What is Operational Technology (OT)?
Operational technology or OT is the hardware and software that are used to detect, monitor, and control devices, ICS systems, and physical processes associated with manufacturing, and gas. Electricity and similar industries.
The main focus of operation technology is to maintain seamless functioning of all the critical infrastructure and industrial environment. It also helps in automating the operation of various machines through designated protocols and tools for building connections with proprietary and legacy systems.
OT encompasses a wide variety of frameworks that include physical access controls, programmable logic controllers, transportation systems, process control domains, distributed control systems, supervisory control, building management, and others.
Unlike IT systems, operational technology is designed to interact with the physical system, devices, and infrastructures in real time. Even though OT is mostly about controlling machines, it also helps in smarter and more efficient operations with better safety and lower operation costs.
What is OT Security?
Operation technology security indicates the practice, strategy, and technology that are employed to protect the industrial control system (ICS), hardware, and software associated with OT infrastructure. OT security has become a key component of security strategy as it facilitates protecting the uptime, security, and availability of industrial systems, processes, and machines.
The increasing demand for the Industrial Internet of Things (IIoT) and a huge number of cyber attacks targeting industrial components have made OT security an important requirement. From oil, gas, food, mining, and petrochemical industries to power plant operators and automobile industries, everyone is opting for OT cybersecurity to safeguard the technology, system, and other assets of OT from modern threats.
These threats to OT systems not only can cause major operation disruption but also lead to financial loss and life risk. This security solution is designed with a centralized interface through which OT teams can access and control all the hardware while having a comprehensive view of the entire infrastructure. Thus, OT teams can easily identify and mitigate cyber threats related to the OT systems before they can make any impact.
What are the Components of Operational Technology?
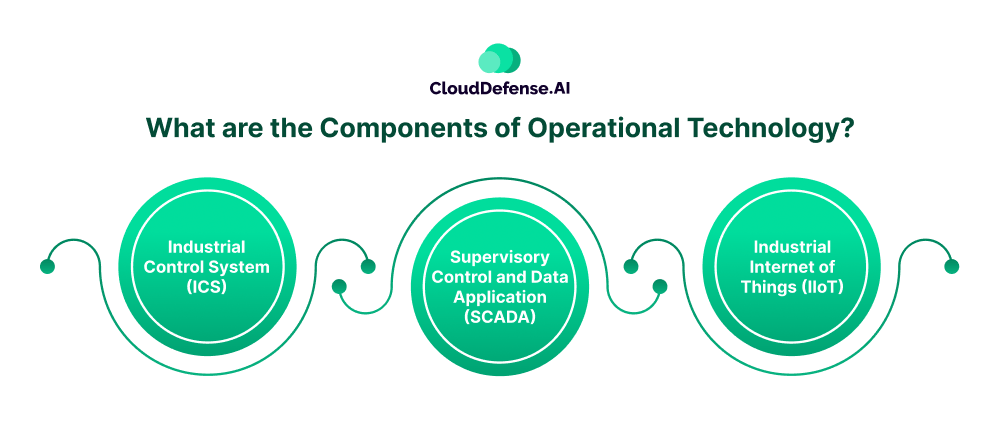
Operational technology is made of various components and each component needs to work together for seamless functioning. Here are the primary components that fill up the OT environment:
Industrial Control System (ICS)
ICS serves as one of the primary pillars of operational technology as ICS includes all types of controls, devices, networks, and systems that are responsible for facilitating different industrial processes. Basically, it indicates the physical functioning of all the hardware components that operate together.
ICS makes sure every machinery, device, and equipment of a particular industry like wastewater treatment or manufacturing plant works at their peak performance while maintaining optimum safety of the staff.
Supervisory Control and Data Application (SCADA)
Also abbreviated as SCADA, it serves as an information component of OT where this system collects all the data from sensors from both on-premises and distributed sites and relays it to the central management.
It serves as a subset of ICS offering a centralized management through which OT teams can manage every aspect including tracking equipment status and making changes to hardware settings.
Industrial Internet of Things (IIoT)
IIoT is the smallest component of operational technology and it indicates the IoT devices that are used in different industrial settings. IIoT devices are widely used in industrial environments to enhance efficiency, meet operational needs, and overcome environmental constraints like heat, moisture, and dust.
IIoT comprises devices like sensors, actuators, and other technologies that are used to collect, monitor, and analyze various types of data from different operations for troubleshooting, maintenance, and enhancing efficiency. IIoT is also used for quality control, supply chain management, inventory management, routine maintenance, process management, and many other ways in industrial settings.
IT vs OT
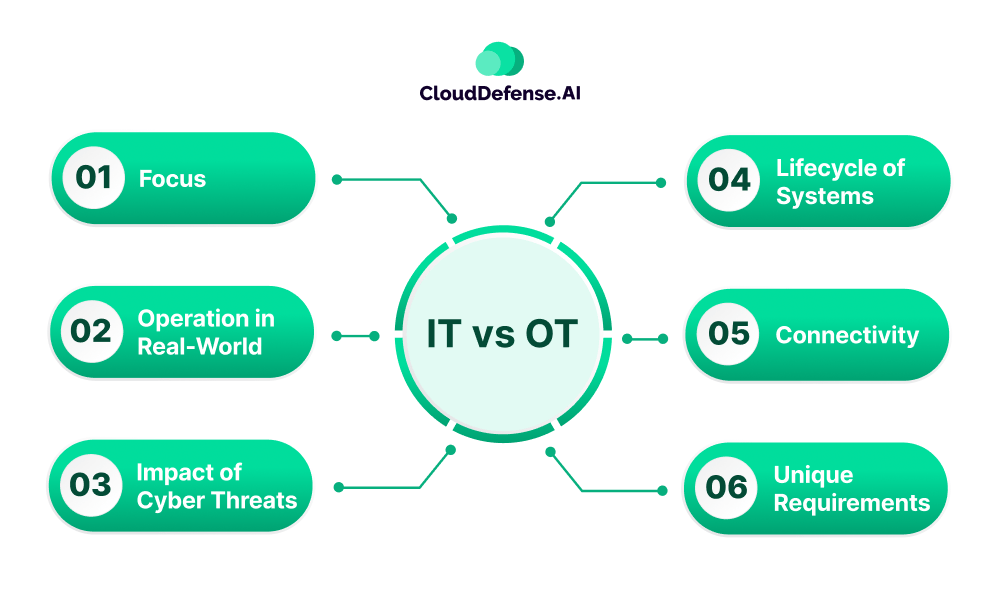
When understanding OT security, it is important to understand the difference between IT and OT. Even though operational technology shares many similarities with information technology, there are certain aspects that make it different from each other. Let’s explore those differences:
Focus
Information technology is all about managing, protecting, and storing data whereas in operational technology the focus is on maintaining, managing, and controlling physical devices and processes. Since OT systems are mostly associated with critical infrastructures and manufacturing plants, efficiency is given more priority which is not the same in the IT world.
Operation in Real-World
OT and IT also differ in how they operate in the real world as IT devices mostly serve as tools for humans whereas OT devices are designed to interact with industrial machines. OT devices offer a centralized console that enables OT teams to monitor and control the devices used in different industrial settings.
Impact of Cyber Threats
When a cyber threat affects the OT devices, it not only jeopardizes the whole operation, and damages equipment but also leads to process fluctuation, impacts on business, and risks human life. On the other hand, a cyber threat on IT only impacts the business continuity and it is recovered with effective mitigation steps.
Lifecycle of Systems
Usually, the lifecycle of OT systems tends to span from 15 to 30 years whereas the lifespan of an IT system is a maximum of 5 years. Importantly, OT systems are part of large industrial infrastructure and they are rarely or never stopped to maintain continuity.
Connectivity
The connectivity mechanisms involved in the IT world are mostly Wi-Fi and Telco whereas the OT system utilizes a varied range of connectivity. OT environment usually involves WiFi, radio signal, satellite, Telco, and powerline carrier.
Unique Requirements
OT devices mostly rely on proprietary operating systems and tools that are not based on traditional frameworks. The updates to the system in the OT world are infrequent and security patching is done rarely. However, this is not the case with IT devices as they are based on a common OS and get frequent updates to improve functionality and performance.
What is IT-OT Convergence?
IT-OT convergence refers to the process when IT and OT devices are connected with each other within the same environment. For decades, IT and OT devices have been operating separately and they never shared any interdependencies. However, the need for increasing efficiency and digital innovation made OT systems converge with IT systems.
Moreover, OT systems run on legacy OS which makes them vulnerable to attack, and a security breach can disrupt the complete operation. As a result, OT systems were air-gapped from IT networks when they were connected to any network.
However in recent times, things have changed as nowadays, it has become for OT systems to be configured with IIoT devices and various computation technologies. The introduction of IIoT devices has enabled OT teams to remotely monitor and control the OT systems from a centralized location, resulting in an increase in efficiency and productivity.
The introduction of IIoT has also enabled the exchange of data from sensors, actuators, and other equipment to applications. Due to this integration, OT systems have achieved a better flow of information, automation in processes, enhancement in management, and better adherence to compliances.
Effective OT Security is not Negotiable
Operational technology security is responsible for safeguarding the uptime and continuity of processes of various critical infrastructure and industrial environments. From water service, emergency services, and gas transmission to traffic management and food production, many critical infrastructures are dependent on OT security for seamless operation.
When a cyberattack impacts an OT device or system, it leads to severe consequences. If an attacker breaches the OT system and makes changes to the traffic system, then it can lead to accidents on the road.
The recent convergence of OT and IT has made OT networks a new target for cybercriminals as they aren’t really hard to attack. Besides, cyber criminals and state-sponsored attackers are also targeting operational technology enterprises with modern attacks.
A recent report from Fortinet has stated that OT security risks have become a concern for many organizations and around 75% of OT organizations have massive amounts of malware attacks in a year. This rapid rise in attacks has affected productivity, efficiency, brand trust, physical safety, and revenue for OT organizations.
Choosing an OT Security Vendor For Your Organization
In modern times, choosing an OT security vendor has become a tricky task for many organizations.
With the OT cybersecurity market reaching a market cap of around $24 billion and an increasing number of vendors, the organization often gets confused. Here are certain tips that you need to keep in mind while choosing an OT vendor:
- Make sure the OT security vendors understand and completely cover the OT protocols.
- The vendor secures both wireless and wired access to the OT system and follows best practices to safeguard the network.
- The vendor must be able to identify all the OT assets, classify them, and prioritize which assets require more safety.
- You will have to check whether the solution comes with the capability to analyze all the network traffic for threats and vulnerabilities.
- All efforts should be made to segment the network dynamically.
- Ensure the OT security vendor offers both detection and mitigation capability.
- Try to opt for a vendor offering native OT security threat intelligence feed which will enable you to mitigate threats before they can affect you.
- Always opt for a vendor whose OT security solution seamlessly integrates with your environment and has a clutter-free centralized dashboard.
- An OT security vendor with comprehensive compliance support will be an ideal choice as it will help in adhering to requirements.
- The solution must be able to offer support across hybrid environments and integration with various other security technologies and devices.
- The vendor must be able to offer the facility to control identity and access management.
What are the Primary Differences Between OT and IT Security?
In terms of security, operational technology and information technology differ from each other in many ways. Here we will compare how OT and IT security are different:
| OT Security | IT Security | |
| Approach | OT security is aimed at protecting physical OT assets in a critical infrastructure and industrial environment. | IT security is focused on protecting data and maintaining availability, integrity, and confidentiality of data. |
| Uniqueness | OT security are custom built and they are designed in such a way they serve specific devices, processes, or manufacturing plants. | IT security is a comprehensive solution and they integrate easily with most platforms whether it is cloud or traditional environment. |
| Impact of Security Breach | When a hacker breaches unprotected IoT equipment in an OT facility, it can get access to a centralized system and control different aspects of a machine or system. | When a hacker breaches the security perimeter of an IT device or network, it can only steal the data but can’t control the settings and functions. |
| Number of Incidents | The number of attacks on OT facilities is limited due to the lower number of gateways. However, a single breach can lead to a destructive outcome. | IT facilities face a lot of security threats on a daily basis due to numerous endpoints and entry points. The motive of the attack is usually stealing data for financial gains. |
| Identifying Assets For Protection | OT teams need to decode packet payloads and assess the communication packet to identify OT assets and anomalies associated with it. Protocols like Modbus, NTCIP, CC-Link, Profinet, etc are utilized for securing industrial networks. | IT security can easily identify assets for protection through various solutions. |
| Security Patching | Security patching OT components is a tricky task as OT teams have to completely shut down all the equipment. In most cases, security patching is done every ten years at a stipulated time. | IT security gets frequent updates and most IT vendors patch any security issue whenever they are reported. |
Why is OT Cybersecurity Important?
As the boundary between information technology and operational technology is gradually blurring, the number of cyberattacks on OT systems is increasing gradually. The integration of IoT devices into industrial equipment and processes has enabled attackers to launch cyberattacks and take control of OT systems.
OT devices, ICS sensors, and instruments used in a critical infrastructure are connected to the OT network, as a result, attackers get the opportunity to exploit the attack vector and harm critical infrastructure. The convergence of IT and OT environments also led to a complex network and it created a gap where the OT team couldn’t have complete visibility into all the equipment.
Nowadays, most critical institutions like government infrastructure, hospitals, manufacturing plants, transportation, etc utilize OT systems. Invariably solid OT cybersecurity is important for every organization dealing with OT systems as it will not only protect the uptime and availability of OT systems but also ensure optimum safety.
When you implement OT security, it will prevent OT malware from disrupting any critical process or equipment. Moreover, it prevents many other consequences like injuries to staff, environmental disasters, water shortages, food supply-chain disruption, damage to installation, criminal liabilities, and others. Another factor that makes OT security important is that it helps organizations adhere to various industrial compliance requirements.
The Need to Converge IT and OT Network Security
IT and OT networks are two different components in an organization and this disparity prevents security teams and administrators from getting a 360-degree view of the organization’s ecosystem.
Moreover, OT teams report to the COO of the organization whereas IT networks report work under the CIO of the organization. Thus each team is restricted to a certain part of the ecosystem which divides their security and threat management effort and makes it daunting for them to offer an all-around protection against cyberthreats.
As a result, the need to converge IT and OT network security has become imminent for every organization as it will enable the organization to have a holistic security approach. It will allow the security team to offer effective security measures across the IT and OT network and prevent any threat from impacting the ecosystem.
OT Security in Operational Environments
OT security plays a significant role in protecting components of the operational environments and ensuring every OT device that is part of IIoT is protected. An OT system includes a variety of components like sensors, monitors, industrial robots, generators, actuators, PLCSs, and various others that are associated with IIoT.
Besides, an operational environment also includes numerous critical machinery which if impacted by cyberattacks can lead to severe consequences including human life risk. A press release made by Gartner indicated that cybercriminals will come up with sophisticated attacks by 2025, allowing them to weaponize OT devices to harm human beings in a physical way.
Operational environments in industries like manufacturing, utility, and resources should focus more on threats to the environment and humans rather than information. OT security serves as an effective solution that can be effective against real-world hazards and ensure OT devices are under the control of the administrators.
Operational Technology Security Best Practices

With the convergence of IT and OT in the industrial environment, traditional security measures of OT security are no longer effective. So what can be done? Securing the OT systems, processes and environments requires the implementation of certain OT security best practices and they are:
Discover OT Assets
To offer comprehensive OT security to the OT networks, organizations need to discover all their OT assets and get complete visibility into every component in the network in real time. OT networks are vast as they spread over multiple geographical locations so it becomes necessary to have control over every asset connected to the network and build a robust OT security strategy.
Monitoring for Suspicious Activity
One of the best ways to maintain the optimum security posture of the OT system is by monitoring the entire network for suspicious activity. The OT network along with service provider and vendor traffic should be monitored in real-time as it will enable identify anomalies or suspicious traffic that can lead to cyber threats.
Apply Network Segmentation
Traditionally, OT networks are always physically disconnected from IT networks for protection and this gap makes it difficult for cyberattackers to exploit OT assets. However, the convergence of IT and OT networks is making OT assets vulnerable to attack.
Organizations must implement a network to replace the air gaps which will isolate OT assets within the network. Besides, network segmentation will also help in implementing OT-specific firewalls that will help the team assess the network for malicious content and access controls across the network.
Deploying OT Threat Prevention
One of the effective ways to secure OT assets in real time and reduce false positives is by deploying OT threat prevention. This secure practice will not only help the OT security team actively detect threats in the OT network but will prevent incorrect blocking of legitimate operations due to suspected malicious activity.
Implementing Zero Trust Framework
Another best practice you should employ is implementing a zero-trust framework where the OT security will assume every device, process, and network is a threat until they are authenticated. Adopting multi-factor authentication is a vital aspect of the zero-trust framework and makes sure only authorized entities are able to access the OT systems.
Opt for Microsegmentation
It is a good practice to implement micro-segmentation instead of traditional network segmentation. Microsegmentation prevents any malicious devices or entities including insiders from getting control of the centralized application console they are not authorized to access.
Utilize Identity and Access Management
Identity and access management is important for the modern OT environment as it will prevent unauthorized access by cyber attackers. Implementing IAM is a necessity because a security breach can lead to physical impact.
Provide Security Teams with Updates on Global Events of IT and OT World
To effectively detect and respond to security threats, security teams need to be exposed to the global threat landscape and get updates on cybersecurity events. Having the information on current events and support of security solutions, security teams can easily investigate the OT domains for possible threats and prevent them before they can make any impact.
Educate Staff in the OT Domain
It is important for OT administrators to conduct training and educate all the staff handling OT systems regarding different types of threats that can affect the OT environment. They should understand the potential vector of most of the possible threats and how they can be mitigated with proper remediation steps.
Challenges to OT Security
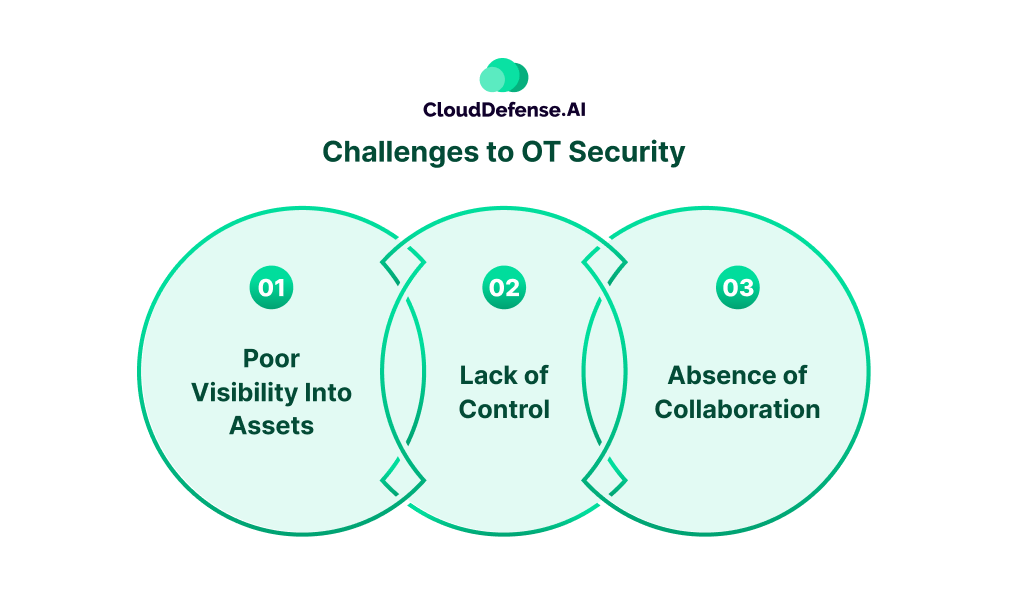
Historically, OT assets have always been isolated from the internet but the deployment of Industry 4.0 technology and communication with cloud and IT networks is making them exposed to cyber threats. Here are some challenges modern cybersecurity threats are facing:
Poor Visibility Into Assets
Most organizations don’t keep an up-to-date inventory of all their OT assets and some assets were installed decades back making them difficult to protect. Due to a lack of visibility into assets, it becomes difficult for security teams to analyze for exposure to malicious traffic, vulnerability misconfigurations, and other issues. As a result, it makes a lot of critical assets vulnerable to attack and it can be utilized by hackers for control over the system.
Lack of Control
Even though network segmentation is followed in most industries, still there are many networks that are left unsegmented, allowing malicious traffic to spread easily. Nowadays remote access through software or other gateway has become a choice for many but not all solutions can analyze communication protocols used by OT assets. Due to this security solutions can’t detect any potential threat that would affect the OT system.
Absence of Collaboration
The absence of collaboration between IT and OT departments and the lack of expertise of IT teams on operations and process control of technology makes it difficult for robust OT security. On many occasions, OT teams don’t offer much security to the network which also makes a severe impact on the organization’s security.
Final Words
Operation technology security has become a key aspect of organizations with critical infrastructures, manufacturing plants, and other related infrastructure. Not only helps them safeguard the OT systems from cyber threats but also ensures operation continuity, integrity, and safety.
In this article, we have discussed all the aspects associated with OT security to make sure you get a better understanding of OT security when you decide to implement it. The convergence of OT and IT environments has made OT security a necessary part of security strategy more than ever.







