What is a Security Operations Center (SOC)?
A Security Operations Center (SOC) is a centralized unit that monitors, detects, analyzes, and responds to cybersecurity threats to protect an organization’s digital assets.
Operating 24/7, the SOC uses advanced tools, threat intelligence, and analytics to identify vulnerabilities and prevent cyberattacks. The SOC team, including analysts, incident responders, threat hunters, and managers, collaborates to protect IT infrastructure, networks, applications, and sensitive data.
They employ security information and event management (SIEM) systems, intrusion detection systems (IDS), firewalls, and endpoint protection tools to detect anomalies and respond effectively.
Some Key Functionalities of SOC
A SOC serves as the nerve center of an organization’s cybersecurity, ensuring continuous protection through proactive threat detection, response, and recovery. Below are its core functions:
Asset Inventory Management
SOC maintains a comprehensive inventory of all assets needing protection, including applications, databases, servers, endpoints, and security tools, ensuring complete visibility of the organization’s IT infrastructure.
Routine Maintenance and Preparation
Regularly applies software patches, upgrades, and updates security measures like firewalls and security policies to enhance the effectiveness of existing security tools and ensure business continuity in the event of cyber threats.
Incident Response Planning
Develops and implements incident response plans defining roles, responsibilities, and metrics for measuring response effectiveness in the face of cybersecurity threats or incidents.
Regular Testing
Conducts vulnerability assessments and penetration tests to identify and mitigate potential security vulnerabilities, fine-tuning security policies and incident response plans based on test results.
Staying Current with Threat Intelligence
Keeps abreast of the latest security solutions, technologies, and threat intelligence to adapt security measures and effectively combat evolving cyber threats.
Continuous Security Monitoring
Monitors the entire IT infrastructure 24/7 for signs of known exploits and suspicious activities using technologies like Security Information and Event Management (SIEM) or Extended Detection and Response (XDR).
Log Management
Collects, analyzes, and reviews log data from network activities to establish baseline activity, identify anomalies, and detect potential threats that may otherwise go unnoticed.
Threat Detection and Response
Identifies, triages, and responds to cybersecurity threats with actions such as root cause investigation, isolating compromised endpoints, and deploying antivirus or anti-malware software to mitigate risks.
Recovery and Remediation
Works to restore systems and recover compromised data following cybersecurity incidents, including wiping endpoints, re-configuring systems, or deploying backups to restore normal operations.
Security Refinement and Compliance Management
Implements continuous improvements based on incident learnings and security roadmap, ensuring compliance with data privacy regulations such as GDPR, HIPAA, and PCI DSS to mitigate risks and protect sensitive data.
Security Operations Staffing and Organizational Structure
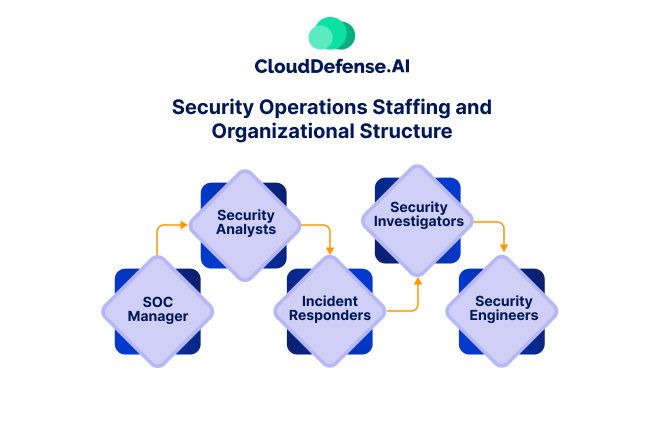
A well-functioning Security Operations Center requires a highly skilled team working in a structured, coordinated manner to protect an organization’s digital assets. Each team member plays a critical role in preventing, detecting, responding to, and recovering from cybersecurity threats. Below is a breakdown of the essential roles and their responsibilities.
SOC Manager
The SOC Manager leads the entire SOC team, ensuring smooth day-to-day operations and aligning security strategies with business objectives. This role involves:
- Overseeing security monitoring, incident response, and risk management activities.
- Developing and enforcing security policies, procedures, and best practices.
- Managing SOC staff, ensuring they are well-trained and equipped to handle threats.
- Reporting security risks, incidents, and compliance status to the CISO or executive leadership.
- Continuously improving SOC processes by integrating the latest cybersecurity frameworks, technologies, and threat intelligence.
Security Analysts (Level 1, 2, 3)
Security analysts serve as the frontline defenders of an organization’s digital environment, and are responsible for monitoring and analyzing security events. They operate at different levels based on expertise and responsibility:
1. Level 1 – Triage & Monitoring:
- Continuously monitors SIEM and other security tools for suspicious activities.
- Identifies and classifies security events, escalating incidents when necessary.
- Assists in initial investigations to determine the severity of a threat.
2. Level 2 – Threat Response:
- Investigates alerts in-depth, correlates security data, and determines the impact of threats.
- Performs hands-on response actions, such as blocking malicious IPs or isolating compromised endpoints.
- Works with incident responders and security engineers to contain threats.
3. Level 3 – Advanced Threat Hunting:
- Conducts deep-dive forensic analysis and proactive threat hunting.
- Identifies indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) used by attackers.
- Refines detection rules and enhances automated security tools to improve the SOC’s threat detection capabilities.
Incident Responders
Incident responders are responsible for reacting swiftly to security incidents, working to minimize damage and restore normal operations. Their responsibilities include:
- It contains and mitigates security breaches by isolating infected systems and terminating malicious processes.
- Assessing the full impact of an incident and coordinating with forensic teams to analyze affected systems.
- Conducting post-incident analysis to determine how an attack occurred and prevent future occurrences.
- Ensuring rapid recovery by assisting in system restoration and implementing additional security measures.
Security Investigators
Security investigators specialize in forensic analysis and deep security investigations to determine the cause and impact of cyber incidents. They play a crucial role in uncovering hidden threats and strengthening defenses. Their tasks include:
- Analyzing network traffic, log files, and endpoint activity to trace cyberattacks.
- Identifying attack vectors, malware behavior, and threat actor tactics.
- Working with law enforcement and regulatory bodies in the event of cybercrime or data breaches.
- Providing detailed reports on incidents and recommending corrective measures.
Security Engineers
Security engineers focus on designing and maintaining the security infrastructure that defends an organization from cyber threats. Their role includes:
- Implementing and configuring security solutions, such as firewalls, intrusion detection/prevention systems (IDS/IPS), endpoint protection platforms (EPP), and zero-trust architectures.
- Automating security workflows using SOAR (Security Orchestration, Automation, and Response) platforms.
- Conducting penetration tests to evaluate the organization’s security posture.
- Optimizing security tools, fine-tuning alert mechanisms, and enhancing response capabilities.
- Ensuring compliance with security frameworks like NIST, ISO 27001, GDPR, and HIPAA.
Organizational Structure
The SOC operates on a hub-and-spoke architecture, with the SOC manager at its core, orchestrating the activities of various teams and systems. This centralized model ensures efficient coordination and oversight, allowing for smooth communication and response to security incidents.
While the SOC primarily functions as an internal, permanent entity within organizations, smaller entities may opt to outsource security functions, integrating subcontracted personnel seamlessly into the SOC framework. This flexibility enables tailored solutions to suit the specific needs and resources of each organization.
In terms of reporting, the SOC interfaces directly with the CISO, who not only manages compliance tasks but also serves as the conduit for communicating security issues to senior management. This hierarchical reporting structure ensures that security concerns are appropriately addressed and prioritized at the highest levels of organizational decision-making.d and prioritized at the highest levels of organizational decision-making.
10 SOC Challenges
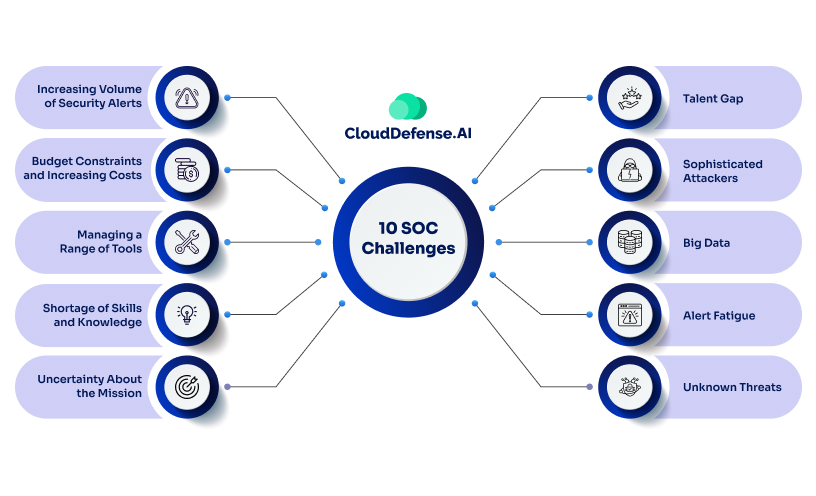
The SOC team’s life isn’t a bed of roses. Even if it is, you do need to remember that roses have thorns too! They often face a myriad of challenges in their daily operations, ranging from technological complexities to human resource management. Here are some of the top ten challenges encountered by SOC teams:
1. Increasing Volume of Security Alerts
The escalating number of security alerts keeps SOC analysts occupied, consuming valuable time in investigating alerts and completing repetitive tasks. This flood of alerts often leads to critical warnings being overlooked or slipping through the cracks, hampering breach detection and resolution timelines.
2. Budget Constraints and Increasing Costs
SOC operations require huge investments, yet budget constraints pose a challenge in justifying spending on cybersecurity measures. Determining the optimal investment to balance security needs against financial constraints remains a persistent challenge, especially given the difficulty in quantifying the potential costs of hypothetical incidents like data breaches.
3. Managing a Range of Tools
As SOC environments require a diverse array of security suites, efficiently monitoring and managing the amount of data provided by numerous tools becomes increasingly challenging. Ensuring integration and centralized management of various technologies is essential for effective security operations and incident response.
4. Shortage of Skills and Knowledge
The shortage of cybersecurity professionals increases the challenge of filling critical roles within SOC teams. Existing employees may struggle to bridge skill gaps, resulting in slower responses and increased risk of errors. Additionally, insufficient knowledge may lead to difficulties in threat perception and an increased false positive rates.
5. Uncertainty About the Mission
Clarity regarding the core mission of the SOC and the prioritization of critical assets for protection is essential for operational efficiency. Without a clear understanding of their objectives, SOC teams may struggle to allocate resources effectively and may overlook significant security vulnerabilities.
6. Talent Gap
A significant shortage of cybersecurity professionals poses challenges in recruiting and retaining skilled SOC personnel. The risk of burnout and attrition among existing team members further compounds the issue, emphasizing the need for talent development and succession planning strategies.
7. Sophisticated Attackers
The evolving tactics of sophisticated cybercriminals pose a challenge to traditional network defenses. SOC teams must deploy advanced tools with machine learning capabilities to detect and mitigate sophisticated threats effectively.
8. Big Data
The exponential growth in data volume poses challenges in real-time analysis and correlation of security-related information. Automated tools are essential for parsing, filtering, and aggregating data to facilitate centralized analysis and timely threat detection.
9. Alert Fatigue
The wave of security alerts, including numerous false positives, contributes to alert fatigue among SOC analysts. Prioritizing alerts based on severity and using behavioral analytics tools can help mitigate alert fatigue and ensure a timely response to critical security incidents.
10. Unknown Threats
Traditional signature-based detection methods may fail to detect unknown threats, such as zero-day attacks. SOC teams must employ behavior analytics to identify unusual behavior and enhance threat detection capabilities.
How can CloudDefense.AI help your SOC Team?
CloudDefense.AI is a CNAPP that has revolutionized the cloud security industry with its range of cloud security tools that are holistically provided in one platform. Let’s explore how CloudDefense.AI can help ease the load on your SOC team by overcoming the many challenges we discussed above.
Addressing the Increasing Volume of Security Alerts
CloudDefense.AI’s Noise Reduction technology helps cut through the clutter of security alerts by prioritizing high-impact threats and actionable insights. By focusing on the most critical alerts, your SOC team can allocate their time and resources more efficiently, reducing the risk of missing important security incidents amidst the overwhelming volume of alerts.
Managing Multiple Tools
CloudDefense.AI offers an all-inclusive Security Suite that provides a wide range of security solutions, from infrastructure scanning to real-time threat detection and automatic remediation. By consolidating multiple security functionalities into a single platform, CloudDefense.AI simplifies tool management for your SOC team, allowing them to monitor and manage security operations more effectively without juggling between disparate tools.
Shortage of Skills and Knowledge
With CloudDefense.AI’s interactive and user-friendly dashboard, even non-technical users can grasp security threats with ease and prioritize risks effectively. Additionally, CloudDefense.AI provides expert support from a team of security professionals who are always ready to assist and guide your SOC team, helping bridge the skill gap and enhance their capabilities in managing security operations effectively.
Uncertainty About the Mission
CloudDefense.AI’s Hacker’s View™ solution provides valuable insights into how hackers perceive your infrastructure, allowing your SOC team to anticipate potential attack pathways and vulnerabilities. By gaining a hacker’s perspective, your SOC team can align their security efforts more effectively with the organization’s core mission and prioritize protection for critical assets, thereby increasing efficiency and effectiveness in defending against cyber threats.
Talent Gap
CloudDefense.AI smoothly integrates with existing tools and cloud providers, eliminating the need for disruptive overhauls and enabling your SOC team to use their existing skillsets more efficiently.
Additionally, CloudDefense.AI’s Code to Cloud approach embeds security best practices from the early stages of development, ensuring vulnerabilities are identified and addressed early on, thus reducing reliance on scarce security talent and mitigating the risk of human error.
Continuous Upgradation
CloudDefense.AI’s AI-powered Security Posture Management (AI-SPM) uses advanced analytics and machine learning to analyze and improve the security posture of cloud environments. By continuously monitoring and analyzing security data, CloudDefense.AI enables proactive identification of emerging threats and vulnerabilities, allowing your SOC team to stay ahead of security risks and ensure ongoing protection for your organization’s cloud infrastructure.







