What is Account Takeover (ATO)?
Account Takeover (ATO) is a sneaky cyber attack where bad actors gain unauthorized access to your online accounts using stolen login credentials. It’s like someone finding the keys to your digital infrastructure and walking right in. These cybercriminals often get their hands on usernames and passwords through various shady means, including data breaches, phishing scams, and social engineering tricks.
Once they have these credentials, they don’t manually try them one by one. Nope, they’re smarter than that. They use bots – automated programs – to test thousands of username and password combos across various platforms like finance, eCommerce, social media, travel, and retail. The goal is to find valid combinations that allow unauthorized access.
So, after the access is secured, the attackers profit by selling the verified credentials or exploiting the accounts directly – such as making fraudulent purchases, transferring funds, or stealing loyalty points.
Why are ATO Attacks Scary?
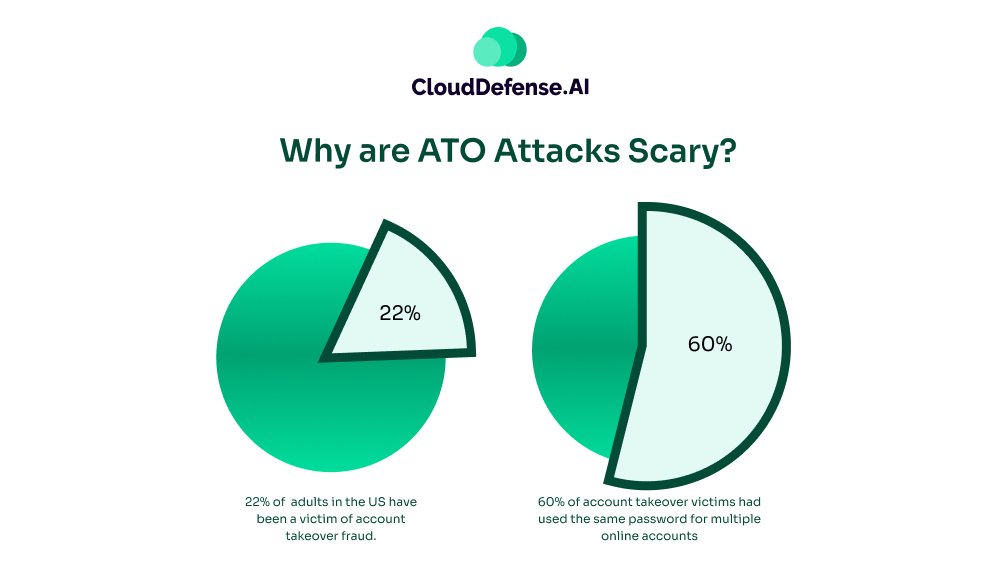
Now, you might be thinking, “I use strong passwords. I’m safe, right?” Well, not quite. Here’s the kicker: most of us are guilty of password recycling. We use the same login details across multiple sites because, let’s face it, remembering a unique password for every account is a pain.
This habit is a goldmine for attackers. If they crack one account, they might gain access to several others. And once they’re in, they can do all sorts of nasty stuff – use your loyalty points, make unauthorized purchases, or even steal your identity.
The scariest part? These attacks aren’t just targeting individuals. Businesses are in the crosshairs, too, with cybercriminals breaking into verification systems of websites, mobile apps, and APIs.
Even tech giants aren’t immune. Take Snowflake, for example. This cloud computing powerhouse recently experienced a breach where attackers gained unauthorized access to some employee accounts.
While Snowflake acted quickly to contain the incident, it serves as a stark reminder that no one is completely safe from ATO attempts. The company had to implement additional security measures and conduct a thorough investigation, showing just how disruptive these attacks can be to business operations.
Frequent Targets Of Account Takeover (ATO) Attacks
While it’s true that nearly anyone and any organization can fall victim to an account takeover attack, some types of accounts are more likely to end up in a hacker’s crosshairs. Let’s take a closer look at the most common targets:
Banking Accounts: This is often the holy grail for attackers. By accessing your bank or credit card accounts, they can directly steal money or go on a shopping spree at your expense. But it doesn’t stop there – they might even mess with your investment portfolios, potentially causing long-term financial damage.
Travel Accounts: Ever collected frequent flyer miles? Hackers love these. They might try to steal your hard-earned miles for their own vacations or sell them on the black market.
Retail Accounts: Online shopping accounts are prime targets. Hackers can make purchases pretending to be you, either shipping items to themselves or to accomplices who can sell the goods for profit.
Government Benefit Accounts: Think Medicare or other social services. If a fraudster gets control of these accounts, they can redirect your benefits to themselves or sell the account information to other hackers online.
Retail Accounts: Those points you’ve been saving up for a big purchase? Hackers see them as free money. They might use your loyalty points for their own benefit or sell them to other fraudsters online.
Cellphone Contracts: Some hackers take over cell phone accounts to make calls, send texts, or use data without paying a dime. It’s like they’re piggy-backing on your plan, leaving you with the bill.
How Does Account Takeover Happen? A Detailed Look
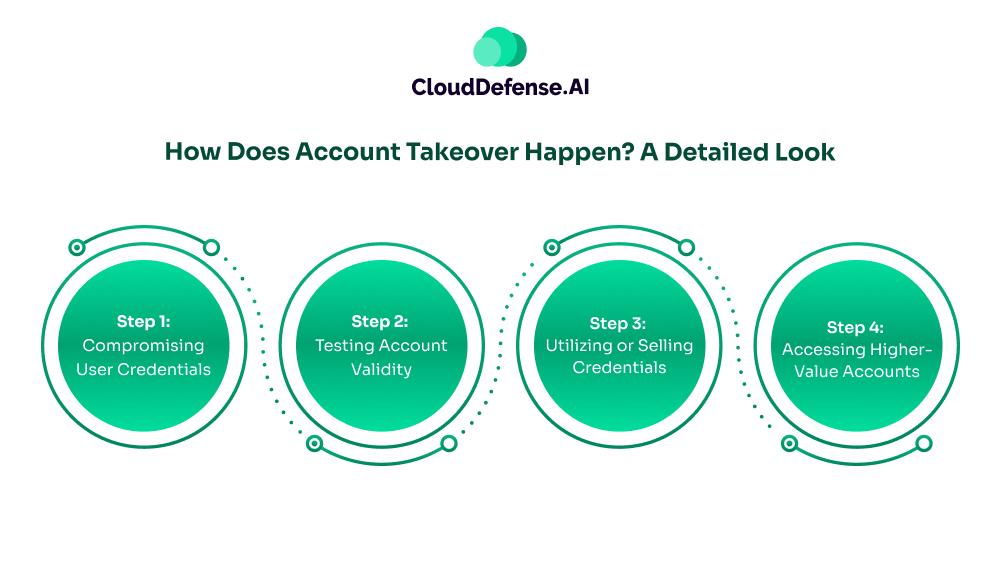
Account Takeover (ATO) is a sophisticated cyber attack that unfolds in several stages. Let’s dive deep into each step:
Step 1: Compromising User Credentials
This crucial first step can happen in various ways:
- Password Reuse: Many people use the same password across multiple accounts. Hackers exploit this by using credentials leaked from one site to access others.
- Credential Stuffing: Attackers use large databases of stolen usernames and passwords, often purchased on the dark web, to attempt logins on various platforms.
- Phishing Attacks: Cybercriminals create fake websites or send deceptive emails to trick users into revealing their login information.
- Keylogging: Malware installed on a user’s device can record keystrokes, capturing passwords as they’re typed.
- Brute Force Attacks: Automated tools try numerous password combinations until they find the correct one.
Step 2: Testing Account Validity
Once attackers have a set of credentials, they need to verify which ones actually work:
- Manual Testing: For smaller-scale attacks, hackers might manually input credentials into login pages.
- Automated Bots: More commonly, attackers use sophisticated bots that can test thousands of credentials rapidly across multiple sites.
- Proxy Servers: To avoid detection, these bots often use a network of proxy servers, making it appear that login attempts are coming from different locations.
- API Exploitation: Some attackers target APIs instead of login pages, as these might have fewer security measures in place.
Step 3: Utilizing or Selling Credentials
After confirming which credentials are valid, attackers have two main options:
- Direct Exploitation:
- Financial Accounts: Drain bank accounts or make unauthorized purchases.
- Email Accounts: Access personal information, reset other account passwords.
- Social Media: Spread malware, conduct social engineering attacks, or damage reputations.
- Selling on the Black Market:
- Credentials are often sold in bulk on dark web marketplaces.
- Prices vary based on the account type, with financial and corporate accounts fetching higher prices.
- Some hackers specialize in obtaining credentials, while others focus on exploiting them.
Step 4: Accessing Higher-Value Accounts
This step involves leveraging initial access to compromise more valuable targets:
- Email Account Takeover: Often a gateway to other accounts, as most services use email for password resets.
- Two-Factor Authentication (2FA) Bypass: Attackers may use social engineering to trick victims into providing 2FA codes.
- Password Reset Exploitation: Using access to one account to reset passwords for others, gradually increasing their reach.
- Corporate Account Escalation: In business settings, compromising one employee’s account might lead to accessing sensitive company data or systems.
How to Identify Warning Signs of Account Takeover Attacks
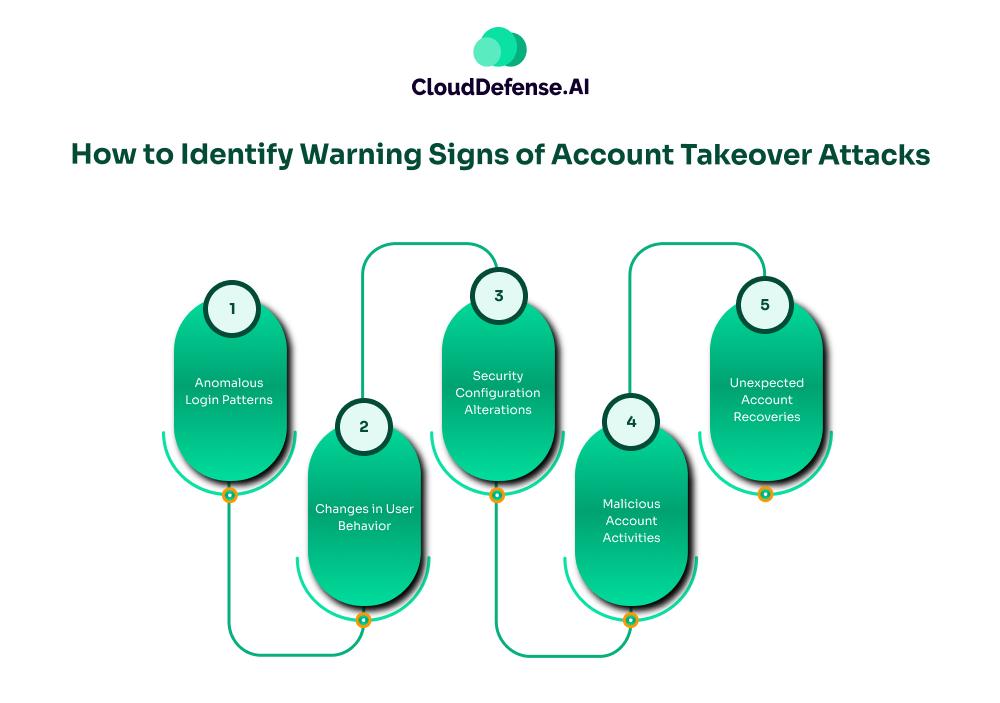
Account takeover (ATO) attacks can be challenging to detect in their early stages, often due to the initial compromise occurring outside an organization’s visibility. However, several key indicators can signal a potential ATO attack in progress. Organizations should be vigilant for the following warning signs:
1. Anomalous Login Patterns
One of the primary indicators of an ATO attack is unusual login activity:
- Increased Failed Login Attempts: A sudden spike in failed login attempts may indicate a brute force attack or credential stuffing effort. Organizations should monitor authentication logs for such anomalies.
- Unusual Login Locations or Times: Access attempts from unexpected geographic locations or at atypical times of day can signal account compromise. This is particularly relevant for organizations with employees in fixed locations or standard working hours.
2. Changes in User Behavior
Established user behavior patterns can serve as a baseline for detecting potential account compromise:
- Deviation from Normal Usage Patterns: Sudden changes in account usage, such as accessing previously unutilized resources or interacting with systems in an uncharacteristic manner, may indicate an ATO attack.
- Unexpected Data Access or Exfiltration: Large-scale data access or transfer, particularly involving sensitive information not typically associated with the user’s role, should be treated as suspicious.
3. Security Configuration Alterations
Attackers often modify account settings to maintain access and evade detection:
- Disabled Security Features: The deactivation of security measures, such as two-factor authentication or login alerts, can be a sign of malicious activity.
- Unusual Account Configurations: The creation of new email forwarding rules, changes to recovery information, or modifications to access permissions may indicate an attacker attempting to entrench their position.
4. Malicious Account Activities
Compromised accounts are frequently used as platforms for further attacks:
- Phishing Attempts: If an account begins sending suspicious emails, especially those containing links or requesting sensitive information, it may have been hijacked for phishing purposes.
- Unauthorized Access Attempts: A compromised account might be used to probe for access to other systems or accounts within the organization.
5. Unexpected Account Recoveries
An increase in account recovery attempts or password reset requests, especially from unfamiliar sources, could indicate an attacker attempting to gain or maintain access to multiple accounts.
When u remain attentive to these warning signs and implement strong monitoring systems, organizations can enhance their ability to detect and respond to account takeover attacks promptly. Early detection is crucial in minimizing the potential damage and preventing further compromise of organizational resources.
How to Secure Against Account Takeover (ATO)
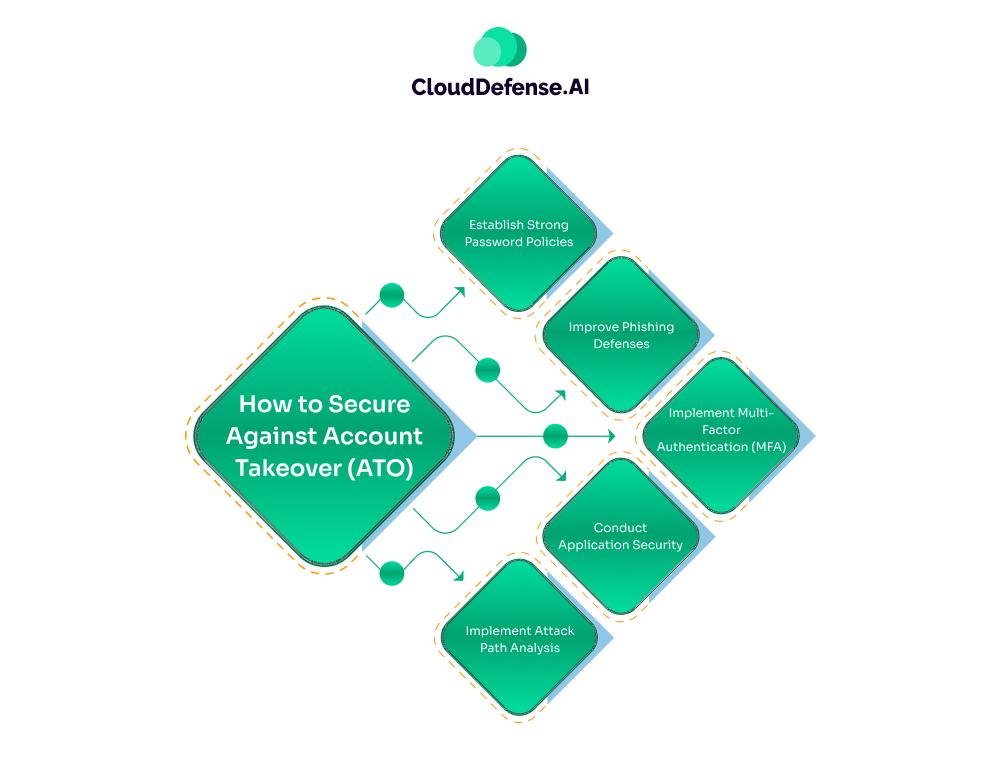
To effectively prevent account takeover attacks, organizations should adopt a multi-faceted security strategy that addresses a variety of vulnerabilities. Below are several strategies, complete with examples, to bolster defenses against ATO:
1. Establish Strong Password Policies
Weak or reused passwords are prime targets for malicious actors. By instituting strong password policies such as requiring a combination of characters and regular updates – organizations can mitigate these risks.
For instance, Google alerts users when their passwords are found in known data breaches, prompting them to make necessary changes. Also, utilizing password managers can assist employees in generating and securely storing complex, unique passwords, relieving them of the burden of memory.
2. Improve Phishing Defenses
Phishing remains one of the most prevalent techniques for obtaining credentials. Organizations can implement email filtering solutions that detect and block phishing attempts. For example, a company might establish rules to prevent emails containing suspicious links or forged sender addresses from reaching inboxes. Furthermore, providing ongoing training for employees on recognizing phishing attempts such as fake “password reset” notifications can significantly strengthen overall security.
3. Implement Multi-Factor Authentication (MFA)
MFA greatly increases security by requiring additional verification steps beyond a password. For instance, a bank may require a one-time password (OTP) generated by an authenticator app alongside standard login credentials. Even if a password is compromised, MFA ensures that the attacker is unable to gain access. Moreover, physical security keys like YubiKeys serve as another effective defense against credential theft related to phishing.
4. Conduct Application Security
Application vulnerabilities, such as exposed API keys and authentication tokens, can provide attackers with direct access to accounts. Security testing should be done with enough regularity to find these issues and remediate them quickly. Use SAST tools that scan the code and DAST tools that scan application behavior to look for weaknesses.
SAST tools look for flaws in source code before the application execution, whereas DAST tools test applications at runtime to find vulnerabilities that occur during runtime. Combining these approaches will offer assurance that any given appraisal of your application’s security will be all-inclusive, and minimize unauthorized access.
5. Implement Attack Path Analysis
Understanding the potential attack paths within your network can significantly bolster security against account takeover attempts. An attack path analysis allows discovery of how an attacker can laterally move across your system after obtaining initial access, pointing out weak links and security gaps that may be used.
In this regard, it gives organizations time for proactive remediation through mapping pathways continuously, enhancing defenses, and consequently reducing the impact, a successful account takeover. It reduces the attack surface area by the proactive approach of active security management and secures critical accounts from being exploited.
How to Assess the Risk of Account Takeover
Assessing the risk of account takeover involves evaluating several factors to understand potential vulnerabilities and their impact. Here are some key questions to guide your risk assessment process:
1. What types of accounts are most critical to your organization?
Identify which accounts hold the most sensitive information or have the highest level of access. For instance, financial accounts or administrative accounts might be more critical and require heightened protection compared to standard user accounts.
2. How frequently are passwords updated, and are they unique across different platforms?
Evaluate your organization’s password policies. Are passwords changed regularly? Are unique passwords used for different accounts? Understanding this helps gauge the effectiveness of your password management practices.
3. What is the current state of your multi-factor authentication (MFA) implementation?
Assess whether MFA is enforced for all accounts, especially for high-risk or administrative access. Are there any gaps in MFA coverage that could leave accounts vulnerable?
4. How are your employees trained to recognize and respond to phishing attacks?
Review the effectiveness of your phishing awareness training programs. Are employees regularly educated about identifying phishing attempts and other social engineering tactics?
5. Are there any exposed API keys or authentication tokens in your applications?
Check if your application’s code or configuration files contain exposed credentials that could be exploited. Regular security testing and code reviews can help uncover these vulnerabilities.
6. What monitoring and alerting mechanisms are in place for detecting suspicious login activities?
Evaluate your systems for detecting and responding to unusual login patterns or failed login attempts. Are there effective monitoring tools and alerting processes in place?
7. How well do you understand the potential attack paths within your network?
Perform attack path analysis to identify how an attacker could exploit network weaknesses to gain access to critical accounts. Are there any overlooked vulnerabilities that need addressing?
8. What incident response plans are in place for handling account takeovers?
Review your incident response protocols for dealing with account takeovers. Are there clear procedures for mitigating damage and recovering compromised accounts?
Addressing these questions can help you better assess the risks associated with account takeovers and implement more effective security measures to protect your organization from potential breaches.
Wrapping Up
To sum up, Account Takeover (ATO) attacks are a lurking danger, posing serious threats to both individuals and businesses. From drained bank accounts to unauthorized access across corporate systems, the consequences can be devastating. No one is safe, these cybercriminals use sophisticated techniques like credential stuffing, phishing, and automated bots, exposing vulnerabilities in even the most secure accounts.
So, don’t wait for an attack to be your wakeup call. Take steps to improve your defenses now with multi-factor authentication, secure password practices, and vigilant monitoring. The price of inaction is steep, and without proactive measures, you risk losing control over your most sensitive data.







