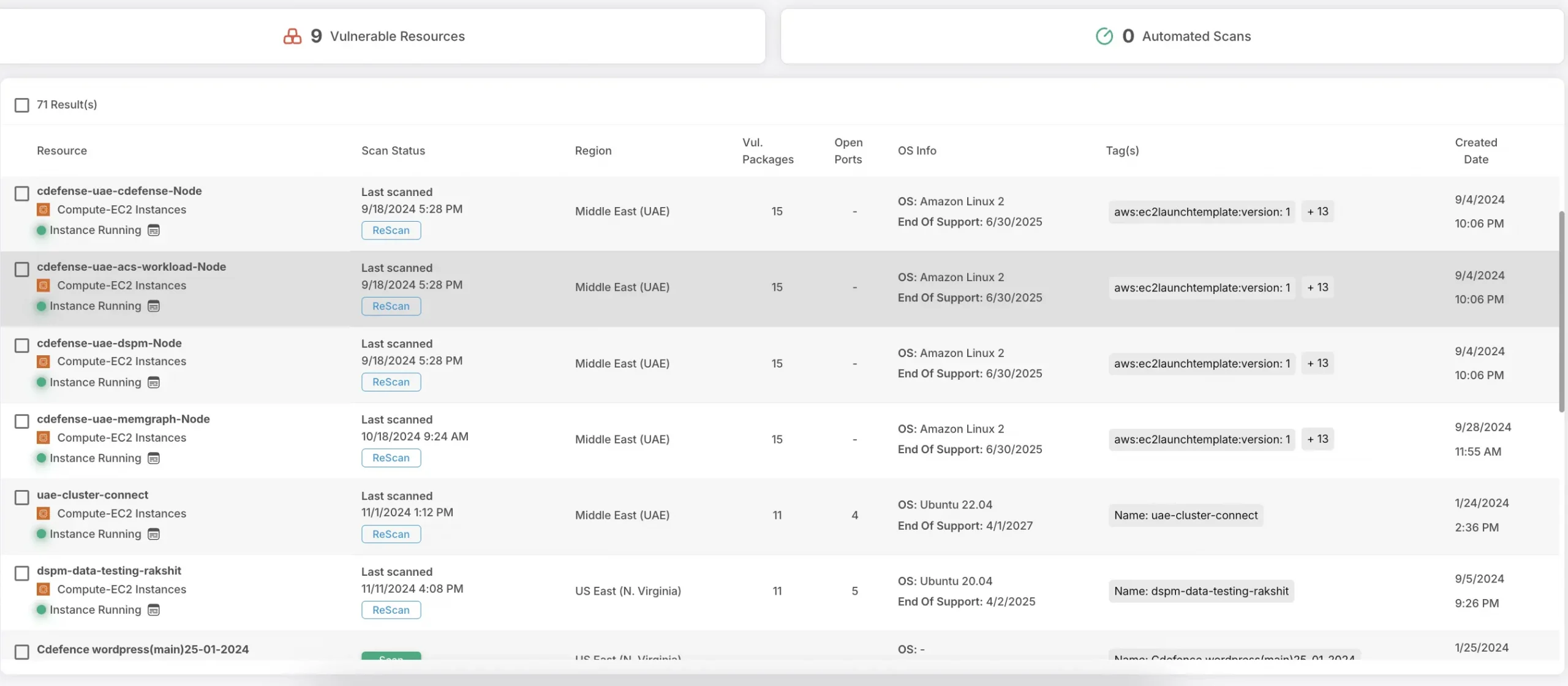
What is a CWPP (Cloud Workload Protection Platform)?
A Cloud Workload Protection Platform (CWPP) is a comprehensive security solution designed to protect cloud-based workloads across various environments, including public, private, and hybrid clouds.
By providing continuous threat monitoring, detection, and automated security measures, CWPP solutions protect workloads on servers, virtual machines, and containers.
They help minimize risks by addressing vulnerabilities in real-time, ensuring workloads remain secure in dynamic cloud environments.
What is Cloud Workload?
A cloud workload refers to a group of cloud-based resources working together to execute a specific business function or process. These resources can range from virtual machines and containers to databases, applications, and data storage.
Cloud workloads are adaptable and can be deployed across public, private, or hybrid cloud environments, making them highly flexible for various business needs. As organizations shift more operations to the cloud, managing and securing these workloads becomes critical.
Cloud workloads enable businesses to scale, optimize performance, and reduce operational costs. However, ensuring proper workload security is essential to protect data and maintain performance across diverse cloud platforms.
Let’s understand cloud workloads beter with this example. Consider an online banking platform that uses the cloud to manage its operations. The platform relies on multiple cloud workloads, including:
- Authentication services: Verifying user identities in a secure cloud environment.
- Transaction processing: Running real-time financial transactions using cloud-based servers and databases.
- Data storage: Storing sensitive customer information securely in a cloud database with encrypted backups.
These cloud workloads work together to ensure the platform remains operational 24/7, allowing users to safely access their accounts and perform financial transactions. The adaptability of these workloads helps the bank scale its resources as user demand fluctuates.
Cloud workloads enable businesses to scale, optimize performance, and reduce operational costs. However, ensuring proper workload security is essential to protect data and maintain performance across diverse cloud platforms.
How does CWPP work?
CWPP uses advanced technologies like machine learning, behavioral analysis, and automated defenses to keep your cloud workloads secure, no matter where they are deployed. It continuously analyzes subtle patterns and behaviors within your environment, building a baseline of what’s considered normal activity.
With this insight, it can detect any anomalies that could indicate a security threat. As soon as suspicious behavior is identified, CWPP instantly triggers automated defenses, including pre-defined response playbooks, to neutralize the threat before it escalates.
The first and most crucial step for a CWPP is achieving complete visibility across all workloads. This means not only understanding each workload’s structure but also how they interact and communicate within the broader cloud environment.
With this visibility in place, CWPP begins by scanning workloads for vulnerabilities and potential weak points. Once vulnerabilities are found, the platform suggests actionable remediation steps to address these risks.
But CWPP doesn’t stop once vulnerabilities are remediated. It continues to monitor your workloads during runtime, staying vigilant for new threats that may appear post-deployment. This constant oversight ensures that your workloads remain protected even as your cloud environment evolves.
From an operational standpoint, CWPP simplifies the work of cybersecurity teams by offering a centralized platform for managing cloud security. Instead of toggling between multiple tools to monitor different aspects of the infrastructure, security professionals get a unified view of their entire cloud environment. This approach enhances their focus on the most critical security risks, allowing them to respond efficiently to threats and maintain complete protection across the entire infrastructure.
Why Do You Need CWPP?
We are well aware of how everything is moving to the cloud today. This makes keeping your workloads secure across different environments even more important than ever. That’s where CWPP comes in.
You need CWPP because it helps protect your cloud workloads no matter where they are, whether it’s a public, private, or hybrid cloud. CWPP tools are built to handle the specific challenges of cloud security, from preventing malware attacks to fixing misconfigurations and vulnerabilities.
With the top CWPP solutions, you get a clear view of what’s happening in your workloads, so you can stop threats before they become a bigger problem. These tools also work well with your current setup, keeping your security consistent across all cloud environments. By using CWPP, you’re making sure your data, applications, and services are safe from new cloud threats.
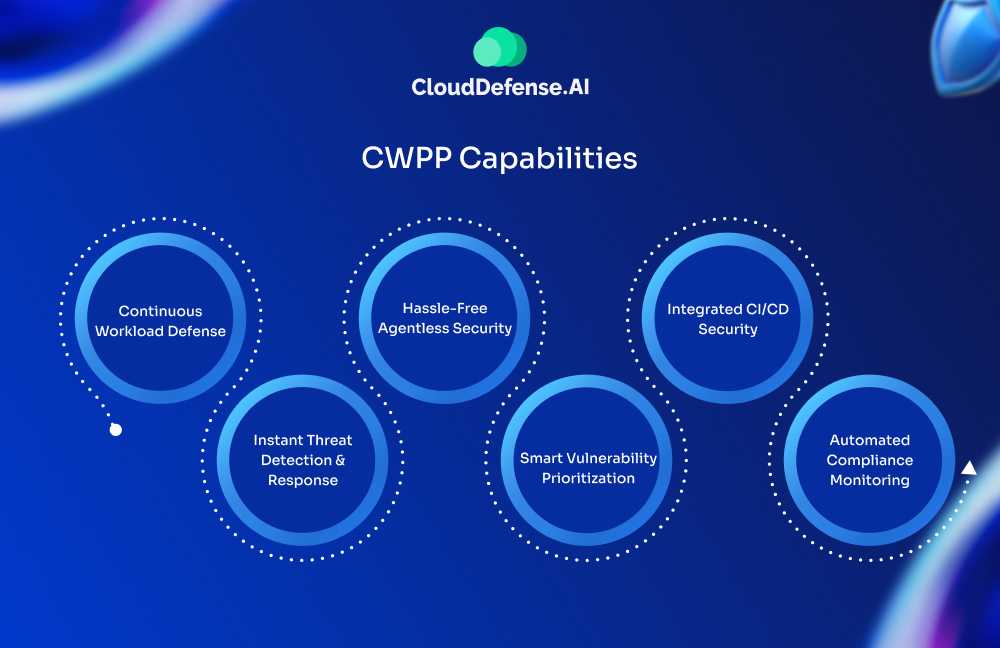
CWPP Capabilities
Nowadays, modern businesses utilizing cloud platforms are constantly under threat from attackers who try to exploit vulnerabilities in the workload and disrupt the system.
With the wide range of cybersecurity solutions available, it’s important to focus on key features when choosing a capable CWPP. You’ll need to assess options based on compatibility, scalability, and specific security needs.
Here are the critical components your CWPP should include:
1. Continuous Workload Defense
A strong CWPP offers real-time protection for your workloads, constantly monitoring and blocking any threats before they cause damage. With this feature, you can ensure smooth operations and minimal disruptions to your cloud environment.
2. Instant Threat Detection & Response
Your CWPP should quickly detect both known and unknown threats, such as malware, unauthorized code execution, or lateral movement in your cloud environment. This instant detection enables swift action to neutralize risks before they escalate.
3. Hassle-Free Agentless Security
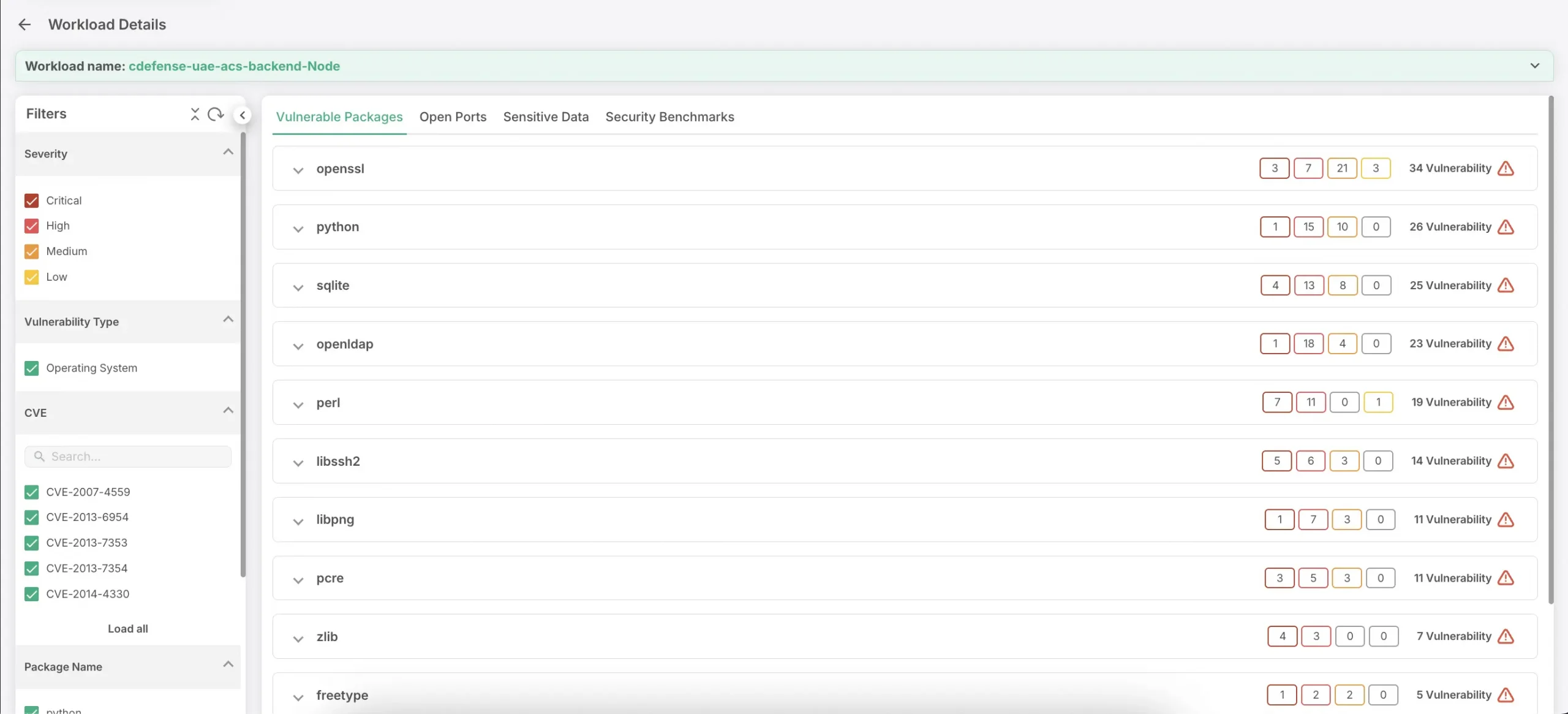
Agentless scanning allows you to monitor cloud resources without deploying agents on every workload. This simplifies security management, reduces resource use, and ensures broad coverage across virtual machines, containers, serverless functions, and databases.
4. Smart Vulnerability Prioritization
Vulnerability management is vital for identifying and addressing security weaknesses. A good CWPP prioritizes vulnerabilities based on risk factors like exploitability and asset value, helping you focus on the most critical issues first.
5. Integrated CI/CD Security
To protect your applications from the ground up, your CWPP should integrate with your CI/CD pipeline. This allows security to be woven into every stage of development, ensuring stronger applications with fewer vulnerabilities.
6. Automated Compliance Monitoring
A complete CWPP solution continuously assesses your workloads against compliance standards and regulations. It should provide clear, actionable reports, such as compliance heatmaps, to help your security team focus on areas needing immediate attention.
Advantages of CWPP | CWPP Benefits
With you knowing how CWPP works and its key features, let’s now take a look at some major benefits of a CWPP tool:
CWPP offers a range of critical benefits that empower organizations to secure their entire technology stack, end-to-end. Here are the key advantages:
- Unmatched Visibility; CWPP provides enhanced visibility across your cloud-based applications, enabling your security team to monitor all activities in real time. This allows for early detection of abnormalities, making it easier to take preemptive action against potential threats. With this level of insight, you can continuously protect sensitive data and protect critical applications before vulnerabilities can be exploited.
- Real-Time Threat Detection; One of the strongest benefits of CWPP is its ability to detect and respond to threats as they happen. By recognizing emerging threats and analyzing their behavior in real time, CWPP helps your organization respond immediately to security incidents. This rapid response minimizes the potential damage and prevents breaches from escalating into larger, more harmful attacks.
- Smooth Policy Enforcement: CWPP allows organizations to enforce security policies consistently across their entire cloud infrastructure. It ensures that these policies are applied automatically, adhering to both internal security protocols and external regulatory requirements. This comprehensive policy enforcement helps maintain a secure environment, ensuring that all workloads follow established guidelines.
- Compliance Auditing and Reporting; Another critical benefit is CWPP’s ability to conduct continuous compliance assessments. By auditing workloads and generating detailed reports, CWPP ensures your organization meets regulatory standards such as GDPR, HIPAA, or PCI DSS. This proactive approach to compliance helps safeguard sensitive data and shields your business from costly penalties associated with non-compliance.
- Centralized management: CWPP simplifies security operations by offering a centralized dashboard, giving security professionals full control and oversight of all workloads across cloud, hybrid, and on-premises environments. This simplified management improves efficiency and focuses on critical security issues.
CWPP Use Cases
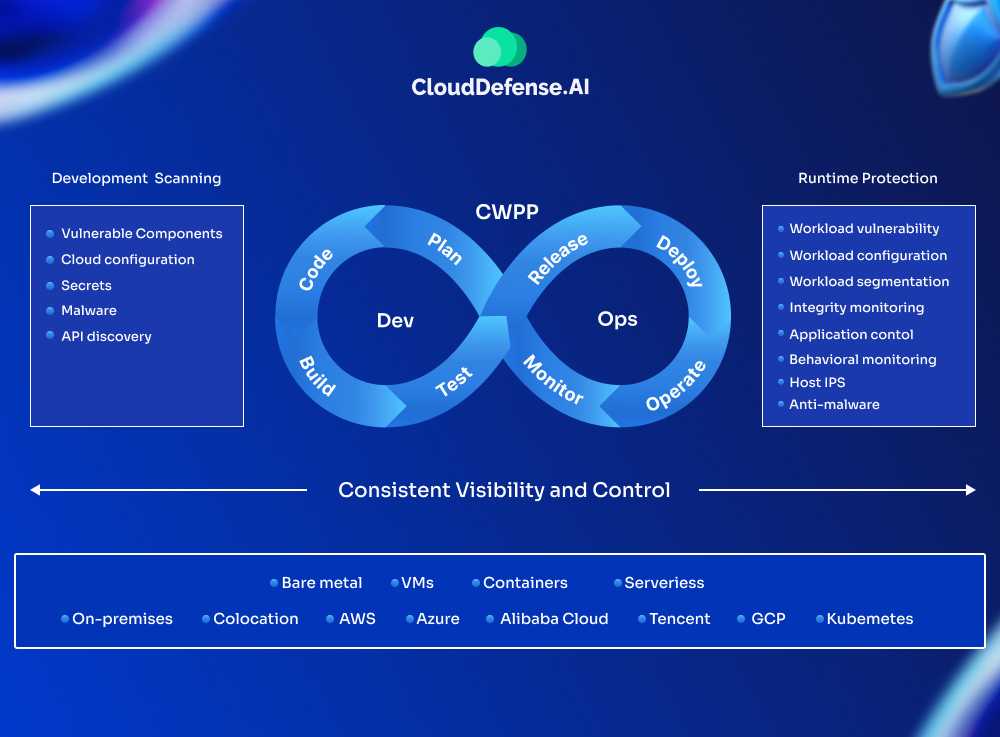
A CWPP tool offers versatile security capabilities designed to protect workloads in dynamic cloud environments. Here are some key CWPP use cases that illustrate its power in defending cloud infrastructures:
1. Detecting Fileless Attacks on Cloud Workloads
Fileless attacks, which execute directly from memory, are particularly difficult to detect as they don’t leave traces on disk. A CWPP plays a critical role in identifying these stealthy threats by monitoring memory behavior and runtime activities.
Take, for instance, the DarkVishnya attack, where attackers used fileless techniques to infiltrate banks in Eastern Europe. They deployed malware from within the network using USB devices, bypassing traditional defenses. With the help of a CWPP tool, security teams can detect such in-memory execution, flag suspicious behavior, and stop the attack before it escalates.
2. Managing Overprivileged Users with CWPP
One common cloud security challenge is managing overprivileged users and services. Over time, services and users may accumulate excessive access rights, leading to potential misuse or exploitation by attackers.
CWPP solutions can be stacked with other Cloud Security solutions such as CIEM that provide granular visibility into permissions and roles across cloud environments. Even though CWPP tools cannot directly manage overprivileged users it can complement identity management solutions by highlighting any suspicious activities.
3. Revealing Cloud Misconfigurations and Configuration Drift
Misconfigurations are a leading cause of cloud breaches, often arising from manual errors or overlooked settings. CWPP helps organizations maintain secure configurations by continuously scanning workloads and cloud environments for misconfigurations.
Through custom host configuration rules, a CWPP tool can automatically detect deviations from secure baselines, even as changes occur over time. In cases of configuration drift—where configurations change unintentionally or due to malicious activity—a CWPP can alert security teams and provide actionable insights to restore the intended security posture.
CWPP vs CSPM: Differences between CWPP and CSPM
While both CWPP and CSPM aim to enhance cloud security, they serve distinct functions. CSPM, which stands for Cloud Security Posture Management, is actually a key component within a CWPP framework, yet they are not the same!
CSPM tools focus on automating the detection and mitigation of security risks across cloud infrastructures, including IaaS, SaaS, and PaaS. Its key applications range from risk visualization and assessment to compliance monitoring, incident response, and smooth DevOps integration.
We can say that CSPM is a vital part of CWPP as it goes on to ensure that security settings are properly configured. In turn, it is helping you to protect both applications and workloads in the cloud.
CWPP is only One Piece of the Puzzle
While you can’t overlook the importance of a CWPP solution, it’s just one element that you will require to secure your cloud environment. CWPP provides complete visibility and threat detection for your workloads, but a well-rounded cloud security strategy demands more.
To fully protect your cloud infrastructure, you need a combination of tools, including:
- CWPP for end-to-end workload protection.
- CIEM to manage access rights and permissions across cloud environments.
- CSPM to ensure secure configuration and resource management.
- DSPM to track and secure sensitive data, ensuring compliance and reducing risks associated with data sprawl.
- And more!
Together, these tools form a CNAPP (Cloud-Native Application Protection Platform), a unified cloud security solution designed to handle the complexity and rapid growth of cloud environments.
By embracing CloudDefense.AI’s modern CNAPP solution, you can simplify cloud security, making it easier to stay ahead of threats thanks to the power of advanced machine learning models and AI!
Want to see how CloudDefense.AI combines these capabilities into a single powerful platform? Schedule a demo to talk with our experts today!







