What is API Security? API Security Defined
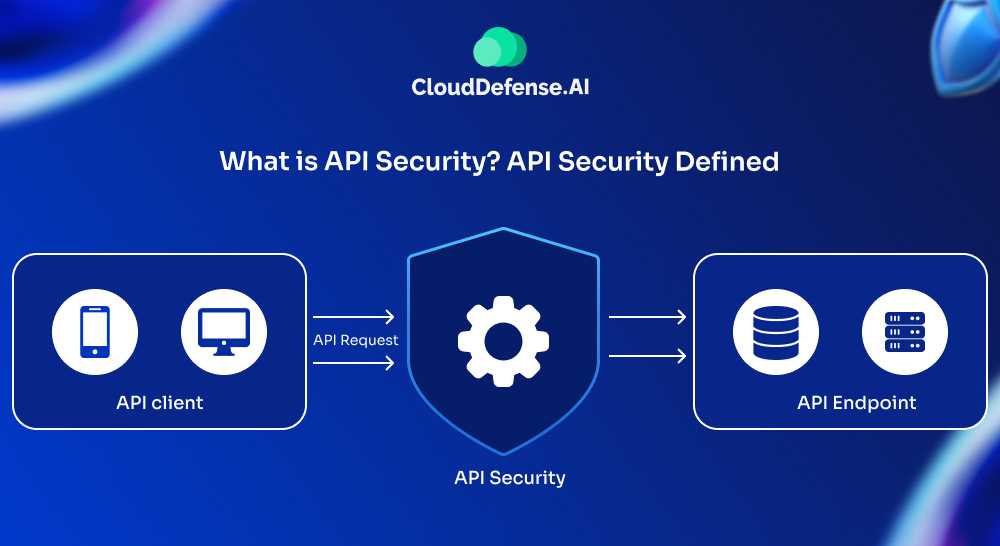
API security refers to the measures and policies used to protect APIs from attacks and unauthorized access. Since APIs are the gateways to most web-based applications, they have become prime targets for hackers aiming to steal data or disrupt services.
APIs enable external users to access key functions of an application, which increases the risk of attacks like MITM, DDoS, Injection, or Broken Access Control.
To counter these threats, security strategies such as API gateways, multi-factor authentication (MFA), and encryption ensure only authorized users can interact with APIs.
API security also involves monitoring, content validation, and rate limiting, making it a critical aspect of modern web application security.
What is API?
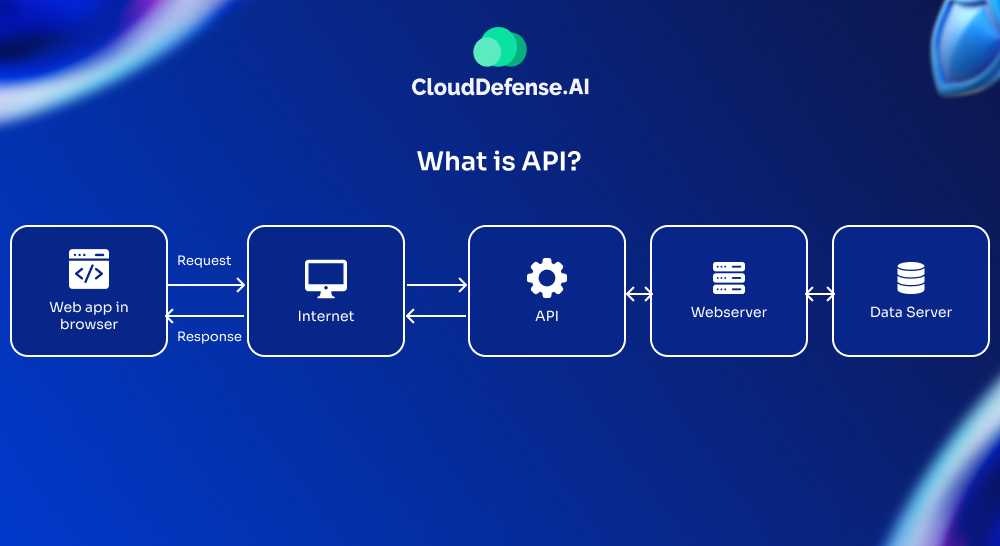
An Application Programming Interface (API) is a set of rules that enables different software entities to communicate with each other.
APIs define the methods and data structures that developers can use to interact with an external software component or service. For instance, when you log in to a website using your Google account, an API enables that communication between the website and Google’s systems to verify your identity.
APIs are foundational to software development because they allow the integration of third-party services, automation of tasks, and expansion of functionalities without starting from scratch. For example, businesses use APIs to integrate payment gateways like Stripe, enable social media login features, or pull data from external databases.
There are different types of APIs, each designed for specific use cases:
- Private APIs – Used internally within organizations.
- Partner APIs – Shared with specific external partners.
- Public APIs – Open APIs accessible to external developers.
APIs simplify and speed up software development but require strong security measures, as they are increasingly becoming targets for attackers.
The Four Common Types of Web APIs
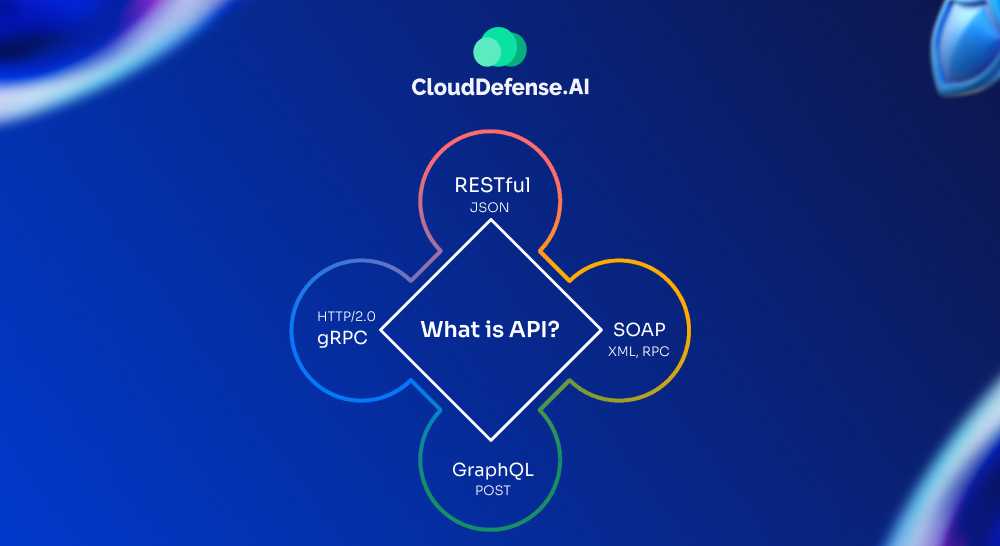
APIs come in various forms, each designed for specific communication protocols and use cases. Understanding the most common types helps in implementing the right security measures.
- REST APIs (Representational State Transfer): These are the most commonly used APIs, adhering to a set of architectural constraints such as stateless communication and resource-based interactions. REST APIs are widely adopted because they use simple HTTP methods like GET, POST, PUT, and DELETE, making them easy to implement and understand.
- SOAP APIs (Simple Object Access Protocol): SOAP APIs are more rigid and require strict message structure formats (typically XML). Although they are more complex than REST APIs, they offer higher levels of security and are commonly used in financial or enterprise-level applications where data integrity and security are paramount.
- GraphQL APIs: GraphQL is a query language for APIs that allows clients to request exactly the data they need, reducing over-fetching or under-fetching of information. It provides more flexibility compared to REST, making it increasingly popular among developers for dynamic data fetching.
- WebSocket APIs: Unlike REST or SOAP, which are request-response-based, WebSocket APIs allow full-duplex communication, meaning data can flow in both directions simultaneously. These are useful for real-time applications like chat services or stock market tickers.
Understanding these four types of web APIs is required in determining the right security measures. Each has its own strengths, weaknesses, and use cases, which influence the security protocols needed to protect them from cyberattacks.
Why is API Security Important?
APIs have become an essential part of modern tech ecosystems, from powering mobile apps to enabling integrations between business systems. However, this level of integration also means that APIs are exposed to the internet, making them an attractive target for cybercriminals.
Without proper security measures in place, APIs can expose sensitive data, enable unauthorized access, and lead to severe financial and reputational damage.
API security is vital for several reasons:
- Data protection: APIs often exchange sensitive data, such as personal information, financial transactions, or proprietary business data. Securing this communication ensures that sensitive information isn’t exposed to unauthorized entities.
- Prevention of unauthorized access: Poorly secured APIs can allow attackers to gain unauthorized access to systems. This can lead to data breaches, service disruptions, or even complete system takeovers.
- Regulatory compliance: Various regulations like GDPR, HIPAA, and CCPA require organizations to secure personal data. APIs handling such data must adhere to these standards to avoid fines and legal consequences.
- Trust and reputation: A secure API fosters trust between businesses and their customers. Conversely, a security breach due to poorly protected APIs can result in a loss of customer confidence and significant reputational damage.
API security is not just a technical necessity but also a business imperative. Ensuring the security of your APIs helps to safeguard sensitive data, maintain regulatory compliance, and protect your organization’s reputation.
OWASP Top 10 API Security Threats
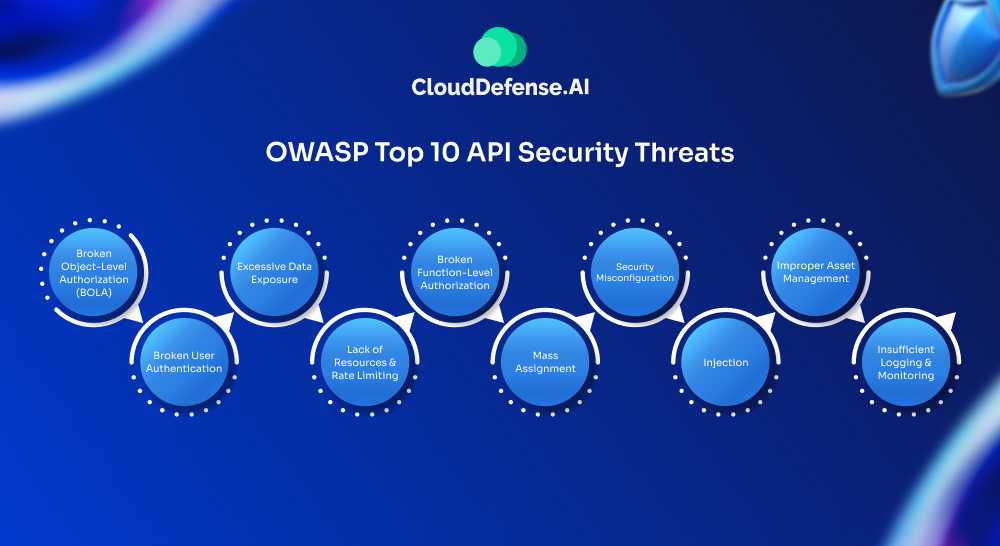
APIs play a critical role in modern software, but they also expose vulnerabilities that attackers can exploit. The OWASP API Top 10 highlights the most prevalent API security threats, including:
- Broken Object-Level Authorization (BOLA): Attackers exploit APIs to access data they aren’t authorized to by manipulating object identifiers, like user IDs.
- Broken User Authentication: Flaws in authentication mechanisms, such as weak passwords or improper session management, allow attackers to impersonate legitimate users.
- Excessive Data Exposure: APIs sometimes return more data than necessary, leaving sensitive information, like personal or financial details, exposed.
- Lack of Resources & Rate Limiting: Without limits, attackers can overwhelm APIs with requests, resulting in Denial-of-Service (DoS) attacks.
- Broken Function-Level Authorization: Misconfigured access controls allow unauthorized users to perform administrative actions.
- Mass Assignment: Attackers manipulate API inputs to modify object properties via overly permissive APIs.
- Security Misconfiguration: Misconfigurations in headers or Cross-Origin Resource Sharing (CORS) lead to vulnerabilities.
- Injection: APIs remain susceptible to SQL, NoSQL, or script injections.
- Improper Asset Management: Exposed old or unused APIs increase the attack surface.
- Insufficient Logging & Monitoring: Poor monitoring allows attackers to persist unnoticed.
Addressing these threats is key to ensuring robust API security and protecting sensitive data.
REST API Security
REST APIs are the most widely used type of API, and their security is critical for protecting sensitive data and services. The open and stateless nature of REST APIs makes them flexible but also introduces security challenges. A well-implemented REST API security strategy includes measures such as secure communication channels, proper authentication, and strong data validation.
How to Secure REST API
- Use HTTPS for Encryption: All data transmitted between the client and the server should be encrypted using HTTPS. This ensures that data cannot be intercepted or tampered with during transmission.
- Implement Strong Authentication: REST APIs should enforce strong authentication mechanisms like OAuth 2.0 or API keys to verify the identity of users and services interacting with the API. Using multi-factor authentication (MFA) adds an additional layer of security.
- Rate Limiting and Throttling: APIs should have rate limiting and throttling mechanisms in place to prevent abuse from automated scripts or brute-force attacks. By controlling the number of requests that can be made, APIs can reduce the risk of being overwhelmed.
- Input Validation: All data inputs should be thoroughly validated to prevent injection attacks. This includes checking the length, type, format, and range of input data to ensure it adheres to the expected values.
- Token-Based Authentication: Using token-based authentication, like JSON Web Tokens (JWT), adds an additional layer of security. These tokens contain encoded information that verifies the user’s identity and session validity.
- Monitor and Log API Traffic: Continuous monitoring and logging of API requests help detect unusual activity or potential attacks. This enables security teams to respond quickly to threats and prevent further damage.
Securing a REST API involves not only protecting the data but also ensuring that the API itself is hardened against unauthorized access and attacks.
Why are Authentication and Authorization So Important for API Security?
Authentication and authorization are critical components of API security, ensuring that only authorized users can access sensitive data and services.
- Authentication: This verifies the identity of the user or system interacting with the API. It ensures that requests are coming from a trusted source, typically through methods like API keys, OAuth tokens, or JWT tokens. Strong authentication mechanisms reduce the risk of unauthorized access.
- Authorization: Once a user is authenticated, authorization determines what actions they are allowed to perform or what data they can access. Role-based access control (RBAC) or attribute-based access control (ABAC) ensures that users can only interact with the resources they are permitted to access, reducing the risk of data exposure or service disruption.
Inadequate authentication and authorization measures can lead to data breaches, service disruption, and unauthorized access. Therefore, it is essential to implement robust methods to verify users and control their access to sensitive resources.
API Security with CloudDefense.AI
CloudDefense.AI is a top-tier cybersecurity platform designed to protect your APIs from exploitation. Its advanced API scanning solution detects vulnerabilities in real-time, safeguarding against OWASP Top 10 threats and more. The API scan runs smoothly on your runtime application using a fully packaged image, requiring no additional installations or integrations.
CloudDefense.AI’s platform supports multiple programming languages like Python, Java, and JS, ensuring compatibility across your environments. With a user-friendly interface and fast setup—completed in just 2 minutes—the platform is accessible even for non-experts. Regular API scans are recommended to quickly identify and fix vulnerabilities, enhancing the security of your API ecosystem.
Trusted by security teams globally, CloudDefense.AI’s API scan offers a complete, hassle-free solution to ensure continuous protection of your APIs, allowing you to secure your systems with just a few clicks.







