Top CNAPP per Gartner
requirements
Protect your Cloud and Applications using CloudDefense.AI’s next-gen Cloud Native Application Protection Platform (CNAPP)
Book a Live Demo
Stay Protected
with the Unified Security of
Code to Cloud
to Cloud Recon
Attack Path Analysis
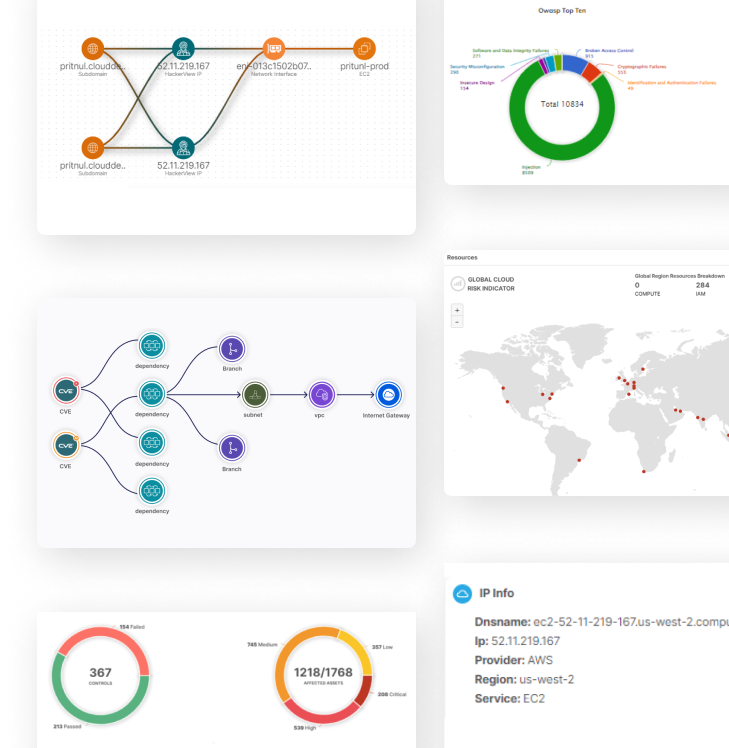
Threat Route Graph
Analyze threats to your system using comprehensive attack path graphs, giving you a better understanding of weak points in your infrastructure.
Check Individual Resources
Dive deeper into your cloud resources with precision. Assess individual resources, ensuring a granular examination for vulnerabilities.
Identify Vulnerabilities
Identify vulnerabilities across each resource on your cloud landscape. Our tool conducts comprehensive scans, spotting potential risks based on their urgency of remediation.
Take Immediate Action
From creating an instant ticket to automatically remediating an issue, respond rapidly to threats in real-time.
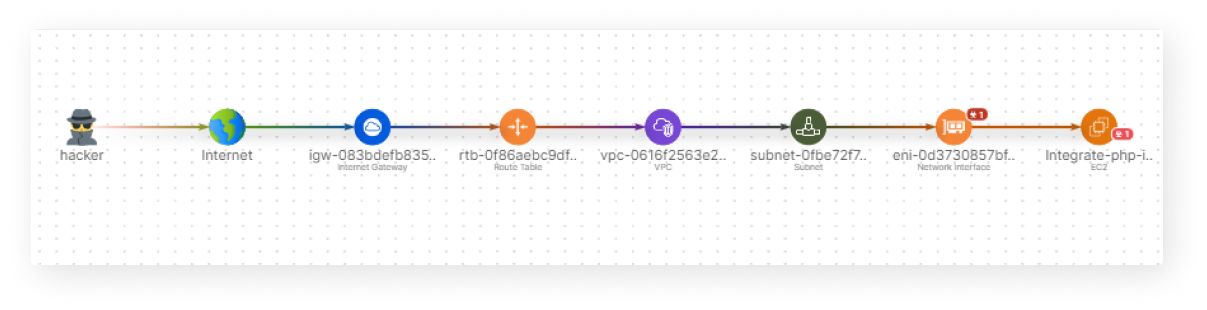
Stay Ahead of Hackers
Meticulously track the route a hacker will take to access your resources. Route maps that will help you to plan your security strategy.
CIEM
Resource Identity
Efficiently manage cloud resource identities. Each resource connected to your infrastructure is uniquely identified and properly categorized.
User Access Analysis
Gain insights into user access patterns, allowing you to understand who accesses what, when, and how.
Identify Risks
The tool scans each identity, pinpointing potential vulnerabilities and access anomalies.
Remediate Risks
Take immediate action to address identified risks. Implement measures recommended by our tool to enhance your access policies.
Individual User Access Map
Understand a user’s access patterns using detailed access maps. Know what actions they can perform on each identity. Actions that withhold risks to your infrastructure are highlighted for you to curb a user’s access to restricted resources.
CWPP
Identify Internal Workloads
Identify all internal and on-premise workloads on your cloud infrastructure.
Workload Vulnerability Scanning
Scan each workload to identify vulnerable packages contained inside it. At the same time, identify all malicious files that can put your system at risk.
Identify Known Vulnerabilities
Each package is scanned against a database of known CVEs, allowing you to identify the CVE code for each vulnerability that the workload contains.
Assess Severity of Risks
Vulnerabilities are marked based on the risk they pose to the system. Severities range from Low to Critical.
Comprehensive Insight on Threats
Receive comprehensive insights and analytics after finishing each scan on your system. This provides you with an holistic view of the threats that lie inside your workloads.
Compliance Management
Compliance Dashboard
One unified dashboard to access all compliance frameworks.
Compliance Resource Scan
Scan your resources to get detailed analytics on compliant and non-compliant resources against 20+ compliance frameworks.
Identifying Non-Compliant Resources
Discover resources that are not compliant. This helps streamlining your path to attaining compliance with your preferred framework.
Remediate Compliance Issues
Remediate non-compliant resources based on their urgency.
A Smarter Approach to Compliance Management
It can not only identify compliant and non-compliant resources but also lets you create your own custom policies to ensure resources are handled according to industry standards.
Threat Detection
Detect Unusual Behavior
Get elevated threat detection to uncover anomalies in real-time, swiftly identifying deviations from normal user behavior patterns.
Comprehensive Threat History
Gain insights into past incidents to understand attack patterns and empower your security teams with the knowledge needed to strengthen your defenses against evolving threats.
Threat Forensic
Conduct in-depth investigations into detected threats, analyzing the event histories of compromised users.
Track the Damage
Track the damage a security incident can do to you. Quantify the impact, identify compromised assets, and streamline the remediation process.
Comprehensive Threat Detection Ruleset
Stay ahead of emerging threats with a robust set of rules that cover a wide range of security scenarios. Keep enhancing your threat detection strategy, ensuring proactive defense.
Hacker's ViewTM
A Hacker's Viewpoint of your Resources
Have a look at your resources from the eyes of an hacker. Receive comprehensive analysis of the threats to your resources.
Compliance Compatibility
Enable compliance frameworks to scan your resources according to the relevant standards.
Analysis of Underlying Threats
Discover threats to your system that are hidden inside the many layers of your infrastructure.
Identify Vulnerabilities
Identify vulnerabilities in your system based on the OWASP top ten category.
Supports Multiple Cloud Services
Receive support for three major cloud services, including AWS, Microsoft Azure, and GCP.
SAST
Identify Vulnerabilities Internally
Detect vulnerabilities early in the development process and promptly address issues without disrupting the build.
Detect Problematic Code
Run scans to detect code that can be a security hazard. Vulnerable code is highlighted and prioritized for you to take swift action.
Comprehensive Code Analysis
Receive in-depth guidance on remediation as your code is analyzed against a CWE database.
Severity of the Risks
Each risk is marked with a severity score to help you strategize your security response.
Interactive Graphical Report
Receive a graphical report of each SAST scan to help you get an overview of the vulnerabilities that your applications contain.
DAST
Identify Vulnerabilities Externally
Detect vulnerabilities that lie in the front of your web-applications.
Attack to Defend
Carry out DAST scans to attack your web-applications like a hacker and identify vulnerable entry points.
Identify Vulnerabilities Immediately
Receive a report of all the vulnerabilities your applications contain at external points without providing access to the source code.
Severity of the Risks
Each risk is marked with a severity score to help you strategize your security response.
Online DAST Scans
Scan your websites using our comprehensive online DAST scans. Simply paste the link on our portal and click on Run Scan to receive a detailed report of all the vulnerabilities on your site.
SCA
Cleanse Your System from the Core
Examine package managers, source code, manifest files, container images, binary files, and other components for a comprehensive analysis.
Bill of Materials
Identified open source resources are compiled into a BOM for you to keep record.
Comprehensive Vulnerability Detection
Your BOM is compared with a number of vulnerability databases, allowing you to identify anything that is out of place.
Severity of the Risks
Each risk is marked with a severity score to help you strategize your security response.
Interactive Graphical Report
Each SCA scan is presented with an interactive graphical report that highlights all the vulnerabilities that are present in the third-party resources that you use.
API Security
Powerful API Scan
Deploy API scans on the fully packaged image of your run-time applications to find vulnerabilities.
OWASP Top 10 Security Threats
API scans that cover all the OWASP top 10 security threats.
Multi-language Compatibility
Whether your application operates on Python, Java, or JS, the API scanning functionality will automatically search for potential issues.
Severity of the Risks
Each risk is marked with a severity score to help you strategize your security response.
Interactive Graphical Report
Each API scan presents you with an interactive graphical report that you can use to identify vulnerable API codes.
Container Security
Continuous Container Image Scans
Carry out continuous scans of your container images to identify any underlying vulnerabilities.
Complete Container Solution
Not only vulnerabilities, but you can also detect misconfigurations and unknown components in your containers.
Comprehensive Vulnerability Database
All the vulnerabilities detected in your containers are matched against a database of known vulnerabilities to help you with the remediation process.
Easily Track Vulnerabilities
Track all the vulnerabilities in your containers at ease.
Remediate Container Vulnerabilities
Get instant guidance on how to remediate the container vulnerabilities detected after a container scan. Easily copy the code that is automatically generated by our tool to resolve the weak point in your containers.