As the use of cloud-native applications is increasing in the industry, so does the number of digital risks and attacks. Since most cloud applications integrate with numerous third-party services and libraries, they provide attackers the leeway to exploit them.
Even though developers are coming up with new mitigation strategies to safeguard the application, keeping up with attackers to prevent them from exploring the vulnerabilities is a daunting task. Thankfully the release of the OWASP top 10 vulnerabilities for 2024 has been a savior because it provides up-to-date information regarding all the significant vulnerabilities of the current days.
This resource is highly valuable for developers because it helps them to develop the application and test it by keeping all these vulnerabilities in mind. It acts as a reference to develop a secure application and safeguard all the data from vulnerabilities offering maximum risk.
So, first, let’s start by knowing about;
What is OWASP?
Open Web Application Security Project, or OWASP, is a non-profit global foundation that performs extensive research to find dangerous security threats to help organizations improve web application security. Through their platform, they provide a lot of tools, open-source programs, techniques, research, and conferences to help developers improve cloud application security.
The main motive of OWASP is to make their research free and accessible to everyone. OWASP was founded on 9th September 2001 by Mark Curphey, a cybersecurity enthusiast who wanted to control the rise of cyberattacks. This non-profit foundation is backed by thousands of reputed web security individuals, and that is why it is considered an important source when it comes to cloud application and API security guidance.
OWASP Top 10 is a primary project conducted by this organization, and it basically acts as an awareness document that lists the top ten web application vulnerabilities that can cause significant breaches. The list offers not only a list of top potential threats but also ways to solve them. Every year, OWASP revises the lists accordingly and comes up with new top ten web application vulnerabilities that are most common and have the maximum impact.
The list is designed by the most trusted security vendors, teams, and consultants from various organizations, and they focus only on major security risks that hamper a web application. For the last many years, it has been considered as the primary guide for best security practices to secure web applications.
OWASP Top 10 Vulnerabilities
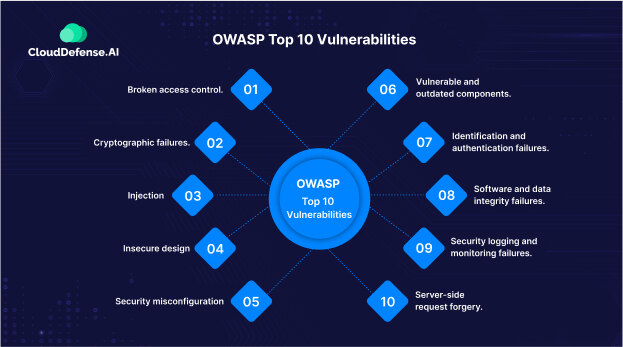
For the year 2024, OWASP has come up with a new list of the top 10 vulnerabilities where they have listed the most impactful security threats to cloud applications. The vulnerabilities have been ranked according to their impact and number of occurrences. So here are OWASP’s top 10 vulnerabilities that every developer and web security team should be aware of;
- Broken access control.
- Cryptographic failures.
- Injection.
- Insecure design.
- Security misconfiguration.
- Vulnerable and outdated components.
- Identification and authentication failures.
- Software and data integrity failures.
- Security logging and monitoring failures.
- Server-side request forgery.
Now, let’s take a look at all these OWASP top 10 vulnerabilities in detail;
1. Broken Access Control
Broken access control is the most common and dangerous security risk web applications face. Almost 94% of web applications have some form of broken access control, and this weakness has allowed many attackers to exploit it. Developers apply access control to web applications which limits users to access only those data and pages that are needed.
However, failure to deploy access control efficiently leads to unauthorized access, leading attackers to perform data modification and information disclosure. Around 34 CWEs related to broken access control have hampered web application security more than any other. A convenient way to mitigate this vulnerability is by building robust access control with role-based authentication and deploying a least-privileged approach.
2. Cryptographic Failure
It was previously known as Sensitive Data Exposure, and this vulnerability refers to a failure in cryptography that leads to sensitive data exposure. Lack of use of cryptography and various encryption for essential data leads to exposure and allows attackers to get hold of them.
Vital data like business secrets, card information, health records, and personal information that are moving or at rest require special protection, especially when they fall under CCPA, GDPR, or PCI-DSS. When these data are stored with poor key management, like outdated keys, or without the latest cryptographic algorithm, then it leads to a vulnerability that exposes the data. The best way to solve it is by encrypting all the data in transit and also the data at rest through encrypted algorithms and protocols.
3. Injection
Injection is the second most occurring vulnerability that affects many web applications, and it leads to service denial, data theft, data loss, and other forms of attacks. According to market research, 94% of web applications in the last year have been affected by some form of injection.
Through this vulnerability, the attackers could inject malicious data, queries, or commands into the interpreter, which compelled it to take undesignated actions like providing data access without authentication. SQL and XSS are the most common and dangerous injection attacks. Using intrusion detection systems, safe API, and server-side input validation helps developers tackle this vulnerability.
4. Insecure Design
It tells you about the vulnerability that often arises due to implementing ineffective control design, which ultimately leads to different vulnerabilities. Insecure design is a broad term that covers a lot of flaws and primarily refers to the security gaps in the design.
This vulnerability guides developers to build a secured application and also decide the level of security before starting the development because it will help prevent poor security control. Implementing robust security practices, utilizing secure design patterns, and integrating security rights in the SDLC stage is a better way to ensure a secure design. Threat modeling for various features is also essential to avoid this vulnerability.
5. Security Misconfiguration
According to research conducted by OWASP, 90% of native cloud applications are plagued by security misconfiguration, even though organizations are focusing more on highly configured software. Security misconfiguration occurs mainly due to inaccurately configuring the security controls, and it puts the whole system at risk.
Security misconfiguration also occurs when the developers go for default settings, enable unnecessary features, provide access to cloud storage, and misconfigure HTTP headers. This vulnerability can occur on any layer of the application stack or cloud infrastructure and cause exposure of vital data. You can mitigate this vulnerability by strengthening the app security, regularly updating the security configuration, and using preconfigured templates.
6. Vulnerable and Outdated Components
Many modern cloud applications utilize open-source components like frameworks and libraries for seamless operation. If any of the components used during development are outdated or have known vulnerabilities, it become vulnerable to attack, compromising the security of the whole system.
Even though this use of components with known vulnerability doesn’t pose a considerable threat like others, it serves as the number one cause for the primary reason of the actual breach. Thus it becomes imperative for developers to maintain a list of component versions being used and continuously scan all the core components for any vulnerability. Removing unused and outdated components also serves as an effective solution.
7. Identification and Authentication Failure
Identification and authentication failure is a widespread vulnerability in web applications, and it poses a severe threat to the resources as well as assets associated with the network. When the web application incorrectly executes any function of user authentication or session management, it allows malicious personnel to compromise keys, passwords, and session tokens.
It also allows attackers to exploit permission and assume the identity of other users either permanently or temporarily. However, this vulnerability can be easily avoided if you implement multi-factor authentication or utilize a firm password policy. Avoiding the use of default credentials is also an excellent way to mitigate this vulnerability.
8. Software and Data Integrity Failure
This vulnerability is a significant threat to modern web application security that OWASP wants every developer to be aware of. When the integrity of critical data, software updates, installed packers, and CI/CD pipelines are not verified, it can lead to software and data integrity failures.
This vulnerability mainly occurs in cloud applications utilizing plugins, modules, or libraries from untrusted sources or CDNs. Auto updates in many applications without integrity checks also lead to a vulnerability where attackers can deploy their own updates across the system. Checking the legitimacy of software and data along with sources through digital signatures can help in curbing the security issue. Your application should only use libraries and modules from trusted repositories.
9. Security Logging and Monitoring Features
This top 10 OWASP vulnerability tells you about the inability of cloud applications to identify and respond to security risks. According to reports from IT Governance, it takes around 200 days on average for attack detection, and this colossal time frame allows attackers to exploit the system.
When monitoring of log activities is not done correctly, dangerous activities are overlooked, and it ultimately leads to this vulnerability. Using automated audit and logging software enabling the system for instant detection will be helpful in solving this risk. Security controls should be implemented to prevent tampering.
10 Server-Side Request Forgery
The server-side request forgery, also known as SSRF, is another severe vulnerability that occurs when cloud applications access data from remote resources without validating the supplied URL.
The attacker has the ability to send a tweaked request to an unexpected destination, even if the application is protected by a firewall or VPN. The best way to mitigate this vulnerability is implementing user-input sanitization and validation and blocking malicious incoming traffic using strict policies.
How CloudDefense.AI Can Help You To Stay Protected From These OWASP 10 Vulnerabilities
Web applications are the main target of many malicious attackers in the digital world, and they sift through applications to look for vulnerabilities. Even though developers use many security practices and application security tools to safeguard their applications, it is not sufficient for them.
Despite several efforts, applications still contain exploitable vulnerabilities, and it is often due to developers being unaware of the latest vulnerabilities and security practices. Identifying and remediating vulnerabilities mentioned in OWASP’s top 10 is an effective way to ensure the protection of the web application.
However, it is easier said than done, and that is where CloudDefense.AI comes in with its robust cloud-native cybersecurity platform. With its powerful vulnerability management, this platform provides complete protection against all the OWASP top 10 vulnerabilities. CloudDefense.AI also helps you easily maintain compliance and reduce any risk across your cloud application.
It is industry-leading agentless vulnerability management that allows security teams to have complete visibility and prioritize vulnerabilities according to their impact. Many prefer CloudDefense.AI’s service because of its frictionless solution to help security teams implement OWASP standards at an early stage to help them perform continuous tracking, testing, and managing security activities.
FAQ
1. What is OWASP's Top 10?
OWASP Top 10 is a regularly updated list of the ten most critical security risks to web applications. It is published by the Open Web Application Security Project (OWASP), a non-profit organization focused on improving software security. The list helps developers, security professionals, and organizations identify and prioritize the most common and impactful web application vulnerabilities.
2. Why is OWASP Top 10 crucial?
OWASP Top 10 provides essential guidance to developers and security teams to understand and address the most prevalent security risks in web applications. By focusing on these vulnerabilities, organizations can enhance their application security posture and protect against common cyber threats and attacks.
3. How can developers and organizations use OWASP Top 10?
Developers can use OWASP Top 10 to understand the common vulnerabilities and design secure code to prevent these issues in their applications. Security teams can prioritize their efforts on addressing these vulnerabilities during the development, testing, and maintenance phases. Additionally, organizations can use the OWASP Top 10 to guide their security training programs and improve their overall application security posture.
4. Are applications with OWASP Top 10 vulnerabilities guaranteed to be insecure?
Having vulnerabilities from the OWASP Top 10 does not automatically mean an application is insecure. However, these vulnerabilities are commonly exploited by attackers, and addressing them significantly improves the application's security posture.
Conclusion
The top 10 OWASP vulnerabilities are a savior for many organizations and developers because they act as a reference for them to address vulnerabilities in their applications.
However, traditional application security tools won’t be sufficient to mitigate maximum vulnerabilities. But cloud security platforms like CloudDefense.AI make it easier for organizations like yours to eliminate all the compliances and ensure you are compliant with all the application security standards.

Anshu Bansal, a Silicon Valley entrepreneur and venture capitalist, currently co-founds CloudDefense.AI, a cybersecurity solution with a mission to secure your business by rapidly identifying and removing critical risks in Applications and Infrastructure as Code. With a background in Amazon, Microsoft, and VMWare, they contributed to various software and security roles.