What is Cloud Computing?
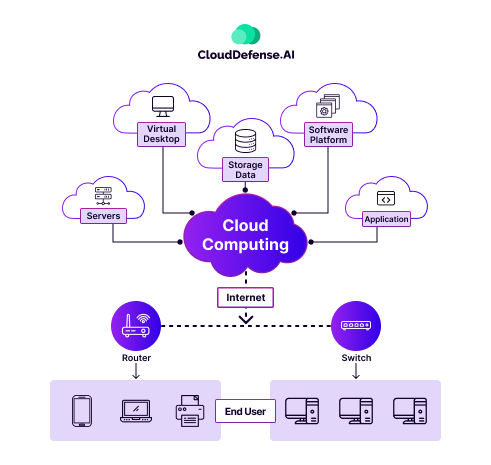
Before stepping into cloud security, let’s clear the air on cloud computing itself—because, honestly, how can we protect something we don’t fully understand? So, cloud computing, in simple terms, is where data and software live on the internet instead of a physical device.
Imagine storing all your files, photos, and apps in a limitless digital warehouse that you can access from any device with a connection. This setup brings unparalleled flexibility, letting businesses and individuals expand their digital reach without the burden of owning massive servers or managing complex tech setups.
| Read More: Curious to dive deeper into cloud computing? Check out our exclusive article for a detailed exploration of cloud computing fundamentals, benefits, and what’s driving its adoption. |
What is Cloud Security?
Cloud security is the strategy and technology stack that keeps cloud-based systems, data, and infrastructure safe from digital threats. It’s about safeguarding what matters most—your data, customer trust, and business continuity—in a virtual environment.
Here’s what cloud security has to offer:
- Protects sensitive data from unauthorized access and leaks
- Detects and blocks cyber threats like malware, phishing, and data breaches
- Ensures compliance with regulations like GDPR and HIPAA
- Manages identity and access controls across users and devices
- Provides visibility into data movement and activity within the cloud
- Maintains data backups to prevent loss or downtime
Why is Cloud Security Important?
In the cloud world, not all environments are created equal. Let’s break it down:
- Public Cloud Environments: These are run by cloud service providers like AWS, Azure, or Google Cloud. The catch? Servers are shared by multiple tenants. While this is cost-effective, it’s also a potential security risk. If one tenant gets compromised, everyone could feel the impact.
- Private Cloud Environments: This can be hosted either in a customer’s own data center or by a third-party provider. Here, servers are single-tenant, meaning no sharing with other companies. The security advantage? You get more control and a more isolated environment. But the trade-off? Higher costs and complexity.
- Hybrid Cloud Environments: This setup blends on-prem data centers with third-party clouds. It’s flexible, but it also requires solid security to manage both environments without gaps.
- Multicloud Environments: Using two or more clouds from different providers is called multicloud. It sounds like a fail-safe, but it adds a layer of complexity when it comes to security. Each provider has its own system, which can make it harder to keep track of threats.
So, why does this matter?
Because in a world where cloud infrastructure is becoming the backbone of everything we do—work, communication, entertainment—its security isn’t just important, it’s critical. Every cloud environment comes with its own set of challenges, and as your systems grow more complex, so does the risk.
A small security gap in a public cloud could lead to massive data breaches. With private clouds, mismanagement of access controls can expose your sensitive data. Hybrid and multicloud setups make it harder to monitor security across the board. The bigger the footprint, the bigger the target.
Here are the risks that comprehensive cloud security practices protects you from:
Stolen credentials: Cybercriminals often use phishing tactics to capture employee login details and infiltrate systems.
Unpatched vulnerabilities: Both hardware and software need regular updates to avoid leaving openings for attacks.
Insider threats: Mistakes or negligence by employees, like misconfigurations or poor decision-making, can create security holes.
Limited resource visibility: Lack of visibility across cloud environments makes it harder to spot and address security risks promptly.
Overwhelming security alerts: When admins are flooded with security recommendations, prioritizing them helps focus on the highest-impact threats.
Excessive permissions: With the rise of multiple cloud services, excessive permissions can expand attack surfaces and increase risk.
Increased attack surface: Cloud security threats are constantly changing, making it crucial to stay ahead of new attack methods.
Lack of development-security collaboration: Without coordination between developers and security teams, vulnerabilities can go unnoticed during the deployment process.
Mismanaged cloud configurations: Incorrectly configured cloud resources can leave critical data exposed to threats.
Third-party vulnerabilities: Relying on external providers can expose your systems to risks from their security flaws.
Data fragmentation: Spreading data across multiple cloud services can create gaps in protection and make it harder to enforce consistent security practices.
These risks aren’t just theoretical—they’re happening in real-time. As cloud technologies continue to evolve, the stakes get higher. Every organization, regardless of size, needs to take proactive steps to mitigate these threats. I
The 6 Pillars of Cloud Security
Cloud security isn’t one thing—it’s a combination of different layers that work together to keep everything safe. These six pillars are the foundation of a strong cloud security strategy.
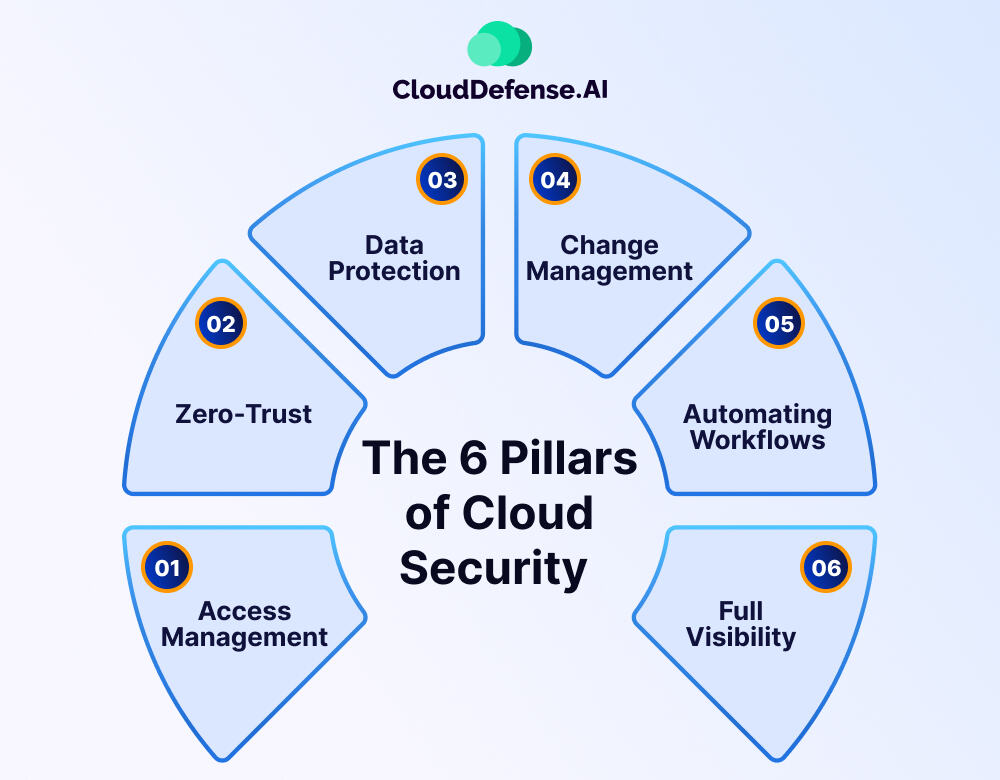
1. Access Management
Controlling who has access to cloud resources is essential. By setting up proper authentication and permissions, organizations can ensure that only the right people or systems can access sensitive data and applications. This includes using strong authentication methods like multi-factor authentication (MFA) and role-based access controls (RBAC).
2. Zero-Trust
Zero-trust means that trust is never assumed. Every user, device, or application is treated as if it could be compromised. This requires continuous verification of users and devices, even if they’re already within the network. It’s about verifying everything before granting access, no matter the situation.
3. Data Protection
Protecting data in the cloud is non-negotiable. This includes encrypting data while it’s stored and during transmission. It’s also about implementing controls to ensure that only authorized users can access or alter sensitive data, and having measures in place for data recovery in case of an incident.
4. Change Management
Cloud environments are constantly changing. Change management ensures that any updates, configurations, or new implementations don’t introduce security risks. Each change should be reviewed, tested, and authorized before it’s made to maintain the integrity of the cloud environment.
5. Automating Workflows
Cloud security is fast-paced, and manual processes can’t keep up. Automating security tasks like vulnerability scanning, patch management, and incident response helps organizations stay ahead of threats. Automation reduces the chance of human error and makes security more consistent and reliable.
6. Full Visibility
To manage security effectively, you need visibility into every aspect of your cloud environment. Real-time monitoring, logging, and alerting allow organizations to identify potential threats and respond before they become bigger problems. The more you can see, the better you can protect your data and systems.
How Cloud Security Works?
Cloud security is all about creating a protective shield around your data and applications in the cloud. It’s not a single solution but a mix of smart practices, cutting-edge tools, and solid planning. Here’s how it works:
- Encryption: Data gets locked up in a secure, unreadable format. Whether it’s moving or sitting still, only authorized users with the right keys can unlock it.
- Access controls: Think of this as the bouncer at the door. Multi-factor authentication (MFA), role-based permissions, and zero-trust principles ensure only the right people get in.
- Network protection: Tools like firewalls, virtual private networks (VPNs), and intrusion detection systems (IDS) act as barriers to filter and monitor traffic, keeping malicious actors out.
- Infrastructure protection and incident response: This is your safety net when things go wrong. It’s about defending your cloud infrastructure and having a solid plan for responding to incidents—identify the threat, contain it, fix it, and recover. Every second counts.
- Continuous monitoring: Imagine having a vigilant guard on duty 24/7. Continuous scanning helps catch unusual activity or weaknesses before they turn into real problems.
- Data backup and disaster recovery: Bad things happen, but backups and recovery plans ensure you bounce back quickly without losing important data.
- Compliance enforcement: Cloud security also means playing by the rules. Following regulations like GDPR, HIPAA, or PCI DSS isn’t just about avoiding fines; it’s about earning trust.
- Automation and AI: Advanced tools use machine learning to predict threats, patch vulnerabilities, and handle security tasks faster than humans ever could.
| Read More: Curious about the most common cloud misconfigurations putting your data at risk? Learn more here to secure your cloud effectively! |
Shared Responsibility in Different Cloud Service Types
In practice, the division of responsibility varies depending on the type of cloud service delivery model being used: Software as a Service (SaaS), Platform as a Service (PaaS), or Infrastructure as a Service (IaaS). Here’s how shared responsibility differs across these models:
| Type of Service | Responsibility of the Vendor | Responsibility of the User |
| SaaS | Security of Applications. | Securing endpoints, managing user access, ensuring network security, addressing misconfigurations, protecting workloads, and data security. |
| PaaS | Security of the platform, including both hardware and software. | Securing developed applications on the platform, managing endpoints, ensuring user and network security, and protecting workloads |
| IaaS | Security of the infrastructure | Securing all applications installed on the infrastructure, including the OS, applications, and middleware. Additionally, managing endpoints, ensuring user and network security, protecting workloads, and protecting data are essential aspects. |
Benefits of Cloud Security
Cloud security offers a range of benefits that help organizations protect their data, applications, and infrastructure. Here are some key advantages:
Enhanced Data Protection
Cloud security solutions employ advanced encryption techniques to protect sensitive data both in transit and at rest, ensuring confidentiality and integrity.
Scalability and Flexibility
Cloud-based security services provide unparalleled scalability and flexibility, allowing organizations to rapidly adapt to changing security requirements and evolving threats. This scalability ensures optimal performance and cost-efficiency.
Cost-Effectiveness
Unlike traditional on-premise security solutions, cloud security eliminates the need for substantial upfront investments in hardware, software, and personnel. With pay-as-you-go pricing models, organizations can align their security investments with actual usage, optimizing cost-effectiveness and maximizing ROI.
Global Coverage and Resilience
Cloud security uses a global network of data centers and points of presence to provide comprehensive coverage and resilience against cyber threats. By distributing security resources across geographically diverse locations, cloud providers mitigate the impact of localized disruptions, ensuring uninterrupted service availability and business continuity.
Managed Services and Expertise
Many cloud security providers offer managed services and expertise to complement their technology offerings. By partnering with experienced security professionals, organizations can offload the burden of managing security infrastructure and personnel, ensuring proactive detection and mitigation of security threats.
Continuous Innovation and Updates
Cloud security providers continually invest in research and development to innovate and enhance their security offerings. By leveraging cloud-based security solutions, organizations gain access to cutting-edge technologies and capabilities that evolve in response to emerging threats and evolving security requirements.
Compliance and Regulatory Alignment
Cloud security solutions help organizations achieve and maintain compliance with regulatory requirements by implementing strong security controls, encryption mechanisms, and audit trails. Cloud security providers often undergo rigorous third-party audits and certifications, assuring compliance and regulatory alignment.
Challenges of Cloud Security
Cloud security is essential but comes with significant challenges that organizations must navigate to safeguard their data and operations.
Securing Third-Party Software and APIs: Third-party applications and APIs are often deeply integrated into cloud environments, but they can create vulnerabilities. Poorly secured APIs and software expand the attack surface, leaving organizations exposed to supply chain attacks, such as the SolarWinds breach.
Lack of Visibility: Cloud ecosystems often involve a mix of IaaS, SaaS, and PaaS components, leading to fragmented visibility. This “cloud sprawl” makes it difficult for organizations to monitor resources effectively, identify vulnerabilities, and respond promptly to incidents.
Shortage of Cloud Security Professionals: The cybersecurity talent shortage has left many organizations relying heavily on third-party services and external tools. Without in-house expertise, addressing the complex demands of cloud-native security becomes a significant hurdle.
Cloud Data Governance Issues: Managing data across multiple cloud platforms presents challenges in ensuring compliance, detecting potential exposures, and understanding data flow. Weak governance frameworks can result in data breaches and long-term reputational damage.
Managing a Rapidly Expanding Attack Surface: The dynamic nature of cloud environments leads to a continuously expanding attack surface. Scaling operations often introduces new vulnerabilities, making it challenging for organizations to secure assets without slowing their pace of innovation.
Insecure Interfaces and APIs: Improperly configured APIs and user interfaces are frequent points of failure in cloud security. If left unprotected, these vulnerabilities can lead to unauthorized access and data breaches.
Lack of a Cloud Security Strategy: Many organizations operate without a clear cloud security strategy. Misunderstandings about shared responsibility models and poor planning result in gaps and weaknesses in cloud defenses.
Compliance Challenges: Regulations like GDPR, HIPAA, and PCI DSS demand strict adherence. Failure to implement adequate security measures and access controls not only invites legal penalties but also undermines trust and brand reputation.
How CloudDefense.AI Helps with Comprehensive Cloud Security?
The challenges outlined above are enough to make anyone concerned about the safety of their cloud environments. Securing data, applications, and workloads in the cloud can feel overwhelming. But don’t worry—CloudDefense.AI is here to help. We simplify security, making it easier to manage without compromising on protection.
Our CNAPP (Cloud Native Application Protection Platform) offers a comprehensive suite of cloud security solutions designed to address these issues head-on.
Here’s a breakdown of our comprehensive suite of cloud security solutions:
Cloud Security Posture Management (CSPM)
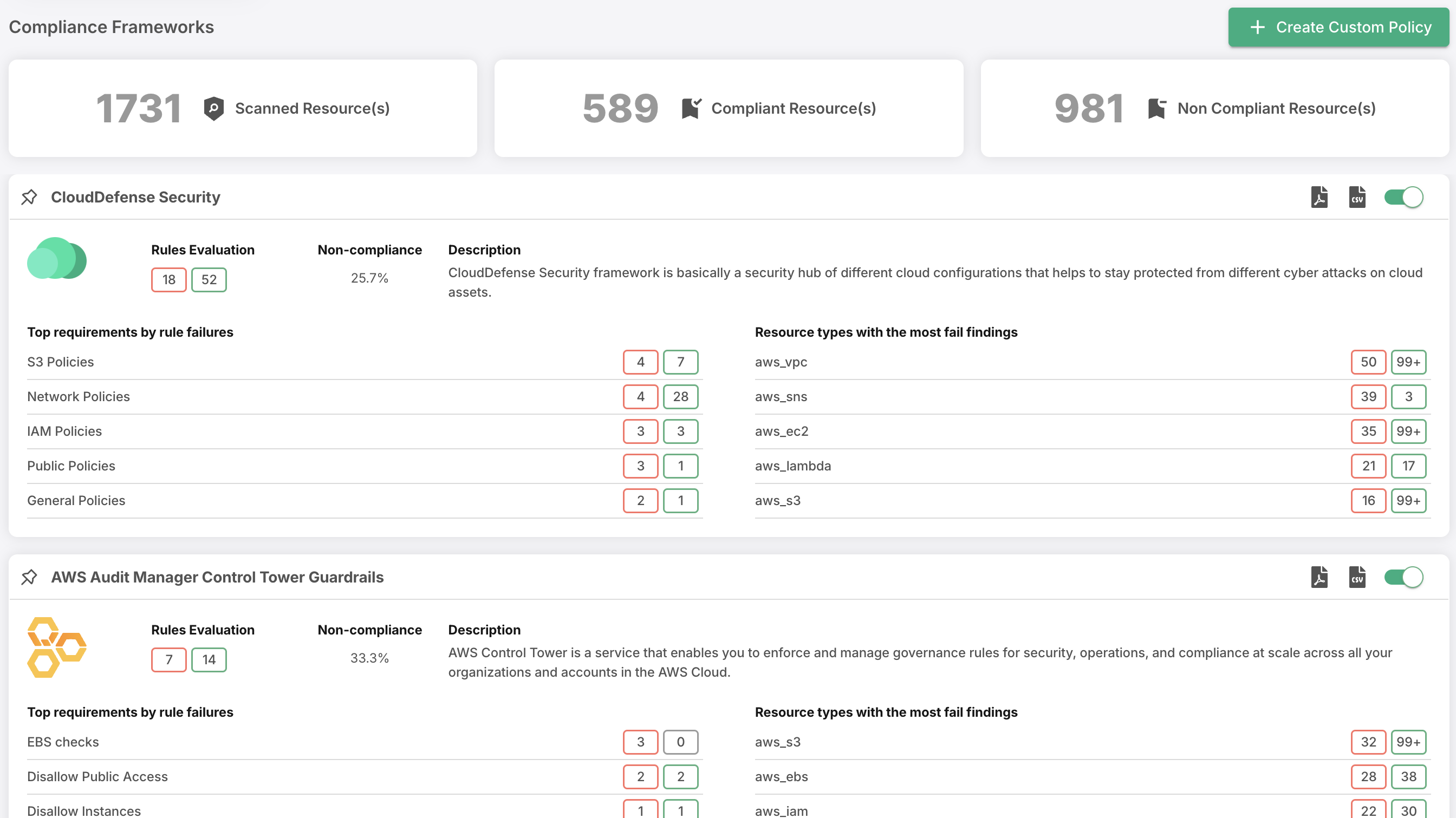
CloudDefense.AI’s CSPM solution continuously assesses your cloud configurations to identify security gaps and misconfigurations. It ensures your cloud environment aligns with industry best practices and compliance standards, reducing the risk of data breaches. With real-time alerts and automated remediation, you can address vulnerabilities quickly before they turn into major issues. Our platform makes it easy to maintain a secure, compliant cloud posture across all your cloud services.
Cloud Workload Protection Platform (CWPP)
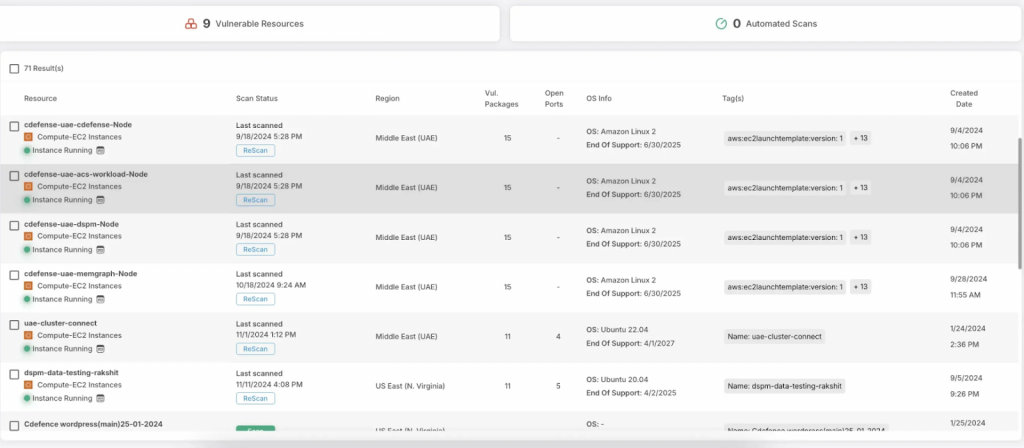
Our CWPP solution is designed to protect workloads across hybrid and multi-cloud environments. It monitors applications, containers, and serverless functions in real time, detecting vulnerabilities and threats that could compromise your data. By continuously analyzing workload behavior, CloudDefense.AI provides automated defenses against known and unknown threats, allowing your teams to focus on innovation without worrying about security gaps.
Cloud Infrastructure Entitlement Management (CIEM)
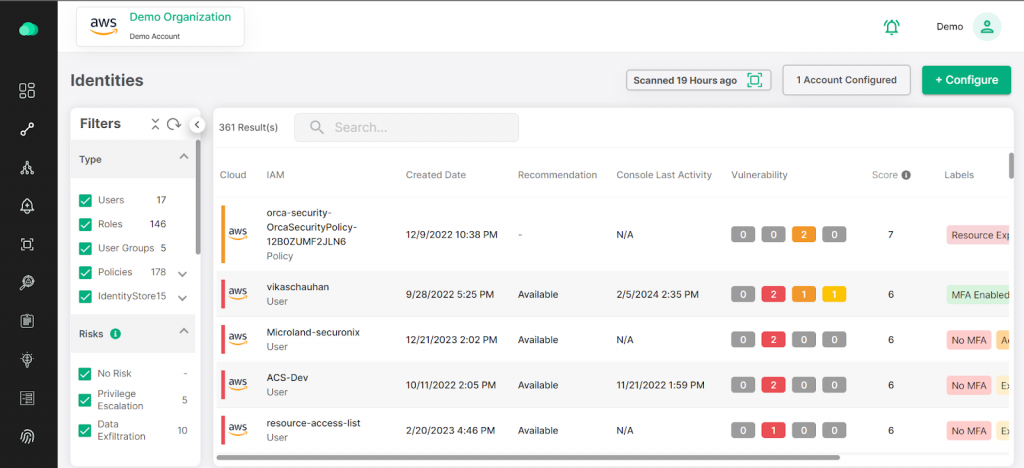
Managing user permissions and entitlements in the cloud can be a complex task. With our CIEM solution, you get granular visibility into who has access to what resources. It helps you manage and enforce the principle of least privilege, ensuring that only authorized users and services have the right permissions. This reduces the risk of insider threats and accidental misconfigurations that could expose sensitive data.
Kubernetes Security Posture Management (KSPM)
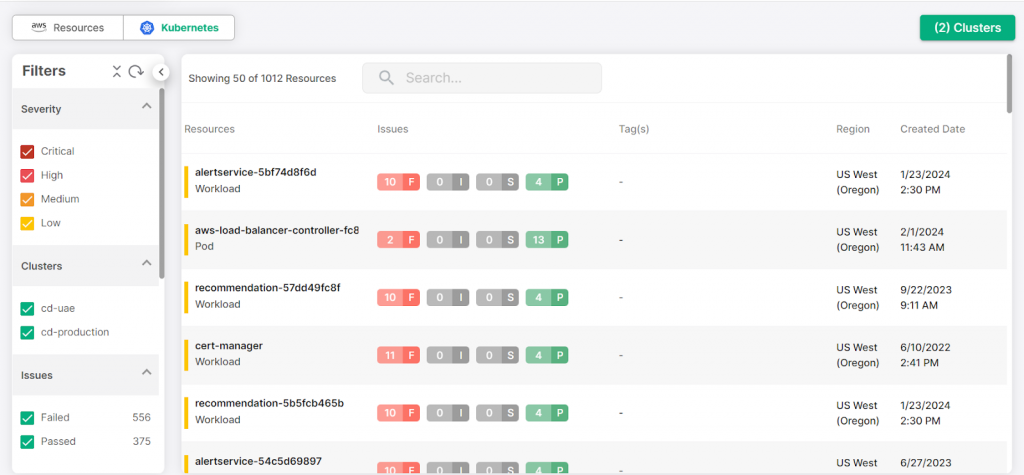
As Kubernetes becomes a key platform for containerized applications, securing it is essential. Our KSPM solution provides continuous monitoring of your Kubernetes environment to detect configuration issues, vulnerabilities, and policy violations. CloudDefense.AI ensures that your Kubernetes clusters are securely configured, preventing unauthorized access and ensuring compliance with security best practices.
Data Security Posture Management (DSPM)
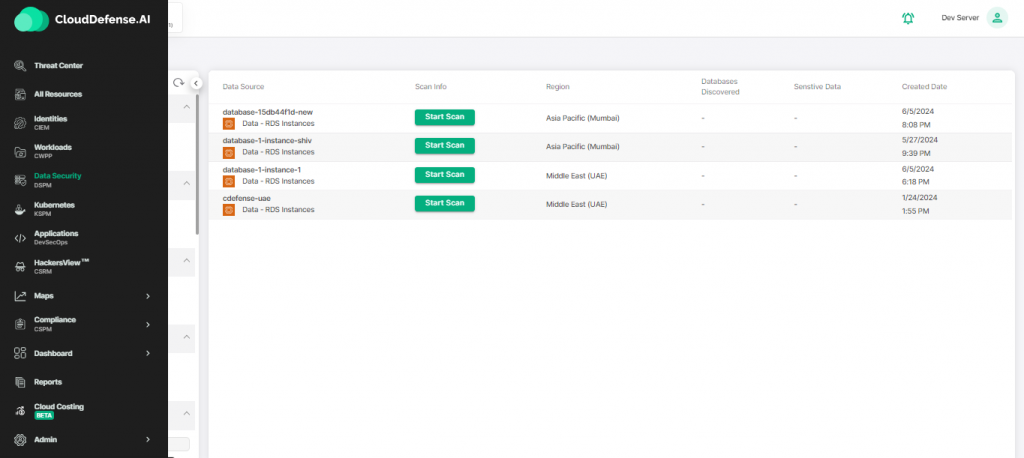
Data security is crucial in the cloud, and our DSPM solution helps you track and secure sensitive data across your cloud environments. By continuously scanning for misconfigured data storage and unauthorized access, CloudDefense.AI ensures that your data remains protected. We provide visibility into where your data is stored, who has access to it, and how it’s being used, reducing the risk of data leaks and breaches.
Real-time Asset Monitoring
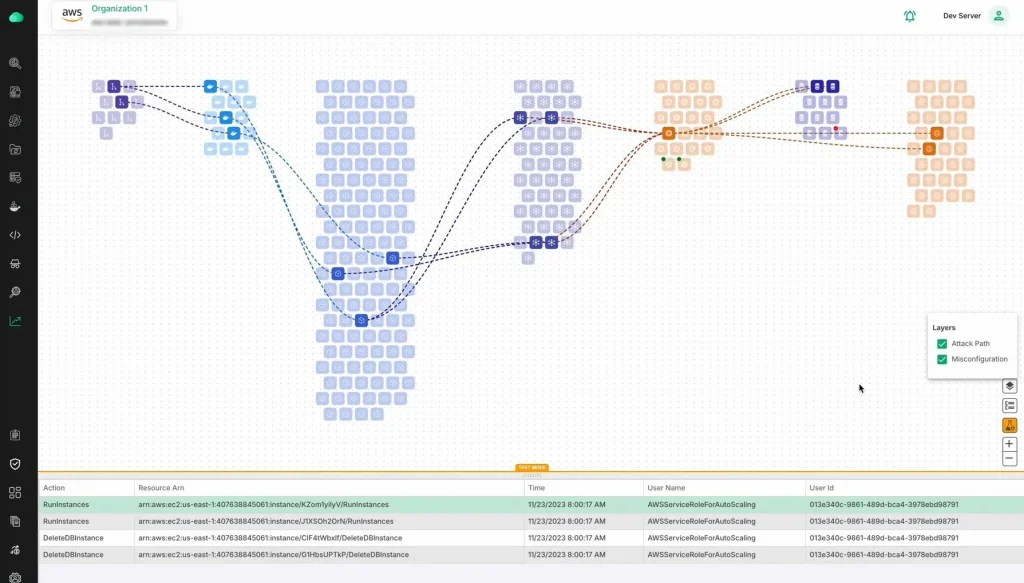
CloudDefense.AI’s real-time asset monitoring tracks every asset in your cloud environment, from servers to containers to applications. Our platform provides an up-to-the-minute view of your infrastructure, detecting changes or anomalies that could signal a potential security issue. With real-time alerts, you can respond quickly to any suspicious activity, preventing threats before they impact your operations.
Hacker’s View
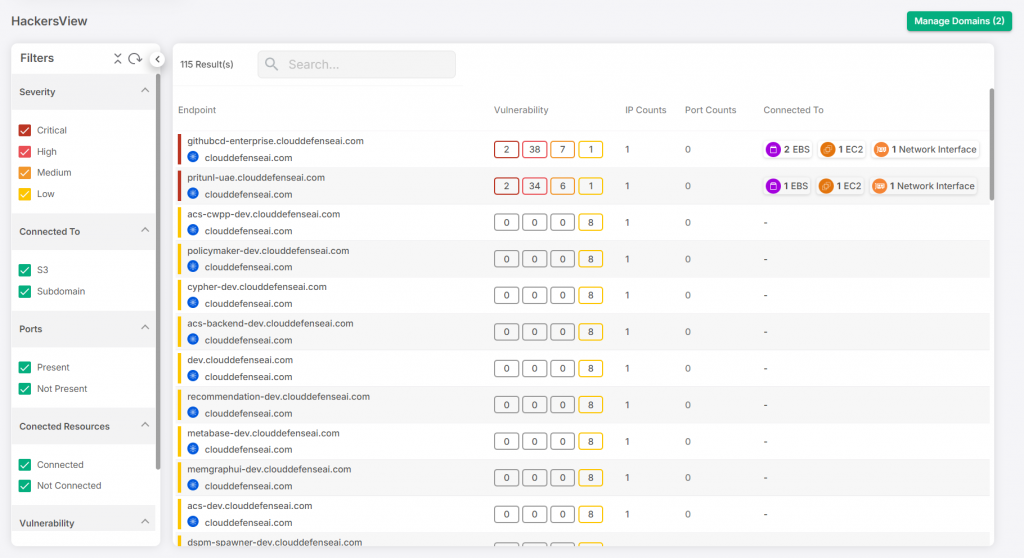
Our Hacker’s View tool gives you a proactive approach to cloud security by simulating potential attack scenarios. By identifying the attack vectors hackers might use, we help you strengthen your defenses. CloudDefense.AI shows you exactly how an attacker would approach your system and highlights weaknesses you can address to prevent a breach before it happens.
AI-SPM
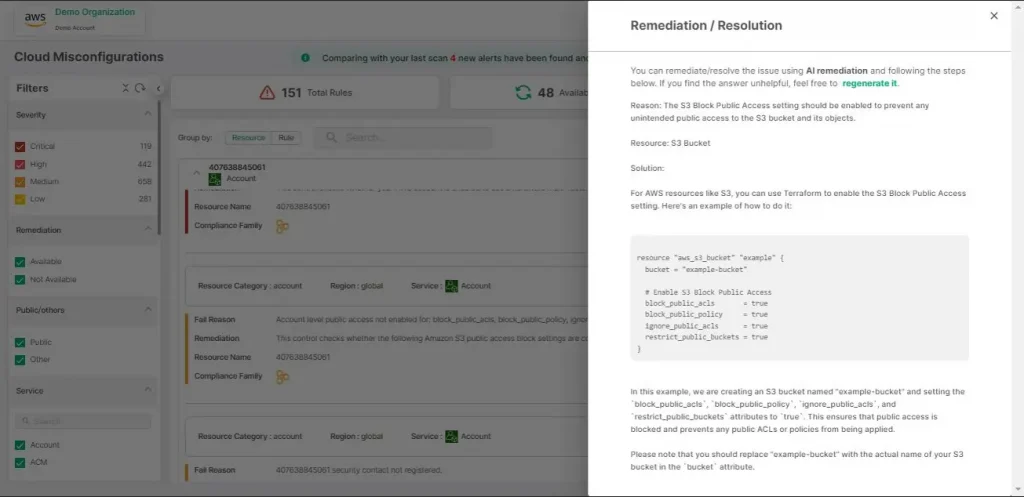
AI-SPM leverages advanced AI technology to continuously assess your cloud security posture. It uses machine learning to detect emerging threats, analyze patterns, and provide insights into potential vulnerabilities. By automating the process of threat detection and risk assessment, our AI-powered solution ensures that your security posture is always evolving and adapting to new challenges.
Ready to see CloudDefense.AI in action? Book a demo today and discover how our comprehensive cloud security solutions can simplify your security operations, protect your assets, and keep your cloud environment safe from emerging threats.







