What is a CRLF Injection Attack?
A CRLF injection attack is a notorious cyber threat or can be defined as a web application vulnerability that occurs when a cybercriminal alters the CRLF with malicious characters into the HTTP response.
The term CRLF refers to the special character elements, where CR indicates Carriage Return (\r) and LF indicates Line Feed (\n). This type of attack arises when the user input is not properly sanitized or validated by the web application before constructing its HTTP response. The attacker utilizes this opportunity to inject the malicious CRLF character into user input to manipulate the HTTP response.
When the attacker injects the characters, it deceives the server into considering that an object has been terminated and a new one has begun. The primary two use cases of CRLF injection are HTTP response splitting and log poisoning which is also known as log injection and log splitting.
This type of injection attack often leads to more malicious attacks on web applications like cross-site scripting, page injection, cache-based defacement, session fixation, and many more. CR and LF are used to denote the ending point of a line and as it separates the header from the content, it enables the server to know when a new header begins or ends.
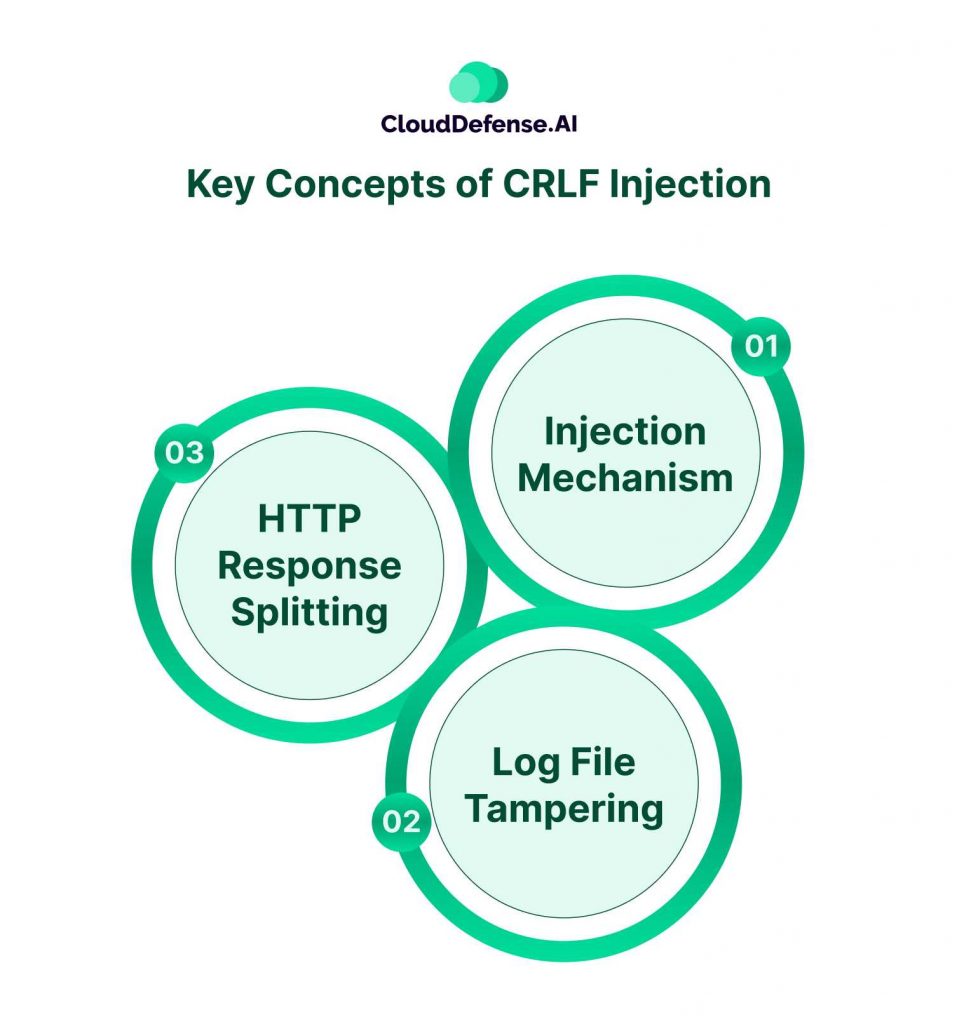
Key Concepts of CRLF Injection
As you have already understood, a CRLF injection attack is basically a web application coding vulnerability that happens when cybercriminals put in a crafted CRLF character. The data input, when incorrectly neutralized, unsanitized, or not neutralized, gives rise to the vulnerability.
Using the specialized text stream, attackers trick web applications into performing harmful and unexpected actions. As the crafted CRLF sequence splits the text stream to embed a text sequence, it causes a serious breach in the web application and modifies the sensitive data. The CRLF injection encompasses three primary concepts:
Injection Mechanism
The injection mechanism serves as one of the primary pillars of a CRLF injection attack. A cyberattacker injects a crafted CRLF sequence into the user input data, which generates a random HTTP head or often splits the HTTPS response. Due to the crafted CRLF sequence, it terminates the existing line and starts a new one.
Log File Tampering
Another key concept of a CRLF injection attack is log file tampering. Through this attack, attackers can put random entries into the application log that are done through a crafted CRLF sequence, and this makes the logs unreliable. As a result, the system administrator can’t track or assess the activities happening within the system.
The sequence is crafted in such a way that the malicious input comes as log entries, and this allows the cybercriminals to generate fake trails, hide malicious activities, and expose the data of users.
HTTP Response Splitting
A CRLF injection attack is carried out by injecting a CRLF character into the user input, and this manipulates the HTTPS response header and body. Due to this injection, attackers get the ability to create multiple HTTPS responses from a single HTTPS response. The splitting of HTTPS response is utilized by attackers in various ways, like changing the response content and generating arbitrary HTTP headers.
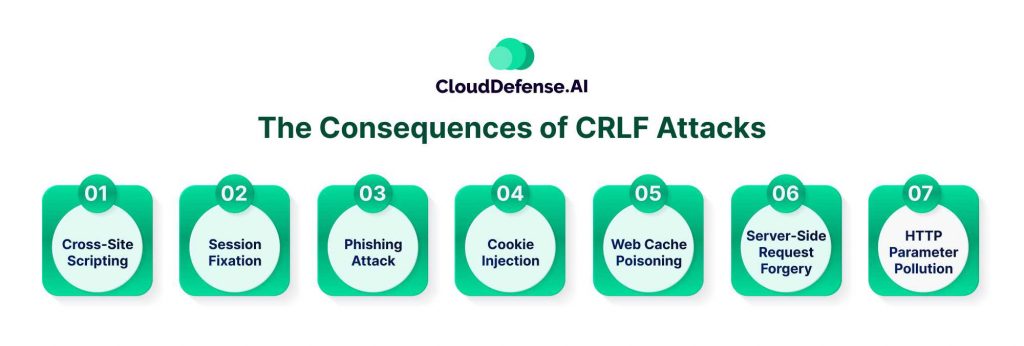
The Consequences of CRLF Attacks
The CRLF attacks lead to varying consequences, and it goes beyond the preconceived norms. Through this attack, a cybercriminal can perform varied types of malicious activities that can impact an enterprise in many ways. Let’s take a look at the consequences of CRLF attacks:
Cross-Site Scripting
Cross-site scripting or XSS is one of the major consequences of CRLF attacks that allows cybercriminals to push malicious scripts into web pages fed to others. XSS is a serious security vulnerability that arises when the attacker splits the HTTP header to inject a malicious script into the endpoint’s browser.
This security vulnerability has a varied impact where some XSS can lead to data leakage. However, some major impacts of cross-site scripting include unauthorized entry into sensitive data and manipulating the user’s interaction with the web application through the browser.
Session Fixation
CRLF injection attack can also lead to a session fixation attack by manipulating or modifying the session identifiers in the header. In this type of attack, the cybercriminal creates a session identifier and manipulates the user into using the malicious session.
On many occasions, cybercriminals cause session fixation to trick victims into using specific sessions that also lead to other attacks.
Phishing Attack
Another major consequence of the CRLF attack is the phishing attack, which serves as one of the favorite choices of attackers to deliver malware to the victim’s system. When the attacker modifies the HTTP header through CRLF injection, they can redirect the victim to a malicious website or show them a fake web page containing malicious content.
Through the malicious website, the attacker tricks the victim into providing sensitive information or downloading malicious programs. Using this attack type, the cyberattacker gets unauthorized entry into the system, which leads to serious threats to the enterprise. From financial loss and data loss to reputation damage, CRLF injection has a huge consequence on the organization.
Cookie Injection
The attacker often leverages a CRLF injection attack to launch cookie injection, and it is done by inserting additional Set-Cookie header fields into the HTTP header. Through CRLF injection, the attacker manipulates the HTTP header and gets the ability to make modifications to the browser’s cookie, leading to strange and malicious behavior.
In cookie injection attacks, the cybercriminal usually changes the user’s settings by manipulating the cooking or setting a cookie for a malicious domain. When such modification occurs, it not only causes unauthorized access to the victim’s account but also impersonation of identity.
Web Cache Poisoning
You will be surprised to know the attacker also leverages the CRLF injection attack to modify the cache control header in the HTTP, and it leads to web cache poisoning. Web cache poisoning is basically the caching of malicious content that affects users who access them, leading to the spread of the malware.
Unlike other CRLF injection attacks, web cache poisoning is highly sophisticated and can be difficult to detect and prevent by security solutions. This attack utilizes a caching proxy and web application, making it difficult to identify.
Server-Side Request Forgery
CRLF injection attacks are often utilized by cybercriminals to commence server-side request forgery or SSRF attacks on the endpoint user. Through the CRLF injection, the cybercriminal injects the crafted malicious request and tricks the server into believing it is a valid request to internal sources, causing the launch of an SSRF attack.
This type of attack is difficult to carry out, but if the attacker is successful, it can allow them to gain unauthorized access to numerous resources.
HTTP Parameter Pollution
HTTP parameter pollution is a dangerous attack that arises due to CRLF injection attacks. Cybercriminals leverage CRLF injection to modify the query string parameter, and it causes HTTP parameter pollution attacks. In such an attack, the web application operates the parameter in an unusual way.
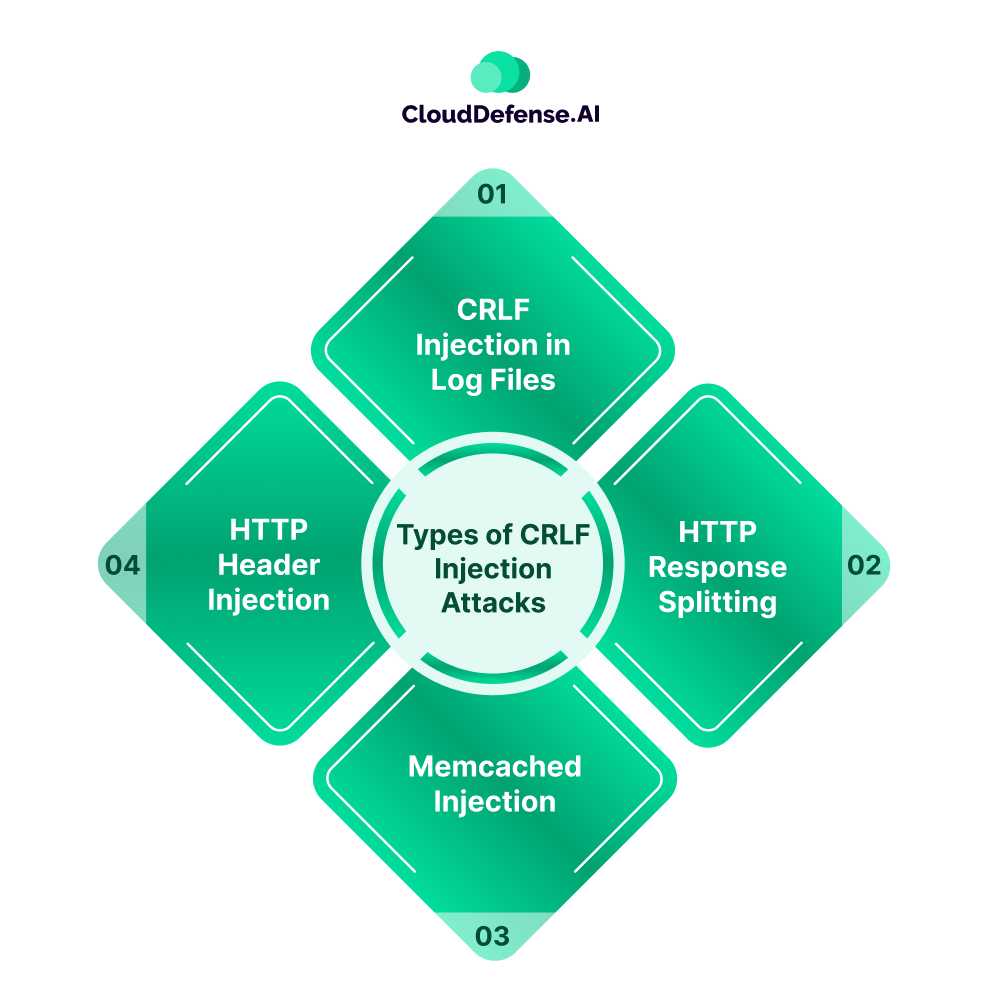
Types of CRLF Injection Attacks
Cybercriminals take advantage of various types of CRLF injection attack types to carry out their malicious intents. Here,are some common types mostly observed by security administrators:
CRLF Injection in Log Files
A common type of CRLF injection attack leveraged by an attacker is CRLF injection in log files, which has serious implications for the integrity of the log data. In this type, the cybercriminal takes advantage of the structure of log files and injects false information, which makes it difficult for security administrators to detect malicious activity properly.
The attackers inject crafted CRLF characters into the HTTP request, enabling them to modify the log file’s content that appears as 123.123.123.123 -22:34- /index.php?page=home. Usually, the modification is accomplished by putting the encoded CRLF character along with the fake log entry into the request query.
So when the server processes the request, it perceives the CRLF character for line termination and starts a new entry, causing a change in the log entry. The manipulation is done in such a way that the log entry will seem to the security team as if it has come from a trusted source. As a result, no one can identify the original source of the malicious activity.
HTTP Response Splitting
Considered the most common type of CRLF injection attack, HTTP response splitting is all about injecting a special CRLF character string into the HTTP response header. Usually, the special CRLF sequence is inserted to split the response into two separate ones. However, it is often used to control the response body and add random headers.
In most occasions, user input is directly added to the HTTP header without sanitizing the CRLF string, and this enables the attacker to put crafted CRLF characters to carry out their malicious actions.
Suppose a cybercriminal puts up a crafted CRLF character into the HTTP header, it would trick the server into considering subsequent input as a new HTTP response. As a result, attackers get the option to make changes in the cache, which gives them the ability to launch XSS and other cyber attacks.
Memcached Injection
The Memcached injection is a unique type of CRLF injection attack where crafted CRLF characters are injected into the values that are kept in Memcached or any other caching system.
When a malicious CRLF character is injected, it gives the attacker the ability to manipulate cached data, which ultimately leads to the poisoning of cached data and unusual application behavior. Many attackers, through Memcached injection, attempt to corrupt the Memcached entries and use them to perform their malicious activities.
HTTP Header Injection
HTTP header injection is another popular choice that is widely used by attackers as it enables them to inject malicious headers and infect various aspects of browsers. This CRLF injection attack type has many similarities with HTTP response splitting, but in comparison to the later type, it is designed to inject crafted headers.
According to its malicious intent, an attacker might put up a set cookie header, and this causes the endpoint’s browser to store the malicious cookie. Using the malicious cookie, the attacker can deliver malware which can help to track browsing data and other activities. On various occasions, malicious headers are inserted without any sanitization, and due to this, attackers can input their malicious code to manipulate the browsing sessions.
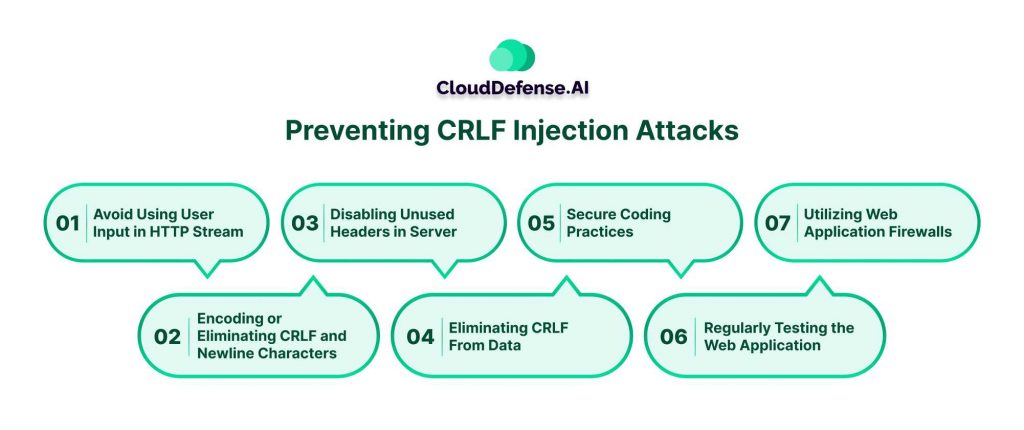
Preventing CRLF Injection Attacks
Given the sophistication of CRLF injection attacks, it is quite challenging to prevent them. However, to tackle the advancement of such attacks, security experts have come up with effective preventive measures. Here are some preventive measures:
Avoid Using User Input in HTTP Stream
Most of the user input in the HTTP header is accepted without sanitization, and this leads to web application vulnerabilities. Putting user input directly into the HTTP stream might seem convenient, but attackers exploit this opportunity to put their crafted CRLF sequence that leads to modification in structure.
As a result, the attacker can access all the activity, steal data, and perform other malicious actions. The best way to prevent this kind of scenario is to avoid putting user input directly and make sure the input is properly validated and sanitized. You can automate the sanitization of user input to streamline the overall process.
Encoding or Eliminating CRLF and Newline Characters
To prevent CRLF injection attacks, you should also encode CRLF characters while putting them in the user input stream. Due to encoding, the CRLF character changes into a format that doesn’t cause the server to consider it as a line break.
So, even if the attacker injects malicious CRLF characters into the user input, it can’t modify the HTTP header. Besides, the attackers also use newline characters to inject crafted CRLF characters into HTTP headers. It is always a best practice to remove newline characters before putting them into the HTTP header.
Disabling Unused Headers in Server
Every HTTP response comes with a set of headers, but not all headers are necessary to provide information about the response. However, not all headers in the series are necessary and you should disable them as it will reduce the chance of vulnerability in the web application.
Limiting the HTTP responses only to suitable headers will prevent the attacker from exploiting the unused headers and launching a CRLF injection attack. There are many ways to filter the header that are unnecessary or unused, and you should use them to filter the required one.
Eliminating CRLF From Data
Another effective way to prevent a CRLF injection attack is by eliminating all the CRLF sequences from the user data while logging data. Many system administrators log users in the browser for tracking and security purposes.
However, cybercriminals capitalize on this situation and inject crafted CRLF sequences into the data to carry out their malicious intent. So, removing any CRLF sequence eliminates the chance of any vulnerability and prevents attackers from using the sequence to manipulate HTTP headers.
Secure Coding Practices
Every developer in your organization should opt for secure coding practices while developing the web application. They should follow all the industry guidelines that will keep the code secured. There are many approaches that you can follow to secure the code during the development process.
Regularly Testing the Web Application
Regularly conduct tests on the web application to discover the manipulated cached entries and CRLF sequences, along with other security issues. Make sure all the security flaws that lead to web application vulnerabilities are fixed. Moreover, the web application should be updated with security patches that help in eliminating vulnerabilities.
Utilizing Web Application Firewalls
Implementing a web application firewall is another effective way to prevent the CRLF injection from affecting your web application. What WAF does is it monitors and filters HTTP requests and responses and prevents the inclusion of any malicious CRLF sequences in the user input. Thus, it blocks the crafted CRLF characters from reaching the application and prevents the attackers from exploiting vulnerabilities.
CRLF Protection with CloudDefense.AI
In today’s modern security landscape, CloudDefense.AI has emerged as one of the leading solutions to protect web applications from CRLF injection attacks. With its web app security, CloudDefense.AI offers real-time monitoring, advanced threat detection, and rapid incident response to prevent all types of CRLF injection attacks.
Not only can you perform thorough detection and implement Zero Trust protection, but you can also adhere to industry-specific regulation requirements with the Airtight Checklist. Along with the web app security, CloudDefense.AI also offers you:
DAST: CloudDefense.AI, through its CNAPP platform, offers an advanced DAST solution geared with black box testing, complete visibility, and runtime vulnerability detection to uncover vulnerabilities that can lead to CRLF attacks.
API Scanning: The powerful API security solution will help your enterprise to proactively safeguard your web application by identifying and mitigating vulnerabilities.
IaC Scanning: You can also leverage the IaC scanning solution from CloudDefense.AI that scans and mitigates vulnerabilities in your CI/CD pipelines and helps you prevent vulnerabilities from the beginning.
SCA: The advanced SCA tool serves as an effective solution to identify and mitigate CRLF injection attacks as it comes with deep code analysis and real-time context to eliminate vulnerabilities.
Conclusion
We are hopeful we have been able to answer your query of “What is a CRLF injection attack?” and give you an in-depth idea regarding this web application vulnerability.
Through this article, we have tried to cover all the possible aspects associated with CRLF injection attacks so that you can have detailed ideas while preparing your security strategy. We have also highlighted how you can prevent CRLF injection attacks and why CloudDefense.AI serves as the best security solution to help you in the process.







