What is CSRF?
Cross-Site Request Forgery, often abbreviated as CSRF or XSRF, is a web security vulnerability that thrives on tricking your browser into executing unwanted actions on a trusted website where the user is currently authenticated. Unlike other web vulnerabilities like XSS (Cross-Site Scripting) that rely on injecting malicious code, CSRF exploits the trust a website has in a user’s browser
Here’s the twist: Behind the scenes, that seemingly innocent click triggers your browser to send an unauthorized request to your bank’s website. This request, however, originates from the attacker’s crafted link, not from your intended actions. Because your browser already has a valid session cookie with the bank, the website processes the request as if it came from you. This is the essence of CSRF – an attacker manipulating your trusted browser session to perform unauthorized actions on your behalf.
The real kicker? You don’t even need to be active on the website for CSRF to work. Just having an active login session is enough. Sneaky CSRF attacks can be launched from other websites, emails, instant messages – anything that can trigger a request from your browser.
How Does CSRF Attack Work?
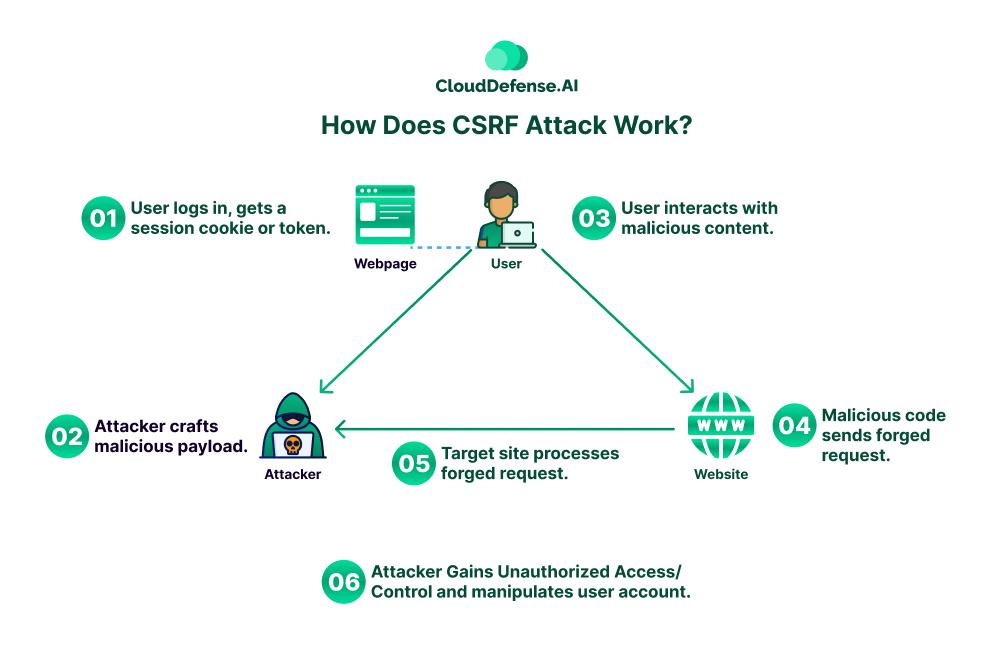
1. User Logs In and Obtains Session Token
The victim accesses a legitimate website and authenticates, receiving a session cookie or token that identifies them as a valid user.
2. Attacker Crafts Malicious Payload
The attacker crafts a malicious webpage, link, or code snippet that contains a forged request targeting the vulnerable website.
3. User interacts with malicious content
The unsuspecting user interacts with the attacker’s malicious content, perhaps by clicking a link, submitting a form, or loading a compromised webpage.
4. Execution of Malicious Request
The malicious code executes in the user’s browser, automatically sending a request to the target website along with the user’s authenticated session credentials (cookie/token).
5. Website Processes Unauthorized Request
The target website receives and processes the forged request because it appears to originate from a legitimate, authenticated user session.
6. Attacker Gains Unauthorized Access/Control
By exploiting the website’s trust in the user’s session, the attacker can gain unauthorized access or manipulate the user’s account actions on the target website without their knowledge or consent.
Exploiting CSRF Vulnerabilities
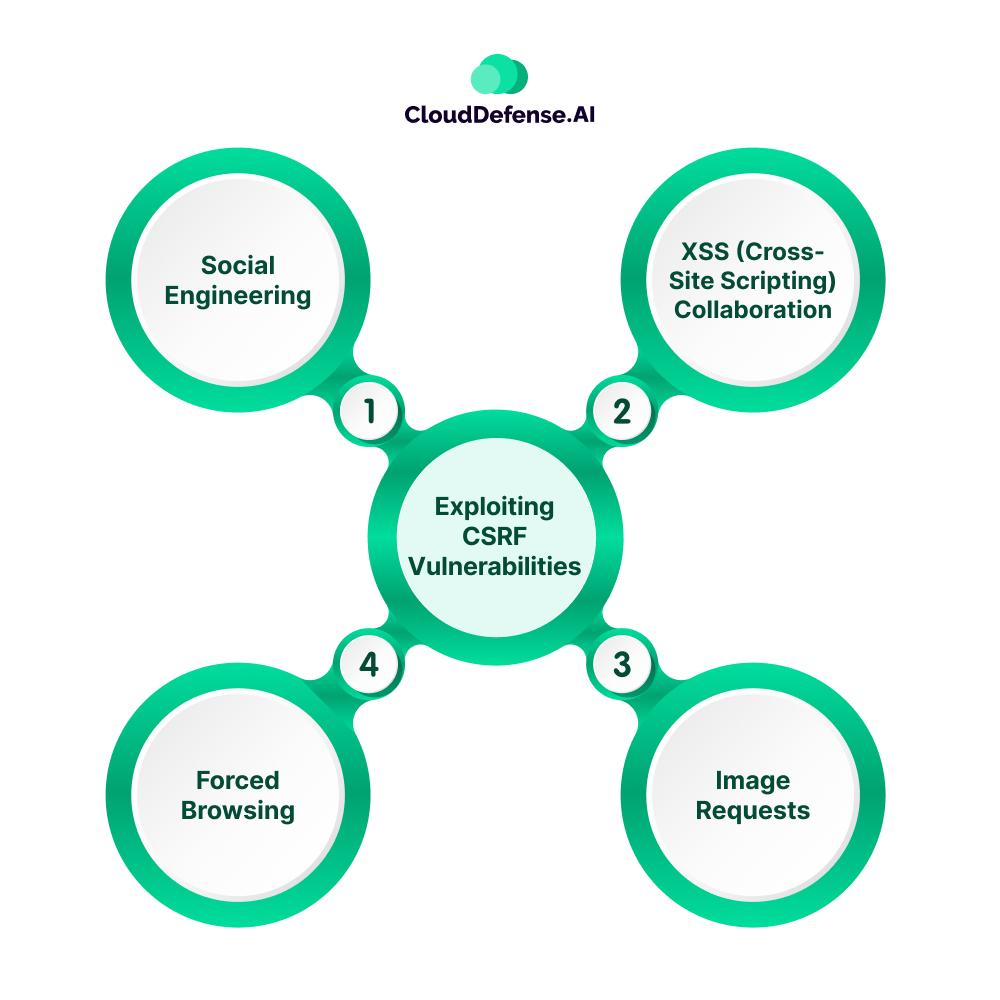
CSRF attacks can have devastating consequences, but how exactly do attackers exploit these vulnerabilities? Here’s a glimpse into their bag of tricks:
Social Engineering
Social Engineering a common tactic where attackers trick users into visiting malicious websites or clicking booby-trapped links. Phishing emails disguised as legitimate sources (like your bank) are a popular method. The email might urge you to click a link to “verify your account” or “claim a reward,” unknowingly leading you to the attacker’s CSRF trap.
XSS (Cross-Site Scripting) Collaboration
Sometimes, attackers combine CSRF with XSS vulnerabilities. An XSS attack injects malicious scripts into a legitimate website. When you visit the compromised site, the script can be used to steal your session cookie or even automatically trigger a CSRF attack in the background without your knowledge.
Image Requests
CSRF attacks can be triggered by seemingly harmless image requests. Attackers can embed malicious code within an image tag on their website. When your browser tries to load the image, it also sends an HTTP request to the attacker’s server. This request can be crafted to exploit a CSRF vulnerability on another website you’re logged into, like your bank.
Forced Browsing
In this technique, attackers might embed a malicious link or form within an iframe (a hidden element) on their website. When you visit the attacker’s site, your browser loads the iframe content in the background. If the iframe contains a cleverly crafted form that automatically submits upon loading, it can trigger a CSRF attack on another website you’re logged into.
These are just a few examples, and new CSRF exploitation techniques are constantly emerging. It’s crucial to stay vigilant and rely on robust security measures to protect yourself from these web-based threats.
How to Find and Fix CSRF Vulnerabilities
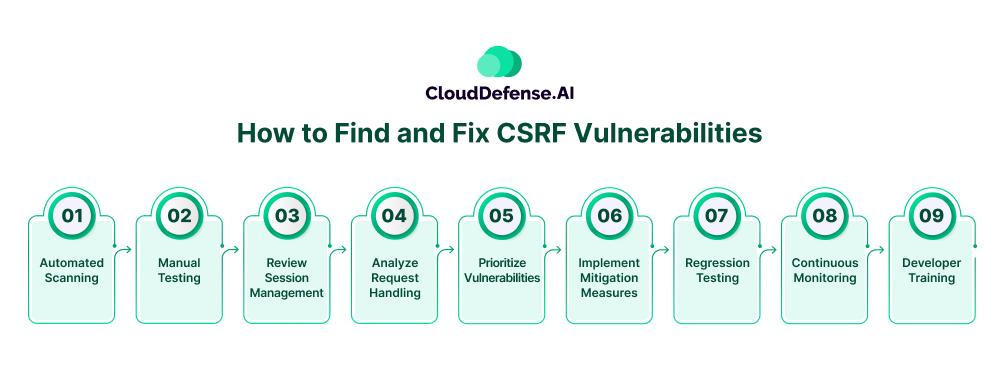
Finding and remediating Cross-Site Request Forgery (CSRF) vulnerabilities is an essential part of securing web applications and protecting users from unauthorized actions. Here are some steps and techniques that can be followed to identify and address CSRF vulnerabilities:
Automated Scanning
- Use automated web application security scanning tools like CloudDefense.AI to scan your application for potential CSRF vulnerabilities.
- These tools can analyze the application’s functionality, simulate user actions, and identify endpoints that are susceptible to CSRF attacks.
- Popular tools like OWASP ZAP, Burp Suite, and others offer CSRF vulnerability detection capabilities.
Manual Testing
- Complement automated scanning with manual testing to identify CSRF vulnerabilities that may be missed by automated tools.
- Manually review the application’s functionality, particularly actions that modify data or perform sensitive operations.
- Simulate cross-site requests by crafting malicious links or scripts and testing them in an authenticated session.
Review Session Management
- Thoroughly review how the application manages user sessions and authentication tokens.
- Identify any weaknesses in session management that could allow an attacker to hijack or forge authenticated requests.
- Ensure that session tokens are sufficiently random, unpredictable, and have appropriate expiration times.
Analyze Request Handling
- Analyze how the application handles incoming requests, particularly those that modify data or trigger sensitive actions.
- Identify any lack of CSRF token validation, referrer header validation, or other security controls that could allow CSRF attacks.
Prioritize Vulnerabilities
- Prioritize identified CSRF vulnerabilities based on their potential impact and the sensitivity of the affected operations.
- Vulnerabilities that could lead to financial loss, data breaches, or account compromises should be addressed with the highest priority.
Implement Mitigation Measures
Once vulnerabilities are identified, implement appropriate mitigation measures, such as:
- Introducing CSRF tokens and validating them on the server-side for each request.
- Implementing referrer header validation or using the Origin header for modern browsers.
- Setting the
SameSiteattribute on session cookies to prevent them from being sent in cross-site requests. - Restricting sensitive operations to safe HTTP methods like
GETorHEAD. - Implementing Content Security Policy (CSP) to restrict resource loading from untrusted sources.
Regression Testing
After implementing mitigation measures, conduct thorough regression testing to ensure that the CSRF vulnerabilities have been properly addressed and that no new vulnerabilities have been introduced.
Continuous Monitoring
- Establish a process for continuous monitoring and periodic retesting of the application to identify any new CSRF vulnerabilities that may arise due to changes or updates.
- Stay up-to-date with the latest security advisories, vulnerabilities, and best practices related to CSRF prevention.
Developer Training
- Provide training and resources to developers on CSRF vulnerabilities, their impact, and the best practices for preventing them during the application development lifecycle.
- Encourage the adoption of secure coding practices and security testing as part of the development process.
How to Prevent Cross-Site Request Forgery Attacks
For Users:
As a user of web applications, it’s essential to be aware of CSRF attacks and take necessary precautions to protect yourself from unauthorized actions. Here are some steps you can take:
- Watch out for sketchy links: If you get a link from someone you don’t know or trust, be very careful about clicking it. Those links could be trying to pull a fast one and make you do things on websites where you’re logged in.
- Log out when you’re done: When you’re finished using a website, especially one with your bank account or other sensitive info, log out! That way, even if someone tries a CSRF attack, they won’t be able to hijack your active session.
- Use unique, strong passwords: Don’t use the same password for everything. If one account gets hacked, the bad guys can’t just waltz into all your other accounts too. Make those passwords long and strong!
- Keep your software updated: Make sure your web browser and other programs are always up-to-date with the latest security patches. Outdated software is like leaving your front door wide open for attackers.
- Be extra careful on public computers: Never log into sensitive accounts on public computers or shared devices. You never know what kind of nasty stuff could be lurking there, ready to steal your info.
- Report shady activity: If you notice anything weird happening with your accounts, like unauthorized actions or suspicious stuff, report it right away to the website owners or service providers.
For Developers:
As a web developer, it’s crucial to implement robust measures to prevent CSRF vulnerabilities in your applications. Here are some best practices to follow:
- Use CSRF tokens: Implement a random, unpredictable CSRF token (or synchronizer token) that must be included in each request that triggers a state-changing operation. Generate and validate these tokens on the server-side for each request.
- Validate referrer headers: Check the Referer HTTP header (or the Origin header for modern browsers) to ensure that requests originate from your legitimate web application domain. Reject requests with invalid or missing referrer headers.
- Implement SameSite cookies: Set the SameSite attribute on session cookies to prevent them from being sent along with cross-site requests. The SameSite=Strict setting is recommended for enhanced security.
- Check for safe HTTP methods: Web applications should only process sensitive actions when the request is made using safe HTTP methods like GET or HEAD. Reject requests that use methods like POST, PUT, or DELETE for sensitive operations.
- Use Content Security Policy (CSP): Implement a Content Security Policy (CSP) that restricts the sources from which resources (scripts, styles, etc.) can be loaded on your web application. This can help prevent the injection of malicious scripts that could enable CSRF attacks.
- Require user interaction: For highly sensitive operations, require user interaction beyond just clicking a link, such as entering a one-time code or performing a multi-step process.
- Implement logging and monitoring: Set up comprehensive logging and monitoring mechanisms to detect and respond to potential CSRF attacks. Look for patterns of suspicious activity, such as multiple requests from untrusted sources or requests with missing or invalid CSRF tokens.
- Educate users: Provide guidance and educational resources to users about the risks of CSRF attacks and the importance of not clicking on untrusted links or visiting suspicious websites while logged into your web application.
CloudDefense.AI: Your Ally in the Fight Against CSRF Attacks
We, at CloudDefense.AI, understand the critical need to fortify your defenses against these attacks. Here’s how our comprehensive Cloud Security Platform empowers you to combat CSRF vulnerabilities:
Automated Scanning
CloudDefense.AI integrates seamlessly into your development workflow and performs automated scans of your application’s codebase. This includes identifying potential CSRF vulnerabilities alongside other security risks. By automating this process, CloudDefense.AI saves developers time and effort, allowing them to focus on core functionalities.
Early Detection
CloudDefense.AI prioritizes early vulnerability detection. By identifying potential CSRF weaknesses early in the development lifecycle, they can be addressed before they become a security nightmare in production. This proactive approach helps prevent costly fixes down the road and protects your application from potential exploits.
Focus on Developer Expertise
We understand that developers are not always security experts. CloudDefense.AI is designed to be intuitive and user-friendly, empowering developers to identify and remediate CSRF vulnerabilities with ease. Our platform provides clear remediation steps and guidance, simplifying the process of securing your applications.
Comprehensive Security
CloudDefense.AI goes beyond just CSRF vulnerabilities. Our platform offers a holistic view of potential security threats, including vulnerability management, threat detection, and API scanning. This comprehensive approach helps developers build secure applications from the ground up.
Integration with DevSecOps
CloudDefense.AI integrates smoothly with DevSecOps practices, making security a seamless part of the development process. This ensures that security considerations are woven into the fabric of application development, leading to more secure and reliable software.
By leveraging CloudDefense.AI’s capabilities, developers can significantly reduce the risk of CSRF attacks and build more secure applications. Our focus on automation, early detection, and developer-friendliness makes them a valuable partner in the ongoing battle against web-based threats.







