Customer data is undoubtedly one of the most precious assets for every organization as it facilitates their business flow. To protect customer data from any kind of theft, organizations are turning to regulations like SOC 2 to showcase their commitment to data security, availability, confidentiality, and integrity.
SOC 2 serves as a third-party validation that enables the organization to protect all the customer data and information they have stored. However, the journey to a successful SOC 2 audit can be a bit overwhelming and time-consuming.
To streamline the audit process various strategies have been developed allowing organizations to achieve SOC 2 certification successfully in a shorter time frame. This article will guide us through seven tips to expedite the SOC 2 audit process.
What is SOC 2 Audit?
SOC 2 is a security framework that outlines how an organization should protect all the sensitive customer data they store from any type of security incident, vulnerability, or unauthorized access. SOC 2 stands for Service Organization Control Type 2 and was developed by the American Institute of CPAs.
This framework defines the criteria to protect customer data. It is based on five trust service principles: security, privacy, confidentiality, availability, and processing integrity.
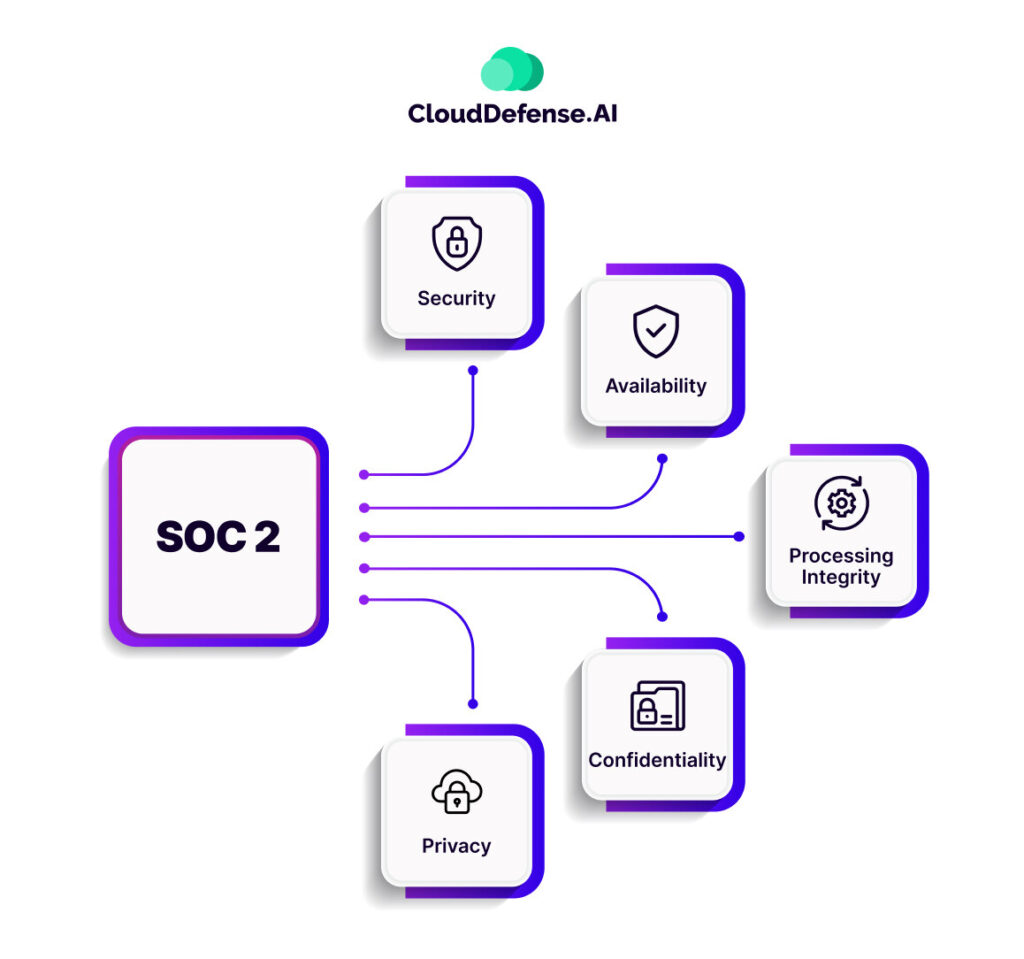
What makes SOC 2 compliance amazing is that it is unique to every organization based on its individuals. Every organization adhering to the SOC 2 framework goes through the SOC 2 audit service.
SOC 2 assesses how an organization manages its customer data and service for the five TSCs. This independent audit ensures that the organization has created a secure infrastructure where sensitive customer information is managed. The audit focuses on the internal controls that the organization has implemented to monitor the services.
Types of SOC 2
SOC 2 compliance reports come in two types: Type 1 and Type 2. Both the SOC 2 attestation reports have their specific purpose and requirements.
The SOC 2 Type 1 report outlines an organization’s internal security controls at a specific point in time.
The main focus of the SOC 2 Type 1 compliance report is to evaluate whether the internal controls are appropriately implemented and designed correctly to protect customer information. It also checks whether the internal controls adhere to the required five Trust Service Criteria. The time of the whole Type 1 audit process and reports is a few weeks.
The SOC 2 Type 2 audit analyzes how the system and all the internal security controls of an organization function over some time. The time span generally ranges from 3 months to a year.
The audit process checks not only whether the control functions safeguard the intended data but also its operational effectiveness. The Type 2 audit process is quite lengthy and quite expensive in comparison to the SOC 2 Type 1 audit. However, a Type 2 report will contain all the information as a Type 1 audit report along with better Pluralize.
Why is the SOC 2 Audit Process Important?
A SOC 2 audit process is of critical importance for numerous reasons, helping an organization strengthen its security posture. It reflects the organization’s commitment to protecting all the customer information they collect. Here are the reasons that make the SOC 2 audit process important:
- The SOC 2 audit process helps evaluate whether the organization is using the right security processes and tools to protect customer data. It also checks whether the organization is complying with all the best practices that will ensure optimum protection of the data.
- The process helps the organization showcase its commitment to customer data protection, which, in turn, helps it gain customer trust.
- The compliance requirement of SOC 2 audit overlaps with the compliance requirement of frameworks like HIPAA and ISO 27001. It helps many organizations verify whether they adhere to the industry-specific security frameworks.
- In the modern competitive business environment, a successful SOC 2 audit helps an organization get an edge over its competitors. Many partners and clients opt for organizations that adhere to SOC 2. Therefore, a successful certification can open more opportunities.
- The complete audit process helps an organization enhance its overall security posture and protect them against modern cyber-attacks. SOC 2 requires an organization to follow certain best security practices that help the organization overcome many security gaps.
- A successful SOC 2 audit report will help an organization avert possible data breaches and prevent financial and reputation damage. It enables the organization to uphold the trust the organization is appropriately protecting the customer data.
- It provides an organization’s top leadership and board members with the confidence that their organization can protect all sensitive customer data. It demonstrates that the organization can tackle all types of security breaches or incidents.
How to Prepare for SOC 2 Audit?
The preparation for the SOC 2 audit is a vital process that involves a systematic period in security controls and practices aligned with the requirements of Trust Service Criteria(TSC). Here are some essential SOC 2 audit checklists you should know about.
Determining the Scope and Audit Type
The first thing you need to determine is the motive behind the SOC 2 audit. Since SOC 2 audit evaluates data security, infrastructure, risk management policies, tools, and various other aspects, you have to consider which aspect would be covered in the audit.
You also need to consider the type of SOC 2 audit report you need. The SOC 2 Type 1 audit is quicker and less expensive period It only evaluates the internal controls’ effectiveness for a particular point in time. The SOC 2 Type 2 audit goes through a time frame of 3 to 12 months, where it accurately evaluates the internal security control and operational effectiveness.
Select The Right TSCs
The SOC 2 audit is based on the Trust Service Criteria and it evaluates your control over them. The five TSCs include security, availability, processing integrity, confidentiality, and privacy.
However, the audit won’t involve all five TSCs at once just the security criteria which is a mandatory component. To save resources, you can choose any criteria along with security that will benefit your organization the most.
Build a Good Compliance Team
The SOC 2 audit is a lengthy process, and one of the best ways to streamline it is by building a good compliance team before starting it.
To build a strong team, you must identify the members and their roles. Some key roles in a compliance team are executive sponsor, project manager, author, legal personnel, security personnel, and external consultant.
Arranging All the Necessary Documents and Policies
Another primary checklist for the SOC 2 compliance audit is arranging all the necessary documents and policies that will be needed during the auditing process.
Documents like common population, procedures, implementation, operation, and policies will be needed during the SOC 2 audit process. The SOC 2 auditor will examine all the critical documents throughout the period. It is best to arrange them beforehand ready to provide them to the auditor when asked.
Run a Readiness Assessment
One of the best ways to prepare for a SOC 2 audit is to perform a readiness assessment. You can perform a readiness assessment by employing the help of an auditor. An auditor will evaluate all the systems, security controls, processes, and other components that will be involved in the official SOC 2 audit process.
After the readiness assessment, the auditor will provide a report highlighting the weaknesses and will also give recommendations to fix them. This process is beneficial because it will help you identify the areas in your system and control those that require improvements before starting the SOC 2 audit.
Run a Gap Analysis
Along with readiness assessment, you should also conduct a gap analysis to prepare your organization for the SOC 2 audit. The gap analysis will evaluate your current situation and provide a clear picture of the condition of your compliance requirement based on SOC 2 trust criteria.
The gap analysis is a time-consuming process that involves implementing many security controls, training employees on security controls, making changes to the workflow, and creating control documentation.
In the end, the gap analysis will highlight the gaps that you need to solve before starting the official audit process. If you are confident with the gap analysis process, you can hire any particular expert or firm who will do the gap analysis on your behalf.
Perform Final Assessment
Before starting the SOC 2 audit process, it is best to perform a final assessment to ensure all the gaps have been closed and there are limited weaknesses in the controls. Once the auditor highlights the weaknesses in the report, you should patch them immediately. Once you have addressed all the gaps and weaknesses, you will be ready for the official SOC 2 audit.
7 Tips to Expedite the SOC 2 Audit Process
The SOC 2 audit is a lengthy process and it entirely depends upon your organization’s scope and objective.
To expedite the audit process, you need actionable strategies that will guide your organization to accelerate the whole process without jeopardizing any aspect. Here are 7 tips you can follow to expedite the SOC 2 audit process:
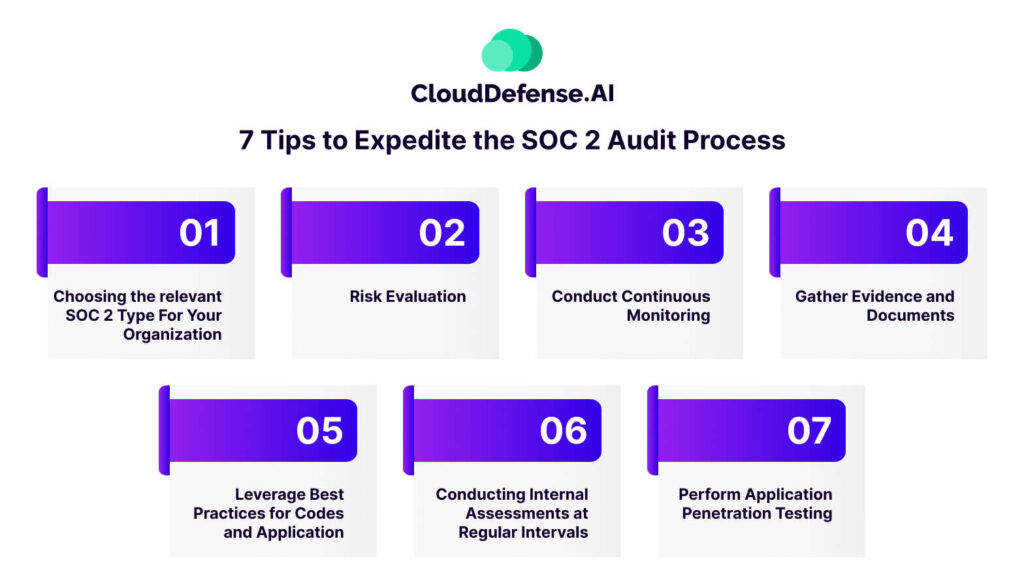
Choosing the Relevant SOC 2 Type for Your Organization
SOC 2 audit reports come in two types: Type 1 and Type 2. Depending upon your organization’s requirements, resources, time constraints, and client needs, you will have to decide the type.
The Type 1 audit is quick and takes a few weeks to evaluate the effectiveness of your system and security control. The Type 2 audit checks the internal controls for over three to twelve months to certify all the internal controls have been appropriately implemented.
You should choose Type 1 if you need to quickly achieve a SOC 2 compliance report. Otherwise, you can choose Type 2 if you are looking for details or have specific client requirements.
Risk Evaluation
To accelerate the SOC 2 audit process, it is always best to perform risk quantification before starting the SOC 2 audit process. All the essential customer and business information that are prone to exposure and risk should be evaluated and quantified. Various methods can be implemented for the risk quantification of customer information and financial assets.
Conduct Continuous Monitoring
Performing continuous monitoring serves as one of the best ways to expedite the SOC 2 audit process. Implementing automated monitoring tools will help you to continuously monitor the system for suspicious activities, vulnerabilities, and potential threats.
It is highly helpful for organizations as it will help them to save resources and direct them elsewhere. Continuous monitoring will also help the organization maintain SOC 2 compliance by constantly assessing the security controls against the five TSCs.
Once you implement an automated monitor, you should regularly review the logs and reports so that your team can promptly remediate issues upon detection.
Gather Evidence and Documents
The documents and evidence regarding your organization’s security posture act as the main proof of your organization’s commitment to security and compliance. You should maintain a well-organized document and proof of your security controls and processes so that it is easier for the auditors to perform SOC 2 audits.
You should keep a central repository where every team will submit evidence, logs, and other documents. This repository will make the SOC 2 auditing process more manageable for the auditor as the auditor can easily access all the information from one place.
The document and evidence gathering should continue throughout the audit period will accelerate the process.
Leverage Best Practices for Codes and Applications
Another efficient way to expedite the SOC 2 audit process is by leveraging the best practices for the security of your codes and applications. Enforcing the best practices for codes and applications before starting the SOC 2 audit process will smooth the process during the official audit.
If you are using GitHub, then you have to first enable the safeguarded branches and create a pull request template while putting in the root of your project. However, you should review the pull requests that are linked to the main product. Only authorized entities should be allowed to push the main as well as deployment branches.
Conducting Internal Assessments at Regular Intervals
Accelerating the SOC 2 audit process isn’t an easy task but regular internal assessment can ease the process. Regular internal assessments help polish the security posture and ensure your internal controls can adhere to the criteria of TSCs.
It is better to perform a self-assessment using SOC 2 criteria to evaluate security controls and procedures so you won’t face any issues during the official SOC 2 audit process. Self-assessment will help you stay prepared by addressing all the gaps and ensuring the whole audit ends quickly.
Perform Application Penetration Testing
Another way to expedite the SOC 2 audit and adhere to SOC 2 requirements is by performing penetration testing through a third-party vendor. Penetration testing serves as an authorized security attack performed by ethical hackers to assess the security posture of the system and determine changes that need to be made to safeguard the system from real attacks.
There are many ways to perform penetration, and you can take assistance from any third-party organization.
How does CloudDefense.AI help with your SOC 2 Audit?
Managing compliance, especially for sensitive customer data, is simplified with state-of-the-art services offered by CloudDefense.AI. Ensure adherence to security standards like SOC 2 effortlessly with the help of our all-in-one suite. Our platform offers a cutting-edge multi-cloud compliance management system that automatically assesses your business resources against industry standards.
Our comprehensive tools offer real-time insights highlighting non-compliant resources, allowing you to compare them with available frameworks. Meticulously tailor security practices with custom policies and create personalized compliance frameworks to help you master the art of staying compliant.
CloudDefense.AI also excels in reducing misconfigurations and enhancing SOC 2 compliance. Our advanced platform employs automated checks and real-time monitoring to identify and rectify potential configuration issues swiftly through our top-of-the-market Cloud Security Posture Manager. Through proactive measures, we significantly reduce the risk of misconfigurations that could compromise the security and integrity of your multi-cloud environment.
Use our platform to help you generate real-time reports with a single click that your security team and executive board can use. Maintain streamlined compliance control for not only SOC 2 but 20+ compliance frameworks, including GDPR, HIPAA, CCPA, ISO, PCI, etc., through CloudDefense.AI’s unified dashboard.
FAQs
How can I expedite the SOC 2 audit process without compromising quality?
To expedite the SOC 2 audit process, your organization needs a strategic approach and comprehensive preparation. Not only do you have to understand the SOC 2 framework, but you must create policies and procedures and perform constant gap analysis. It is important that you conduct internal audits, perform mock audits, and engage external consultants to accelerate the audit process.
How much does a SOC 2 audit cost?
The SOC 2 audit cost varies widely. The average quotation for the audit ranges from $5,000 to $60,000. Most reputed firms quote around $20,000 for SOC 2 Type 1 audit while the quotation for SOC 2 Type 2 may go up to $30,000.
The overall cost depends upon the organization’s size, audit readiness, the complexity of the internal controls and system, auditor, and selected TSCs.
How long does a SOC 2 Audit take?
The SOC 2 audit process has an audit time between a few weeks to twelve months. However, it entirely depends upon the type of SOC 2 audit you desire. The SOC 2 Type 1 audit takes between a few weeks and three months, while the SOC 2 Type 2 audit process takes between three to twelve months.
The period of the audit process depends upon multiple factors, especially the complexities of your controls and how well the organization is prepared with the documents.
Who can perform a SOC 2 Audit?
The SOC 2 audit can be only done by a licensed CPA auditor or a firm recognized by the AICPA. The SOC 2 auditor or firm must have no official connection with the organization they are auditing. The SOC 2 audit firm or auditor must comply with AICPA’s professional standards and the latest guidance to perform an official SOC 2 audit.
Conclusion
Expediting the SOC 2 audit process is not an easy task, but it is entirely achievable. Through this guide, we have provided all the tips and checklists you need to follow to accelerate the SOC 2 audit process.
The acceleration depends upon many factors, especially the SOC 2 audit preparation and documentation. It is always wise to hire an external auditor or firm to review your security posture and control implementations before conducting an official SOC 2 audit because it increases the chance of approval.







