What is Dynamic Code Analysis?
Dynamic Code Analysis, also referred to as DAST, is a security testing methodology that analyzes an application’s behavior while it’s running. Unlike static code analysis, which examines the code itself, DAST simulates real-world scenarios and attacks to uncover vulnerabilities that might not be apparent from just looking at the code.
To understand it better, let’s consider a scenario. Imagine you’re testing a new lock on your door. Static analysis would be like inspecting the lock’s internal components to see if they’re properly designed. Dynamic analysis, on the other hand, would be like trying to pick the lock with various tools and techniques, mimicking how a burglar might try to break in.
Also, there can be some confusion around the term “dynamic code analysis” in security circles. While it might seem like the natural counterpart to static code analysis, dynamic code analysis itself isn’t a widely used term within the security space, and it often refers to the same concept as DAST and it goes beyond just analyzing code.
Why Dynamic Analysis is Critical
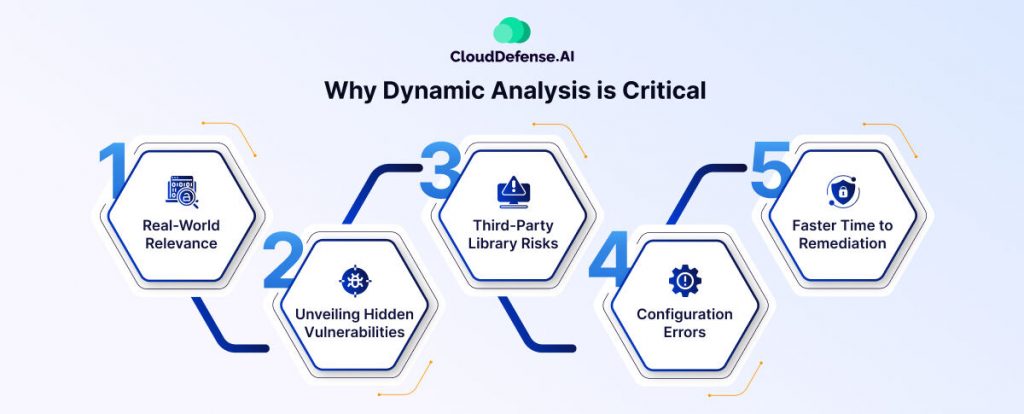
In today’s threat landscape, where cyberattacks are becoming increasingly sophisticated, Dynamic Code Analysis has become a critical tool for ensuring software security. Here’s why:
Real-World Relevance
Static code analysis, while valuable, can miss vulnerabilities that only emerge during runtime. Dynamic code analysis bridges this gap by simulating real-world scenarios, including user interactions and potential attacks. This allows for a more accurate assessment of the application’s security posture.
Unveiling Hidden Vulnerabilities
Certain vulnerabilities, like memory leaks or race conditions, are difficult to detect through static analysis alone. It can pinpoint these issues by monitoring the application’s behavior as it executes, providing a more comprehensive security analysis.
Third-Party Library Risks
Modern software heavily relies on third-party libraries. These libraries can introduce vulnerabilities that might not be readily apparent in your own codebase. Dynamic code analysis can analyze the application’s interactions with these libraries, helping to identify potential security risks from external dependencies.
Configuration Errors
Sometimes, security problems creep in because of mistakes in how the software is set up. Dynamic code analysis jumps in to the rescue by pretending to be our software in a make-believe deployment, sniffing out any configuration errors that could spell trouble later on.
Faster Time to Remediation
One of the coolest things about dynamic code analysis is how it helps us catch vulnerabilities early on, while we’re still developing the software. This means we can squash those bugs before they cause any real harm. Plus, it saves us a ton of time and effort compared to fixing things after the software is already out in the wild.
Static vs. Dynamic Analysis
Static and dynamic code analysis are two mainstays of application security testing, each offering a distinct perspective on potential vulnerabilities. While they may seem like competing methods, they actually complement each other, providing a more comprehensive security assessment.
Static Analysis
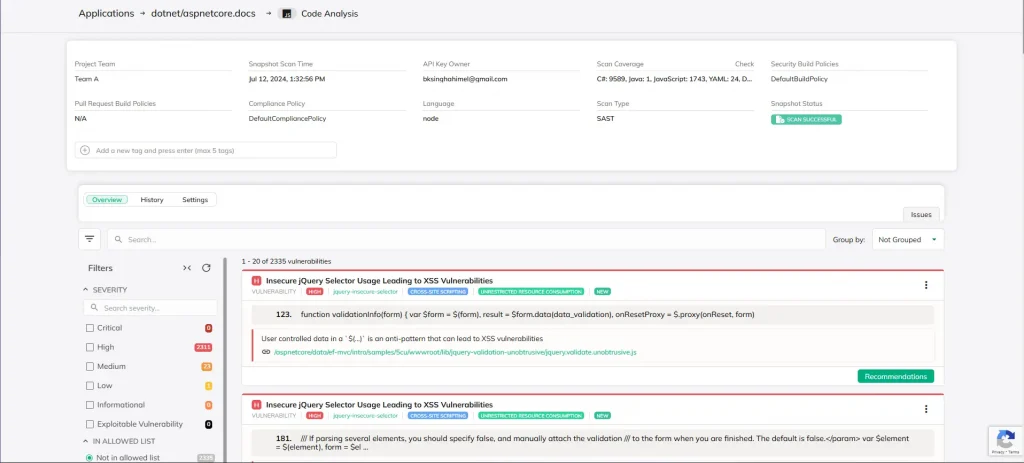
Think of static analysis as a code inspector. It examines the application’s source code, building a map of its execution flow. By applying predefined rules to this map, SAST can identify common vulnerabilities like injection flaws, buffer overflows, and coding errors. Since it doesn’t require a fully functional application, SAST can be integrated earlier in the development lifecycle, allowing developers to catch and fix issues early on.
Dynamic Analysis
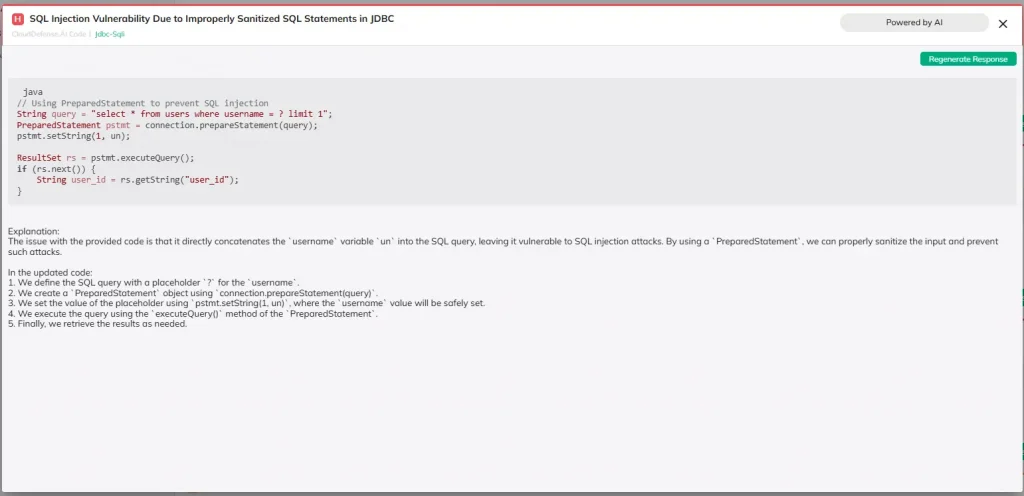
In contrast, dynamic analysis is all about observing the application in action. It simulates real-world scenarios, including user interactions and potential attacks, to see how the application behaves at runtime. This allows dynamic analysis tool to uncover vulnerabilities that might be missed during static analysis, such as configuration errors, memory leaks, and interaction issues with third-party libraries.
Here’s a table summarizing the key differences:
| Feature | Static Analysis | Dynamic Analysis |
| Execution | No code execution needed | Requires code execution |
| Focus | Code structure, syntax, potential coding errors | Application’s runtime behavior |
| Strengths | Fast, efficient, analyzes large codebases | Uncovers hidden vulnerabilities, real-world context |
| Weaknesses | Misses runtime vulnerabilities, prone to false positives | Slower, requires configuration and maintenance |
Dynamic Analysis in the Cloud: Security Testing Beyond Source Code
Traditional code analysis methods often assume access to the application’s source code. However, in today’s cloud-centric world, this isn’t always the case. Many organizations leverage cloud platforms and APIs from various vendors, creating a complex ecosystem where they might not have access to the entire application’s codebase.
This is where Dynamic Analysis in the Cloud (DAST in the Cloud) comes to the rescue. Unlike SAST that scans source code, DAST in the Cloud focuses on the application’s runtime behavior.
Here’s why DAST in the Cloud is a game-changer for cloud-based applications:
Security Testing Beyond Code
DAST in the Cloud doesn’t require access to the source code. It analyzes the application’s behavior as it interacts with users and data in the cloud environment. This allows for security testing even for applications built and deployed by third parties.
Real-World Scenario Testing
DAST in the Cloud simulates real-world attacks and user interactions. This approach helps identify vulnerabilities that traditional code analysis might miss, such as misconfigurations, logic flaws, and API security issues.
Hybrid and Multi-Cloud Support
Modern organizations often utilize hybrid and multi-cloud environments. DAST in the Cloud can seamlessly integrate with these complex cloud deployments, providing a unified security testing approach across different cloud vendors.
Let’s consider an example: Imagine a web application built on a cloud platform like Google Cloud Platform (GCP). Even if you don’t have access to the application’s source code, DAST in the Cloud can analyze the behavior of the application’s API. By simulating user interactions and testing for malicious inputs through the API, DAST can reveal security vulnerabilities that might be missed by traditional code analysis methods.
In essence, DAST in the Cloud empowers organizations to effectively secure their cloud-based applications, even with limited access to the underlying code. It provides a powerful and practical approach to security testing in the ever-evolving cloud landscape.
Bottom Line
The cloud revolution has fundamentally changed how we develop and deploy software. With the rise of cloud-based applications, serverless architectures, and containerization, traditional security testing methods sometimes fall short.
As we’ve explored, both static and dynamic analysis play critical roles in securing your applications. Static analysis provides a solid foundation for early detection of potential issues, while dynamic analysis validates your application’s security posture under real-world conditions.
Cloud security is a complex challenge, but you don’t have to go it alone. CloudDefense.ai offers a comprehensive suite of security solutions specifically designed for cloud-based applications. Our platform seamlessly integrates DAST and SAST vulnerability scanning, providing a holistic view of your application’s security posture. Whether you’re developing serverless applications or leveraging containerized microservices, CloudDefense.ai can help you identify and remediate vulnerabilities throughout your development lifecycle.
Ready to experience the power of CloudDefense.ai firsthand? Schedule a demo to see their solutions in action, or request a free trial to discover how we can seamlessly integrate into your development workflow and empower you to build secure, cloud-native applications with confidence.







