What is Secure Code Review? Definition of Secure Code Review
A secure code review is a systematic process of examining software source code to detect and fix security vulnerabilities. It can be manual, involving human inspection, or automated, using tools to scan for issues.
Manual review provides contextual understanding, while automated review offers speed. Both methods aim to improve the software’s security by identifying weaknesses in the codebase. This approach saves time, money, and reputation by preventing potential breaches and attacks.
How does Secure Code Review work?
A secure code review is a structured approach that combines manual and automated processes to assess code for potential vulnerabilities and security flaws thoroughly. Here’s how it works:
- Initiation of Code Review: Secure code review can be initiated automatically or manually, triggered by notifications or set at specific stages in the SDLC. This review can take place at any point, though starting early in the process allows for faster, easier adjustments to the code.
- Automated Code Review During Development: Automated tools scan the code in real-time as developers write, identifying issues immediately. Using tools such as SAST, developers can detect and address vulnerabilities in real time, promoting quick fixes before code moves further along the SDLC.
- Manual Review for Contextual Insight: Once code is ready for commits or merges, manual review becomes critical. Experienced developers review code manually, focusing on business logic, developer intentions, and nuanced security issues that automated tools may not catch. This step ensures that code not only functions securely but also aligns with business needs.
- Self-Review: Developers perform their own quick reviews while coding. This proactive approach ensures they catch basic issues and align code quality with security standards, enhancing secure coding practices throughout development.
- QA and Combined Analysis: QA testing complements code review by verifying functionality under realistic scenarios. Integrating insights from both automated tools and manual reviews ensures thorough security validation.
The combined approach ensures secure code review is efficient, catches a wider range of vulnerabilities, and aligns code security with business logic and compliance requirements.
Why is Secure Code Review Important in SDLC?
Secure code reviews are essential in the SDLC, strengthening application security by identifying vulnerabilities before deployment. As businesses increasingly depend on software, secure code reviews serve as a critical safeguard against potential breaches.
Integrating secure code reviews into the SDLC reduces the likelihood of security incidents by detecting vulnerabilities early, allowing developers to address issues swiftly. This process also reinforces code quality by encouraging secure coding practices, which strengthen overall software integrity.
Additionally, secure code reviews promote a security-aware culture within development teams, making developers more conscious of security risks in future projects. Unlike standard code reviews, secure code reviews specifically target security vulnerabilities, such as input validation flaws, authentication issues, and data leakage risks.
Elements of Secure Code Review
Effective secure code review relies on several essential elements:
- Integration of Manual and Automated Reviews: Combining manual inspection with automated scanning ensures comprehensive vulnerability detection and coverage, addressing issues that tools or humans alone might overlook.
- Collaborative Knowledge Sharing: Engaging the team in knowledge-sharing sessions and discussions about lessons learned promotes a shared understanding of security best practices, strengthening code quality.
- Metrics and Data-Driven Insights: Analyzing code review metrics helps identify recurring vulnerabilities and reduces defects and policy violations, creating a refined process before merging code into production.
Together, these components enhance the codebase’s security, quality, and consistency.
The Effective Secure Code Review Process
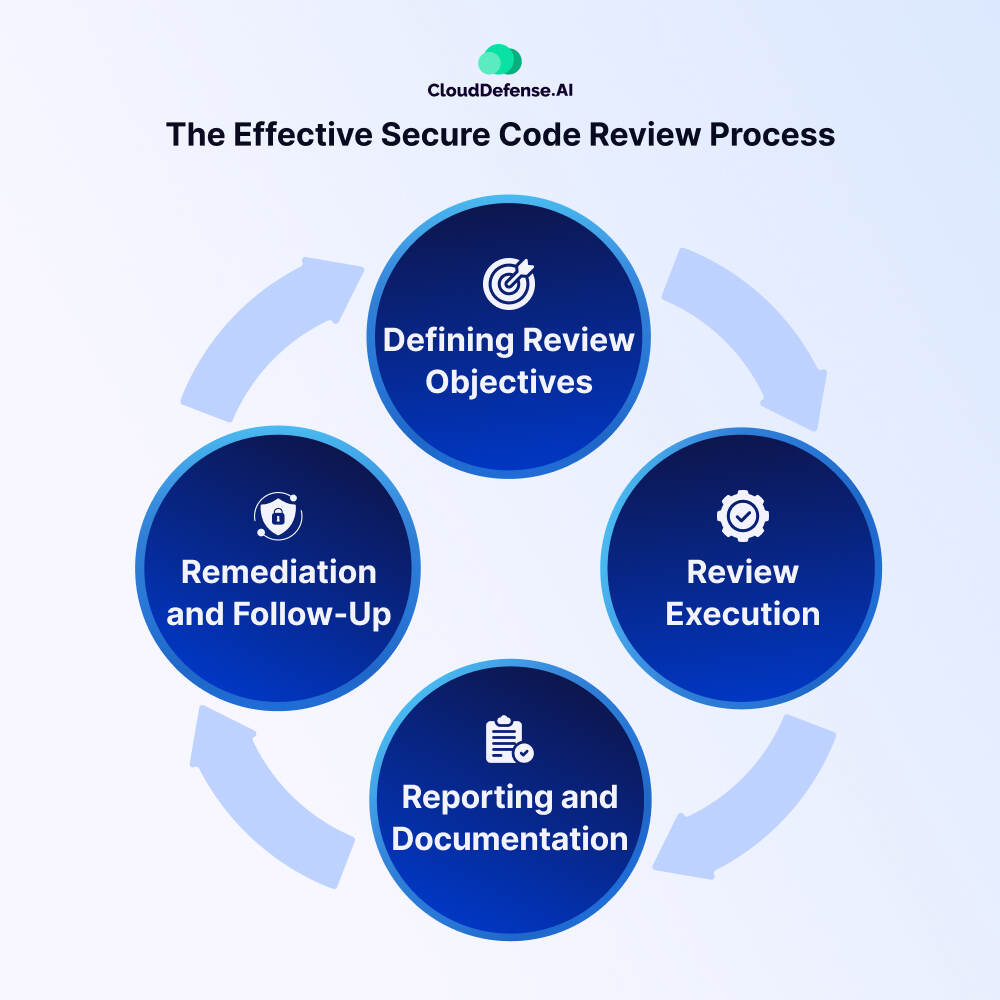
The secure code review process is not a one-time event but rather a continuous and systematic approach aimed at identifying and diminish security vulnerabilities in software applications.
- Defining Review Objectives: This initial stage involves setting clear objectives for the code review. Understanding the key areas of concern and the types of vulnerabilities to be detected helps focus the review efforts. Additionally, gaining insights into the application’s architecture and functionality aids in guiding the review process. Defining the scope of the review is essential for prioritizing code segments that require examination.
- Review Execution: The execution stage involves the actual review of the source code. This can be performed manually by skilled reviewers who analyze the code line by line, searching for potential security vulnerabilities. Common issues such as injection attacks, cross-site scripting, and insecure object references are among the targets. Alternatively, automated tools can be utilized to scan the codebase for known vulnerabilities and generate reports of identified issues.
- Reporting and Documentation: Once the review is complete, the findings must be documented and reported comprehensively. This involves creating a detailed report outlining the identified vulnerabilities, their severity levels and recommended remediation steps. The report serves as a valuable reference for the development team and aids in tracking the progress of remediation efforts. Automated security testing tools can enhance the generation of these reports, ensuring clarity and consistency.
- Remediation and Follow-Up: The final stage involves addressing the identified vulnerabilities through remediation efforts. The development team implements the recommended fixes to mitigate the security risks effectively. Following remediation, a follow-up review is conducted to verify that the vulnerabilities have been adequately addressed. This ensures that the application’s security posture is strengthened, and any remaining issues are promptly resolved.
Benefits of Secure Code Reviews
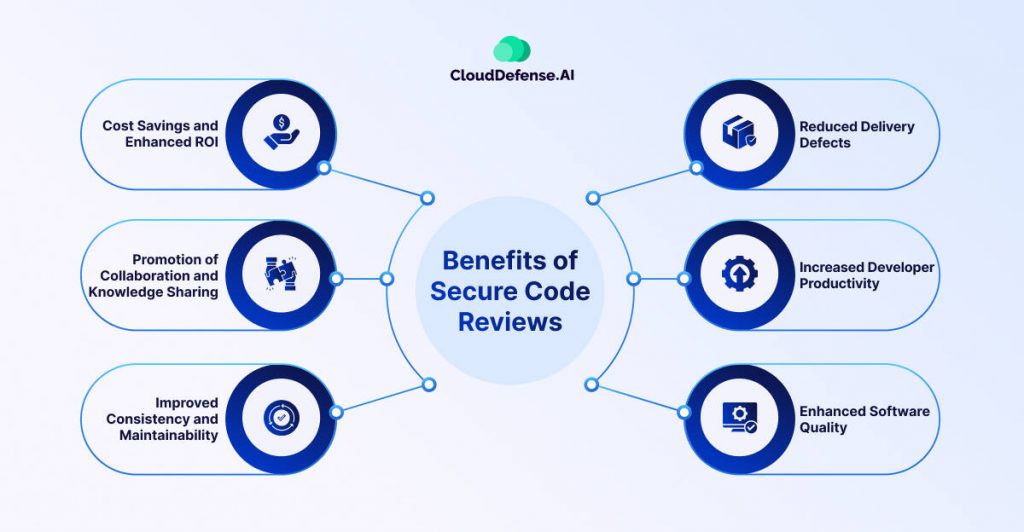
Secure code review offers a range of benefits to development teams and organizations, making it an irreplaceable practice for ensuring the security, quality, and efficiency of software development. Here are some key advantages:
Reduced Delivery Defects
By identifying and addressing security vulnerabilities early in the SDLC, secure code review helps to reduce the number of defects that would otherwise be discovered at later stages. This minimizes the likelihood of costly rework and delays in product delivery.
Increased Developer Productivity
Addressing defects during the development phase consumes significantly less time and effort compared to fixing them in later stages. Secure code review enables developers to catch and rectify issues promptly, leading to increased productivity and smoother project progression.
Enhanced Software Quality
By systematically reviewing code for bugs and security vulnerabilities, secure code review contributes to the overall quality of the software. Fewer bugs and vulnerabilities in the codebase result in more strong and reliable applications, ultimately leading to improved user satisfaction and trust.
Improved Consistency and Maintainability
Secure code review helps to enforce coding standards and best practices across codebases, promoting consistency in development practices. Additionally, by identifying and addressing code complexities and dependencies early on, secure code review enhances the maintainability of the software over its lifecycle.
Promotion of Collaboration and Knowledge Sharing
Secure code review promotes collaboration among team members by encouraging peer review and feedback. It provides opportunities for developers to share insights, techniques, and best practices, thereby enhancing collective knowledge and skill levels within the team.
Cost Savings and Enhanced ROI
Investing in secure code review yields long-term cost savings by reducing the overhead associated with addressing security vulnerabilities post-deployment. By detecting and mitigating issues early, organizations can avoid the financial repercussions of security breaches, as well as the expenses related to extensive rework and maintenance.
Tools for Secure Code Review
Secure code review is a critical component of software development aimed at identifying and mitigating security vulnerabilities in applications. Various tools are available to aid in this process, each offering unique capabilities and approaches. Here are some common types of tools used for secure code review:
- Static Application Security Testing Tools: SAST tools analyze source code at a static level, detecting potential security issues without requiring the code to be executed. They scan code line by line, identifying common coding errors and vulnerabilities such as SQL injection and cross-site scripting. While efficient, SAST tools may produce false positives and might miss complex vulnerabilities.
- Dynamic Application Security Testing Tools: DAST tools test applications in their running state by simulating attacks to identify vulnerabilities. They interact with the application like a potential attacker, observing its responses to simulated attacks. DAST tools are effective at detecting runtime errors and input validation errors but may also produce false positives and miss hidden vulnerabilities.
- Interactive Application Security Testing Tools: IAST tools combine aspects of both static and dynamic testing, monitoring an application during execution to identify vulnerabilities. They analyze behavior and data flow, providing a comprehensive review of potential security issues. However, IAST tools can be complex to set up and manage and may impact application performance.
- Software Composition Analysis Tools: SCA tools analyze application components, including libraries and frameworks, to identify security vulnerabilities. They compare components against databases of known vulnerabilities, helping to ensure the security of open-source components. While useful, SCA tools may produce false positives and might not always be up to date with the latest vulnerability databases.
- Manual Code Review Tools: Manual code review tools are essential for complementing automated tools, and providing human judgment and expertise. These tools often include features such as syntax highlighting, code comparison, and annotation capabilities, making it easier for reviewers to identify security issues. While time-consuming and requiring expertise, manual code reviews are indispensable for a comprehensive secure code review process.
Best Practices for Secure Code Review
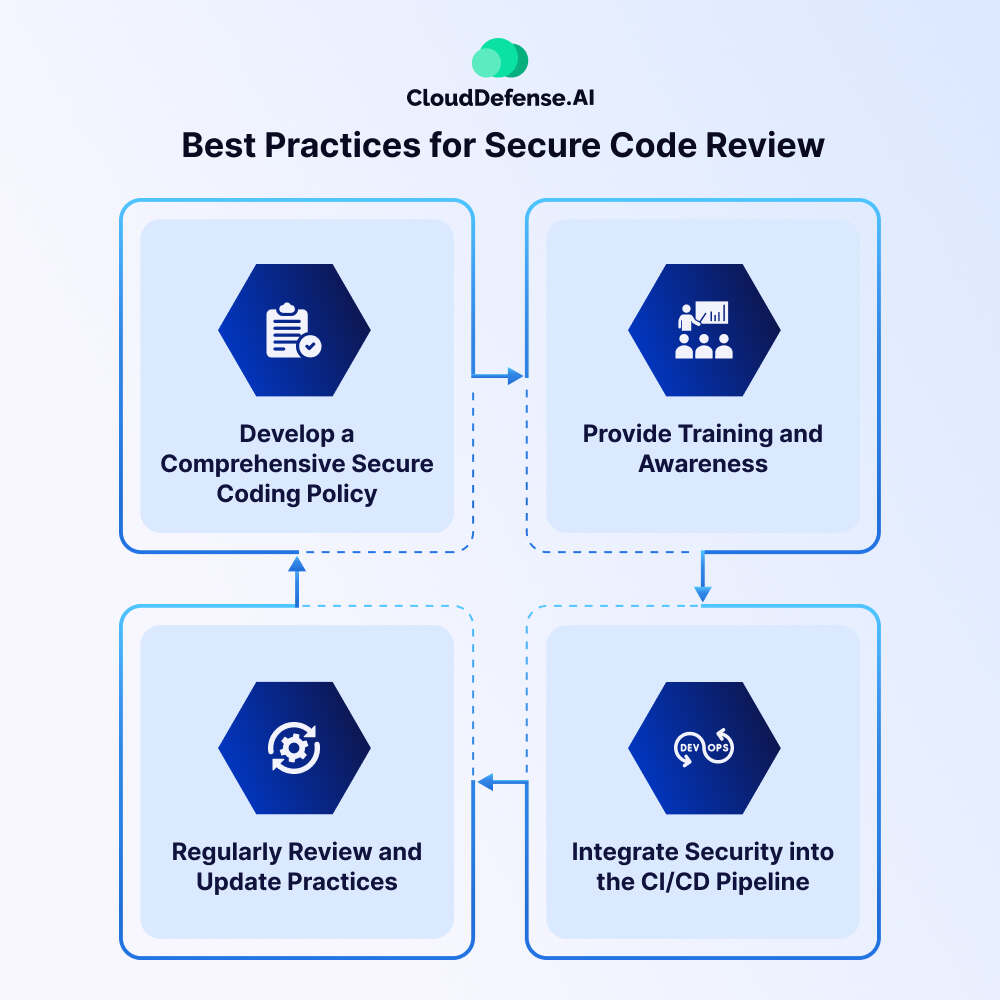
Implementing a secure code review process is essential for protecting software applications against potential security vulnerabilities. Here are some best practices to follow:
Develop a Comprehensive Secure Coding Policy
Create a secure coding policy that outlines principles and guidelines for writing secure code. Cover all aspects of coding, including data handling, user input validation, error handling, and logging. Tailor the policy to your organization’s specific needs and the type of software being developed. Regularly update the policy to address emerging threats and technological advancements.
Provide Training and Awareness
Build a culture of security awareness among your development team by providing regular and ongoing training in secure coding practices. Encourage developers to think with a security mindset and equip them with the knowledge and tools to identify and mitigate potential vulnerabilities. Offer resources for self-learning, such as online courses and workshops, and facilitate practical, hands-on training exercises.
Integrate Security into the CI/CD Pipeline
Incorporate security into your CI/CD pipeline to catch and fix security issues early in the development process. Implement strong access controls and secure configuration settings, and regularly evaluate CI/CD tools for vulnerabilities. Automate security testing using tools like SAST and DAST to scan code for flaws.
Regularly Review and Update Practices
Conduct periodic audits of your secure coding policy, training programs, and CI/CD security measures to identify and address any gaps. Stay informed about the latest security trends and threats, and update your practices accordingly. Encourage a culture of continuous learning and improvement among your development team, and provide opportunities for knowledge sharing and growth.
Conclusion
Secure code review is essential for identifying and mitigating vulnerabilities such as SQL injection and cross-site scripting. Automated tools that combine SAST, DAST, and SCA streamline this process by reducing false positives and offering actionable remediation suggestions. Seamless integration with IDEs and CI/CD pipelines ensures that security is embedded throughout the development lifecycle, improving both code quality and development efficiency.







