Staying ahead of threats while managing tight budgets has become more essential than ever for security professionals. To make the right purchase, a good evaluation of different intrusion defense tools is important to get the right one in your budget.
One such tool, the Intrusion Prevention System, often confused due to its similarities with its predecessor, the Intrusion Detection System. However, IPS represents a significant evolution in cybersecurity technology, offering advanced capabilities that allow you to fight modern threats head-to-head.
In this blog, we’ll discover more about what Intrusion Prevention Systems are, explore their functionalities, and shed light on how they operate to strengthen network defenses.
Let’s dive right in!
What is an Intrusion Prevention System?
An intrusion prevention system, or IPS, is a network security tool designed to monitor and protect against malicious activities. Functioning as either hardware or software, it continuously scans network traffic for potential threats.
Unlike intrusion detection systems, which merely flag suspicious behavior, an IPS takes immediate action to prevent attacks. It accomplishes this by alerting security teams, terminating dangerous connections, removing malicious content, or triggering other security measures. IPS solutions are proactive, swiftly responding to potential threats to mitigate risks and secure network integrity.
IPS solutions play an important role in strengthening network defenses. They are often integrated into NGFWs or UTM systems, ensuring complete protection without compromising network performance.
Why Intrusion Prevention Systems are Important?
IPS is considered to be an essential pillar in enterprise security systems for several reasons. Firstly, in multi-cloud networks with numerous access points and high volumes of traffic, manual monitoring and response are impractical.
This is especially true in cloud environments where the interconnected nature can expand the attack surface, heightening vulnerability to threats.
The internet has presented businesses with an increasing amount of sophisticated threats. In such scenarios, the automated capabilities of IPS become essential, enabling rapid threat response without burdening IT teams.
As a fundamental part of an enterprise’s security infrastructure, IPS helps to prevent some of the most serious and sophisticated attacks.
By monitoring network traffic in real time and utilizing network behavior analysis, IPS identifies potential threats swiftly.
In the event of unauthorized network access, IPS promptly identifies suspicious activity, logs relevant information, and triggers automated responses based on pre-established rules set up by network administrators.
How Does Intrusion Prevention System Work?
IPS operates as a vigilant guardian within the network, positioned inline to carefully check the traffic flows between the public internet and the company network. Unlike its passive predecessor, the IDS, the IPS takes measures to reduce potential threats in real time.
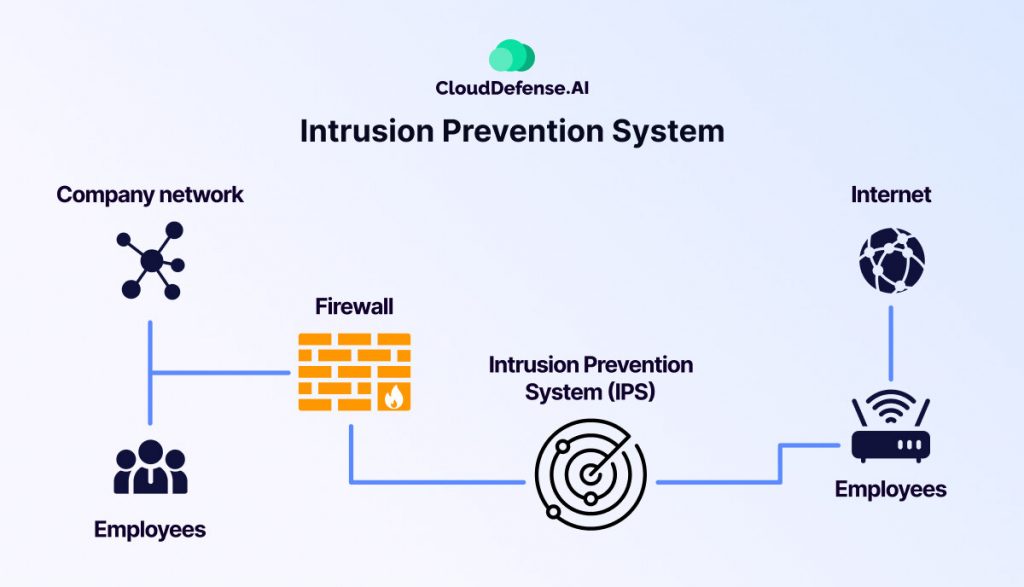
IPS is situated ahead of firewalls and excels in analyzing the traffic for any malicious behavior. It identifies suspicious activities and triggers automated responses to mitigate risks.
These responses range from alerting administrators to dropping malicious packets, blocking traffic from suspicious sources, resetting connections, or configuring firewalls to strengthen defenses against future attacks.
To fulfill its role effectively, the IPS must balance efficiency, speed, and accuracy, ensuring seamless operation without compromising network performance. IPS commonly uses two techniques for threat prevention:
- Signature-based Detection: This method relies on a database of uniquely identifiable patterns or signatures of known exploits. When a new exploit is discovered, its signature is recorded and added to the database. Signature-based detection can target specific exploits (exploit-facing signatures) or underlying vulnerabilities (vulnerability-facing signatures), though the latter may increase the risk of false positives.
- Anomaly-based Detection: Anomaly-based detection compares network traffic against pre-calculated baseline performance levels. When deviations from the baseline are detected, indicating potentially malicious activity, the IPS takes action to prevent further threats.
Types of IPS Detection?
IPS includes various types of detection tools that cater to specific security needs
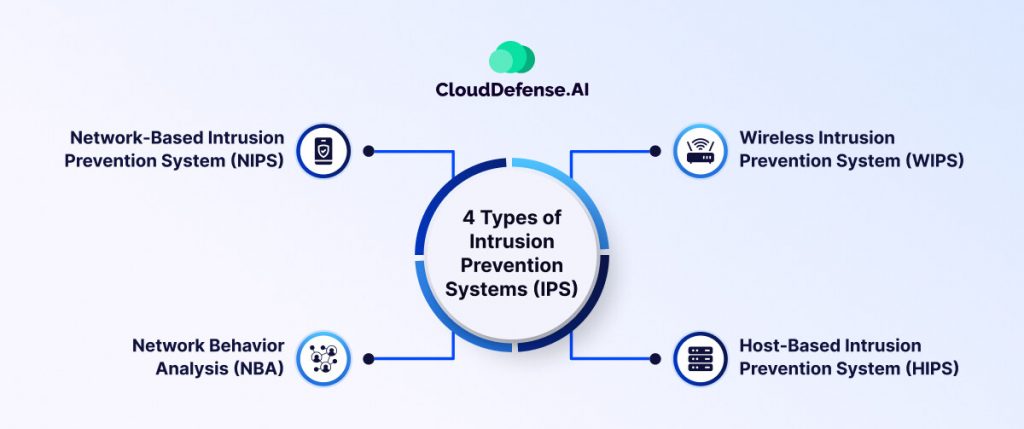
Network-Based Intrusion Prevention System (NIPS)
Deployed strategically at critical points within the network infrastructure, NIPS monitors all incoming and outgoing traffic, actively scanning for potential cyber threats.
By analyzing network packets in real-time, NIPS can swiftly detect and prevent malicious activities, serving as a frontline defense mechanism for the entire network.
Wireless Intrusion Prevention System (WIPS)
Specializing in Wi-Fi network security, WIPS acts as a gatekeeper for wireless networks, identifying and removing unauthorized devices that attempt to gain access.
By continuously monitoring wireless traffic, WIPS ensures the integrity and security of the Wi-Fi network, preventing unauthorized access and potential breaches.
Host-Based Intrusion Prevention System (HIPS)
Installed directly on endpoints such as individual computers or servers, HIPS monitors inbound and outbound traffic specific to that device. While complementing NIPS, HIPS serves as a last line of defense, blocking threats that may have evaded detection by the network-based system.
This localized approach provides additional protection for individual hosts, enhancing overall security posture.
Network Behavior Analysis (NBA)
Focused on analyzing patterns and anomalies within network traffic, NBA detects unusual behaviors or traffic flows that may indicate potential threats, such as DDoS attacks.
By monitoring network behavior, NBA enhances threat detection capabilities, enabling response to security threats and vulnerabilities.
Why Do You Need an IPS?
An IPS is an irreplaceable piece of network security tech. With the constant emergence of new threats and vulnerabilities, traditional security measures alone are insufficient to provide adequate protection.
An IPS acts as a proactive defense mechanism, continuously monitoring network traffic for suspicious activities and taking immediate action to prevent potential breaches.
By analyzing inbound and outbound traffic, as well as internal data transfers, an IPS provides real-time threat detection and mitigation capabilities. Unlike IDS, an IPS offers automated response mechanisms, reducing the burden on IT teams and ensuring rapid threat response.
Deploying an IPS strengthens the overall security posture of an organization, helping to mitigate risks, prevent unauthorized access, and protect sensitive data.
Conclusion
Intrusion Prevention Systems are steadfast at providing your company with complete protection against intruders. Unlike IDS, IPS not only detects but also prevents malicious activities, ensuring swift response to potential breaches.
By continuously monitoring network traffic and deploying automated mitigation measures, IPS enhances your company’s security posture and reduces risks effectively. Deployed at network edges, data centers, or endpoint devices, IPS serves as a frontline defense mechanism, protecting your sensitive data and infrastructure from cunning cyber attackers.
Consider reading our article on Intrusion Detection Systems, if you haven’t done so already.







