In today’s agile software development world, developers leverage varied programming languages like Python, Java, Go, and JavaScript to streamline the process. Having support for different programming languages, developers can quickly deliver applications to the market. However, to ensure all the codes are secure before they are deployed, organizations need to leverage AppSec tools.
A Static Application Security Testing (SAST) tool serves as a cornerstone of modern software development, enabling developers to scan and remediate vulnerabilities in code. But you need to remember that the programming language you use determines how the SAST will perform and what vulnerabilities it will find. This guide will give you a detailed idea of how SAST works for Python, Java, JavaScript, and Go, and what vulnerabilities it finds for each language.
How SAST Tools Work
At the core, SAST tools leverage a parsing methodology that creates an AST of the codebase of the application and then performs code analysis. Parsing allows the tool to understand how the code is input and whether it will lead to any security threat, like SQL injection or XSS. A SAST tool utilizes different code analysis techniques when parsing a codebase, and it is largely influenced by the programming language used.
Codes in some programming languages are statically typed, while in others they are typed dynamically. Whether a code is compiled or interpreted also has an effect on how the tools perform and the accuracy of their findings.
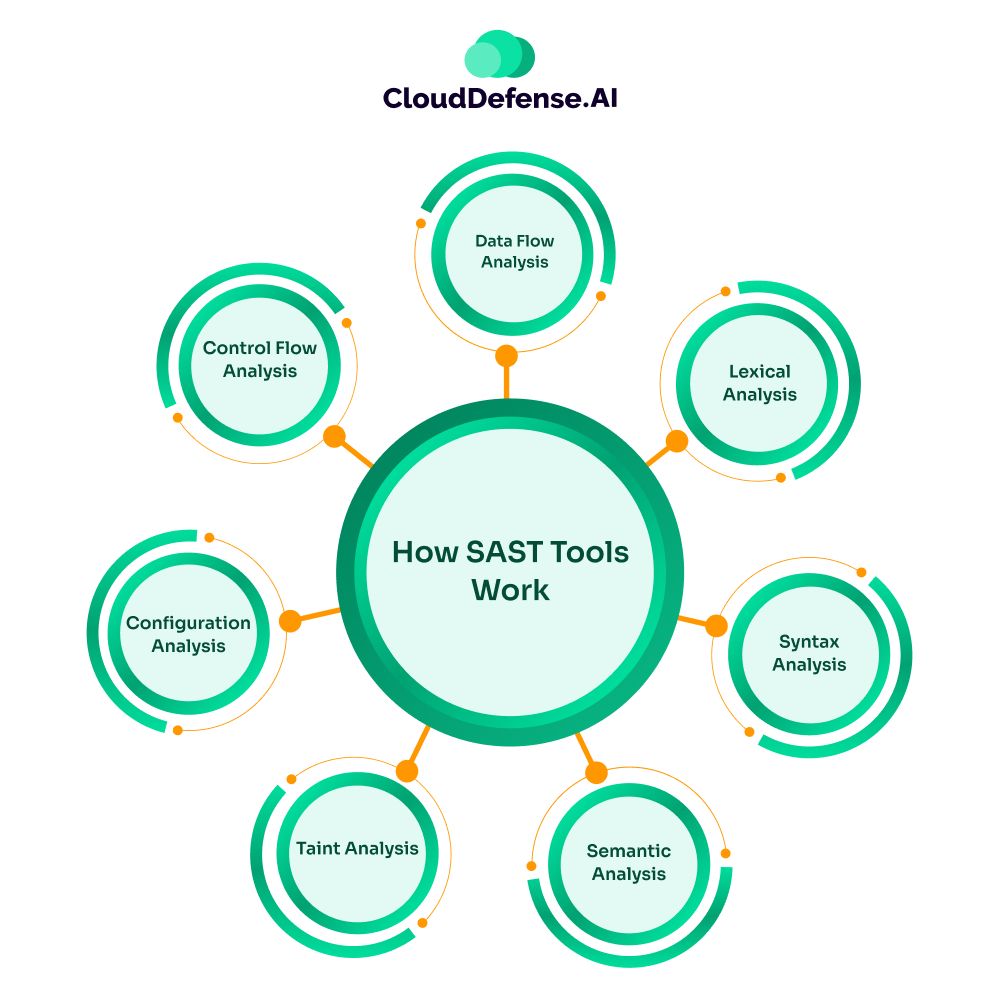
Some of the primary code analysis techniques that are utilized by SAST tools are:
- Control Flow Analysis: It serves as one of the core analysis techniques for SAST tools, where it analyzes the execution paths through the code. While analyzing, it assesses different aspects like loops, function calls, and conditional statements to uncover vulnerabilities. Dead code and infinite loops are some common security threats uncovered by this technique.
- Data Flow Analysis: It is a crucial technique that SAST leverages to track the complete flow of the data, from input to execution. It is highly useful in identifying any malicious input and preventing it from flowing into important functions in the production stage.
- Lexical Analysis: It is a basic technique that enables SAST to scan code for validating the syntax and uncover basic errors. In this technique, the source code is segregated into individual tokens and analyzed to ensure the code follows appropriate rules and structure.
- Syntax Analysis: This is a basic analysis technique that SAST tools utilize to ensure the code is compliant with all the grammatical rules. It ensures the code is free from any syntax errors.
- Semantic Analysis: SAST tools not only analyse the syntax but also utilize semantic knowledge to understand the meaning and context of the code being committed. This technique enables SAST tools to identify logical vulnerabilities like SQL injection.
- Taint Analysis: Some SAST tools utilize this technique to track the propagation of untrusted data in the application. It marks any malicious input data and tracks it to identify any potential security breach.
- Configuration Analysis: SAST tools also involve configuration analysis techniques to scan configuration files in web applications. It is useful in identifying security issues like exposed protocols or hardcoded secrets.
SAST For Python
The Python language has always been a favorite for developers because it offers dynamic typing, flexibility, simplicity, and a wide range of libraries. Developers widely use this programming language for streamlining their development process. However, when it comes to utilizing SAST for Python, the dynamic nature makes it challenging for the analysis tool.
Factors Influencing SAST Analysis for Python
When SAST tools analyze code based on Python, their effectiveness and detection accuracy are determined by certain factors:
- Dynamic Typing: Python is a dynamically typed language, as the variable type analysis is done at runtime. When implementing SAST for Python, it needs to employ advanced techniques to track the data types and potential security threats that might arise from it.
- Global Interpreter Lock: This programming language comes with a GIL that limits the parallel execution of any bytecode. As a result, it affects the SAST analysis process on detecting and analyzing concurrency-related security threats.
- Huge Library and Framework Support: Python supports a vast range of libraries and frameworks. This mandates SAST tools to extensive rule sets to uncover vulnerabilities depending on the frameworks and libraries.
Common Vulnerabilities SAST Identifies in Python
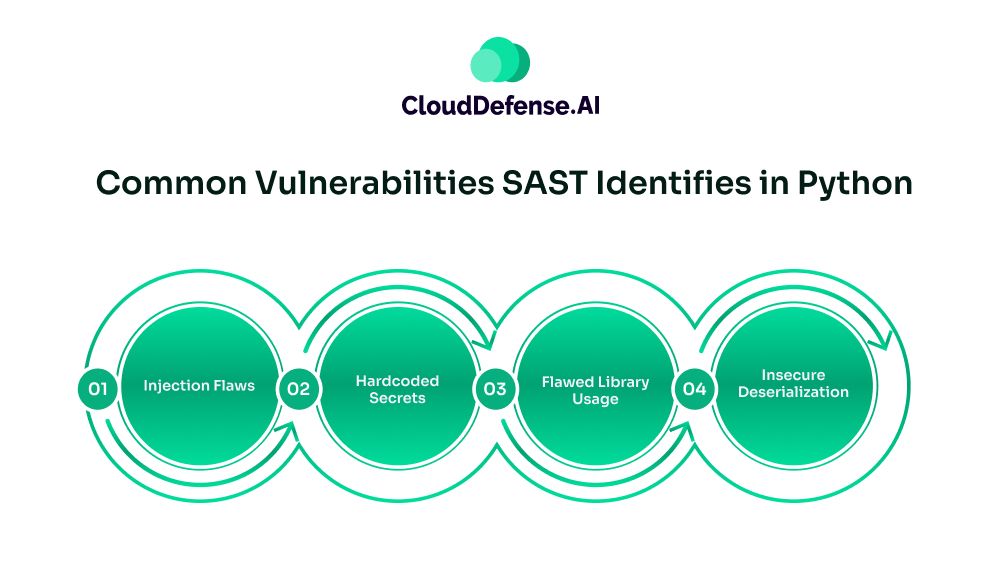
Here are some common vulnerabilities SAST catches in Python:
- Injection Flaws: It is the most common vulnerability type that is flagged by SAST in Python-based code. The code analysis tool thoroughly looks for unsanitized inputs to uncover SQL injection or LDAP injection.
- Hardcoded Secrets: Developers, while coding using Python, often store sensitive data like passwords in code. SAST looks for these hardcoded secrets and flags them.
- Flawed Library Usage: Python projects often utilise outdated or vulnerable third-party libraries for executing certain functions. SAST looks for such flawed libraries and puts an alert.
- Insecure Deserialization: Integration of SAST for Python enables developers to identify vulnerabilities from the deserialization of flawed data. When an erratic code is executed from deserialization, SAST can identify it.
SAST for Java
Java is an object-oriented and compiled programming language that is widely utilized by organizations for building applications. This programming language is statically typed and has a structured environment, enabling SAST to provide an overview of code and data flow. All the variables in the code are declared, and codes are always compiled, helping SAST to achieve more accuracy.
Factors Influencing SAST Analysis for Java
The factor that determines the accuracy when developers use Java SAST tools is:
- Assessment of Bytecode: In Java, all the codes are compiled into bytecode before they are executed. Moreover, the static typing of code enables Java SAST tools to have a better understanding of the data flow and code structure. This helps in better vulnerability identification accuracy and reduces uncertainty.
- Dependency Management: Like Python, Java is also highly reliant on third-party libraries. SAST needs to integrate with the Software Composition Analysis tool to uncover vulnerabilities and flag them.
- Complex Frameworks: Java works with complex and large frameworks to carry out different functions. Thus, the knowledge base of SAST tools regarding common misconfiguration and security patterns in these specific frameworks plays a role in determining their capability.
- Concurrency: The Java programming language is often utilized for building concurrent applications. SAST tools need to utilise techniques that will enable them to detect concurrency-related vulnerabilities like deadlocks and race conditions.
Common Vulnerabilities SAST Identifies in Java
Some of the flaws SAST identifies in Java-based application code are:
- XML External Entity: Some Java applications parse XML from flawed sources, and this leads to XXE attacks. However, SAST can identify such a vulnerability by assessing the XML parser configuration.
- Broken Authentication: Java SAST tools are proficient in identifying weak password policies or insecure session handling while scanning Java-based code.
- Injection Flaws: Injection flaws are also common in Java applications. SAST tool analyzes the user input and its execution in database queries to find SQL injection or NoSQL injection.
- Insecure Direct Object References: SAST holds the ability to identify issues of unapproved access when an application utilizes a user-supplied input for accessing objects.
SAST For JavaScript
JavaScript is a popular programming language that is dynamically typed, event-driven, and structured. It is leveraged by developers as it offers client-side scripting, helping in development for web browsers. However, nowadays, it is widely utilized with Node.js for performing server-side development. The use of both sides makes it challenging for SAST to do static analysis for JS-based development.
Factors Influencing SAST Analysis for JavaScript
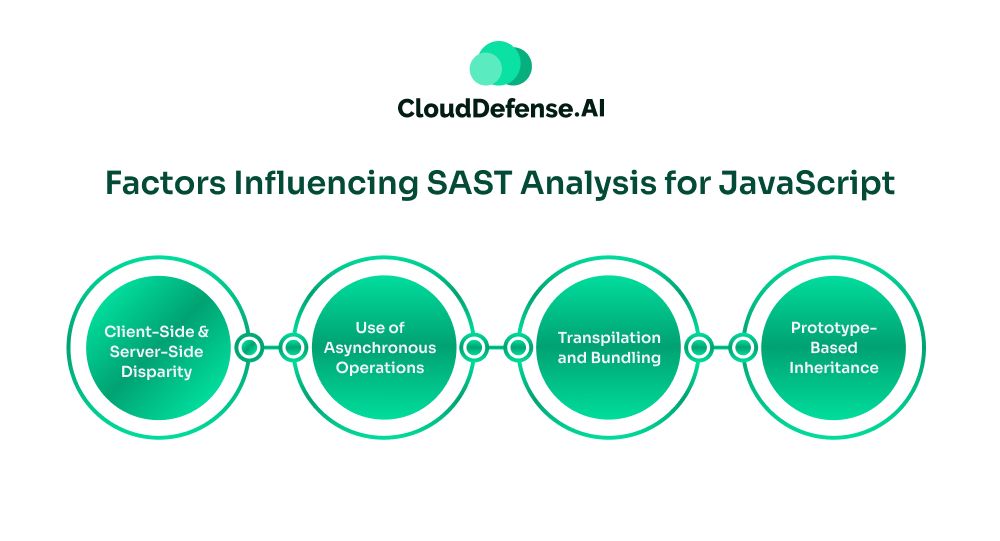
The effectiveness and accuracy of static analysis for JS-based developments are also dependent on various factors. They are:
- Client-Side and Server-Side Disparity: JavaScript is utilized by developers on both the client and server sides. As a result, SAST tools have to address vulnerabilities in the context of the browser and server side. This significantly affects the effectiveness and makes the process time-consuming.
- Use of Asynchronous Operations: JavaScript is a dynamic programming language that heavily uses asynchronous operations like callbacks and promises. This makes it difficult for SAST to track down the execution path of data throughout the operation, from origin to execution. Node.js also gets an architecture that is based on events, adding complexity to analysis.
- Transpilation and Bundling: Many developers are reliant on JavaScript for transpilation and bundling during development. A SAST tool in such situations has to assess the intermediate representation or main codebase to identify threats.
- Prototype-Based Inheritance: JavaScript is highly reliant on prototype-based inheritance models. SAST tools have to identify issues like prototype pollution while assessing the code.
Common Vulnerabilities SAST Identifies in JavaScript
When static analysis for JS-based application code is performed using SAST, the common vulnerabilities it detects are:
- Cross-Site Scripting: Most client-side JavaScript development faces cross-site scripting issues. However, SAST uncovers it by finding segments where unsanitized user inputs were executed in the browser.
- Server-Side Forgery: SAST tool actively identifies server-side forgery vulnerabilities in Node.js-based applications. It identifies code paths that attackers can utilize to make malicious requests and remediates them.
- Regular Expression Denial of Service: Malicious attackers leverage faulty or poor regular expressions in the JavaScript-based source code to launch a DoS attack. However, SAST identifies it by assessing for insecure patterns.
- Prototype Pollution: SAST tool is highly effective in identifying prototype pollution vulnerability. Attackers make modifications to the prototype of the base object, which allows them to launch DoS or carry out other malicious activity.
SAST for Go
Go is a statically typed and compiled programming language. It is popular among developers as it offers the simplicity and performance they need for swift application development. Most importantly, it has a simple syntax, which makes it easy for SAST for Go secure scanning. What’s more? The static type streamlines the process to analyze the data flow.
Factors Influencing SAST Analysis for Go
- Simplistic Nature: Go has a simplistic nature with minimal use of libraries for carrying out different functions. This simplifies SAST’s process to easily identify vulnerabilities.
- Concurrency Model: This programming language is built with a concurrency model. This enables SAST tools to identify concurrency security issues like race conditions.
- Explicit Error Handling: Go has an explicit error handling capability that assists SAST tools in easily uncovering all the errors that can give rise to vulnerabilities in the code.
Common Vulnerabilities SAST Identifies in Go
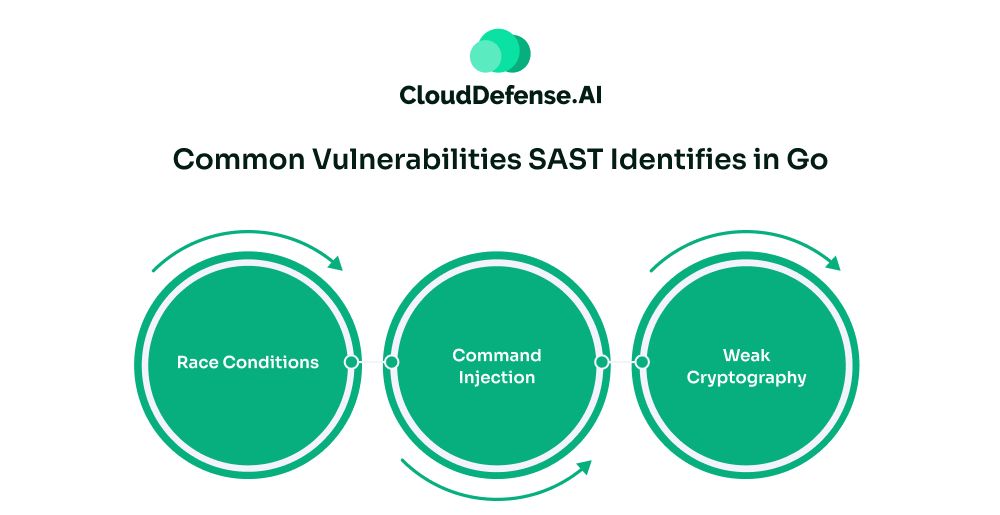
Vulnerabilities that are discovered during Go secure scanning by SAST tools are:
- Race Conditions: The SAST tool is highly effective in identifying race conditions that originate when the concurrency model of Go is poorly handled.
- Command Injection: It is a common vulnerability that SAST tools can easily identify when unsanitized inputs are maliciously used in system commands. It tracks the data flow and uncovers the issue.
- Weak Cryptography: Developers, while working on Go, often use weak cryptography algorithms. SAST tools can identify such issues and make remediation.
Final Thoughts
Irrespective of the programming languages, the SAST tool is all about identifying vulnerabilities in the code in the development workflow without executing them. However, the analysis approach, rules, and target of these AppSec tools vary according to programming languages like Python, Java, JavaScript, and GO. Each programming language has specific characteristics and design.
While the SAST tools are effective in most cases, the vulnerability identification process and accuracy vary according to the programming languages. When implementing a SAST for Python, Java, JavaScript, or Go, make sure it is effective and compatible with your programming language nuances. An effective SAST result will be highly accurate and generate low false positives, leading to secure coding. Try CloudDefense.AI’s new AI-SAST, book a free demo of QINA CLARITY.







