The cloud has transformed business operations, offering unmatched flexibility, scalability, and cost savings. Yet, as cloud adoption grows, so do the risks, threats, and challenges to digital security.
This article explores 15 top cloud security issues every organization should address to protect sensitive data. Together with listing down the issues we will also cover the best mitigation strategies that your company can use,
Cloud Security: Risks vs Threats vs Challenges
The terms risks, threats, and challenges often get mixed up, but each represents a unique angle on cloud security. Before we dive into the biggest cloud security issues, let’s clarify the differences for you.
- Risk is a vulnerability or weak spot that could lead to a security breach, like an unpatched system or a misconfigured access point.
- Threat refers to any actor or attack that could exploit that vulnerability, from cybercriminals to malware.
- Challenge describes the obstacles your organization faces in building and maintaining robust cloud security—such as resource limitations, complex configurations, or balancing security with user accessibility.
Learning about these differences, can help you prepare better for, detect, and respond to potential issues in the cloud.
Is the Cloud Secure?
Concerns about cloud security are understandable, especially when sensitive data resides outside company walls. However, cloud storage often provides stronger security than local devices.
Cloud providers use advanced encryption, which means data can only be accessed with a unique digital key, keeping unauthorized users out. Furthermore, data is spread across multiple servers and backed up redundantly, so even if one server fails or a cyberattack occurs, data remains safe and accessible.
This structured methodology helps ensure that your information is resilient against potential threats. So, while data security is always a priority, the cloud’s built-in protections make it a highly secure option for storing and managing sensitive information.
5 Cloud Security Risks
As organizations increasingly turn to the cloud, they also face various security risks that require constant vigilance. Common cloud security risks include data breaches, misconfigurations, human error, an uncontrolled attack surface, and API vulnerabilities. Each of these can lead to serious consequences, from reputational damage to financial loss.
Data Breach
Data breaches occur when unauthorized parties gain access to sensitive information, posing significant financial and reputational risks. In cloud environments, data breaches are especially concerning due to the high volume of sensitive information stored, such as PII (Personally Identifiable Information) and proprietary business data. These breaches may result from weak access controls, misconfigured storage, or compromised user credentials.
Data Breach Example
In 2018, a major data breach occurred at Uber due to an improperly secured AWS bucket, exposing over 57 million records of both customers and drivers. The misconfiguration lacked both encryption and access restrictions, allowing hackers to access the stored data.
Mitigation Strategies
- Implement strong encryption methods for data both in transit and at rest.
- Use multi-factor authentication to strengthen access controls.
- Conduct regular security audits to identify vulnerabilities and tighten permissions.
- Employ data loss prevention tools to monitor and secure sensitive information.
Misconfigurations
Misconfigurations happen when cloud resources are set up without adequate security protocols, leaving them open to exploitation. These errors are common, especially in multi-cloud environments where each platform has unique security requirements. Misconfigurations often result in open data storage, unprotected applications, and unauthorized access.
Misconfigurations Example
A misconfigured cloud database on a large retail platform allowed unauthorized public access, exposing millions of customers’ payment data. Attackers easily exploited the misconfiguration, leading to customer information being compromised.
Misconfigurations Mitigation Strategies
- Automate security configurations with tools like CloudDefense.AI’s CSPM, which regularly scans for and remediates misconfigurations.
- Establish standardized security protocols across all cloud platforms.
- Regularly review and update configuration settings, especially after new deployments.
- Provide ongoing training for administrators to understand each platform’s specific security features.
Human Error
Human errors, from accidental sharing of sensitive information to improper access control settings, remain a major security risk in cloud environments. Simple mistakes can lead to major breaches, as cloud services rely heavily on user input for setup and management.
Human Error Example
A finance company accidentally exposed critical financial documents due to an employee’s misstep while managing a cloud storage service. This minor human error led to the exposure of thousands of confidential records to the public.
Human Error Mitigation Strategies
- Educate employees on cloud security best practices through regular training sessions.
- Use access controls and limit permissions based on roles.
- Implement automated monitoring systems to detect and alert on anomalies resulting from human error.
- Employ guardrails and automated alerts to reduce the chance of accidental exposures.
Uncontrolled Attack Surface
An uncontrolled attack surface in the cloud results from a vast number of connected devices, applications, and third-party services, which increase entry points for potential attackers. Shadow IT and unmanaged assets make it challenging for security teams to identify and protect all vulnerable points.
Uncontrolled Attack Surface Example
A technology firm suffered from a data breach after attackers exploited an unmanaged microservice within their cloud infrastructure. The overlooked asset allowed attackers to gain unauthorized access and compromise customer data.
Mitigation Strategies
- Use tools like CloudDefense.AI’s Attack Path Analysis to map and monitor all assets within the cloud environment regularly.
- Implement continuous vulnerability assessments to detect and secure weak points.
- Enforce strict controls on third-party applications and conduct regular reviews of their security compliance.
- Adopt a zero-trust approach, treating all connections and devices as potential security risks until verified.
API Vulnerability
APIs are essential for cloud functionality but also create vulnerabilities when improperly secured. Since APIs often handle large amounts of data and provide direct access to applications, any vulnerability can lead to unauthorized data access or system control.
API Vulnerability Example
An API flaw on a popular social media platform exposed user data due to improper authentication checks. Attackers used the vulnerability to gain access to personal information across millions of accounts.
API Vulnerability Mitigation Strategies
- Secure APIs with API gateways and enforce strong authentication measures.
- Use CloudDefense.AI’s API scanning to detect and resolve API vulnerabilities early in development.
- Regularly update APIs to ensure they meet current security standards and conduct routine testing for potential vulnerabilities.
- Limit data exposure in APIs by following the principle of least privilege and applying strict permissions.
How to Manage Cloud Security Risks?
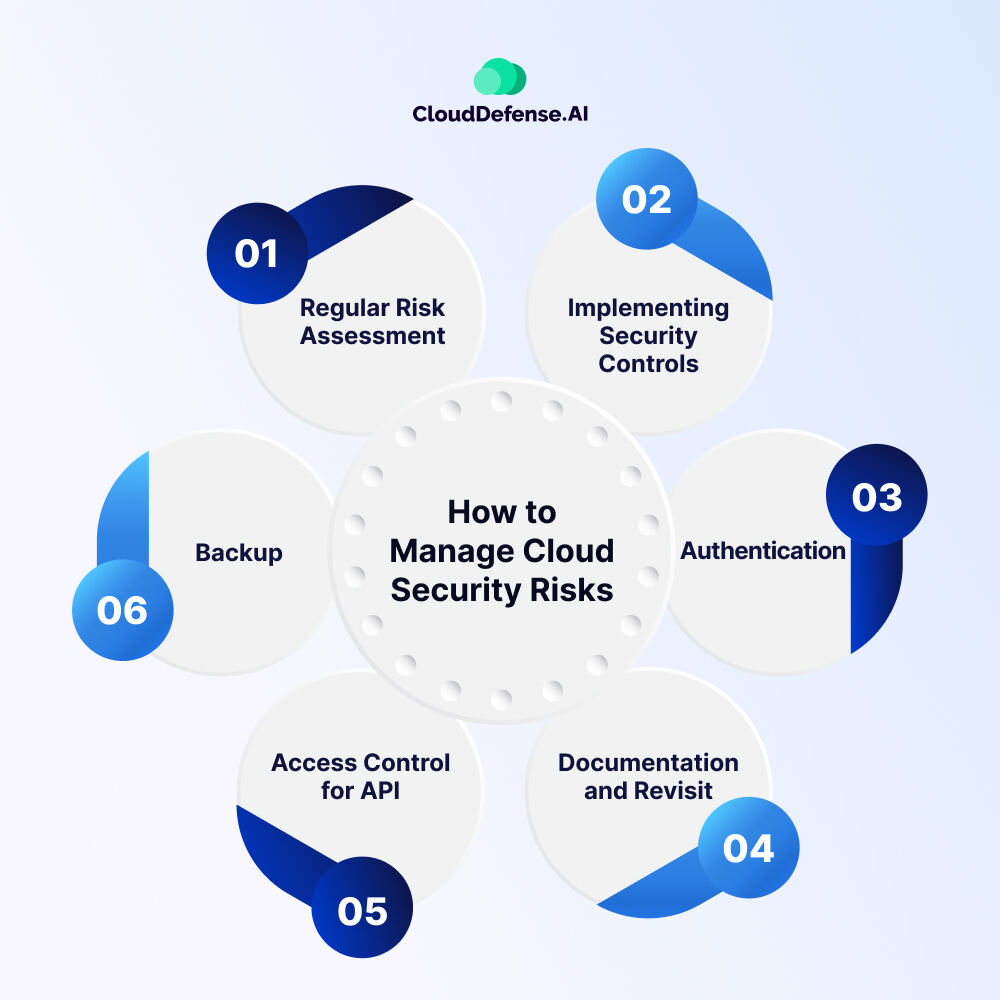
Managing cloud security risks has become a vital aspect of every organization because it helps minimize the impact that the most common security risks have on offer. Here are a few tips that will help you to manage cloud risks effectively:
- Regular Risk Assessment: When you conduct regular risk assessment in your public cloud through constant monitoring and proactive measures, it will help you unveil many potential risks.
- Implementing Security Controls: Understanding the security risk posture and implementing appropriate security controls is one of the best ways to manage it.
- Authentication: Utilizing authentication methods such as two-factor authentication or encryption keys can help you manage cloud security risks like data breaches. Centralizing logging is a smart way to manage cloud security risks and investigate events.
- Documentation and Revisit: You can document risks and revisit them, which will help you manage potential risks lingering in your cloud environment.
- Access Control for API: It is important for every organization to implement access control for API and employ other best security practices to minimize the chance of unauthorized access.
- Backup: Keeping a backup of all the sensitive data is a smart way to minimize cloud security risks, as the data can be recovered to maintain business workflow.
5 Cloud Security Threats
Cloud security threats are types of attacks where malicious actors exploit the risks to access your cloud assets. Even though modern security threats are evolving with the advancement of cloud technology, there are certain threats that daunt most organizations. Here are the top 5 cloud security threats that you should be aware of:
Zero Day Exploits
Zero-day exploits occur when attackers leverage previously unknown vulnerabilities in applications to access a cloud environment. These attacks are particularly dangerous as they can bypass standard configurations and security measures, putting critical assets at risk before a patch is available.
Zero Day Exploits Example
In 2021, a critical vulnerability in Microsoft Exchange allowed attackers to exploit unpatched servers worldwide. The zero-day exploit led to unauthorized access and data theft across multiple organizations before security teams could apply necessary fixes.
Zero Day Exploits Mitigation Strategies
- Use CloudDefense.AI’s continuous vulnerability management to identify potential risks in real-time.
- Implement network segmentation to contain the impact of zero-day exploits within limited areas.
- Enable automated patch management tools to apply updates quickly when vulnerabilities are disclosed.
- Utilize behavior analysis tools that detect abnormal patterns, potentially identifying exploits in early stages.
Insider Threat
Insider threats arise from individuals within the organization, like employees, contractors, or partners, who have legitimate access to cloud resources. This access can be misused, either intentionally or unintentionally, leading to unauthorized data access or exposure.
Insider Threat Example
A former employee of a U.S. healthcare provider misused their access to steal sensitive patient data, which was later exposed in a security breach. The incident highlighted the risks associated with failing to properly revoke access for departing personnel.
Insider Threat Mitigation Strategies
- Implement strict RBAC and review access rights periodically.
- Use CloudDefense.AI’s threat monitoring capabilities to detect unusual activity from insiders.
- Educate employees on security best practices and regularly train them on identifying phishing or social engineering threats.
- Set up alert systems that notify security teams of unusual access patterns from internal accounts.
Cyberattacks
Cyberattacks encompass a range of tactics, including DDoS, phishing, and malware attacks, often aimed at stealing data or disrupting operations. Cloud environments are especially vulnerable to such attacks due to their accessibility and dependency on the internet.
Cyberattacks Example
In 2020, a large e-commerce platform experienced a DDoS attack that disrupted its operations during peak shopping hours, leading to significant revenue losses. The attack was attributed to a lack of advanced threat detection and response capabilities.
Cyberattacks Mitigation Strategies
- Implement DDoS protection services, which can absorb and mitigate attack traffic before it reaches cloud resources.
- Use multi-layered firewalls and secure email gateways to minimize phishing attempts.
- Use CloudDefense.AI Hacker’s View™ for real-time threat detection and automated response to emerging cyber threats.
- Conduct regular security audits to identify and close any weak points that attackers could exploit.
Advanced Persistent Threats
Advanced Persistent Threats (APTs) involve prolonged and targeted attacks where malicious actors gain and maintain unauthorized access to cloud environments to steal data gradually. These threats are typically orchestrated by skilled adversaries, who employ a blend of tactics to avoid detection.
Advanced Persistent Threats Example
In a high-profile APT attack, an energy company discovered hackers had infiltrated their network and maintained access for over a year. During this period, sensitive operational and proprietary data was siphoned out without triggering any security alerts.
Advanced Persistent Threats Mitigation Strategies
- Use AI-driven tools like CloudDefense.AI to detect unusual patterns that may indicate APT presence.
- Adopt a zero-trust security framework, limiting access only to verified and authorized users.
- Conduct periodic penetration testing to identify potential weaknesses.
- Enable log monitoring and anomaly detection across all cloud resources to detect suspicious, prolonged activity.
Insufficient Identity, Credential, Key and Access Management
Weak identity and access management practices, such as poor password policies or inadequate multi-factor authentication, expose cloud resources to unauthorized access. Attackers can exploit weak credentials or compromised API keys to gain entry into sensitive environments.
Insufficient Identity, Credential, Key and Access Management Example
A leading technology firm experienced a security breach when an attacker acquired valid API credentials, enabling them to access sensitive data stored in the cloud. The credentials had been insufficiently protected, leading to significant reputational and financial damages.
Insufficient Identity, Credential, Key and Access Management Mitigation Strategies
- Use identity and access management solutions, such as CloudDefense.AI’s CIEM, to manage privileges and identities.
- Regularly rotate API keys and limit their permissions to only what’s necessary.
- Implement strict account management policies, including automatic session expiration and restricted access to high-privilege accounts.
- Conduct regular access reviews to ensure that only authorized personnel can access critical cloud resources.
How to Handle Cloud Security Threat?
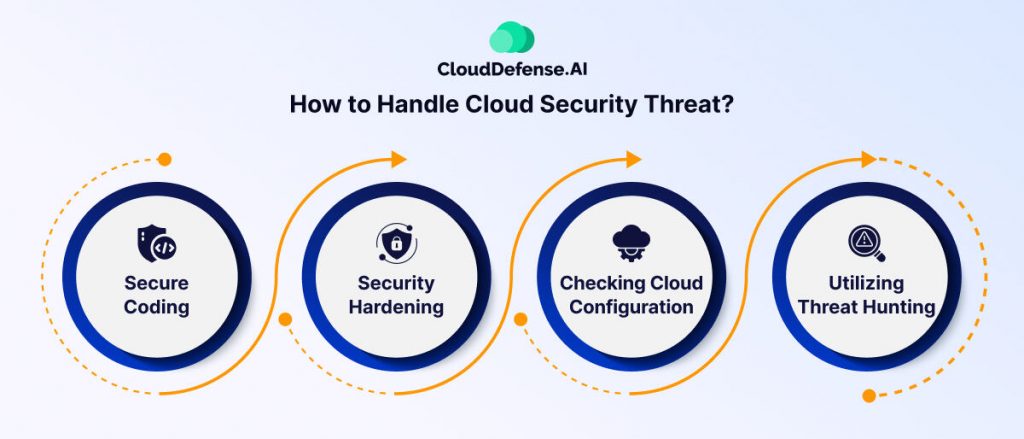
The number of cloud security threats is increasing with time, and it can be daunting for organizations to prevent all types of threats. However, following some basic guidelines can help the organization in protecting its cloud assets. Here are some ways you can handle cloud security threats:
- Secure Coding: One of the efficient ways to handle cloud security threats is by maintaining a secure coding standard throughout the development lifecycle. Securing the codes during microservice development will prevent attackers from using zero-day exploits.
- Security Hardening: Organizations must focus on hardening their infrastructure security from the core, which will reduce the chance of exploiting user identity to gain access. Implementing advanced tools like CIEM and various security policies will secure identities and prevent attackers from accessing them easily.
- Checking Cloud Configuration: Checking the cloud configuration at regular intervals will prevent various security threats from appearing. Whenever any cloud configuration is placed, the team should check them thoroughly to ensure there is no gap.
- Utilizing Threat Hunting: Making use of a threat-hunting solution is an offensive way of handling cloud security threats. Rather than waiting for the threats, the security team can use Threat Hunting to identify various types of threats in the cloud environment and mitigate them before they can make any impact.
5 Cloud Security Challenges
Even when an organization has a robust cloud security strategy in place, it still faces numerous cloud security challenges. These challenges are basically the hurdles they have to overcome to implement cloud security practically. Today, we will mention five top cloud security challenges every organization faces when they start implementing cloud security:
Lack of Cloud Security Skills and Strategy
The shortage of cloud security skills is a prevalent challenge, especially as many organizations transition from traditional data centers to cloud environments. Without specialized knowledge, security teams struggle to implement robust strategies, leading to vulnerabilities and exposing data to potential breaches.
Lack of Cloud Security Skills and Strategy Example
A large healthcare organization, lacking skilled cloud security personnel, implemented a cloud environment without properly securing it. This led to several vulnerabilities in its database, allowing unauthorized access and putting sensitive patient information at risk.
Lack of Cloud Security Skills and Strategy Mitigation Strategies
- Invest in training programs to upskill existing employees in cloud security practices.
- Implement a security-first strategy with continuous monitoring and routine audits to identify gaps and improve security policies.
Shadow IT
Shadow IT refers to employees using unauthorized applications or services outside the organization’s IT management, often to improve productivity. Unfortunately, these unsanctioned tools introduce significant security risks, including data leaks and compliance issues.
Shadow IT Example
In a technology firm, a group of developers used a third-party cloud service to expedite development. Because it was outside the IT department’s oversight, this usage created a security gap, leaving data exposed and non-compliant with internal security protocols.
Shadow IT Mitigation Strategies
- Use tools like CloudDefense.AI’s Attack Path Analysis to scan and detect any unmonitored resources within the cloud infrastructure.
- Educate employees on the risks associated with Shadow IT and enforce strict policies for cloud service usage.
- Implement role-based access controls and conduct regular checks to limit unapproved application access.
Compliance
Cloud-based organizations must meet various regulatory standards like GDPR, HIPAA, and PCI DSS. However, the shared responsibility model in cloud environments complicates compliance, as it requires both the cloud provider and organization to adhere to specific security standards.
Compliance Challenges Example
A financial institution faced fines after failing to meet the PCI DSS standards required for handling credit card data in its cloud environment. A gap in compliance protocols resulted in unauthorized access to sensitive customer data.
Compliance Challenges Mitigation Strategies
- Automate compliance checks using solutions like CloudDefense.AI’s CSPM, which can ensure adherence to regulatory standards.
- Set up compliance management as an ongoing process, with regular audits and updates to security protocols.
- Implement secure access controls and encryption for sensitive data to stay aligned with regulatory requirements.
Identity and Access Management
IAM is crucial for controlling who has access to cloud resources, but it is also one of the hardest security controls to implement effectively. Defining roles, permissions, and multi-factor authentication is time-intensive but critical for preventing unauthorized access.
IAM Example
A manufacturing company without a robust IAM system saw a breach when an employee’s compromised credentials were used to access sensitive data. The absence of defined access controls meant that multiple roles could access the same information, putting critical data at risk.
IAM Mitigation Strategies
- Use CloudDefense.AI’s CIEM to enforce strict IAM policies and limit access to essential personnel only.
- Implement multi-factor authentication and RBAC to enhance security.
- Regularly review and update permissions to ensure only authorized users can access sensitive resources.
Lack of Visibility
As cloud environments grow more complex, achieving complete visibility becomes challenging, especially with hybrid and multi-cloud architectures. Without a full view of all resources, monitoring security and managing potential risks become nearly impossible.
Lack of Visibility Example
An e-commerce company using a hybrid cloud setup struggled to monitor new resources added by third-party vendors. This lack of visibility led to several unmonitored assets, creating vulnerabilities that attackers could exploit.
Lack of Visibility Mitigation Strategies
- Deploy CloudDefense.AI’s real-time monitoring and alerting to maintain visibility over all cloud resources.
- Use continuous monitoring and threat detection to track assets and quickly identify suspicious activity.
- Integrate tools for centralized logging and analysis to improve visibility across hybrid or multi-cloud environments.
How to Overcome Cloud Security Challenges
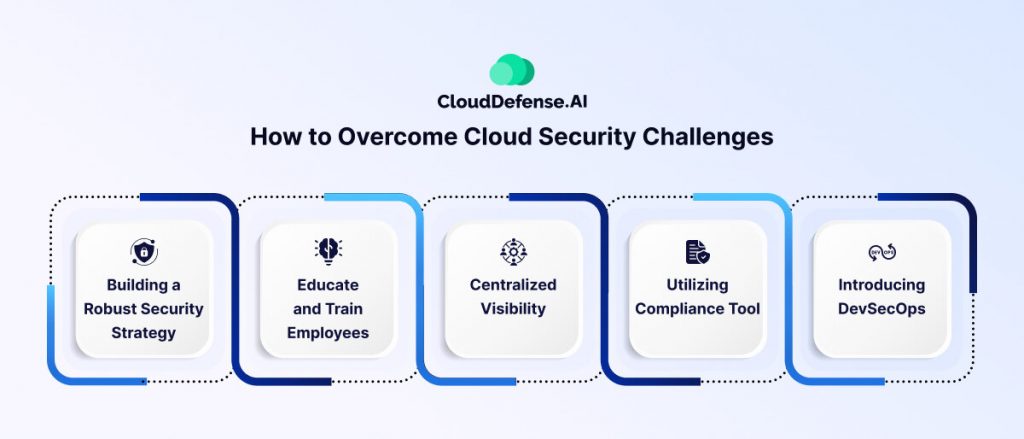
Overcoming cloud security challenges is not an easy task and it requires you to make a comprehensive approach. However, each challenge poses a different issue, and you will have to address them uniquely. Here are some ways to overcome cloud security challenges:
- Building a Robust Security Strategy: Your primary goal should be to build a robust security strategy that will help you take a comprehensive approach in addressing many common challenges.
To build a sound security strategy, you will have to automate vulnerability identification, include security at every level, create identification control, and use encryption.
- Educate and Train Employees: To properly implement cloud security measures, organizations must emphasize on educating and training employees.
Conducting regular workshops and training on various cloud security aspects and how employees can employ best security practices will ultimately help in building and maintaining security posture.
- Centralized Visibility: Ensuring a centralized visibility of all the cloud components will be highly useful for organizations to implement various security measures and policies properly. Through continuous monitoring and identification, security teams can govern all the activities happening in the cloud.
- Utilizing Compliance Tool: One of the best ways to stay compliant is by implementing compliance tools as it ensures regular audit and proper implementation of controls. These tools also make sure everyone follows best security practices to adhere to compliance guidelines.
- Introducing DevSecOps: DevSecOps brings a shift in the culture where it introduces security at every application development stage. Importantly, it comes highly useful to prevent Shadow IT as it enables security teams to keep track of every resource.
How CloudDefense.AI Can Help with Risks, Threats, and Challenges?
Organizations face increasing risks, evolving threats, and a variety of security challenges. Successfully defending against these requires a comprehensive security approach that proactively identifies, prioritizes, and mitigates vulnerabilities.
CloudDefense.AI provides a powerful solution with features that go beyond traditional security tools, making it a key ally in managing these complex aspects of cybersecurity.
Effective Risk Management with CloudDefense.AI
Managing risk effectively starts with visibility into your entire environment. CloudDefense.AI enables organizations to achieve full coverage across both cloud and on-premises systems through its continuous, agentless assessment capabilities. This ensures all assets are monitored for potential risks without slowing down performance. With real-time risk scoring and context-aware insights, CloudDefense.AI empowers your team to address the most critical risks first, optimizing resource allocation and strengthening security strategies.
- Proactive Risk Identification: CloudDefense.AI provides continuous monitoring that automatically scans for potential risks in real-time, ensuring no vulnerabilities are overlooked.
- Impact-Based Prioritization: Through smart prioritization, the platform assesses risk based on potential impact, helping you focus on the most severe risks to reduce overall exposure.
Threat Intelligence and Defense with CloudDefense.AI
With rising threats, a robust security posture requires not only detection but also understanding the complexity of potential attacks. CloudDefense.AI’s advanced threat intelligence delivers ongoing insights into emerging threats, integrating live updates for CVEs and providing comprehensive threat data to stay ahead of attackers.
- Real-Time Threat Alerts: Stay informed of new threats and critical vulnerabilities with automated threat alerts, minimizing response times and allowing for faster mitigation.
- Attack Path Analysis: CloudDefense.AI conducts detailed analysis to highlight possible multi-vector attack paths, giving your team insight into how various vulnerabilities may be exploited together and reinforcing proactive defenses.
Managing Security Challenges with CloudDefense.AI
For organizations, navigating modern security challenges requires seamless integration into daily workflows and development pipelines. CloudDefense.AI simplifies this through features designed to align with the fast pace of DevSecOps and compliance needs. Its CI/CD integration brings security directly into the development lifecycle, automatically scanning for vulnerabilities to catch issues early before they reach production.
- CI/CD Pipeline Security: By embedding security scans within the CI/CD workflow, CloudDefense.AI enables proactive vulnerability detection and remediation, supporting a smooth, secure development process.
- Automated Compliance Checks: Built-in support for regulations like ISO 27001, SOC II, and GDPR simplifies compliance, allowing organizations to maintain regulatory standards with automated checks and reporting that reduce the burden on security teams.
Complete Vulnerability Management with CloudDefense.AI
CloudDefense.AI tackles vulnerability management with precision and automation, reducing the manual workload and empowering teams to focus on what matters most. With AI-driven remediation suggestions, CloudDefense.AI provides guided steps to quickly resolve issues through automated patches, reconfigurations, and other mitigation actions.
- Contextual Insights for Prioritization: Vulnerabilities are not prioritized by severity alone; CloudDefense.AI also evaluates the context and potential impact, ensuring teams can target high-risk areas effectively.
- Automated Remediation: AI-powered remediation offers targeted suggestions to fix vulnerabilities, simplify resolution with precision and help to maintain a stronger security posture.
Attack Path Analysis with CloudDefense.AI
Managing risks, threats, and challenges requires comprehensive visibility into all assets. CloudDefense.AI’s asset inventory and continuous monitoring ensure that nothing slips through the cracks. Every component in your IT infrastructure is tracked, giving you full control over your security posture and enabling faster, more informed decisions.
- Full Asset Inventory: With complete asset tracking and visibility, you can monitor all devices, services, and applications in real time, reducing the risk of unknown assets compromising security.
- Centralized Dashboard: A user-friendly dashboard consolidates all security information, enabling quicker decision-making and facilitating a streamlined approach to risk management.
Taking Control of Security Today
CloudDefense.AI is more than a security tool—it’s an all-inclusive solution that empowers organizations to navigate the complexities of modern cybersecurity. By addressing risks, threats, and challenges with an integrated approach, CloudDefense.AI helps organizations protect their IT infrastructure, simplify compliance, and enhance their overall security posture.
Book a free demo today to see how CloudDefense.AI can redefine your security strategy, providing the defense you need to stay resilient against rising cyber threats.







