What is Hacktivism?
Hacktivism is the fusion of hacking and activism, where individuals or groups leverage computer technology to advocate for political, social, or ideological causes. This digital form of protest typically targets governments, corporations, or other significant institutions to highlight issues, challenge opposing viewpoints, or push for reform. While the motivations are often rooted in advocacy, the methods and legality of hacktivism can vary widely.
At its core, hacktivism uses hacking techniques not for personal gain but to promote or oppose particular beliefs. For example, hacktivists may aim to raise awareness about internet freedom, environmental issues, or social justice. However, while some activities remain lawful, such as organizing online campaigns or releasing information to the public, others can cross into cybercrime territory.
How Hacktivism Works?
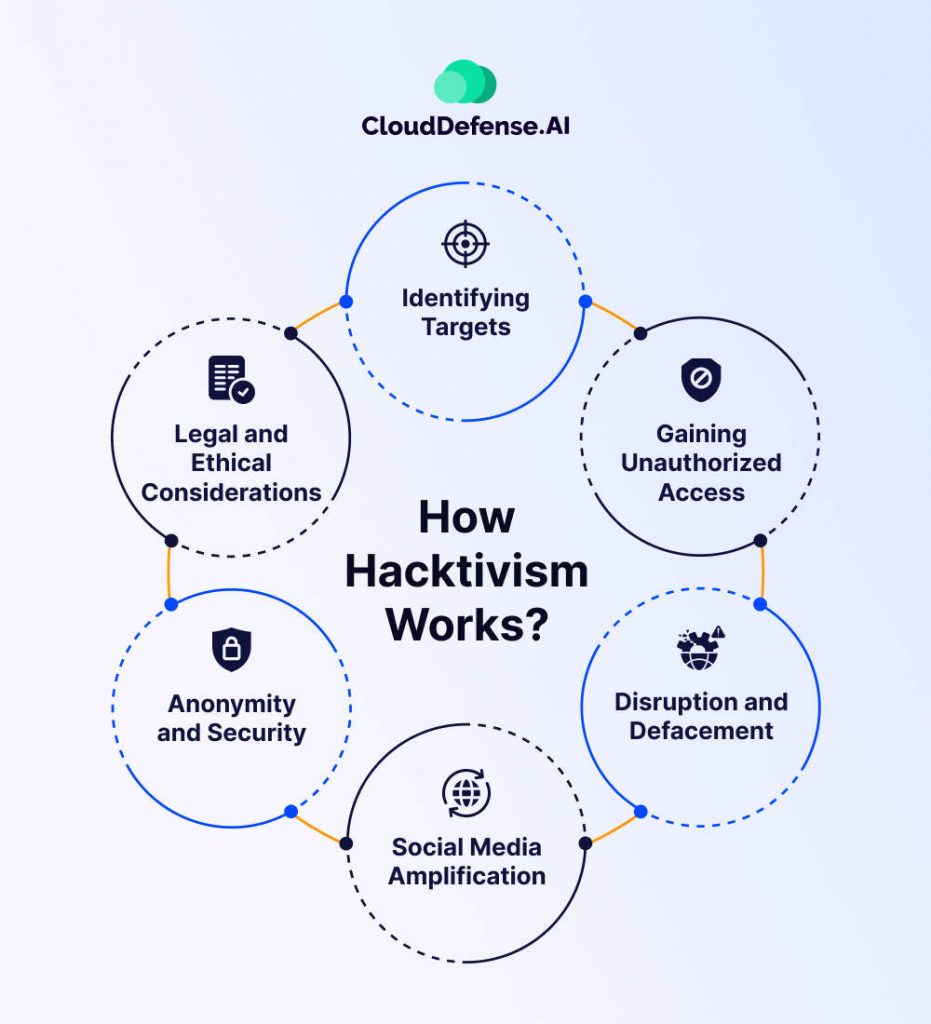
Hacktivism operates at the intersection of hacking techniques and activist goals, using digital tools to promote or oppose specific causes. Hacktivists leverage their technical expertise to make bold statements, disrupt operations, or expose wrongdoing, often targeting governments, corporations, or institutions they believe undermine their values. The ultimate aim is to drive social, political, or ideological change.
Reconnaissance and Target Identification
Before launching an attack, hacktivists conduct extensive research to identify vulnerabilities in their target’s digital infrastructure. This involves:
- Scanning Networks: Using tools like Nmap or Wireshark to map out networks and detect open ports or misconfigured servers.
- Gathering Public Information: Leveraging open-source intelligence (OSINT) through platforms like Shodan or online repositories to gather publicly available information about the target.
Exploitation of Vulnerabilities
Once a target is identified, hacktivists exploit weaknesses in systems or applications. Common methods include:
- SQL Injection: Inserting malicious SQL code into a website’s input fields to extract sensitive data.
- Phishing: Creating fake emails or websites to trick employees into revealing credentials.
- Exploiting Unpatched Software: Targeting outdated systems with known vulnerabilities using tools like Metasploit.
Execution of Cyber Attacks
Let’s check out some of the ways the cyber attacks are executed:
1. Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
Hacktivists flood a target’s server or network with excessive traffic, overwhelming it and rendering services inaccessible. They achieve this by:
- Using botnets: Networks of compromised devices controlled remotely to send massive requests simultaneously.
- Using tools like LOIC (Low Orbit Ion Cannon) or HOIC (High Orbit Ion Cannon) to automate attack traffic.
2. Website Defacement
Hacktivists gain access to a web server and modify its content to display their messages. This often involves:
- Exploiting web server vulnerabilities (e.g., weak admin credentials).
- Replacing HTML files or injecting malicious scripts into web pages.
3. Data Breaches and Leaks
Hacktivists steal sensitive data from databases and leak it to expose wrongdoing. Techniques include:
- Privilege Escalation: Gaining administrative access to extract critical data.
- Man-in-the-Middle Attacks: Intercepting communications to access sensitive information.
4. Ransomware Deployment
Some hacktivists use ransomware to lock systems and demand action instead of payment, such as public acknowledgment of a specific cause.
Dissemination and Amplification
Once an attack is executed, hacktivists ensure their message is widely disseminated:
- Social Media Campaigns: Platforms like Twitter and Reddit are used to amplify their actions and gather support.
- Dark Web Forums: Hacktivists often share details of their exploits anonymously on platforms like Tor to avoid detection.
- Leaking Platforms: Data may be uploaded to sites like Pastebin or WikiLeaks for public access.
Counter-Censorship Measures
Hacktivists bypass restrictions to ensure their actions and messages are accessible, employing techniques like:
- VPNs and Proxies: Masking their identity and accessing censored content.
- Encryption Tools: Securing communications to evade detection by authorities.
- Anonymity Networks: Using services like Tor to remain untraceable.
Tools and Technologies Commonly Used
- Kali Linux: A popular operating system for ethical hacking and penetration testing.
- Burp Suite: Used for web application security testing.
- Hydra: For brute-forcing login credentials.
- Maltego: For OSINT and mapping relationships between data.
Hacktivism is polarizing, with its ethical implications depending on perspective. While some view it as a legitimate form of protest against injustice, others criticize its potential to cause collateral damage. For instance, a DDoS attack on a government website may disrupt services for ordinary citizens, raising concerns about the harm caused to innocent parties.
Types of Hacktivism
Each type of hacktivism applies different methods to achieve its objectives. Whether it’s raising awareness, disrupting operations, or advocating for social and political change. These tactics showcase the diverse strategies employed by hacktivists to challenge authority, promote transparency, and advance their causes
| Type | Definition |
| Website Defacement | This involves altering the appearance of a website to convey a political message or protest. It is a form of digital graffiti, drawing attention to the hacktivist’s cause. |
| DoS Attacks | In a DoS attack, the website’s server is overwhelmed with traffic, rendering it inaccessible to users. This disrupts operations and brings attention to the underlying issues. |
| Data Breaches | Hacktivists infiltrate systems to access and expose confidential information, often aiming to reveal hidden secrets or misconduct, functioning as digital whistleblowers. |
| Redirection | Hacktivists manipulate website traffic to redirect users to sites that highlight their advocated issues, amplifying their message and reaching a broader audience. |
| Anonymous Blogging | Through anonymous blogging, hacktivists provide a platform to share views and raise awareness about social or political issues without revealing their identities. |
| Doxing | This involves publicly exposing private information about individuals or organizations to harm their reputation or advance a cause. |
| Geobombing | Geobombing targets geographical locations to create visual impact, often done by manipulating mapping services or changing place names to convey a specific message. |
| Website Mirroring | When a website is censored, hacktivists may create copies under different URLs to ensure the content remains accessible to the public. |
| Code Alteration | Changing website code allows hacktivists to display messages or errors to visitors, altering the public perception of an organization or entity. This can involve gaining administrator credentials through various means like phishing or keylogging. |
Who Do Hacktivists Target?
Hacktivists typically target individuals, organizations, or institutions perceived as oppressive, corrupt, or unjust. This may include governments, corporations, law enforcement agencies, or individuals in positions of power who are seen as violating principles of democracy, freedom of speech, human rights, or environmental sustainability.
Targets can vary widely, from political figures advocating policies deemed harmful to marginalized communities, to corporations engaged in unethical practices or environmental destruction. Regardless of the motives behind their actions, hacktivists aim to hold these entities accountable and raise awareness about pressing social and political issues.
Hackers vs Hacktivists
Often confused to be the same concept, there is a lot of difference between a hacker and a hacktivist. Here’s a table outlining the differences between hackers and hacktivists. The table provides a clear comparison between hackers, who may operate for various motives including personal gain, and hacktivists, who are primarily driven by political or social causes.
| Aspect | Hackers | Hacktivists |
| Motivation | Personal gain, curiosity, challenge | Political or social causes, activism |
| Ethical Stance | Varied: White hat (ethical), black hat (malicious), gray hat (in-between) | Primarily gray hat (unsanctioned, but often with noble intentions) |
| Skill Set | Proficient in computer systems, programming | Proficient in computer systems, programming |
| Activities | Finding and fixing vulnerabilities (white hat), exploiting vulnerabilities for gain (black hat) | Unauthorized access to systems, disrupting operations, leaking information |
| Relationship with Organizations | White hat hackers may work with organizations to improve security | Often in conflict with organizations, targeting those perceived as oppressive or unjust |
| Legal Status | White hat activities legal, black hat activities illegal | Operate in a gray area of legality, involving unauthorized access which can be illegal |
| Focus | Technical expertise, system security | Social or political activism, advocacy |
The History of Hacktivism
Hacktivism, the fusion of hacking and activism, has a rich and evolving history rooted in the early days of digital networks. This unconventional form of protest has challenged power structures, amplified social movements, and raised critical debates about ethics and legality.
The Foundations: Phreaking and Early Digital Activism (1980s)
The origins of hacktivism trace back to the 1980s, a time when the concept of “phreaking” emerged. Phreakers manipulated telephone networks to make free calls, showcasing an early blend of technical expertise and rebellion against corporate control. While not formally termed hacktivism, these actions laid the groundwork for later movements.
In 1996, the term “hacktivism” was officially coined by Omega, a member of the hacking collective Cult of the Dead Cow. This marked the beginning of a new era where hacking techniques were explicitly tied to activism.
The Growth of Hacktivism: The Internet Revolution (1990s)
The 1990s saw the rise of personal computers and the internet, providing a fertile ground for hacktivist activities. Digital platforms became a new battleground for protest against societal issues.
One of the earliest notable examples occurred in 1994, when the Zippies—a countercultural group—launched an attack against the UK government. This was in opposition to proposed laws restricting open-air raves, demonstrating how hacktivists could leverage technology to voice dissent.
The Rise of Organized Groups: Diversification in the 2000s
The 2000s marked a significant shift in hacktivism with the emergence of highly organized groups such as Anonymous and LulzSec. These collectives carried out sophisticated attacks on corporations, governments, and institutions they deemed unethical or oppressive.
Key events from this era include:
- Fine Gael Website Attack (2011): Anonymous defaced the website of the Irish political party, criticizing their policies and stance.
- Sony Data Breaches: LulzSec exposed vulnerabilities in Sony’s systems, leaking sensitive data and drawing attention to corporate negligence in cybersecurity.
Hacktivism during this time became more than just a form of protest—it was a tool to expose corruption, promote transparency, and challenge authority.
Hacktivism as a Catalyst for Global Movements (2010s)
In the 2010s, hacktivism played a pivotal role in global movements, leveraging technology to combat censorship, promote communication, and amplify grassroots activism.
Notable contributions include:
- The Arab Spring: Hacktivists supported protestors by bypassing government-imposed internet restrictions, enabling communication and coordination.
- Occupy Movement: Hacktivists used digital platforms to amplify the movement’s message, targeting corporate and financial institutions.
These events showcased the potential of hacktivism as a force for societal change, highlighting its dual role as both a disruptive and empowering tool.
Famous Examples of Hacktivism Events
Numerous notable hacktivism events have captured global attention and sparked intense debate. From targeting corporations and government agencies to exposing sensitive information and supporting social movements, hacktivists have used their digital skills to challenge authority and advocate for change. Here are some famous examples of hacktivism
Operation Payback (2010):
Operated by the hacktivist group Anonymous, Operation Payback was a series of retaliatory attacks against major organizations involved in anti-piracy operations. The operation gained significant attention when Anonymous targeted companies that withdrew support from WikiLeaks, demonstrating the group’s solidarity with the whistleblower platform.
Arab Spring (2010-2012):
The Arab Spring was a wave of anti-government protests, uprisings, and armed rebellions that swept across much of the Arab world. Hacktivists played a major role in this movement, using their skills to circumvent government censorship, disseminate information, and organize protests. Platforms like social media and online forums became crucial tools for coordination and mobilization.
Hacking Team Exposure (2015):
In 2015, a yet-unidentified hacktivist leaked 400 gigabytes of data from Hacking Team, an Italian company specializing in intrusion and surveillance technologies. The leaked data exposed the Hacking Team’s controversial clientele, which included oppressive governments known for human rights abuses. This event raised ethical questions about the role of surveillance technology in facilitating authoritarianism.
The Ashley Madison Data Breach (2015):
The Impact Team, a group of hacktivists, breached the systems of Ashley Madison, a dating website catering to individuals seeking extramarital affairs. The group leaked user data online, exposing the identities and personal information of millions of users. While the breach was illegal and caused harm to individuals, The Impact Team justified its actions by criticizing Ashley Madison’s business practices and ethical standards.
Panama Papers (2016)
In one of the largest data leaks in history, an anonymous hacktivist leaked over 11.5 million documents from the Panamanian law firm Mossack Fonseca. The leaked documents, known as the Panama Papers, revealed how wealthy individuals and powerful figures worldwide used offshore firms to evade taxes and conceal illicit wealth. The event shed light on systemic corruption and sparked investigations and reforms in numerous countries.
7 Tips for Preventing Hacktivism
Preventing hacktivism requires a number of steps that include technical, legal, and ethical strategies. Here are seven tips for you on how you as an organization can mitigate the risks associated with hacktivism
Tip 1 – Prioritize Cybersecurity Measures: Invest in strong cybersecurity practices, including regular system updates, encryption protocols, intrusion detection systems, and firewalls. These measures form the foundation of defense against hacktivist attacks.
Tip 2 – Educate Employees: Conduct regular cybersecurity training sessions to educate staff about phishing attempts, safe online practices, and the importance of vigilance in preventing security breaches caused by human error.
Tip 3 – Enforce Legal Consequences: Advocate for strict laws and regulations against unauthorized hacking activities, ensuring that legal repercussions serve as a deterrent to potential hacktivists.
Tip 4 – Promote International Cooperation: Create collaboration and shared standards among countries to effectively address cross-border cyber threats, recognizing that hacktivism often transcends geographical boundaries.
Tip 5 – Operate Ethically and Transparently: Uphold ethical standards and transparency in organizational practices, addressing potential grievances and respecting privacy rights to mitigate the likelihood of becoming a target for hacktivist groups.
Tip 6 – Implement Additional Security Measures:
- Conduct Regular Vulnerability Assessments: Identify and address potential weaknesses in infrastructure security through routine vulnerability assessments.
- Deploy Multifactor Authentication: Enhance login security by implementing multifactor authentication systems to protect against compromised credentials.
- Utilize Security Software: Deploy strong antivirus software and other security tools to provide an additional layer of protection against cyber threats.
Tip 7 – Establish Response Procedures: Develop and support procedures for responding to data breaches, ensuring that staff are equipped to react swiftly and effectively in the event of a security incident.
Hacktivism is an illegal act and must be dealt with strongly, keeping aside whether it is done for a noble cause or not. By implementing strong cybersecurity measures, creating legal frameworks, promoting ethical practices, and educating stakeholders, organizations can work on strengthening their defenses against hacktivism.







