Definition – What is a Living Off the Land (LOTL) Attack?
Let’s consider a simple scenario to make it easy for you to understand. Imagine a thief breaking into your house, but instead of using crowbars and lockpicks to break in, they cleverly exploit everyday tools – a screwdriver from your toolbox, a rope from your garage.
That’s what a LOTL attack looks like. However, in the digital world, attackers leverage legitimate programs and functionalities already present on a system to carry out malicious activities.
Here’s the breakdown:
- Traditional Attacks vs. LOTL: Regular cyberattacks often involve malicious software (malware) that leaves a digital footprint. Security systems can identify these red flags. LOTL attacks, however, are far more deceptive.
- Exploiting What’s There: Attackers leverage legitimate tools and features already present on a victim’s system. This could be anything from PowerShell (a scripting tool on Windows) to system utilities for managing files and processes.
But Why LOTL?
There are two main reasons:
- Stealth: By using trusted tools, LOTL attacks fly under the radar of traditional security measures that focus on detecting malware signatures.
- Leave no Trace: LOTL attacks are often “fileless,” meaning they don’t leave malware files behind, making them even harder to track.
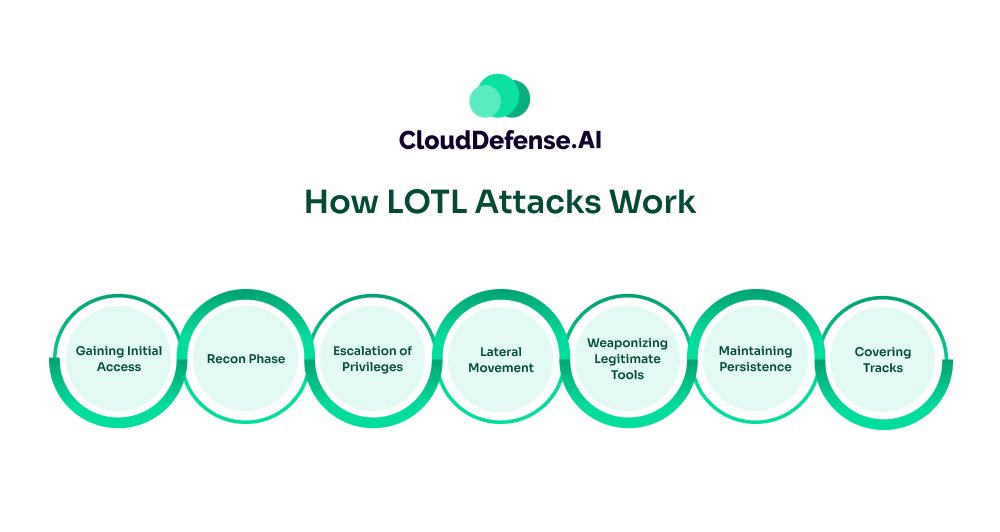
How LOTL Attacks Work
LOTL attacks are like a well-orchestrated heist. You know how in every heist movie, the bad guys have to do a ton of recon work before they can pull off the big job? Well, LOTL attackers follow a similar playbook, but their methods are way more insidious.
Let’s break down the typical stages of a LOTL attack to understand how they infiltrate systems:
Gaining Initial Access
The first step for any attack is establishing a foothold. Phishing emails, compromised websites, or even infected USB drives can be used to gain initial access to a target system. Attackers often exploit vulnerabilities in operating systems or applications to achieve this.
Recon Phase
Once inside, attackers use legitimate tools to gather information about the system. It usually starts with them scoping out your digital turf, trying to map out what kind of legit tools and software are already installed on your systems. This recon phase is crucial because it lets them figure out which everyday utilities they can abuse for their nefarious purposes.
Escalation of Privileges
Leveraging the recon information, attackers identify weaknesses in the system’s configuration or the functionalities of trusted tools. This might involve using utilities like ipconfig (Windows) or ifconfig (Linux) to map the network layout or tools like net user (Windows) or id (Linux) to identify user accounts and their privileges. They might also exploit vulnerabilities in these systems to elevate their privileges and gain more control.
Lateral Movement
With a foothold established, attackers can use tools like PowerShell remoting or SSH (Secure Shell) to move laterally across the network. This allows them to compromise other devices and expand their reach within the system.
Weaponizing Legitimate Tools
Now comes the core of the LOTL attack. Hackers leverage pre-installed tools for malicious purposes. Here are some examples:
- PowerShell: This powerful scripting tool can be used to download malicious payloads, steal data, or even launch denial-of-service attacks.
- Command Prompt: Simple commands like copy or move can be used to exfiltrate sensitive data.
- System Utilities: Tools like Regsvr32.exe (Windows) can be misused to load malicious code disguised as legitimate libraries.
Maintaining Persistence
To ensure continued access, attackers might use tools to create hidden user accounts, schedule malicious scripts to run automatically, or modify system configurations.
Covering Tracks
Throughout the attack, LOTL attackers strive to remain undetected. They might use tools to clear logs, disable security software, or manipulate timestamps to mask their activity.
The key takeaway is that LOTL attacks are deceptive. They manipulate legitimate functionalities in unexpected ways, making them challenging to detect and prevent. By understanding these stages, you can be better prepared to defend against these stealthy threats.
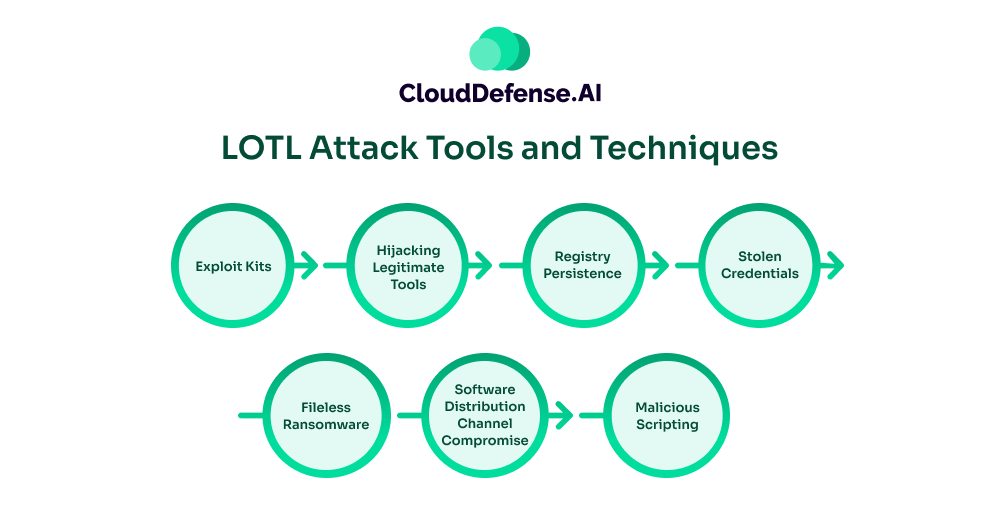
LOTL Attack Tools and Techniques
Here’s a breakdown of common LOTL tools and techniques:
Exploit Kits
One way LOTL attackers gain initial access is through exploit kits – collections of exploits that target vulnerabilities in operating systems or installed applications. Exploits allow injecting malicious code directly into memory without writing anything to disk, making them well-suited for fileless LOTL attacks.
Exploit kits often include a management console for the attacker and may even scan for vulnerabilities to craft customized exploits on-the-fly. Victims are typically lured through phishing or social engineering.
Hijacking Legitimate Tools
At the core of LOTL attacks is hijacking trusted, native tools for malicious purposes like escalating privileges, lateral movement, data theft, and deploying malware. Common hijacked tools include:
- FTP clients or functions like PsExec for transferring files
- Password extraction tools like Mimikatz
- PowerShell scripting framework for system administration
- Windows Management Instrumentation (WMI) interface
Registry Persistence
Instead of downloading a separate malware file, some LOTL malware like Poweliks, Kovter, and GootKit inject malicious code directly into the Windows registry. This code can self-launch at system startup while remaining undetected by antivirus focused on scanning files.
Stolen Credentials
Attackers may kick off LOTL attacks by compromising legitimate credentials to access the target system. From there, they use native tools like WMI and PowerShell for malicious activities and establish persistence by hiding code in the registry, kernel or creating backdoor accounts.
Fileless Ransomware
Ransomware groups are adopting fileless techniques like embedding malicious macros in documents or exploits that inject code into memory. The ransomware then hijacks tools like PowerShell to encrypt files without ever writing itself to disk.
Software Distribution Channel Compromise
You know those routine software updates you diligently install to keep everything running smoothly? LOTL attackers can potentially hijack those trusted distribution channels and sneak in malicious code disguised as a legitimate update or installer.
Malicious Scripting
LOTL attackers may employ scripts, whether batch scripts or PowerShell scripts, to automate their attacks and carry out various malicious activities on the targeted systems.
The real danger of LOTL attacks lies in how they blend in with normal system activity. By the time you realize what’s happening, they’ve already made themselves at your system – and not in a good way.
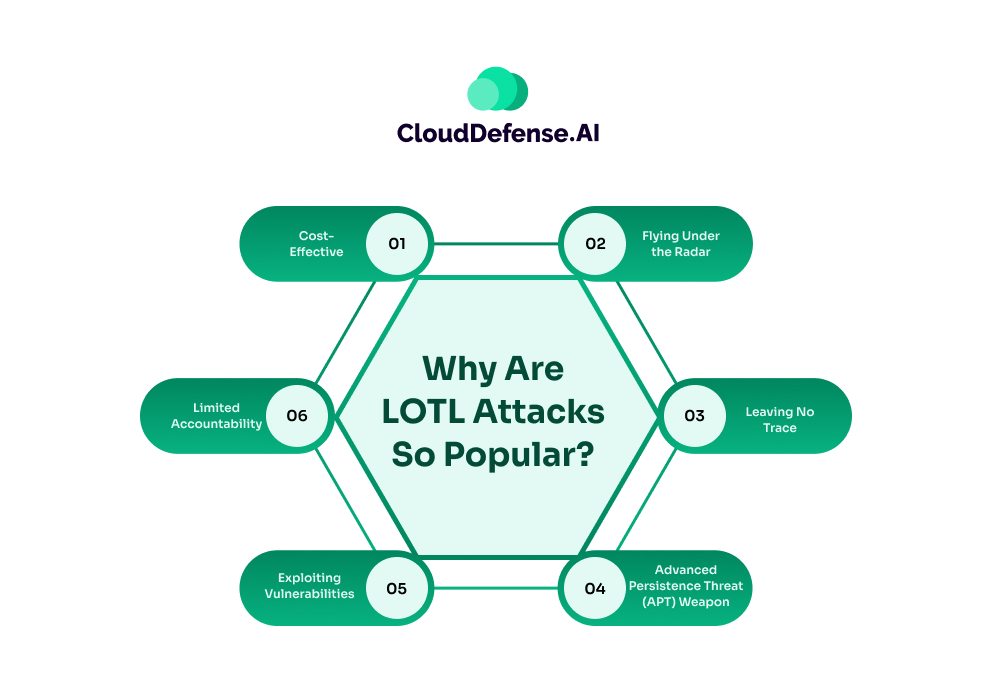
Why Are LOTL Attacks So Popular?
Living Off the Land (LOTL) attacks have become a favorite weapon for cybercriminals due to several key advantages they offer:
Flying Under the Radar
One of the biggest reasons LOTL attacks are all the rage these days? Because they can slip right past traditional security defenses. Most antivirus and endpoint protection tools are focused on catching known malware signatures or blocking sketchy executables from running. But LOTL attackers? They’re using the perfectly legit tools already installed and approved on your systems.
Leaving No Trace
Lots of LOTL attacks are “fileless,” meaning they don’t leave any malicious executable files lying around on your hard drive. Instead, they inject their nasty code straight into memory or hijack built-in tools to do their dirty work. It’s like they were never even there! This minimal forensic footprint makes it crazy hard for investigators to uncover evidence of the attack during the clean-up process.
Advanced Persistence Threat (APT) Weapon
LOTL attacks are a favorite tactic of APTs, highly skilled attackers targeting specific organizations. By using legitimate tools, APTs can maintain persistence within a system for extended periods, gathering intelligence and achieving their objectives.
Exploiting Vulnerabilities
Some LOTL attacks don’t even need stolen credentials to get in. They take advantage of unpatched vulnerabilities in trusted software and services to slip through the cracks. By chaining together these exploits against the apps and tools you already use and trust, they can compromise your systems without triggering any alarms that would go off for traditional malware.
Cost-Effective
From the attacker’s perspective, LOTL techniques are like a bargain deal on chaos. Instead of investing tons of time and resources into developing custom malware (which can be crazy expensive), they can just repurpose the tools already sitting on your systems to carry out their attacks. It’s efficient, cost-effective, and sneaky as hell.
Limited Accountability
Here’s the real kicker: because LOTL attacks involve abusing legitimate system tools, it’s way harder to pin the blame on any specific threat actor or hacker group. This perceived lack of accountability just further incentivizes cybercriminals and nation-state baddies to double down on these sneaky tactics.
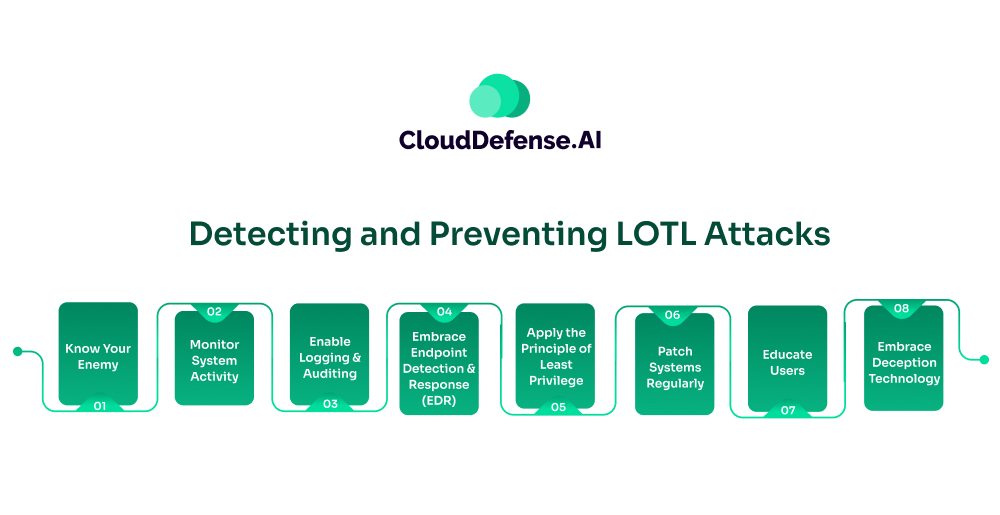
Detecting and Preventing LOTL Attacks
Living Off the Land (LOTL) attacks can feel like a fight against a ghost. They use legitimate tools, making them hard to spot. But fear not! Here are some steps you can take to become a cyber-security vigilante:
Know Your Enemy
Familiarize yourself with common LOLBins (Living Off the Land Binaries) on Windows systems and their legitimate uses. Learn about common scripting languages and how they can be misused. Understanding these tools will help you recognize suspicious activity.
Monitor System Activity
Keep a eye on what’s happening across your systems. Deploy monitoring tools to track everything – process executions, network traffic, file access – you name it. If an app is running at a weird hour or a process looks sketchy, that’s your cue to investigate further.
Enable Logging and Auditing
This one’s crucial – comprehensive logging gives you the receipts to analyze any sketchy behaviors. Review those logs regularly and look for anomalies sticking out like a sore thumb.
Embrace Endpoint Detection and Response (EDR)
EDR solutions go beyond traditional antivirus by providing real-time monitoring and analysis of system behavior. They can detect malicious use of legitimate tools and provide faster response times to potential threats.
Apply the Principle of Least Privilege
The principle of least privilege recommends granting users only the minimum permissions necessary to perform their tasks. This way, you can limit the potential damage caused by an attacker who gains access to a compromised account.
Patch Systems Regularly
Leaving security holes unpatched is like giving LOTL attackers an open invitation. Stay on top of patching everything – apps, operating systems, you name it. Seal up those cracks!
Educate Users
Empower your users to be the first line of defense. Train your employees to spot phishy emails, dodge shady links/attachments, and report any weird system behaviors ASAP.
Embrace Deception Technology
Consider implementing deception technology that creates honeypots – fake systems designed to lure and trap attackers. By monitoring honeypot activity, you can gain valuable insights into attacker tactics and techniques.
Conclusion
Living-off-the Land attacks are a scary new threat we can’t ignore. The bad guys are turning our own trusted tools against us – how messed up is that? Getting your systems back under control after one of these attacks is an absolute nightmare.
You’ve got to do complex digital detective work, kick out the intruders, and then try to make sure they didn’t leave any backdoors open on their way out. You better stay on high alert and boost your defenses with cutting-edge security tools like CloudDefense.AI. Every second counts – strengthen your defenses now before it’s too late!







