Cursor and Windsurf have become two prominent choices for developers. With their capabilities of generating contextual AI codes and completing functions from natural-language prompts, organizations are getting highly benefited.
However, the biggest issue with AI code assistant tools is that they utilize various third-party dependencies and models to generate contextual code. This often leads to vulnerabilities in the codebase, which, when deployed, can jeopardize the whole application.
That is why it is essential that organizations need to perform Windsurf and Cursor vulnerability detection and eliminate flawed AI code before they are committed. This guide will explore different techniques for scanning and remediating vulnerabilities in the AI-generated code.
How AI-Generated Code From Cursor and Windsurf Introduces Vulnerabilities
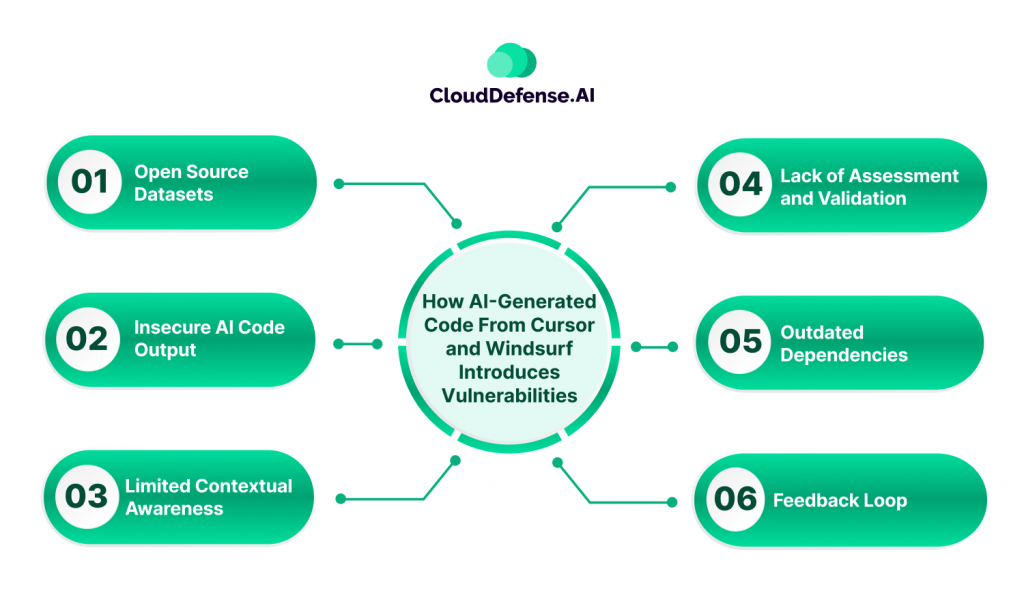
The vulnerability in the AI code output of Cursor and Windsurf originates due to various reasons:
- Open Source Datasets: Cursor and Windsurf are trained on massive datasets, which include public code repositories and third-party libraries. In most instances, these datasets are prevalent with common vulnerabilities and flawed code patterns. As AI codes learn from these sources, they inherit the vulnerabilities, and it gets introduced in the codebase.
- Insecure AI Code Output: Cursor and Windsurf may create static code patterns to meet any contextual requirements. These static code patterns are vulnerable to cyber threats when they are committed without validation. Attackers can exploit these patterns for their malicious intentions. AI code editors to achieve context and efficiency often utilize reusable templates (also known as boilerplate code).
- Limited Contextual Awareness: AI coding tools like Cursor and Windsurf hold the capability to generate codebase and project-aware code suggestions. However, they lack contextual understanding regarding the application’s security requisites, best security practices, business motive, and code sanitization. As a result, these AI code editors generate code that is often functionally exploitable by attackers.
- Lack of Assessment and Validation: AI coding assistants are helping developers with AI code generation and auto code completion. It is also assisting in automating certain repetitive tasks in the codebase. But this rapid generation of code is not providing time for the security team to assess and validate the code. This practice is leading to vulnerabilities in the application.
- Outdated Dependencies: Cursor and Windsurf are known for using outdated dependencies for training purposes. These dependencies can be third-party frameworks or libraries that carry numerous known vulnerabilities. So when a developer accepts these AI codes without sanitization, it invariably introduces vulnerability.
- Feedback Loop: AI training models, in some cases, leverage AI-generated code that is insecure and unsanitized. As a result, it results in a feedback loop that enables vulnerabilities to go live and affect the whole application gradually.
Vulnerability Scanning Techniques for All AI-Suggested Code Snippets of Cursor and Windsurf

For organizations relying on Cursor and Windsurf, identifying vulnerabilities in the AI-suggested code has become a necessity. There are various vulnerability scanning techniques that organizations can leverage by integrating them into the development environment where AI code is suggested. These techniques are:
- Static Application Security Testing: SAST serves as one of the most effective vulnerability scanning techniques that can also be integrated into IDE as a plugin. It can efficiently identify common vulnerabilities like flawed patterns, plausible injection attacks, and sensitive data leaks within AI code. Importantly, it can analyze and provide alerts regarding vulnerability in the AI-suggested codes as developers work using Cursor and Windsurf. It would be ideal to consider a SAST tool that is not tied to Cursor and Windsurf, as it will produce fair security suggestions.
- Detailed Human Review: Along with automated scanning for vulnerabilities, developers also need to pay extra attention to AI-generated code. The developer must spend time reviewing the AI-suggested code for security flaws, logic errors, third-party interactions, and compliance with security standards. The team should also assess for AI code that, upon deployment, can introduce insecure functionalities in the application.
- Software Composition Analysis: Windsurf and Cursor often integrate external dependencies with AI code that carry common vulnerabilities. In such situations, security teams can automate SCA tools that will assess all the dependencies, especially the ones included by AI-suggested code. It checks all the dependencies and libraries against various known vulnerability databases, including CVE, and provides the report. It needs to be integrated into the CI pipeline so that it can ensure AI code doesn’t include outdated libraries or vulnerable dependencies.
- Secret Detection: AI codes on many occasions carry hardcoded secrets like passwords, API, and other sensitive information. These secrets, if exposed, can make the application as well as the whole system vulnerable. Integrating Secret Detection tools in the developer’s workflow will help in scanning AI codes for any pattern that will indicate the accidental presence of secrets. Once it detects any secret, it will provide an alert to prevent developers from committing the AI code.
- Penetration Testing: Penetration testing can come in handy to identify vulnerabilities lurking in all the AI codes from Cursor and Windsurf present in the codebase. The security team, through this testing, can simulate how different cyber threats can exploit AI-based applications. Manual or automated penetration testing can be utilized to identify the vulnerabilities.
- Dynamic Application Security Testing: An Organization can also make use of DAST to scan for vulnerabilities in a running application developed on AI code. It mainly identifies security threats like broken access control and authentication issues that originate during runtime. It can also be used for identifying security flaws in the interaction of different components in an AI-code-based application. DAST also offers security teams with behavioral security assessment capability to analyze the function of AI codes.
Vulnerability Remediation Techniques For Cursor and Windsurf’s Output
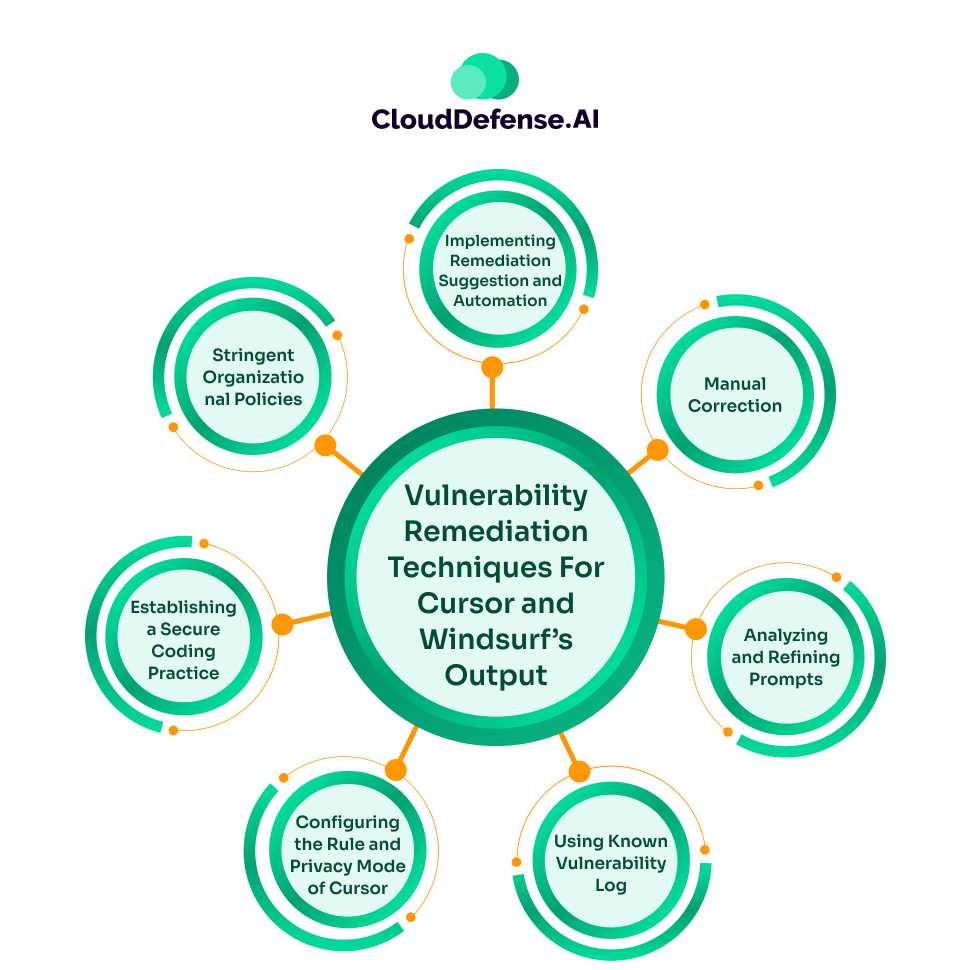
Vulnerability scanning technique will help your organization to identify vulnerabilities in the AI code provided by Cursor and Windsurf. However, it is important that those vulnerabilities be remediated effectively. Here are some remediation techniques that the organization can utilize:
- Implementing Remediation Suggestion and Automation: Most SAST and SCA, upon integration in the IDE, offer users contextual remediation suggestions for identified vulnerabilities. Some advanced versions of these security tools can provide automated fixes for various vulnerabilities in the AI code from Cursor and Windsurf. It is a highly useful approach for developers to remediate security issues while writing code using AI code editors.
- Manual Correction: In many instances, automated fixes from advanced SAST, SCA, and Secret Detection tools might not be available. In such a situation, developers, along with assistance from the security team, must remediate vulnerabilities. They must follow secure coding policies and organization security requirements while remediating those issues. Developers should also utilize the opportunity to enhance the maintainability of the AI code within the project.
- Analyzing and Refining Prompts: To prevent common vulnerabilities in AI code from reappearing, developers should work towards refining the prompt. The developer should first analyze and understand the reason why a particular AI-generated code from Cursor or Windsurf is vulnerable. They should assess whether the prompt lacked the security requisite or proper command. Then they should refine the prompt with specific security requirements, and it will help in generating secure AI code.
- Using Known Vulnerability Log: Developers can maintain a log of all the vulnerabilities that were detected in common AI code suggestions. It would serve as a learning tool as they can study those vulnerabilities and develop ways to avoid them in the future.
- Configuring the Rule and Privacy Mode of Cursor: Cursor offers developers the Rule feature. It can be tweaked in accordance with the organizational security policies and coding standards. As a result, it will cause Cursor to function by following all the guidelines. In addition, Privacy Mode can be utilized, which will ensure important project code won’t be stored in remote servers or the cloud.
- Establishing a Secure Coding Practice: It is vital for organizations to establish a culture where developers develop the habit of emphasizing security while committing AI code. “Shift left” culture must be prioritized while relying mostly on AI gendered code from Cursor and Windsurf. All the code must be validated and reviewed before they are introduced.
- Stringent Organizational Policies: Organizations should implement strict policies that ensure secure usage of Cursor and Windsurf. All the developers should go through various training sessions to get adapted to organizational policies.
Conclusion
Detecting and fixing vulnerabilities in AI-generated code from Cursor and Windsurf has become a necessity for all organizations around the world. For most developers who rely on AI code editors, it is important to implement various techniques to identify the vulnerabilities in the AI code.
This guide will highlight all the necessary vulnerability detection and remediation techniques that can help eliminate all the security threats. The secure usage of AI-suggested code requires a strong approach to implementing security through the software development environment. In the coming years, AI code is going to be prominent in all IDEs, so these techniques can come in handy for developers.







