What is Application Security?
Application Security refers to the practices, tools, and measures designed to protect applications from threats throughout their lifecycle—from development to deployment and beyond.
Here’s What Application Security Helps With:
-
- Protects applications from vulnerabilities, including injection attacks, cross-site scripting, and unauthorized access.
-
- Ensures code integrity and secures sensitive data within applications.
-
- Identifies vulnerabilities in the software before they’re exploited.
-
- Secures sensitive data from being accessed by unauthorized users.
-
- Provides continuous monitoring for real-time threat detection and response.
-
- Supports compliance with industry standards like OWASP and regulatory requirements.
-
- Strengthens software by integrating security checks early in the development lifecycle.
At the end of the day, application security is about staying one step ahead. It’s the difference between “safe and sound” and “exposed and vulnerable”—and, let’s face it, in today’s world, it’s a no-brainer.
Why is Application Security Important?
Every app—whether it’s handling banking transactions, health records, or just your daily social media feed—is a potential target for cybercriminals. Weak security opens doors for data theft, loss of user trust, and brand damage.
Let the Stats Tell the Story:
-
- Over 70% of breaches happen because of vulnerabilities in applications.
-
- The average cost of a data breach in the U.S. is now $9.44 million, with breaches involving application vulnerabilities being the most expensive.
Now, let’s break it down with a real-world scenario: Imagine your company builds an e-commerce platform. It’s running smoothly—orders are coming in, customers are happy, and you’re gearing up for Black Friday.
But what if a hacker exploits a vulnerability in your payment system? They inject malicious code, grab customer credit card details, and before you know it, you’re dealing with a massive breach.
It’s not just the immediate loss of data or money—it’s the damage to your reputation, the legal trouble, and the long-term recovery costs. That’s why securing your applications isn’t just important—it’s non-negotiable. It’s the backbone of trust, stability, and survival in an increasingly hostile digital world.
Benefits of Application Security
Securing Sensitive Information
Ever wonder what happens if your app’s sensitive data gets into the wrong hands? Securing sensitive information isn’t just a best practice—it’s a must. Whether it’s user passwords, credit card numbers, or personal details, this data has to be locked down.
Encryption and secure storage are key to making sure only the right people can access it. Without proper security, all that information is at risk. And when it’s gone, it’s gone.
Fixing Misconfiguration
Misconfiguration is one of the most common vulnerabilities in application security. It’s like leaving the door to your house wide open without realizing it. Have you checked your app’s settings lately?
Things like incorrect permissions, exposed databases, or unused features left running can create serious risks. Fixing these small mistakes can save you from big problems. It’s about making sure your app is locked down at every level.
Minimizing Breaches
Nobody wants a breach, but if it happens, the faster you can spot it, the less damage it’ll cause. Minimizing breaches starts with preventing them in the first place. By testing your app for vulnerabilities, you’re identifying potential weaknesses before they’re exploited.
But even with the best defenses, breaches can still happen. That’s why it’s essential to have a solid response plan and tools in place to limit the damage. If your app is breached, how fast can you get it back under control?
Staying Compliant
Regulations are getting stricter every year. GDPR, HIPAA, CCPA—these laws are here for a reason. They’re designed to protect user privacy and ensure businesses handle data responsibly. If your app isn’t compliant, the penalties can be severe. Beyond that, it’s about building trust.
When users know their data is being handled securely and within the law, they’re more likely to engage. Application security helps you stay compliant while also protecting your reputation.
Code Analysis
Writing secure code isn’t just about functionality; it’s about thinking ahead. Is your code vulnerable to injection attacks? Does it leak sensitive data in unexpected ways? Regular code analysis is essential to identifying these risks before they become problems. Automated tools can catch some issues, but human oversight is key. After all, the safest code is the one you’ve thought about from every angle.
| Did you know? In 2023, nearly 1.7 billion records were exposed due to data breaches related to application attack surfaces. |
The Application Security Process
The application security process isn’t just a one-time checklist. It’s a continuous cycle that involves identifying risks, building defenses, testing them, and keeping things secure over time. Think of it like a fortress—just because the walls are up doesn’t mean you stop watching for weaknesses. Here’s how it all breaks down:
Identifying Risks and Planning Ahead
The first step is identifying what could go wrong. It’s like a preemptive strike—mapping out potential threats before they even get a chance to show up. This phase is about understanding the app’s functionality, data flow, and where attackers might try to break in. Threat modeling is crucial here. It helps teams focus on the risks that matter most, so they can develop a tailored security plan. What vulnerabilities exist in your app, and how can you tackle them head-on?
Building Security into the Design
Once you know where the risks are, the next step is to design your app with security baked in from the start. During development, teams follow secure coding practices to ensure that vulnerabilities aren’t accidentally coded in. Think input validation, strong authentication, proper error handling—these are all non-negotiables. Security should never be an afterthought. By making security part of the design, you’re building resilience from day one. So, how secure is your code before it even hits the production environment?
Thorough Code Checks and Testing
Now, it’s time to inspect and stress-test the code. This is where flaws get caught—before they become exploits. Code reviews and testing play a critical role in finding hidden vulnerabilities. Static code analysis looks for weak spots in the code, while dynamic testing simulates actual attack scenarios to see how the app holds up. The goal is to spot weaknesses, fix them, and keep iterating.
Evaluating Security Through Real-World Testing
Once the code is solid, security testing steps in to make sure everything works as intended. This phase is all about verifying that the security controls are in place and functional. Penetration testing, vulnerability scanning, and red teaming are used to simulate attacks and identify any gaps. Compliance with industry standards and regulations is also checked, ensuring that the app meets all security requirements. Are you testing the limits of your security, or just assuming it works?
Deployment and Monitoring
Deployment is just the beginning. The real work starts after the app is live. Constant monitoring is key to ensuring long-term security. Logging and monitoring tools keep track of any unusual behavior, so you can respond quickly to incidents. But it doesn’t stop there—regular security patches and updates are essential to keeping up with new vulnerabilities. Is your app still secure post-launch, or have new threats emerged that need attention?
Application Security Trends 2025
In 2025, organizations saw a massive inflow of complicated and sophisticated cyber attacks that had a huge impact on applications. To counter it, different application security trends have emerged, and they are:
Increasing Importance of Software Supply Chain Security
After the Log4J attack, there is an increase in demand for software supply chain security. Organizations are implementing security measures to discover gaps and enforcing advanced security measures at every stage of the supply chain. It is preventing attackers from exploiting faults in open-source repositories and links in the supply chain.
Rise of ASPM Technology
In 2025, application security posture management is garnering a lot of attention as securing cloud infrastructure is getting more complex. Attackers are coming up with modern and sophisticated ways to infiltrate the cloud-native applications, making application security more complex. ASPM is making things easier for organizations and enhancing overall security.
Cloud Security Takes Center Stage
With more applications running in the cloud, ensuring security at every level—from code to cloud configuration—is a must. Infrastructure-as-Code (IaC) and application security testing are becoming essential components of cloud security. If your cloud setup isn’t secure, your whole app is at risk.
CISO Joining Executive Committee
In 2025, the Chief Information Security Officer (CISO) is no longer just an advisor but a key decision-maker in the executive team. With cybersecurity becoming a national priority—especially in the wake of political conflicts like the Ukraine war—CISOs are tasked with safeguarding not just data, but entire infrastructures. But with limited resources, they’ll need to get creative with technology and strategies.
What are the Challenges of Modern Application Security?
Modern application security has evolved in many ways, but despite all the advancements, it still faces many challenges globally. Here are some crucial challenges faced by modern application security:
Inherited Vulnerabilities
One of the biggest headaches in app security is inherited vulnerabilities. No matter how vigilant developers are, some security gaps exist by default. Software is a living, evolving ecosystem, and as it grows in complexity, hidden cracks inevitably emerge. Legacy code is a classic culprit here—it’s outdated, can’t keep up with modern threats, and security teams must prioritize rooting out these weak points to maintain stability.
Lack of Relevant Skills
There’s a major talent gap when it comes to cybersecurity, especially in application security. Every company wants experienced professionals, but the reality is the demand far outpaces the available talent. To bridge this gap, many companies hire fresh grads to secure applications, which can lead to gaps in expertise and experience. Without highly skilled hands on deck, application security can feel like a race against an impossible clock.
Legacy Security Approach
A surprising number of organizations still rely on outdated, “scan-at-the-end” security tactics. But modern development is all about speed and agility. Today, security needs to start early—what’s known as the “shift-left” approach, where security is baked in from day one. Ignoring this means risking blind spots that attackers love to exploit.
Dependence on Third-Party Libraries
Developers today rely heavily on third-party and open-source libraries, which—while convenient—come with baggage. These libraries can be a goldmine for hackers if they contain vulnerabilities. Older, unmaintained libraries are especially risky. Setting policies and using robust scanning tools to catch these risks early on is key to ensuring that outside code doesn’t create inside problems.
Lack of a Comprehensive Vulnerability Tool
Despite huge leaps in security tech, we still lack a one-size-fits-all tool that identifies every possible vulnerability. Security teams have to juggle multiple tools to get full coverage, and that adds to complexity. Plus, new zero-day vulnerabilities pop up regularly, keeping security teams in a constant scramble.
Absence of Centralized Management
Not all application security comes with a centralized dashboard, and this prevents security teams from constantly monitoring application security posture. Having centralized management will enable security teams to address backlogs in a timely manner and track various metrics.
Insider Threats
Insider threats are one of the biggest challenges to application security as they are unknown vulnerabilities and can jeopardize the overall security. The application security renders useless when an insider threat occurs.
OWASP Top 10 Application Security 2021: Highlights
Given the complex set of application security challenges listed above, the OWASP Top 10 stands as a valuable guide for prioritizing and addressing the most critical vulnerabilities. Updated every few years, the OWASP Top 10 is a community-driven standard that highlights the most common and severe security risks facing modern applications.
CloudDefense.AI can serve as a valuable solution to most of the issues. Here are the highlights of the top 10 application security risks:
1. Broken Access Control: Broken access control is a severe risk to application security as it will allow attackers to get entry to all the assets of the application, infrastructure and other assets.
2. Cryptographic Failure: The lack of encryption or any kind of error in the encryption can make all the sensitive data in the application exposed to attackers.
3. Injections: Injection attack is an advanced attack that mostly occurs when the attacker runs malicious code, and the application is unable to distinguish between user input and its own code. It allows an attacker to obtain sensitive information from the database.
4. Insecure Design: Insecure design highlights design and architectural flaws that appear when security isn’t implemented from the start of the development.
5. Security Misconfiguration: Access control misconfiguration is a major issue that allows attackers to easily access sensitive customer information. Use of default credentials, inappropriate permissions, misconfigured HTTP headers and unnecessary feature activation are some common security misconfigurations.
6. Vulnerable and Outdated Components: Every modern application utilizes third-party components that have code which is not supervised by the organization and it leads to many security issues. When a vulnerability appears in a component, it can jeopardize the security application and allow attackers to gain access to the database.
7. Identification and Authentication Failure: Any improper implementation of function associated with session management and user authentication leads to vulnerability. The vulnerability usually causes exposure to security details, enabling users to impersonate, and gaining excess privilege.
8. Software and Data Integrity Failure: When an attacker interferes with the application or its associated database, it can cause a failure in the integrity of the software and data. Such failures also affect other components to not recognize their integrity.
9. Security Logging and Monitoring Failure: Absence of effective security logging and monitoring function can lead to a security breach. This aspect of OWASP top 10 helps organization to focus on identifying and resolving such security incidents through logging and monitoring.
10. Server-Side Request Forgery: It is a serious vulnerability that recently came into the limelight. Through this vulnerability, an attacker can utilize an unauthenticated URL to get access to data on a remote resource. It mostly happens when their user input is not validated from the server side.
Types of Application Security Scanning Tools
When it comes to application security, scanning tools serve as an essential component that enables developers to properly assess the application. However, this tool isn’t of a single type, and you will come across different types of application security scanning tools having unique scanning capabilities. Here are six scanning tool types:
Static Application Security Testing
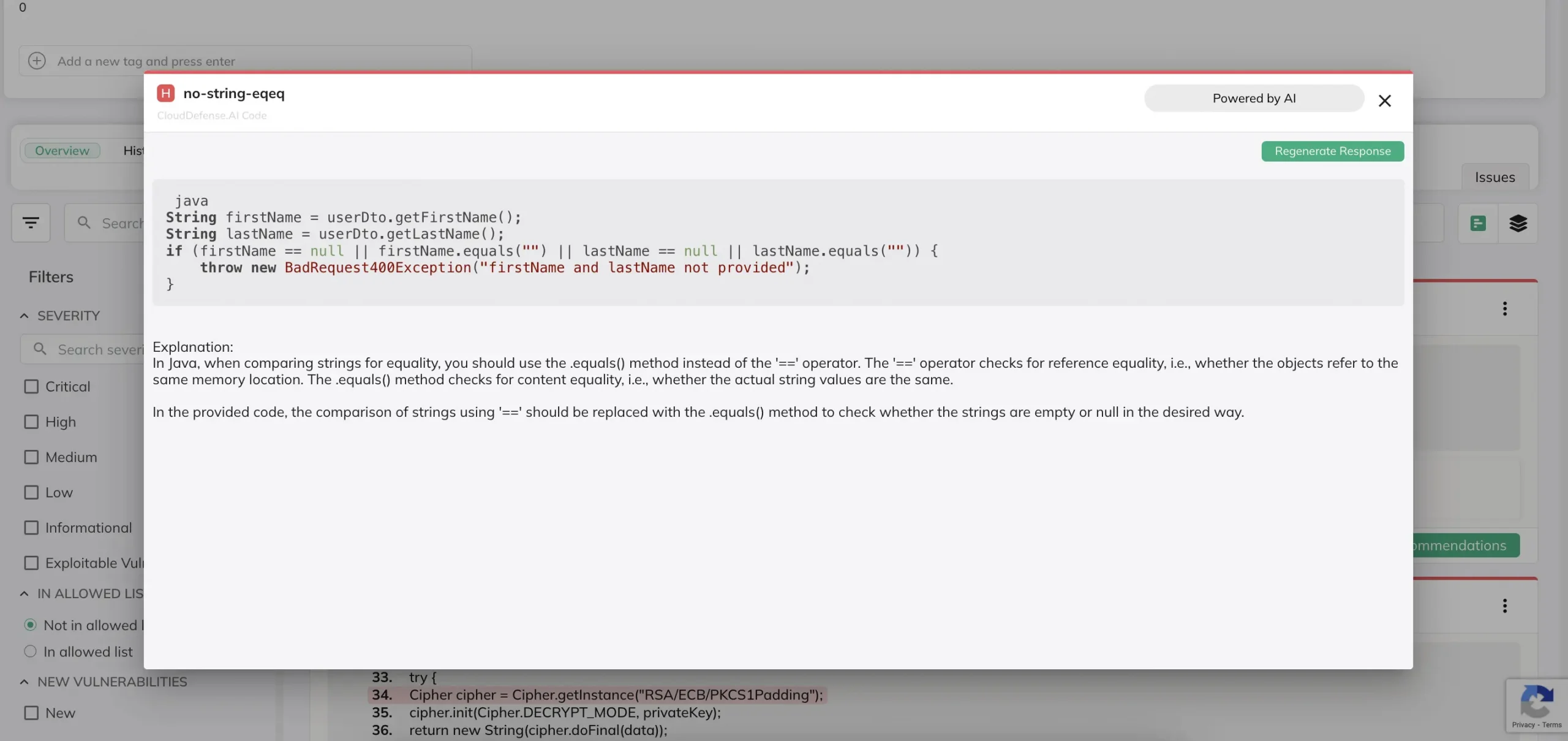
SAST tools dive deep into your source code, looking for vulnerabilities before your app even runs. They’re like a pre-flight check for your software, scanning line-by-line to catch issues early in development. This tool is a developer’s best friend because it helps spot security flaws during the coding stage, making fixes faster and more cost-effective.
Dynamic Application Security Testing
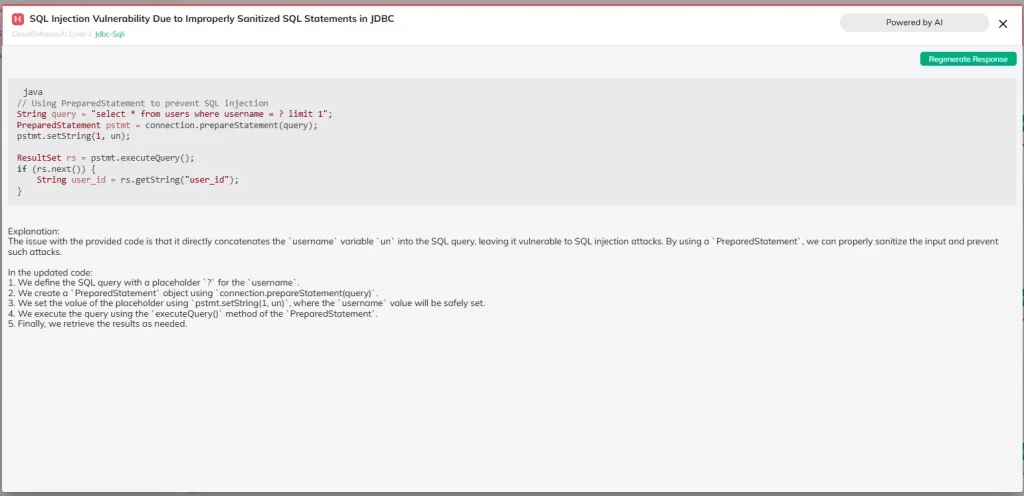
DAST tools are like stress tests for your live applications. Instead of analyzing static code, they simulate attacks on a running app, searching for vulnerabilities as they appear in real-time. Think of it as a controlled attack against your app, allowing you to catch weaknesses hackers would exploit in the wild.
Software Composition Analysis
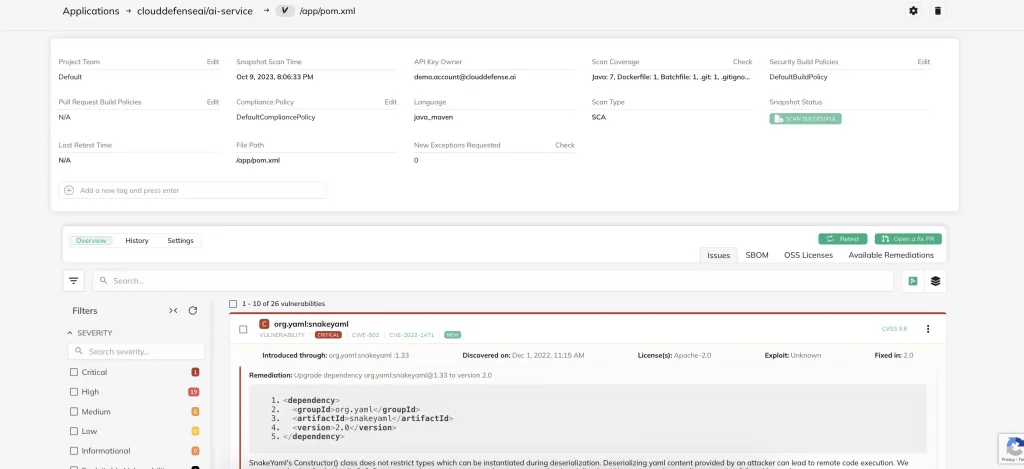
Nowadays, nobody builds an app completely from scratch. Developers pull in libraries and packages from open-source repositories, which means you’re inheriting potential risks. SCA tools scan these components for known vulnerabilities, helping you spot outdated or vulnerable third-party code before it’s too late.
Infrastructure as Code (IaC) Scanning
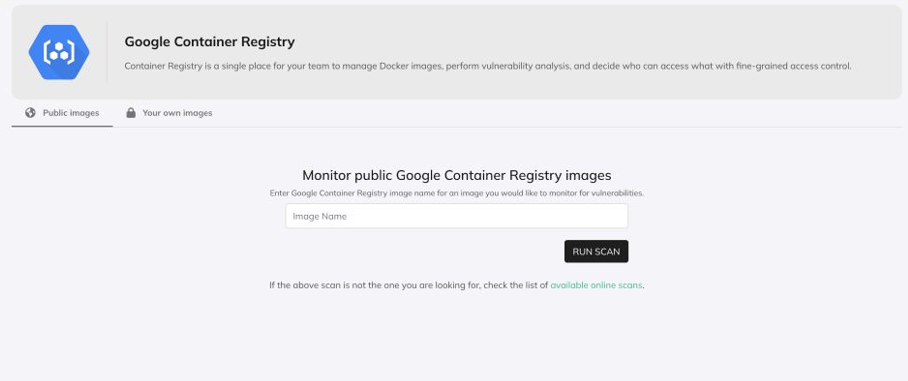
IaC tools scrutinize the code that sets up your infrastructure. As infrastructure increasingly moves into code (think cloud environments), these tools catch misconfigurations early, ensuring your foundation is as secure as the applications running on it. It’s like building a fortress with blueprints designed to withstand attack from day one.
Container Security
Containers make app deployment fast and efficient, but they come with unique security needs. Container security tools monitor and protect the entire container ecosystem, from the images you use to runtime behaviors. These tools keep your microservices clean and secure, defending against attacks targeting container vulnerabilities.
API Security
APIs are the connective tissue of modern applications, and with that flexibility comes exposure. API security tools protect these gateways, monitoring for unauthorized access, injection attacks, and other threats unique to APIs. They’re essential as businesses increasingly rely on APIs to integrate services and share data, making sure nothing slips through the cracks.
How CloudDefense.AI Helps With Application Security
All these tools and solutions we’ve just outlined come together in CloudDefense.AI’s CNAPP suite—alongside a full set of cloud security solutions. It’s an all-in-one package that covers security from code to cloud. This means you get a unified approach to securing every layer of your application, from the development stage to production.
But here’s where it gets even better: CloudDefense.AI doesn’t just flag vulnerabilities; it provides automated remediation guidance for each tool, making fixes faster and more straightforward. And with attack path analysis, it doesn’t stop at showing you the vulnerability—it maps out potential attack pathways, helping you proactively address weak spots before attackers get a chance.CloudDefense.AI offers the ultimate DevSecOps suite for application security, all in one platform that evolves with your needs. Ready to see it in action? Book a free demo today and take the first step toward securing your applications, end-to-end.







