AI coding assistants like Cursor and Windsurf are no longer a concept for developers. It has become a widespread phenomenon. Most developers are harnessing the prowess of AI code editors to enhance their productivity and streamline complex coding tasks. However, this highly productive software development process also introduces vulnerabilities and security threats through AI code.
Since Windsurf and Cursor are trained on different third-party models, they often inherit vulnerabilities associated with them. An effective way to maintain development without compromising on AI code security is the Shift Left AI code approach. This guide will help you implement the shift left strategy to integrate AppSec early into the software development workflow involving Cursor and Windsurf.
What is the Shift Left Approach?
Shift left approach in application security is a modern strategy to enforce security early in the SDLC. Usually, security testing is done at the end of SDLC. However, this approach indicates security testing should be done early in the application and software development phase.
It helps security teams to identify and mitigate vulnerabilities as early as possible rather than addressing them after development. It is a proactive security strategy that is highly useful in assisted software development processes. It secures the AI code as they are generated and reduces costly mitigation costs.
Primary Benefits of Adopting Shift Left
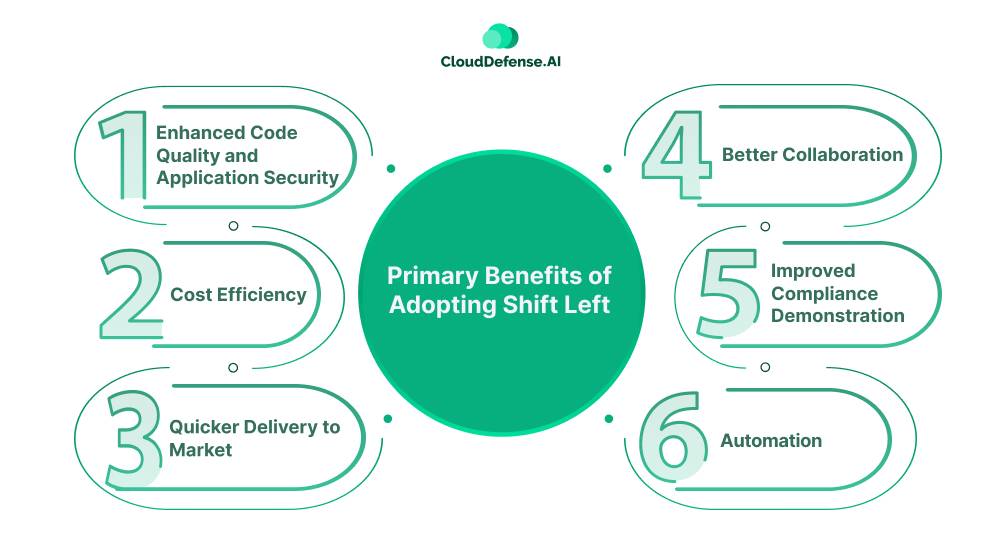
Implementing shift lift in AI-driven software development benefits the organization in many ways:
- Enhanced Code Quality and Application Security: Embedding security from the beginning of SDLC prevents the addition of vulnerability through AI code. This approach helps in assessing AI code from Cursor and Windsurf for vulnerabilities before they are added. Thus, it enhances code quality and improves application security.
- Cost Efficiency: The shift left approach helps organizations detect and mitigate vulnerabilities early in the development stages. This approach safeguards the organization from the expensive process of fixing those vulnerabilities in the post development stage.
- Quicker Delivery to Market: Adopting shift left helps the organization eliminate any delays due to vulnerability remediation action or development tasks. It fixes all the issues in the beginning to lower the deployment time and deliver applications quickly. It is highly useful with DevSecOps development involving AI-code editors.
- Better Collaboration: When an organization opts for this approach, it helps in building strong communication between developers, security, and the QA team. It promotes shared responsibility so that everyone can work together to effectively mitigate security threats.
- Improved Compliance Demonstration: The shift left approach involves integrating security tools early in the development phase. This helps the organization to showcase its compliance with all the necessary industry regulations. Importantly, it helps organizations in addressing any compliance issue in the early stage and avoids fines associated with it.
- Automation: A huge benefit of this approach is that it favors the implementation of automated security security in the software development environment. This not only reduces various errors but also an effort to perform various complex development tasks.
Why Is Shift Left Necessary for AI-Assisted Development Process?
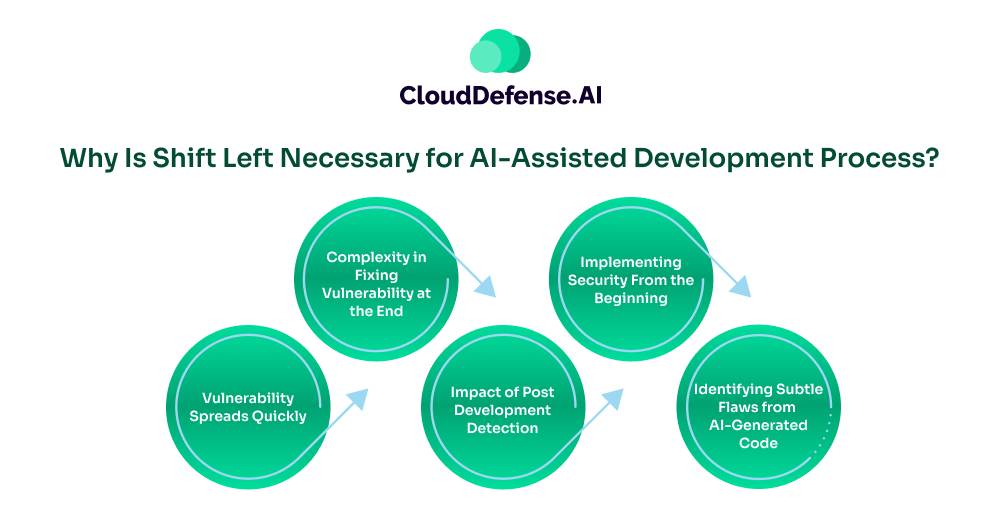
Organizations relying on AI coding assistants like Cursor and Surfer can’t efficiently use traditional security tools. These standard tools are infective against the huge amount of AI code that is generated while developers write code. Here are some crucial reason that makes shift left a necessity:
- Vulnerability Spreads Quickly: AI code editors utilize a lot of third-party dependencies that may carry vulnerabilities. When an insecure AI code is committed by multiple developers without proper security checks, vulnerability can spread quickly.
- Complexity in Fixing Vulnerability at the End: Identifying and fixing vulnerabilities from AI code at the end of the SDLC introduces a lot of tasks. Not only does the remediation process get complex but it also hampers the productivity of the development process.
- Impact of Post Development Detection: The approach to assess and discover vulnerabilities introduced by AI code post development, can severely impact the organization. Security threats identified in the production stage can cause hefty fixing costs, data loss, the possibility of security breaches, and damage to reputation.
- Implementing Security From the Beginning: AI code assistant tools generate a lot of AI code at speed. So it becomes a necessity to introduce security from the beginning. The shift left approach helps in implementing security in the development phase and promotes the culture of security as a shared responsibility.
- Identifying Subtle Flaws from AI-Generated Code: Cursor or Windsurf often generates AI code that is functional but carries subtle insecure patterns that are difficult to identify. However, the shift left approach involves automated security tools that can identify those subtle vulnerabilities and fix them before they lead to critical security threats.
Enforcing Shift Left Strategy to Identify Vulnerabilities Early in AI-Assisted Workflow
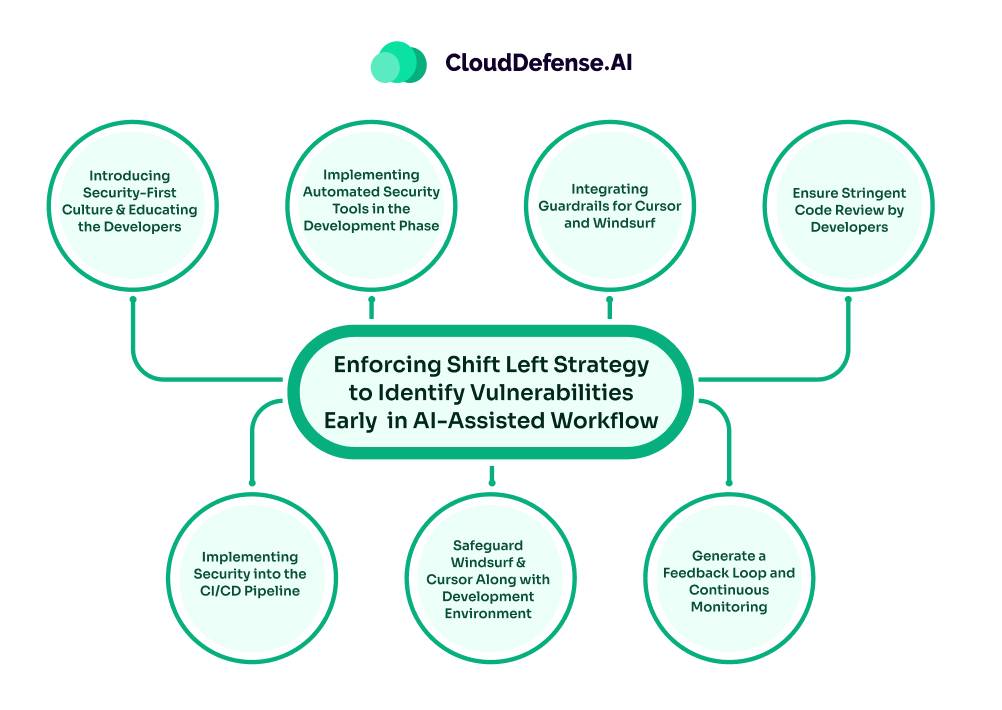
Enforcing the shift left strategy for the Cursor and Windsurf secure pipeline is not only about implementing security tools. It requires a careful and multi-step approach to effectively apply the strategy:
Step 1: Introducing Security-First Culture and Educating the Developers
The first step to enforcing the shift left strategy for Windsurf and Cursor early security is to introduce a security-first approach. Organizations must conduct training to make developers aware of vulnerabilities associated with AI and how they are introduced. The training should also cover application-related vulnerabilities from OWASP’s top 10 and SANS’s top 25.
To effectively implement the shift left strategy, training developers to input secure prompts is crucial. Organizations must conduct workshops to educate developers in creating secure prompts with specific security requirements for vulnerabilities.
Developers must be provided with guidelines that will prevent them from including secrets in the prompts for Cursor and Windsurf. In addition, AI code must be treated as an insecure component from the beginning and they should be reviewed thoroughly.
Step 2: Implementing Automated Security Tools in the Development Phase
Introducing AppSec early requires integrating automated security tools in the IDE and workflow involving Cursor and Windsurf. Here are the tools organizations can integrate:
- SAST: Static Application Security Testing tool is a highly effective tool that should be integrated within the IDE as a plugin. Developers need to configure the tool so that it can provide real-time alerts regarding vulnerabilities in the AI code. The ruleset also needs to be configured to identify common vulnerabilities.
- SCA: Along with SAST, organizations also need to implement Software Composition Analysis tools. When integrated into the IDE, it will automatically assess the dependencies associated with the AI code from Cursor and Windsurf. It will alert the teams regarding known vulnerabilities in these dependencies and provide suggestions for remediation.
- Secret Detection: This tool will automatically scan the AI code in real time to identify hard-coded secrets and prevent them from getting deployed. It will integrate with IDE to prevent the committing of any AI code carrying a password or API key.
- IaC Scanner: Organizations can also utilize it in the development environment when Cursor and Windsurf are used for creating IaC templates. It will identify and provide alerts regarding any misconfiguration that can cause security issues in the infrastructure.
Step 3: Integrating Guardrails for Cursor and Windsurf
Along with automated security tools, organizations also need to implement AppSec guardrails for all the AI-generated code from Cursor and Windsurf:
- RBAC: Organization should deploy Role Based Access Control as Windsurf is often configured to perform tasks like executing commands autonomously. RBAC will help security teams in regulating their access privileges and other capabilities based on POLP.
- Input Validation: Security teams need to deploy processes that assess all the input prompts in Cursor and Windsurf. It will identify malicious instructions or injection attacks in prompt and prevent them from execution.
- Secure Prompt Guideline: Organizations can also set detailed guidelines or best practices for writing prompts that will help in generating secure AI codes.
- AI-Generated Code Sanitization: A plugin or dedicated tool must be implemented that will automatically check all the AI code. The main aim is to check the AI code against a set checklist and identify any malicious pattern, hard-coded secret, or insecure function.
- PaC: Organization can also work to establish compliance policies as code in the development stage. It will ensure AI code follows all the requirements.
Step 4: Ensure Stringent Code Review by Developers
Organizations must develop policies to mandate stringent code reviews. All the AI-generated code must be reviewed by experienced developers. They should flag AI code that involves authorization and authentication functionality.
While reviewing the AI code, developers should also emphasize understanding the logic and its impact on the application. Four-eye principles can also be established when developers are working on sensitive modules.
Step 5: Implementing Security into the CI/CD Pipeline
For the shift left strategy, integrating security checks into the CI/CD pipeline also serves as a vital aspect. SAST, SCA, DAST, and IAST tools must be integrated into the CI/CD pipeline. These tools will serve as security gates that will prevent deployment when critical vulnerabilities are detected in the code. In addition, organizations can also include tools to automate the security analysis of APIs for security flaws or unusual authentication.
Step 6: Safeguard Windsurf and Cursor Along with Development Environment
Along with securing the AI-generated code, organizations must secure the AI coding assistants and development environment. To safeguard all the tools:
- Update the Tools and Plugins: All the AI tools especially Cursor and Windsurf should be regularly updated. It will help in patching misconfiguration or vulnerabilities in the tool. Along with the tools, plugins, and IDEs should also be updated for security patches.
- Establish a Secure Configuration for AI Tools: Security can apply secure configuration on Cursor and Windsurf. These configurations must adhere to best security practices and prevent unnecessary privileges or data-sharing functions.
- Secure all The Secrets: On many occasions, Windsurf and Cursor may utilize various secrets like API keys for different operations. A secure storage must be introduced to manage the secrets and prevent accidental leakage.
Step 7: Generate a Feedback Loop and Continuous Monitoring
Shift left strategy is not a one-time implementation, it is a continuous process. An organization must track and log all the activities and code suggestions of Cursor and Windsurf.
In addition, it would be helpful to maintain a detailed log of identified vulnerabilities and their origin. Based on the security findings, security teams must reconfigure the guidelines and update training resources.
Conclusion
Cursor and Windsurf have enabled modern organizations to cope with modern requirements and make significant advancements in software development. However, these AI coding assistants need to be utilized securely to prevent them from introducing vulnerabilities in the application or software.
Implementing a shift left strategy in the AI-assisted development workflow will help organizations to develop applications rapidly without compromising on security. For most organizations, shift left strategy is no longer an option, it has become a necessity to securely utilize the Cursor and Windsurf. This guide will navigate you to seamlessly implement a shift left AI code strategy in your organization and identify vulnerabilities at earliest.







