
- Filter malicious traffic to ensure legitimate requests are prioritized.
- Absorb attack surges without compromising service availability.
Working with a trusted security provider ensures your systems remain resilient during an attack.
Use Content Delivery Networks (CDNs)
CDNs improve your website’s performance by distributing its content across a global network of servers. They also act as a barrier against DDoS attacks by:
- Preventing attackers from targeting a single server location.
- Detecting and filtering suspicious traffic before it reaches your site.
With a CDN in place, your infrastructure is better equipped to handle high traffic volumes.
Enable Rate Limiting
Rate limiting helps control the number of requests coming from a single IP address within a given timeframe. This prevents attackers from:
- Flooding your servers with excessive traffic.
- Exploiting botnets to overwhelm your system.
Implementing rate limits ensures a fair distribution of resources and adds an additional layer of security.
Deploy Web Application Firewalls (WAFs)
A WAF is a powerful tool for detecting and blocking malicious traffic targeting specific vulnerabilities in your web applications. It’s especially effective against:
- Application-layer DDoS attacks (Layer 7) that exploit HTTP requests to overwhelm your servers.
With a WAF, you can protect critical applications and maintain performance even under attack.
Conduct Regular Security Audits and Vulnerability Assessments
Cybersecurity is a continuous process. Regular assessments can:
- Identify and fix potential weaknesses in your infrastructure before attackers exploit them.
- Help you stay compliant with security standards.
Using modern security solutions like CloudDefense.AI, you can take a proactive stance in fortifying your systems against evolving threats.
Develop a Robust Incident Response Plan
When a DDoS attack occurs, a well-structured incident response plan is essential. This plan should include:
- Clear communication protocols for notifying internal teams and stakeholders.
- Resource allocation strategies to maintain operations during an attack.
- Recovery procedures to quickly restore normal service.
A prepared team can minimize downtime and reduce the impact of an attack.
Stay Informed and Educated
Knowledge is a critical defense against cyber threats. Ensure your team:
- Stays updated on the latest DDoS trends and attack techniques.
- Learns to recognize early warning signs of potential threats.
- Follows best cybersecurity practices to avoid accidental vulnerabilities.
By building a culture of awareness, you empower your team to respond effectively to any challenge
Conclusion
DDoS attacks remain one of the persistent threats today, and staying vigilant, continuously evaluating your security posture, and implementing robust mitigation strategies are the only ways out. That said, CloudDefense.AI is a leading provider of comprehensive cloud protection solutions, empowering businesses to combat these sophisticated attacks and ensure uninterrupted operation.
Our multi-layered approach encompasses advanced threat detection, real-time monitoring, and neutralize attack vectors before they can be exploited. Book a free demo with CloudDefense.AI today and witness the top-notch capabilities of our comprehensive cloud security solutions.







