What is Code to Cloud Security?
Code to Cloud Security is a practice designed to secure cloud-based applications throughout their lifecycle. It aims to minimize vulnerabilities using a dual approach.
Moving forward, it identifies and addresses potential security risks in the code before they reach the cloud.
In reverse, it detects security issues in the cloud environment and traces them back to their origin in the application code, enabling precise and effective remediation.
How Does Code to Cloud Security Work?
As we discussed, Code to Cloud Security ensures that security is integrated throughout the entire software development and deployment lifecycle.
This approach offers comprehensive protection by proactively securing the code before it is deployed to the cloud and tracing any emerging security issues back to the original code.
Let’s explore the key processes involved in maintaining a secure cloud environment using Code to Cloud Security.
Securing Code Before It’s Deployed to the Cloud
Before your code even reaches the cloud, several steps ensure its security:
Software Composition Analysis (SCA)
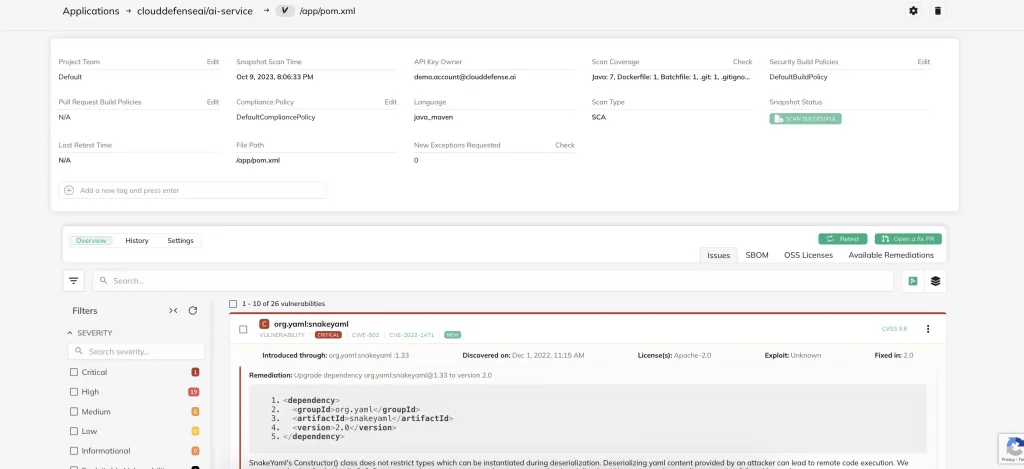
SCA is an in-depth analysis of the third-party components used in your code, such as open-source libraries and frameworks. It creates a dependency map to visualize how these components interact and checks them against a database of known vulnerabilities.
If a match is found, the component is flagged, enabling you to address the risk before deployment. SCA also ensures compliance with licensing regulations, preventing legal issues later.
Static and Dynamic Application Security Testing (SAST & DAST)
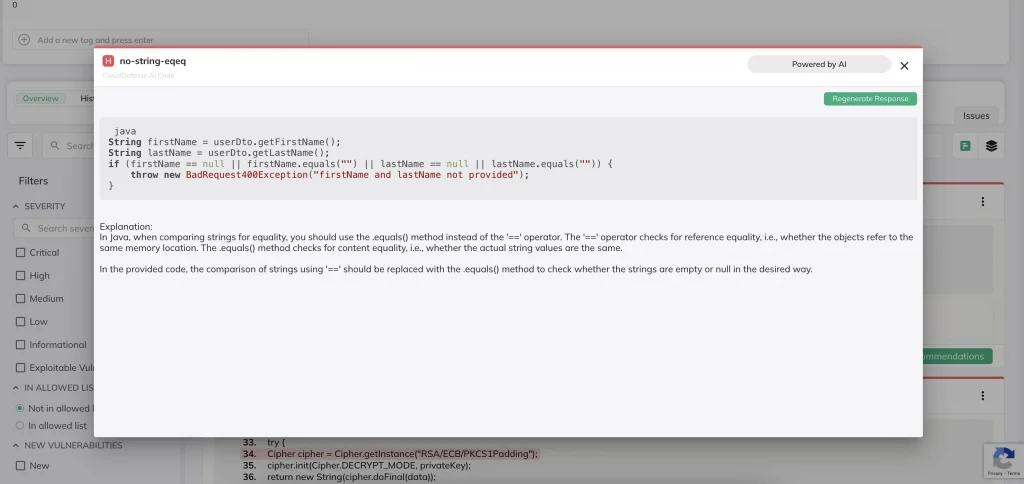
Both SAST and DAST are essential for identifying vulnerabilities early and late in the development process:
- Static Application Security Testing (SAST) analyzes source code for security flaws without executing it. This approach helps detect issues like injection vulnerabilities and insecure configurations early in development.
- Dynamic Application Security Testing (DAST) evaluates running applications to identify vulnerabilities that occur during execution, such as cross-site scripting (XSS) and SQL injection.
Together, SAST and DAST provide a comprehensive security assessment, identifying both code-level issues and runtime vulnerabilities before deployment.
Securing Infrastructure as Code (IaC)
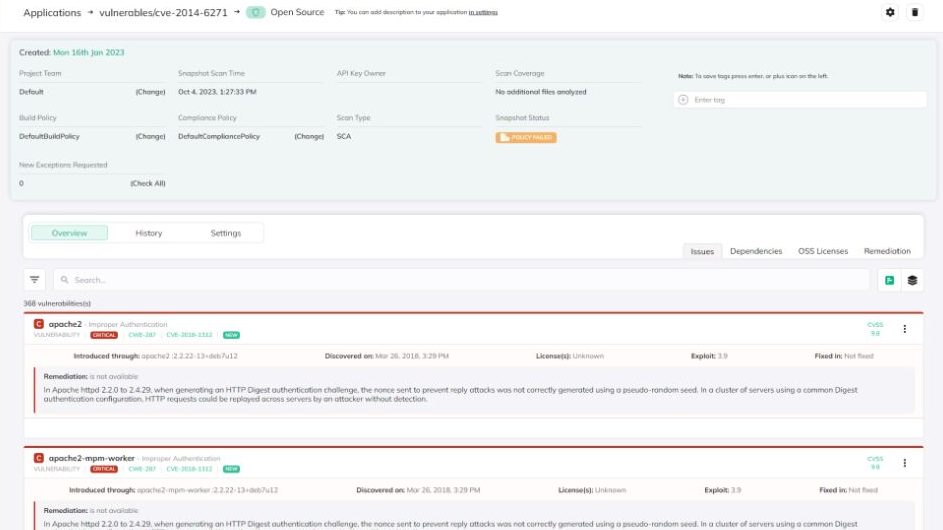
Infrastructure as Code (IaC) is essential for cloud-native applications, and vulnerabilities in IaC can jeopardize the entire cloud setup. Securing IaC involves:
- Scanning templates (like Terraform and AWS CloudFormation) to detect misconfigurations or policy violations.
- Using version control to monitor changes and roll back if necessary.
- Testing IaC code with specialized frameworks before deployment.
- Implementing strict access control to ensure that only authorized personnel can modify IaC.
Secret Management
If exposed, sensitive information such as passwords or API keys can be hard-coded within the code, posing severe security risks. Secret scanning tools detect and remove these hardcoded secrets, ensuring they aren’t inadvertently pushed to the cloud and compromised.
Tracing Security Issues in the Cloud Back to Code
Once your code is deployed to the cloud, ongoing monitoring and tracking are essential to detect and fix any emerging security issues. Here’s how it’s done:
Cloud Workload Protection Platforms (CWPP)
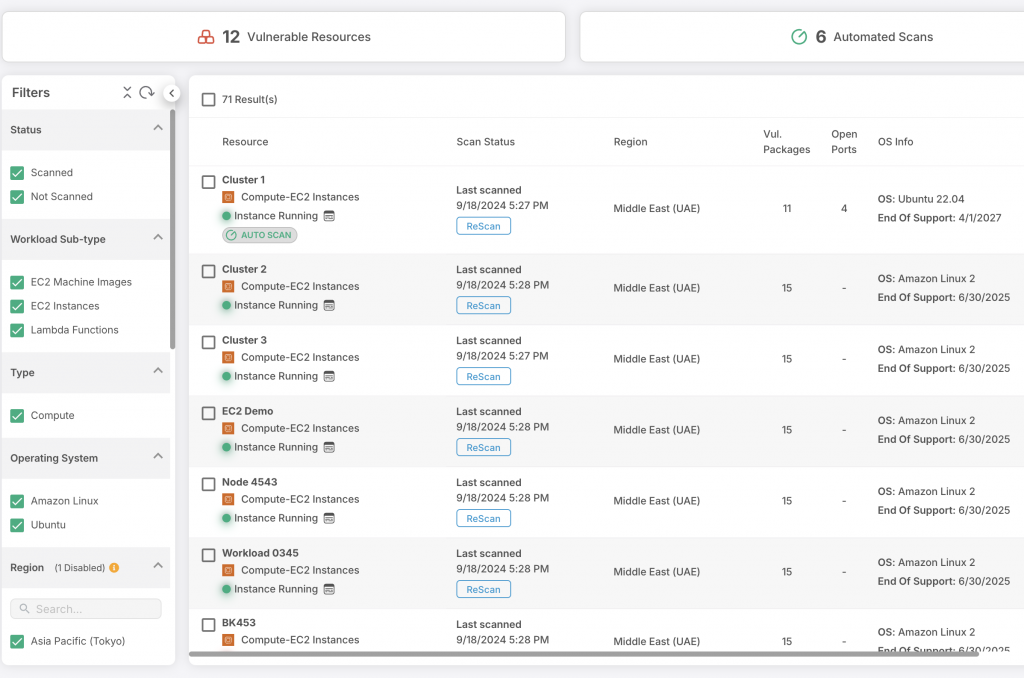
CWPP helps monitor cloud workloads in real time, detecting unauthorized access, malware, and other suspicious activities. Key features include:
- Real-Time Monitoring: Continuously watches for unauthorized access attempts and potential threats.
- Misconfiguration Detection: Regular scans to identify misconfigurations and outdated resources.
- Network Segmentation: Limits lateral movement within cloud networks if a breach occurs, reducing overall risk.
Cloud Security Posture Management (CSPM)
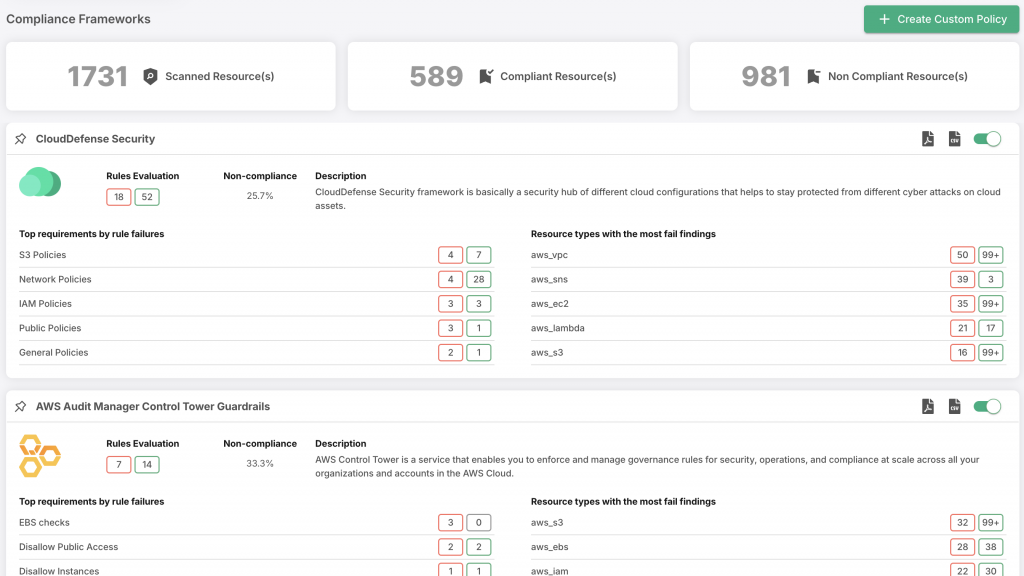
CSPM continuously monitors cloud resources to ensure security and compliance:
- Constant Monitoring: Keeps an eye on your cloud environment to detect any security anomalies.
- Compliance Checks: Identifies compliance gaps and offers suggestions to rectify them.
- Threat Detection: Flags critical threats and ranks them based on their potential impact.
- Automated Fixes: Automates the remediation of configuration issues, improving operational efficiency.
Kubernetes Security Posture Management (KSPM)
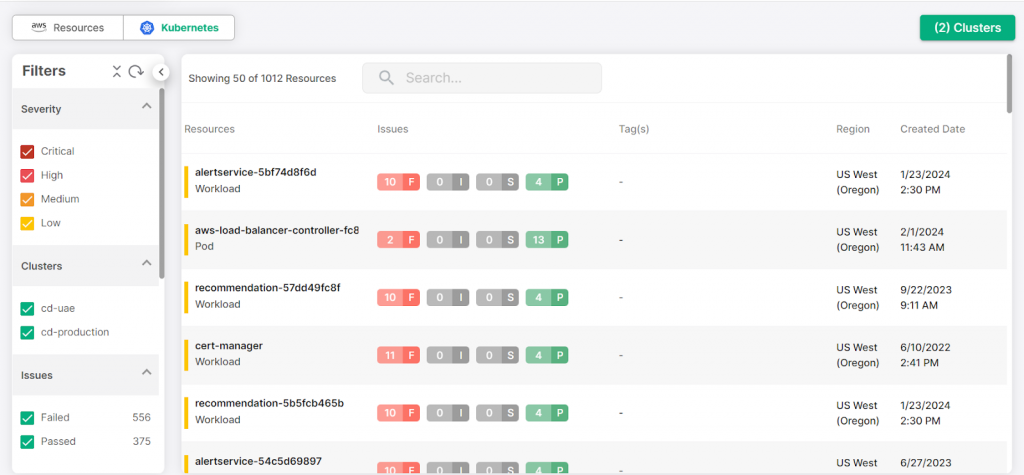
Designed for Kubernetes environments, KSPM helps secure containerized applications by:
- Configuration Checks: Ensuring Kubernetes clusters are configured according to security best practices.
- Policy Enforcement: Enforcing security policies across the Kubernetes environment to reduce risk and maintain compliance.
- Continuous Monitoring: Regularly scans for vulnerabilities, misconfigurations, and security threats within Kubernetes workloads.
Web Application and API Protection (WAAP)
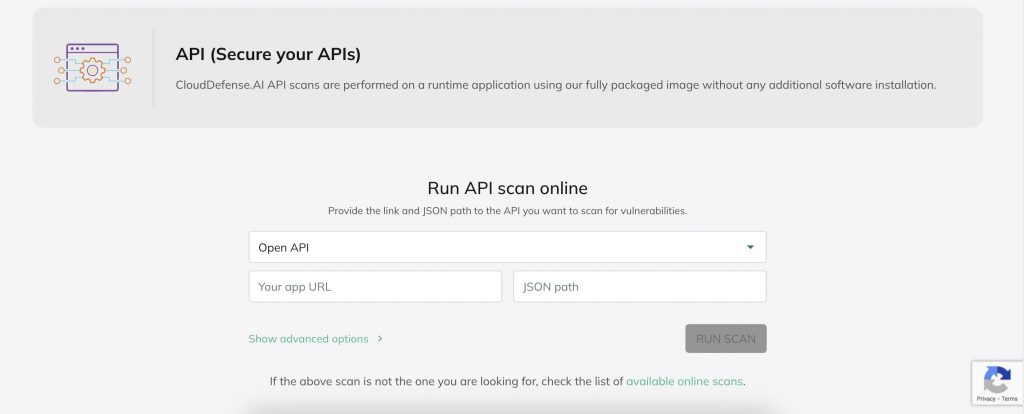
WAAP protects web applications and APIs from common threats, such as cross-site scripting (XSS), DDoS attacks, and brute-force hacks. By continuously monitoring web traffic and API requests, WAAP helps identify vulnerabilities in cloud applications and traces them back to the code source. This ensures that any identified security issues are quickly fixed, minimizing the risk of a breach.
Code to cloud security ensures your applications remain secure from development through cloud deployment. By securing code before it reaches the cloud and tracing issues back to their source, organizations can identify and address vulnerabilities early, significantly reducing the risk of cyber threats and ensuring complete cloud security.
Key Elements of Code to Cloud Security
To successfully implement Code to Cloud Security, several key elements work together to provide protection across the entire SDLC.
These elements ensure that security is continuously integrated, addressing risks at every stage, from code creation to cloud deployment. Here are the essential components:
1. Secure Coding Practices: By incorporating secure coding practices, developers proactively address potential vulnerabilities within the codebase.
This step helps reduce the risk of weaknesses being introduced early in development, allowing teams to prevent security issues before they escalate into more significant threats when the code is deployed to the cloud.
2. Security Automation: Automated security testing plays a pivotal role in Code to code to cloud security.
Tools like SAST and DAST help continuously monitor code for vulnerabilities.
Automation ensures that security checks are performed regularly, catching potential issues before they make it into production and improving the overall efficiency of the security process.
3. Identity and Access Management (IAM): Effective Identity and Access Management (IAM) is crucial for controlling who can access, modify, or deploy code.
By implementing strong IAM practices, organizations can prevent unauthorized access to sensitive code and protect against supply chain attacks.
Role-based access controls (RBAC) and multi-factor authentication (MFA) further strengthen cloud security by ensuring that only authorized individuals have access to critical resources.
4. Supply Chain Security: Modern applications often rely on third-party libraries and components, which can introduce vulnerabilities.
Supply chain security helps mitigate these risks by incorporating Software Composition Analysis (SCA) to monitor and evaluate the security of third-party code.
This ensures that any external code included in the project does not present a security risk before being deployed in the cloud.
5. Compliance Support: Maintaining regulatory compliance is a significant challenge in multi-cloud environments.
Automated compliance validation tools ensure that applications meet regulatory standards like GDPR, HIPAA, or PCI DSS at all stages of development.
By automating compliance checks, organizations can maintain security while minimizing the risk of non-compliance, ensuring applications meet necessary legal and security requirements.
Why is Code to Cloud Security Crucial?
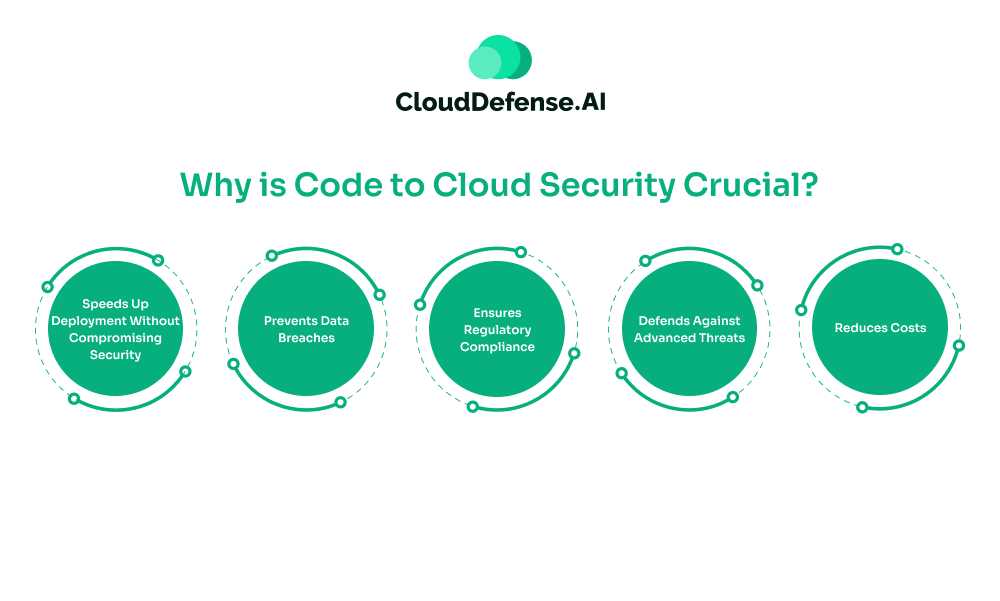
Ensuring the security of cloud applications is essential for protecting sensitive data and maintaining business continuity. Code to cloud security addresses this need by embedding security measures throughout the software development lifecycle, reducing vulnerabilities before they reach production. Here’s why it’s vital for modern organizations:
Speeds Up Deployment Without Compromising Security
By automating security checks and integrating feedback loops into the development pipeline, code to cloud security ensures faster releases while maintaining compliance and minimizing vulnerabilities. This allows teams to focus on building features rather than firefighting security issues at the last minute.
Prevents Data Breaches
Vulnerabilities like SQL injection and XSS can provide attackers with access to critical data. Code to cloud security detects and addresses these issues early, protecting against data breaches that can lead to significant financial and reputational damage.
Ensures Regulatory Compliance
Organizations must adhere to strict data protection regulations such as GDPR and HIPAA. Code to cloud security helps businesses maintain compliance by proactively identifying and fixing vulnerabilities, avoiding costly fines and legal issues.
Defends Against Advanced Threats
With the rise of sophisticated attacks, including supply chain breaches, code to cloud security provides early detection and remediation of subtle vulnerabilities. This proactive approach helps protect against advanced threats before they can compromise systems.
Reduces Costs
Identifying vulnerabilities early in the development process is far more cost-effective than addressing issues post-deployment. Code to cloud security minimizes the costs associated with remediation, data breaches, and regulatory non-compliance.
Best Practices to Implement Code to Cloud Security
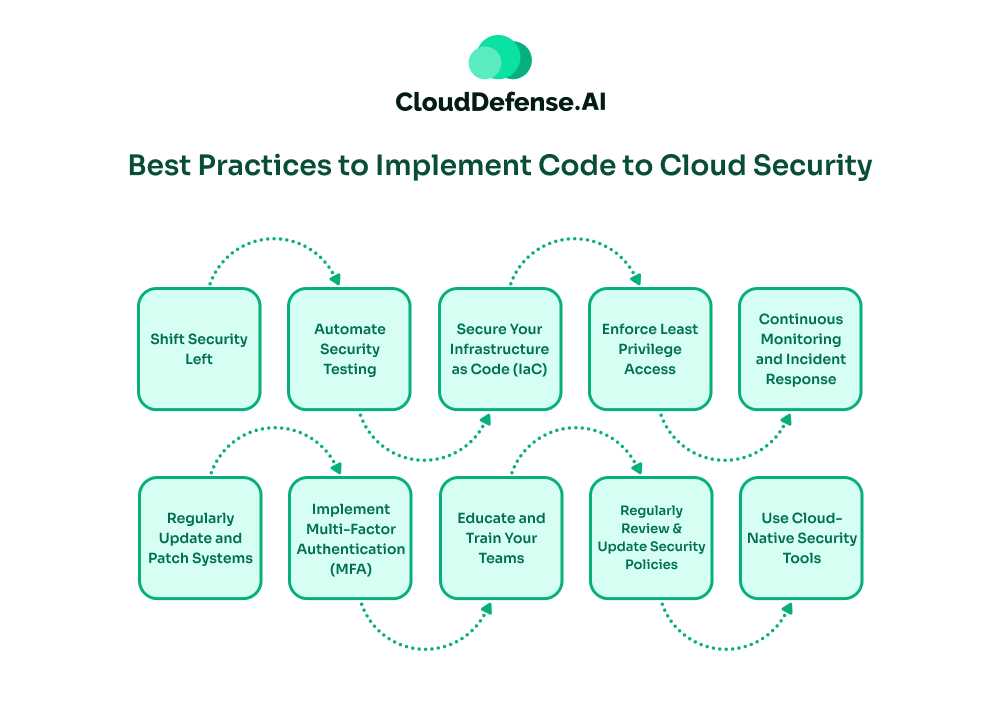
Getting Code to Cloud Security right means covering all your bases—from the first line of code to ongoing cloud operations. Here’s how to make sure your security game is strong:
Shift Security Left
- Start thinking about security early on in development.
- Regularly review code and run vulnerability checks during the build process.
- Use tools like SAST, DAST, and SCA to catch issues before they hit the cloud.
Automate Security Testing
- Set up automated tools to constantly check for vulnerabilities and misconfigurations.
- Use CI/CD pipelines to run security checks at every stage of deployment.
- Automate secret management to find and get rid of hardcoded secrets.
Secure Your Infrastructure as Code (IaC)
- Regularly scan IaC templates to catch misconfigurations and policy breaches.
- Use version control to track changes and roll back if needed.
- Enforce strict access controls to make sure only the right people can tweak IaC.
Enforce Least Privilege Access
- Only give access to cloud resources based on what’s absolutely necessary.
- Use role-based access control (RBAC) to manage permissions smartly.
- Regularly audit who has access and update controls as needed.
Continuous Monitoring and Incident Response
- Deploy tools like CWPP and CSPM to keep an eye on your cloud environment non-stop.
- Set up alerts for any suspicious activity or potential threats.
- Have an incident response plan ready to tackle and fix issues quickly.
Regularly Update and Patch Systems
- Keep all your software, frameworks, and third-party tools up to date with the latest security patches.
- Schedule regular updates for your cloud environment to close off any vulnerabilities.
Implement Multi-Factor Authentication (MFA)
- Require MFA for all access to cloud environments and critical systems.
- MFA adds an extra security layer, cutting down the risk of unauthorized access.
Educate and Train Your Teams
- Hold regular security training sessions for development, DevOps, and operations teams.
- Make sure everyone knows why security matters and how to practice it daily.
Use Cloud-Native Security Tools
- Take advantage of cloud-native security tools that work smoothly with your cloud provider.
- Use the built-in security features your cloud provider offers to boost your security.
Regularly Review and Update Security Policies
- Keep your security policies current with the latest industry standards and best practices.
- Regularly review and tweak policies to keep up with new threats and changes in your cloud setup
Final Words
Are you sure you’re doing enough to protect your digital assets? Given the lightning-fast digital world, securing everything from code to cloud is non-negotiable. But here’s the thing—just following best practices like shifting security left, automating testing, and monitoring your cloud environment might not be enough. Managing all that manually? It’s a nightmare waiting to happen.
That’s where CloudDefense.AI’s CNAPP steps in. CloudDefense.AI gives you a complete toolkit to lock down your security without the hassle. From catching risks in your codebase to locking down your cloud workloads, CloudDefense.AI automates the tough stuff, so you don’t have to worry. With the right tools and strategies, you can protect your digital assets in the cloud and breathe easy, knowing you’ve got it all under control.







