Everyone knows that a defensive strategy is only as strong as the weakest point. When talking about Single Delivery Platform Cybersecurity, this is especially poignant. It doesn’t matter how many robust defense components you implement as long as you’re utilizing weak and outdated security tools in other areas.
Operating on this frame of mind, it turns out that the average cybersecurity team is utilizing multiple tools, sometimes as many as 40+ tools to manage their security infrastructure.
With businesses moving from the traditional perimeter security structure to a cloud-based environment, this “frankencloud” method of security doesn’t cut it.
What Is the Frankencloud and Why Is It a Problem?
The “frankencloud” is a term to describe the mish-mash approach of organizations taking advantage of the growing cloud trend while still maintaining some of the traditional methods for data storage, security, and collaboration.
This is what pushes organizations to adopt countless software tools, especially security tools, in order to maintain some semblance of order within their digital environment.
These attempts at maintaining traditional structures created a hybrid cloud approach that has created many gaps in security infrastructures and left many organizations spending far more money than is necessary.
This is especially true considering the fact that social engineering is the number one cause for web application security breaches.
Now, more than ever, the value of DevSecOps is shown. While developers are focused on making this new transition streamlined, checking for bugs and making sure everything is running smoothly the security team is protecting your business from all kinds of dangers, as well as keeping tabs on all the licenses and compliances that you need to adhere to.
In fact, the numbers show that:
- In 2020, ⅓ of breaches utilized social engineering methods
- 95% of network breaches were brought on by spear-phishing attacks
- And 43% of workers have openly admitted to making mistakes that have compromised security
In many instances, companies don’t need more tools, they need to educate their employees on security best practices. However, that doesn’t mean there isn’t a sorely needed reckoning for the way cybersecurity toolsets are structured.
Three Problems with Frankensecurity
Outside of budgetary expense, the many issues with a Frankenstein approach to security infrastructure are easily boiled down into three distinct problems:
1. Data Overload
These teams are using everything from intrusion detection systems and firewalls to VPNs and web filtering proxies to guard their systems and data. This extensive list of common security tools all from different vendors has also created a problem of information overload:
“They need to use the threat information to determine what is applicable to their organization and tailor it to their industry. Risk has a number of factors, not only the impact to organization but also the real probability of the threat,” Chenette said.
Security teams need to distill down all of that threat intelligence and find what matters in relation to their business because most enterprises aren’t regularly testing all of their security tools, “The alerts that matter are being missed,” Chenette said.
What good are security alerts and analytical reports if there is too much information for a security team to digest and act on?
2. Lack of Cohesive Integration
While every software vendor loves to tout the integrative capacity of their tools, these claims are not always backed up in practice, especially when it comes to security. The “bolt-on” method for attaching tools leads to assumptions made about the layers of security.
Essentially companies will continually add more and more tools to their infrastructure as needs arise, thinking that the software patch act is creating more security.
This decentralized approach to security infrastructure creates its own host of issues, including:
- Outdated and unpatched software
- Inability to stay current with other vendor updates
- Lack of visibility into the holes created by other vendor products
This is exactly the lack of centralized control that created Android’s reputation for easy-to-breach software.
Google creates the Android operating system, then distributes it to multiple phone manufacturers, all of which have control over how that operating system will appear and function on their devices.
Phone manufacturers would alter and add what is known as “bloatware” to the operating system, which diminishes the integrity of the user experience.
This also means that these phone manufacturers can decide which Google updates they will push to their users, leading to some Android users running on outdated and unsecured versions of the OS.
Contrast this system to Apple, which has full end-to-end control of their operating systems and the ability to push updates to its user’s phones, leading to a more seamless and secure experience. No bloatware, no missed security patches, and no incongruity.
Right now, most organizations are operating on a disjointed Android-like model with all kinds of different tools that don’t work together with updates coming at seemingly random intervals.
3. Abundance Potential Failure Points
This follows into the next issue, which is the issue with all complexity. The more complex the solution to a![]() problem, the higher the chances of failure. Kind of like the difference between a Toyota and a Mercedes Benz.
problem, the higher the chances of failure. Kind of like the difference between a Toyota and a Mercedes Benz.
A Toyota is simple, understandable, and reliable, while a Mercedes Benz is complex, high tech, and prone to reliability issues as it ages.
A patched-together cybersecurity infrastructure is no different. No security team can account for the potential issues that might exist in a dozen software tools.
As the infrastructure ages, the creation of new technologies threatens these ecosystems at multiple levels, which means the security team is responsible for further patching, updating, and ultimately adding more security tools. This is an unsustainable model and inevitably leads to failure.
Single Delivery Platform Cybersecurity Is the Solution
The answer to all of this complexity is for organizations to rid themselves of the myriad of tools they’ve swamped themselves in and introduce a singular security delivery platform (SDP) that meets their network and data security.
swamped themselves in and introduce a singular security delivery platform (SDP) that meets their network and data security.
This structure allows organizations to deploy network and security tools through a singular platform run by a single vendor, allowing them to get consistent service, reports, and solutions without the confusion of the traditional model.
These SDPs employ inline visibility and security that works throughout your organization’s network and cloud infrastructure so security teams can monitor data and traffic that flows in and out of their entire work environment.
No more dealing with tools that no longer communicate with each other. No more redundancies, missed alerts, and unnecessary complexity. Everything runs through a single security provider.
This type of consolidation is taking many forms, including the emergence of secure access service edge (SASE) architecture. SASE is a newer term coined by Gartner, which describes a security infrastructure that combines a multitude of next-generation network and security technologies.
This concept ditches the traditional perimeter security concept and instead adopts an edge-based architecture that secures, monitors, and delivers traffic and data between users and the cloud.
SASE architecture utilizes all kinds of functions that many vendors are striving to consolidate under singular platforms, including:
- Zero Trust models
- Cloud Access Security Brokers (CASBs)
- Firewall as a Service (FWaaS)
- Software-Defined Wide Access Networking (SD-WAN)
- Next-Generation Secure Web Gateways (NG-SWG)
- Advanced Threat Protection
- Malware Scanning
- And many others
Consolidated single platforms also have the benefit of seamless interaction between different functionalities. SASE architecture employs many AI and machine-learning techniques to develop user personas in order to detect unusual behaviors, such as:
- Irregular login times
- Alteration of asset data
- Movement of data
- Attempted alteration of user privileges
- Screenshotting data
- Movement of professional data to personal applications
- Attempted lateral movement to other systems
Single platforms don’t have to deal with the incongruencies that come up when using tools made by multiple vendors all with their own design, detection, and alert systems. Using a single vendor ensures security cohesion.
The biggest benefit to SDP and SASE besides the decrease in overall complexity is the ability to scale this infrastructure.
Software as a Service (SaaS) and Infrastructure as a Service (IaaS), two major components of SDP and SASE, both allow organizations to focus on their core functions while the vendor(s) they work with scale the network and security solutions as needed.
This way organizations are able to adapt to changing needs and security threats as they arise without investing in new “bolt-on” solutions that may or may not work within an existing framework.
How CloudDefense.AI Works Within an SDP (Single Delivery Platform Cybersecurity) Framework
The software development life cycle (SDLC) is an arduous process full of complexities and ever-changing variables. The last thing you want is your development toolset to reflect that complexity and lower the level of your vulnerability management.
CloudDefense.AI works within an SDP framework by providing the functionality of multiple application development security tools, including SCA, SAST, DAST, and container security.
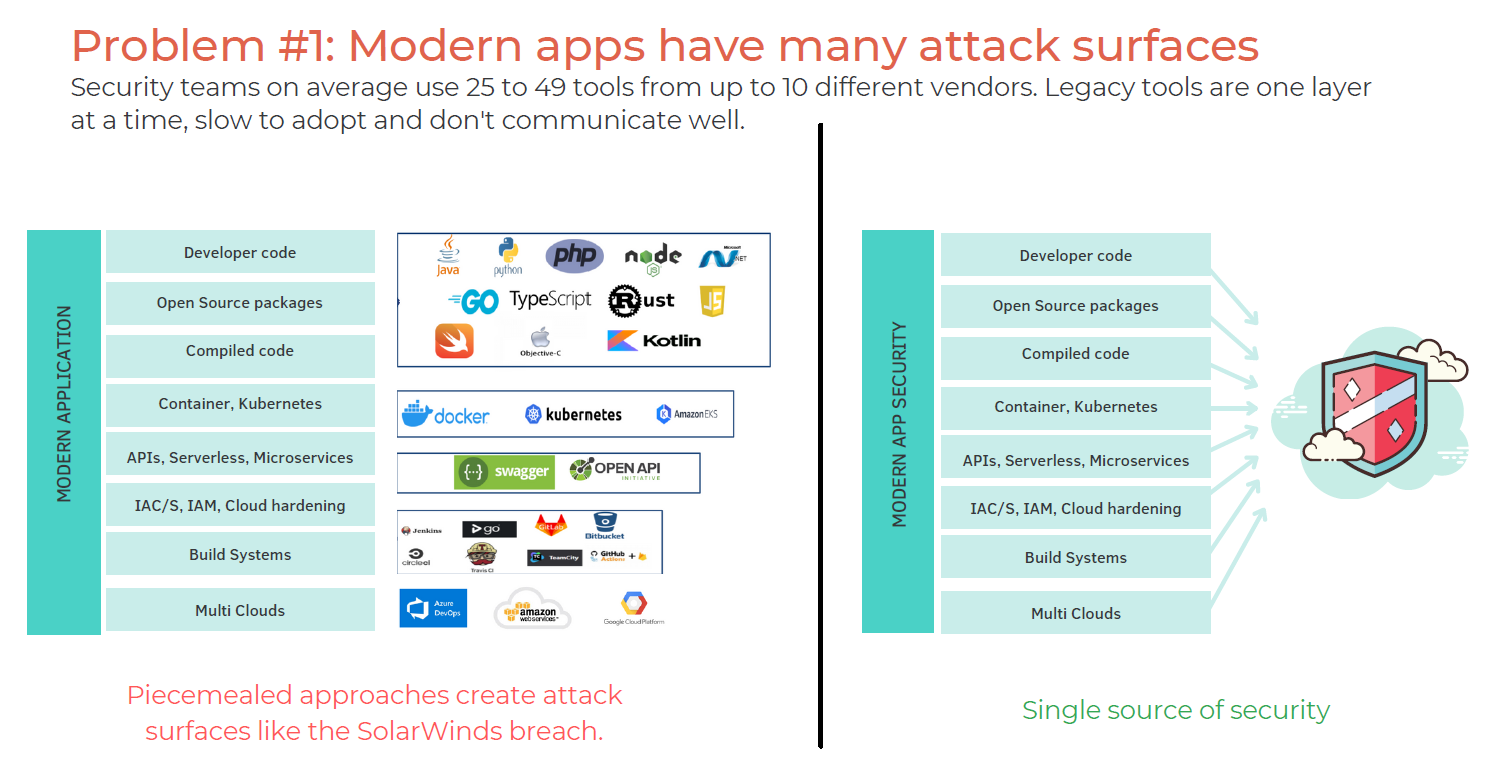
Instead of piecing together this toolset through hours and hours of trials, testing, negotiation, and purchase, CloudDefense.AI offers all of the functionality in one seamless platform.
You can avoid the problems of uneven update schedules, lack of integrations, and scattered functionality which requires extensive manpower and expertise.
CloudDefense.AI will help you secure your application development cycle, all while saving you time, money, and the headache of countless moving parts.
Save yourself the stress, pare down your toolset, and streamline your security with CloudDefense.AI.







