Practically mitigating a two-pronged risk chain—OSS compliance and security.
Open source software (OSS) is a type of software with source code that can be altered, enhanced, and viewed by anyone.
Github’s ‘State of the Octoverse’ report—which amalgamates insights on community and open source user projects—caught a large jump in the number of open source projects after about March.
“While developers have been putting in longer working hours, they’ve also spent more time on open source projects.”
Over 60 million new repositories were created in 2020. JavaScript was the most popular language, with Python overtaking Java as second-most. Nigeria had the largest percentage growth in user contribution, closely followed by Hong Kong (SAR).
What is OSS License Compliance Lawsuit?
Curiously: Students, designers, teachers, data analysts, and scientists increasingly joined GitHub which suggests that collaboration is moving beyond more than just code. This however makes for uncertain footing with potential legal hazards.
OSS compliance lawsuits are already common even at large scale such as Panasonic’s settlement of a 100 million dollar lawsuit.
Software developers also need threat detection systems that keep pace with build processes—this need was seen just last year, when billions of confidential records were stolen due to exposed MongoDB and Elasticsearch databases, and other combinations of human error.
We should also note that closed-source software has its own problem set, as seen with SolarWinds. Nevertheless, last year’s top concern in a multi-year OSS survey of 1000+ professionals was predictably ‘OSS licensing compliance.’
We can see security as an off-shoot issue. How can you optimally manage the two diverging and converging issues?
Risk-Chain Link 1 – Compliance
SaaS companies want to avoid reaching the point of a legal battle like the $9 billion Google v. Oracle on the nature of computer code v. copyright law. They can start by being properly informed about OSS licenses and compliance.
What Is the OSS license?
Open source software (OSS) licenses protect software and by extension can extend to protecting owners.
- An OSS license is a risk when you don’t know your obligations or fail to abide by them.
- As the owner, you have a given set of responsibilities and duties to uphold.
- And it’s the reason why 2020’s OSS programs focused on compliance.
Your license explicitly details what responsibilities you have to uphold if you wish to use the related software to build applications. There will typically be terms to obey if you want to distribute your software.
Failing to comply potentially puts you in violation of the license, thus subject to legal forces. There are two general categories of OSS licenses. What you choose will depend on your project needs and philosophy.
Permissive Licenses
Permissive software licenses let you modify or enhance OSS intellectual properties to make your own derivative proprietary products without any need to make those derivatives freely available for other recipients.
Three prominent examples of permissive licenses are MIT, Apache and BSD licenses, also called ‘non-copyleft’ licenses. Your typical main responsibility is to attribute the source to its original developers—but not always—and there may be other limited requirements.
Because of the lack of reciprocity, OSSs under a permissive license may suddenly close to the public or be available at a charge.
Restrictive Licenses
Restrictive software licenses retain the software’s openness but strictly limit you against deriving closed proprietary products—any code alteration must be made available to future recipients in such a way that they can recreate that product.
GPL (GNU general public license) is the most common restricted license—GPL is sometimes just referred to as ‘copyleft’ license, but other copylefts exist, like Mozilla’s MPL-2.0.
And copyleft describes that underlying contract design wherein licensed intellectual properties may be freely distributed and modified—but with the caveat that those same rights are applied to all derivative works.
The copyleft / restrictive license type is thought of as protective or reciprocal.
Choosing a License
Your license choice is critically important as it dictates your distribution privileges and how your open source library can be put to use or even accessed. You may also open your software to other companies, letting them leverage it—if you choose a wrong license. No redacting.
“Switching to a different license later, during the life of the project, can be difficult if not impossible.”
— Linux Foundation.
Not to mention possibly very expensive.
Scenario 1
Derivative / Distributed Works: You are Microsoft. You discover a commercially marketable product:
Word. However, you notice that it contains a certain portion of open source code. Under GPL, “as a result of this oversight, all users of Microsoft Word now have a license to freely distribute, reproduce, and modify Word” (source: General Attorney, Theresa Gue).
Scenario 2
License Less: Let’s give Microsoft a worse day; if you derived Word without a license, you’ve violated the owner’s copyright. You are heavily sued, like these firms: Cisco-Linksys, who had no idea that its router had GLP code; Samsung; and Best Buy ($27 million).
Risk-Chain Link 2 – Hackers / Breaches / Malware
Some of this increased risk is inevitable—for instance, on the hackers, vulnerabilities, and malware end of things; every once in a while some piece of novel software is able to break a company’s supply chain, sending it into downtime or actually obtaining sensitive data.
A Brief Discussion on Vulnerabilities
Only a few weeks ago from the time of this writing, more than 35 tech firms were successfully attacked in this event.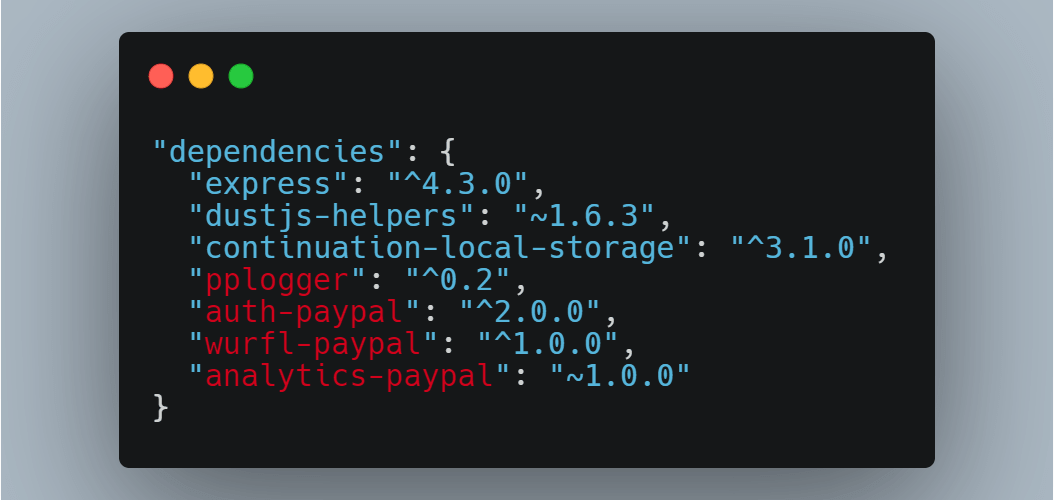
It was a proof of concept attack, no actual damage was done.
All carried out by a researcher, Alex Birsan.
With the help of his colleague Justin Gardner, who was paid a healthy bonus for his discovery of the supply chain vulnerability, making headlines.
The proof of concept attack—carried out through a form of ‘ethical hacking’—permeated through preventative barriers of several major technological firms including PayPal, Tesla, Netflix, Shopify, Yelp, and Uber.
It exploited how each system used open source software in public repositories. The attack injected malware into open source repositories, was distributed downstream, and infected the internal applications of its targets.
The researcher’s dependencies, made for a Paypal package
International Data Privacy Convergence With Cybersecurity Standards
The European GDPR set a trend of international data privacy in 2018. Following this, the California Consumer Privacy Act (see CPA) and New York’s Stop Hacks and Improve Electronic Data Security Act (“SHIELD Act”) became its US statewide counterpart. Even though California is on the frontline in cyber security they are still having issues with big ransomware attacks.
The movement is towards imposed rigorous cybersecurity standards, frequent security testing, and continuous monitoring. Other US states including Nevada and Maine have already passed data privacy bills or scheduling it for 2021.
In 2021, attackers will undoubtedly reconvene their APT (advanced persistent threat) campaigns. Businesses must rely on ‘high levels of detection and to deliver consistently good products’—according to Mark James, security specialist at Eset.
Software developers need to avoid the avoidable in such a way that does not pile on project management concerns and damage agility.
Let’s go over practical implementations and preventions
How CloudDefense.AI Covers You to Avoid OSS License Compliance Lawsuits and Vulnerabilities
CloudDefense.AI has a CI/CD compliance & protection tool to avoid OSS License Compliance Lawsuits and Vulnerabilities that covers your full agile development process.
![]()
It knows that data is the ultimate prize for hackers. They relentlessly look for ways to exploit application vulnerabilities and gain access to private data. Then there are compliance oversights.
There are always marginal cases with blurred conceptual compliance borders such as the ongoing Google v Oracle battle, these are rare and your day-to-day ‘full fledged compliance’ concerns should be with keeping your product in line with essentials.
And the typical enterprise company handles hundreds of pieces of software and the scale, expectedly, leads to security headaches for SecOps teams who endlessly pen-test, certify, and validate each application’s security posture.
With the SecOps team bottlenecked by overwhelming work, developers tug at their own hair in impatience. CloudDefense.AI helps here.
Automatically Detect Conflicts
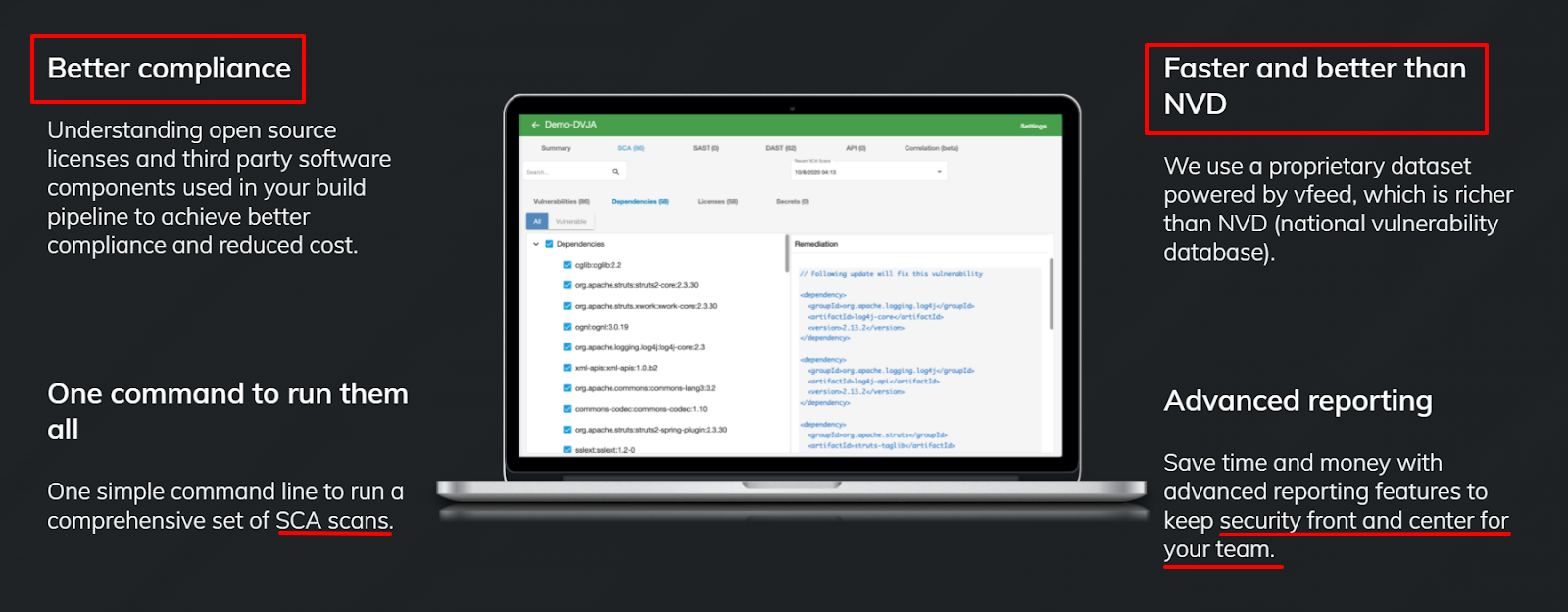
CloudDefense.AI’s proprietary Software Composition Analysis (SCA) for open source libraries feature comprehensively searches your source code for compositions containing open source libraries (SCA) data.
The typical application consists of 60%-70% of open source libraries. These must be carefully reviewed because not all open source libraries can be used for commercial products, due to complex licensing requirements—for reasons that we have already explored.
This can otherwise take months of manual effort to resolve. That’s not mention legal issues from unapproved licenses.
Ever-Lasting Compliance
With the obvious entropic caveats.
Why should you integrate your CI/CD with compliance? Because compliance and security aren’t one-time deals. That’s why you should not stop with SCA compositional analysis capabilities. It sounds obvious, but let’s simulate a further simple case-study based on General Attorney Thrue’s…
Scenario: You’ve founded the Microsoft company and built a profitable piece of software—Word—but one of Word’s updates features a single piece of restrictive OSS code. In order to be compliant, the update needs to be scrapped, or Word’s full source code made public.
You may also face legal fines for revenue generated in the launch and nondisclosure of the update’s source code.
Speed Compliance Without Risk Trade-Offs
CI/CD integrations continuously prevents such compliance issues (and speeds up compliance).
Continuous delivery and continuous integration (CI/CD) are participative philosophies for delivering software products faster to end users through efficient better management of operations, without detectable downtime during deployments.
The CI/CD pipeline developed through a growing union between IT operations and software development tasks, opening up a healthy space for DevOps.
DevOps Seeks to harmonies IT operations and software development processes so that a company is capable of delivering software at a maintainable high pace, no one’s health care bills will be high due to too much work.
By closing the gap found in traditional boundaries between the two, quality software capabilities and applications get delivered on time to end users.
Altogether, this is an agile iterative approach to project management which software development teams have notably adopted and is summed up by the Agile Manifesto’s mantra, “the continuous delivery of valuable software.”
Get better compliance cover over your product’s full life-cycle. Avoid the natural slack-handedness that comes with time. Integrated CI/CD workflows is a major CloudDefense.AI capability (read more).
Superior Threat Assessments
Security issues both converge and diverge with license compliance issues, so the two need to be integrated synchronistically, while honoring the best separate practices for each sphere. Let’s go over CI/CD friendly security protections.
Firstly, we beat NVD-based scanners: The CloudDefense.AI breakthrough CI/CD tool powers you with a leading-edge platform—this integration (with hundreds of subset integrations eg. APIs) feature means that CloudDefense.AI assesses your full application stack’s risk posture continuously as it develops…
Which opens the door to a more agile DevSecOps conception—compliance, security, and development joined in one body with multiple parts.
Why don’t the older existing threat detection models work as well? The problem with NVD is that it takes on average 54 days to upload new security fixes to its database. This is too slow for the modern era, when—in that very same period of time—hundreds of millions of public records can be eaten by hackers, and digested.
CloudDefense.AI is faster than NVD (the National Vulnerability Database) and provides vulnerabilities that are not available in NVD. It integrates the latest discoveries while securing you against easily preventable problems, which will give security the legs to keep pace with development.
Superior vFeed Engine
CloudData’s proprietary dataset uses vFeed—200,000+ vulnerabilities tracked and 100+ data sources correlated; the vFeed engine gathers big data, standardizes it, and runs it through correlation algorithms to establish rigorous build-on threat and vulnerability feeds.
Limit your risk exposure and priorities remediation’s through highly actionable vulnerability intelligence as a service indicators, melded alongside rigorous and diverse security standards and automated penetration testing.
CloudDefense.AI reduces the time and energy needed to profile your asset threat; puts your findings through accuracy and reliability checks to validate the threat; and correlates hundreds of aggregated associated references.
AIRTIGHT Shared Management
To avoid embarrassments and legal slip ups, CloudDefense.AI gives SecOps and Compliance teams a bird’s-eye view of key issues ahead-of-time via advanced automatic shared reporting: OSS vulnerabilities, internal application risks, and legal compliance issues—to help with planning out your licenses philosophy, i.e. AIRTIGHT compliance protocol management
CloudDefense.AI’s front and center developer friendly reporting dashboard provides a user-friendly, solutions and risk oriented Compliance and Security roadmap.
Visual Roadmap
Avoid failing to make available / publish source code packages using a visualized detailed compliance checklist that meets licence obligations
Checklists Steps
Ensure correct source codes are provided by using an extra verification compliance checklist step exactly corresponding to the distributed binary version.
Manage Airtight
Do not fail to label open source codes that have been modified and provide a summary of changes: by adding this as a checklist item before the source code’s release; as a checklist item for inspections before release; and a milestone, to ensure that the source code was marked this way.
Unite your team with auto reports inside our proprietary system By Developers, For Developers. CloudDefense.AI is trusted by enterprise level security teams. But non security experts can use it. Getting started takes two minutes.
The first step to a tight compliance and security design is to secure and automate the essentials. We offer a powerful CI/CD tool; breakthrough vulnerability safeguarding and continuous scanning; and shared reports to remove single points of failure when systemizing your compliance practices.
Sign up for CloudDefense.AI’s 14-day free trial, or request a personalized demo.







