Kubernetes has become a standard for containerization that has revolutionized the way applications are developed and deployed as microservices. Due to its immense support for different application requirements, more and more organizations are adopting Kubernetes.
However, it has also become important to look after the Kubernetes security as a malicious attack or malware can lead to complete failure and other security incidents. Most vendors don’t emphasize the security of Kubernetes, so when you adopt Kubernetes as your container orchestration platform, you don’t get security measures as a default.
As per a report by Red Hat in 2023, around 90% of respondents were affected by security issues in their Kubernetes environment. So what should you do to protect your Kubernetes runtime environment? Getting a Kubernetes security tool is the best bait. In this article, we will cover the best 10 Kubernetes security tools in 2025 along with:
- What is Kubernetes security posture management?
- What are Kubernetes security tools?
- What to look for in a Kubernetes security solution.
- Kubernetes security solution comparison.
- How to choose the best Kubernetes security tool.
Now, let’s get started.
What is Kubernetes Security Posture Management (KSPM)?
Kubernetes security posture management or KSPM can be described as a comprehensive approach or set of practices for monitoring, evaluating, and managing the security of the Kubernetes environment.
It helps automate security and compliance across the Kubernetes environment to identify and remediate security issues. KSPM is only focused on securing K8 clusters that are mostly vulnerable to different types of attacks due to their dynamic environment. Basically, this security solution provides security teams with a set of technologies and methodologies to help them protect not only the K8 cluster but also the workloads running within it.
The primary goal of KSPM is to prevent all kinds of attacks on cluster components and configurations while maintaining efficient deployment of the workloads in the K8 cluster. This security solution also plays a crucial role in the overall security posture because it helps you define security policies and categorize threats.
Modern KSPM has been designed in such a way that it can automatically detect misconfiguration that enables non-admin users the ability to create pod or other administrative privileges.
What are Kubernetes Security Tools?
Kubernetes security tools are cloud-based security solutions that ensure comprehensive governance and management of the Kubernetes environment. The main job of these tools is to protect the Kubernetes resources and other aspects while adapting to the evolving regulatory landscape.
These security tools are also tasked with maintaining compliance and delivering cluster management capabilities. They take a proactive approach where they detect all types of security threats and deploy the principle of least privilege access to ensure security breaches from user accounts.
Some Kubernetes security tools have been designed to validate and enforce configuration in the Kubernetes environment so that they meet best security practices. These tools also leverage behavioral monitoring to identify anomalies and malicious behaviors and prevent serious breaches.
What to Look For in a Kubernetes Security Solution?
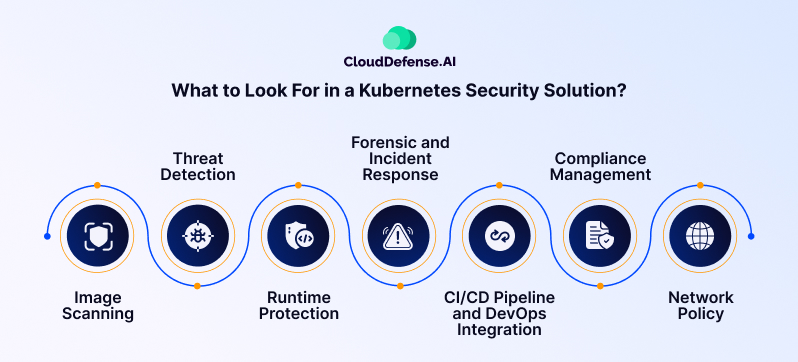
When assessing a Kubernetes security solution, there are certain key features that you should take into consideration because they will ensure optimum protection. Here are the following factors you should look for in a solution:
Image Scanning
When you are assessing a Kubernetes security solution, the first thing you should check is the image scanning capability. The solution should be able to scan the container image to identify security issues and malware before deployment. It not only minimizes the deployment of compromised images but also maintains the integrity of the application.
Runtime Protection
Runtime protection is an important aspect of Kubernetes security because it helps in identifying and responding to any kind of risk, vulnerability, or security threat during runtime. It plays a vital role in mitigating security issues in the application at runtime and preventing access even when the application has been deployed.
Forensic and Incident Response
It is necessary for a Kubernetes security solution to have a forensic and incident response feature because it helps the team assess security incidents and find the root cause. The incident response enables us to assess the fundamentals of the security incident and create necessary changes to prevent such issues from occurring in the future.
CI/CD Pipeline and DevOps Integration
Make sure the Kubernete security tool you will choose must integrate with your CI/CD pipleine and automate the security check. When it integrates with your workflow, it will identify and mitigate any security issues throughout the software development lifecycle. Besides, integrating with DevOps will also help in automating policy enforcement throughout the lifecycle and maintaining optimum security posture.
Compliance Management
Having compliance reporting and auditing features in the security solution will help the developers maintain requirements for industry standards and regulations. The security solution must help you stay compliant to regulations like PCI DSS, HIPAA, ISO, and others as non-compliance will cause serious implications.
Network Policy
While assessing the Kubernetes security solution, you should look for capabilities that will help you implement network policies within the Kubernetes cluster. Applying policies will enable you to govern and control the communication between external networks and pods.
10 Best Kubernetes Security Tools in 2025
Now that you have an in-depth understanding of Kubernetes security, it is time we dive into the top 10 Kubernetes security tools you can utilize in 2025. Here are those tools:
CloudDefense.AI

CloudDefense.AI 
When it comes to considering the best Kubernetes security tools in 2025, CloudDefense.AI serves as the undisputed leader in the market. The top-tier KSPM solution seamlessly integrates with your workflow to discover and remediate issues in your K8 clusters.
It eases the complexity of monitoring by automating security scans across the cluster and prevents all kinds of issues. It takes a comprehensive approach towards Kubernetes security where it identifies misconfiguration and vulnerabilities in real time and remediates them before they can cause an impact.
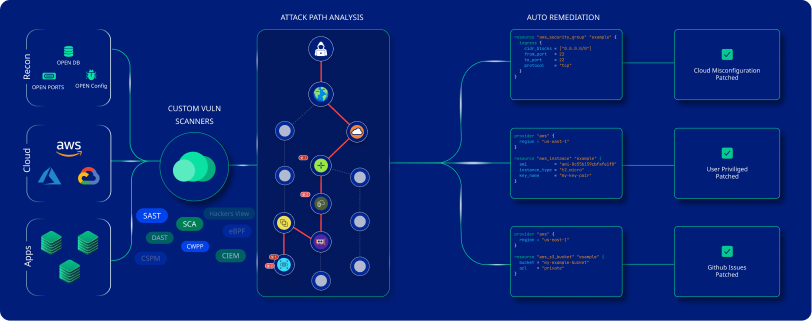
Features
Here are some key features that define CloudDefense.AI as one of the best Kubernetes security tools:
Seamless Cloud Asset Management
CloudDefense.AI delivers seamless cloud asset management that provides a holistic view to monitor clusters, resources, identities, workloads, and other assets. It continuously updates the resources for real-time visibility and helps in ingesting Kubernetes data for comprehensive control.
Automated Scanning
This solution automates security scanning across all your Kubernetes cluster and enables the team to easily identify vulnerabilities and misconfigurations in the environment.
Custom Security Policy
With this KSPM solution, you can define your custom security policies and enforce rules that cater to your organization’s requirements. Setting custom policies, allows you to maintain a comprehensive approach towards the protection of the Kubernetes environment.
Full Stack Risk Assessment
CloudDefense.AI, through this platform, maximizes your Kubernetes security through impeccable risk analysis and prioritizing risk. It amalgamates contain image scanning, IAM misconfiguration detection, compliance enforcement, and network exposure visualization to protect all the assets.
Compliance Automation
It ensures your organization stays compliant with different industry standards and regulations by automating compliance. It eases up the process of identifying violations, audits, and report generation and empowers your organization.
Pros

From scanning and monitoring to compliance management, CloudDefense.AI automates all the processes.

It helps in remediating misconfigurations, violations, and risk privileges thoroughly.

It helps you gain deep insight into your compliance status and security posture.

You can make changes to the security policy to cater to your security needs.
Cons

The employees would require expert guidance and training to manage all the features.
What Sets CloudDefense.AI Apart?
CloudDefense.AI has emerged as a leading Kubernetes security tool by offering a holistic security approach. Here are some areas that set it apart:
Rapid Response To Critical Threats
CloudDefense.AI can rapidly respond to critical threats like Log4Shell by enabling the security team to identify vulnerable assets and patch them. It collects data from various vulnerability sources to accurately identify threats.
Tailored Security Policy
This security solution allows you to customize your security policy and enforce rules to ensure comprehensive protection of your K8 clusters.
Holistic Risk Analysis
This platform combines numerous security features to provide a holistic risk analysis capability and enable your team to seamlessly address all types of issues.
Superior Support
When you opt for CloudDefense.AI, you will be rewarded with the assistance of a security professional team who will impress you with their impeccable assistance on all matters.
Aqua Security

Aqua Security
Aqua Security is another platform that is known for its top-notch Kubernetes security tool. Not only does it provide you with runtime protection and role risk assessment, but it also performs penetration testing and determines the workloads. It utilizes Kubernetes-native capabilities to protect the application.
Features
It provides real-time visibility into your nodes, containers, namespaces deployments, network connection, and other aspects.
Leveraging K8 attributes and OPA, you get to control the workload admission, which ultimately helps in enhancing security posture.
It utilizes Aqua's Image Assurance Policies and eliminates the chance of deploying malicious workloads.
Automates whole compliance checks of your Kubernetes environment by following CIS Kubernetes benchmark.
Prisma Cloud

Prisma Cloud
With impeccable scanning capability and continuous monitoring features, Prisma Cloud often serves as a favorite choice for organizations for Kubernetes security. It offers flexible protection to safeguard your Kubernetes apps and containers and prevents any vulnerability from reaching the deployment stage.
Features
Prisma Cloud continuously monitors the code in container registries and also defines trustworthy images and repositories in the Kubernetes environment.
You can monitor the compliance posture through a dashboard covering all your Kubernetes, containers, and hosts.
It introduces vulnerability scanning, hardens the security checks in the CI/CD, and ensures security issues are addressed before deployment.
Automates baseline policies across the network and Kubernetes clusters to ensure optimum security and that too with complete scalability.
Red Hat Advanced Cluster Security

Red Hat Advanced Cluster Security
You can define Red Hat Advanced Cluster Security as a one-of-a-kind Kubernetes security solution that helps protect containerized applications. This tool hosts a large set of features that work with the dynamic state of the containers to protect the application through its lifecycle.
Features
Utilizes controls embedded in Kubernetes for deploying security policies across the clusters and avoids using third-party proxy tools that might hamper the operation.
Negates all complexity and operational conflict and provides complete scalability and resilience to Kubernetes.
It leverages built-in controls and declarative data to deliver better insight regarding Kubernetes' security posture and ensure continuous hardening.
It streamlines the security analysis and remediation using Kubernetes context and curbs the overall effort needed for implementation.
Kubescape

Kubescape
You can consider Kubescape if you are looking for highly effective open-source Kubernetes security for your K8 clusters and CI/CD pipeline. It is one of the fastest growing tools that offer simple CLI interfaces and flexible output to help admin reduce efforts and resources.
Features
Helps in reducing attack surfaces by effectively detecting misconfigurations and responding with corrective remediation processes.
Seamlessly integrates with different cloud providers like AWS, Azure, and GCP and different Kubernetes distributions.
Scans all the container images to identify vulnerabilities that are embedded into the memory and can lead to security threats to workloads.
It automates Kubernetes security and compliance into your workflow and helps you to secure the CI/CD pipeline completely.
PingSafe

PingSafe
When you are considering the best Kubernetes security tool, you need to take PingSafe into account. It is a top Kubernetes security tool that has a comprehensive security approach to the Kubernetes environment. Moreover, it also helps in detecting misconfiguration and ensuring compliance.
Features
Provides complete visibility into your environment, including SBOM, to help your security team identify vulnerabilities and implement the correct remediation process.
Employs real-time secret scanning capability to scan over 800 secrets available in GitHub, GitLab, and BitBucket.
This security tool generates contextual alerts by analyzing Kubernetes clusters for potential issues and enables the team to remediate them quickly.
It offers continuous compliance monitoring for almost all the popular industry regulations and standards like PCI DSS, GDPR, ISO, HIPAA, and others.
NeuVector

NeuVector
NeuVector by SUSE is a remarkable Kubernetes security tool that delivers DevOps vulnerability protection, automated runtime security, and lifecycle container security. It is one of the kind security tools having a built-in Layer 7 container firewall. Whether you use Azure or GPC, NeuVector supports all platforms and technology.
Features
It utilizes patented container firewall technology to protect the network and all the data associated with the application.
Automated compliance assessment and reporting make it easy for security teams to maintain compliance and also pass audits with ease.
It scans all the container registries and implements admission controls to prevent unauthorized activities that can lead to breaches.
It encompasses the application through the complete CI/CD pipeline through compliance scanning, admission control, and vulnerability management.
Sysdig

Sysdig
Emerged as a highly effective Kubernetes security tool, Sysdig has been helping businesses remediate misconfiguration and isolate faulty images that can lead to potential issues. It provides security teams and DevOps with complete visibility across the Kubernetes environments, which ultimately helps in reducing the attack surface.
Features
Automates the scanning process of images in the CI/CD pipeline and registries and prevents malicious images from getting deployed with the application.
It helps you get complete visibility of the network communication between applications, pods, and services in Kubernetes.
Helps in applying consistent policies across the Kubernetes cluster with the assistance of OPA and ensures adherence to compliance.
It continuously validates CIS benchmarks and compliance and automates compliance.
Anchore

Anchore
Anchore is truly an impressive Kubernetes security tool that helps organization continuously monitor running images and prevent deployment of malicious ones. It is an open-source engine that not only helps you to achieve compliance but also scans all the container images and contents of container registries for vulnerabilities.
Features
Seamlessly integrate with your Kubernetes environment and make sure all the images are scanned before deployment.
Make sure the scanned images are completely free from secrets like API keys and passwords that could be exploited by hackers.
Perform continuous monitoring of the Kubernetes clusters to discover vulnerabilities that can jeopardize the workflow and running containers.
Leverages SBOM data to assess the security posture and compliance violations throughout the deployment phase.
Kube-Bench

Kube-Bench
Kube-Bench is a simple yet highly efficient Kubernetes security tool that primarily checks whether the Kubernetes has been deployed securely. It assesses the deployment by running all the checks listed in the CIS Kubernetes Benchmark. This tool follows authorization and authentication checks and also helps implement the principle of least privilege access.
Features
Kube-bench is extremely easy to implement, and it is compatible with a wide variety of Kubernetes services.
It can efficiently identify security vulnerabilities in the Kubernetes containers and fix them after discovery.
Helps in inspecting the primary node of your Kubernetes clusters and the node configuration using the Kube-bench.
All the tests are configured with YAML files.
Top 10 Best Kubernetes Security Solution Comparison
Tools | Visibility and Vulnerability Detection | Compliance | Integration | Pricing |
Available | Available | Cloud and SIEM. | ||
Aqua Security | Available | Available | CI/CD and SIEM. | The standard pricing starts at $50,000 per year. |
Prisma Cloud | Available | Available | CI/CD and SIEM. | The yearly subscription for the base edition starts at $9000. |
Red Hat Advanced Cluster Security | Available | Available | Native Kubernetes platform. | Red Hat charges $500 per year for every instance. |
Kubescape | Limited | Available | CI/CD pipeline. | It is an open-source tool. |
PingSafe | Available | Available | CIEM and Cloud. | Pricing is offered after a custom quote request. |
NeuVector | Available | Available | Cloud and Kubernetes native. | The pricing depends upon the user node requirement. |
Sysdig | Available | Available | SIEM and CI/CD. | You will get a custom quote upon request. |
Anchore | Available | Available | CI/CD and Registry. | The organization provides custom pricing depending on usage. |
Kube-bench | Limited | Limited | Kubernetes native. | Completely free. |
How to Choose the Best Kubernetes Security Tool?
Selecting the best Kubernetes security tool is a complex task, and the selection should be based on various factors. Here are certain factors that you should take into account:
Feature Availability
While choosing a Kubernetes security tool, you should emphasize on the features available with the tool. The tool should not only be able to detect misconfiguration and vulnerability but also scan containers for security issues. It should carry other features that would prevent the deployment of applications with vulnerabilities.
Usability
The Kubernetes security tool should be easy to use by everyone as it will ensure convenience and user experience. It must come with a simple interface and intuitive control so that the team can use it without going through a steep learning curve.
Compliance Support
The ability to automate compliance, generate compliance reports, and prevent violations is important for a Kubernetes security solution. It should enable the security team to manage workloads effortlessly and make necessary changes in the policy to stay compliant with all the specific industry standards and regulations.
Vendor Reputation
It is always a wise move to choose a Kubernet security tool vendor who is trusted and reputed among organizations. You should assess the developer's credentials and the integrity of the organization. Choosing an unknown vendor can result in vulnerabilities, data theft, and other serious security incidents.
Subscription Pricing
Most Kubernetes security solutions are now offered in the subscription model, and pricing varies by requirement. Many modern vendors offer flexible pricing for the tool, so you should lean to such vendors as you can get better pricing by customizing the requirement.
Conclusion
The Kubernetes security tool has become a necessity for organizations adopting containerized technology. However, choosing the best Kubernetes security tool can be a tricky task.
That is why we did the research on your behalf and came up with the best 10 Kubernetes security tools that will track vulnerabilities and remediate them effectively. In this tool, we have included both top-tier and open-source security tools so that you can choose according to your requirements.







